Watobo/Usage/Fuzzer
Description
In this lesson, you will learn about fuzzing basics and how to use the Fuzzer module.
Our example will be based on WebGoat, Session Management - Hijack a session. In this example, you will see how to exploit a vulnerable session because of a weak encryption.
Fancy tag
This technique isn't really fuzzing. We are going to force the generation of the same page to get the value of the WEAKID cookie for each, and try to find a pattern in it.
Point your browser to WebGoat at the address of the exercise (Session Management Flaws > Hijack a Session): http://localhost:8080/webgoat/attack?Screen=139&menu=1800, enter foo and bar respectively as login and password and submit the form.
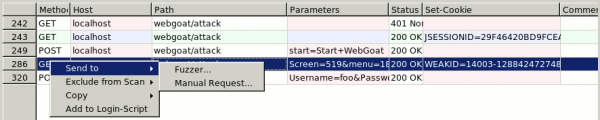
Identify the chat that is responsible of the WEAKID cookie definition (#286 in the screenshot). Right click on it and select Send to > Fuzzer.
Define a fancy tag that generates 50 session IDs
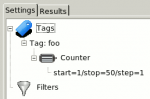
- In the right panel, double click on Tag and give it the name foo
- Double click on the newly created foo tag and select a generator from type Counter. Define it with these values: Start=1, Stop=50, Step=1.
- Uncheck the box "Update Session Information" to be sure that the ID will be different each time
- In the left panel, click on the Start button to start fuzzing
- In the right panel, select the Results tab and export them (click on "Save Matches") in a path of your choice (e.g. /data/tmp/fuzz.txt).
Analyze the results
- The exported results show the server's responses. We have a file that is grepable. Issue this command:
$ cd /data/tmp/ $ grep Set-Cookie fuzz.txt | sort
It indicates to show only the lines where the Set-Cookie (the definition of our WEAKID) appears, and we send the result to the unix sort function to order the results.
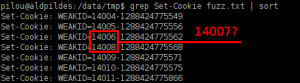
- We notice holes in the sequence. Here is an example:
Crack the session
Now we have the first missing pat of our WEAKID but we still need to know the second part. See how the cookie is generated:
| First part | Second part |
|---|---|
| 14005 | 1288424775556 |
| 14006 | 1288424775562 |
| 14007 | 1288424775??? |
| 14008 | 1288424775568 |
| 14009 | 1288424775571 |
Notice in bold the fixed part. The variable part is increasing from one ID to the other. So we deduce that the value that we are looking for is between 562 and 568.
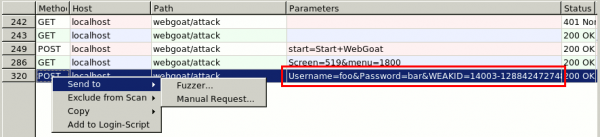
Now, we need to use the record where we send the WEAKID cookie with the credentials. Right click on it and send it to the fuzzer:
Do following actions in the fuzzer window:

- Modify the entire value of WEAKID with the prefix we have found
- Replace the 3 last characters with a variable %%crack%% that we will use as tag
- In the right panel, create a tag named crack
- Right click on that tag and create a generator of type Counter with values between 562 and 568 with an increment of 1
- Uncheck both "Update Content-Length" checkbox and "update Session Information" checkboxes.
- Click on the "Start" button
- On the right panel, go to the results tab and click on the "Save Matches" button. Export the results in /data/tmp/fuzz2.txt.
Analyze the results
- Open a terminal window and point to /data/tmp or whatever directory where you saved fuzz2.txt
- We have completed the exercise:
$ grep -i congrat fuzz2.txt <div id="message" class="info"><BR> * Congratulations. You have successfully completed this lesson.</div>
By further analyzing the file, we deduce that the solution is:
WEAKID=14007-1288424775565
We could also use the Manual Request module to check it:
And by clicking on Browser-View: