Windows-credentials-editor
Jump to navigation
Jump to search
Description
Windows Credentials Editor (WCE) is a tool for Windows boxes that will list, add, edit and delete logon sessions. It outputs a file containing LM/NT hashes that are then crackable via a NTLM brute-forcer.
Installation
The tool is available here: http://www.ampliasecurity.com/research/wce_v1.0.tgz
Usage
Basic usage
C:\cwe\> cwe.exe [options]
Options
- -l
- List logon sessions and NTLM credentials (default).
- -s
- Change NTLM credentials of current logon session.
- -r
- List logon sessions and NTLM credentials indefinitely.
- Refresh every 5 seconds if new sessions are found.
- Optional: -r.
- -c
- Run in a new session with the specified NTLM credentials.
- -e
- List logon sessions NTLM credentials indefinitely.
- Refresh every time a logon event occurs.
- -o <file>
- Save all output to a file.
- -i <LUID>
- Specify LUID instead of use current logon session.
- -d
- Delete NTLM credentials from logon session.
- -v
- Verbose output.
Output example
Here is an example. Following command issued while connected as administrator on a Windows XP box...
C:\wce\>wce.exe -o output.txt
...produces:
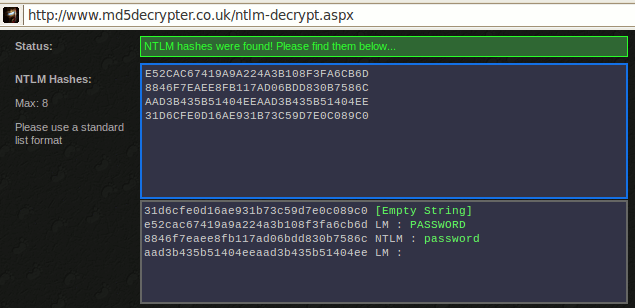
Administrator:WIN-D4CC369A8C5:E52CAC67419A9A224A3B108F3FA6CB6D:8846F7EAEE8FB117AD06BDD830B7586C willyboy:WIN-D4CC369A8C5:AAD3B435B51404EEAAD3B435B51404EE:31D6CFE0D16AE931B73C59D7E0C089C0 WIN-D4CC369A8C5$:ALDEID:AAD3B435B51404EEAAD3B435B51404EE:31D6CFE0D16AE931B73C59D7E0C089C0
We can then use online resources (e.g. http://www.md5decrypter.co.uk/ntlm-decrypt.aspx) to reverse the hashes: