SysAnalyzer/SysAnalyzer
| You are here: | SysAnalyzer
|
Description
SysAnalyzer is an application that was designed to give malcode analysts an automated tool to quickly collect, compare, and report on the actions a binary took while running on the system.
The main components of SysAnalyzer work off of comparing snapshots of the system over a user specified time interval. The reason a snapshot mechanism was used compared to a live logging implementation is to reduce the amount of data that analysts must wade through when conducting their analysis. By using a snapshot system, we can effectively present viewers with only the persistent changes found on the system since the application was first run.
While this mechanism does help to eliminate allot of the possible noise caused by other applications, or inconsequential runtime nuances, it also opens up the possibility for missing key data. Because of this SysAnalyzer also gives the analyst the option to include several forms of live logging into the analysis procedure.
Usage
Wizard
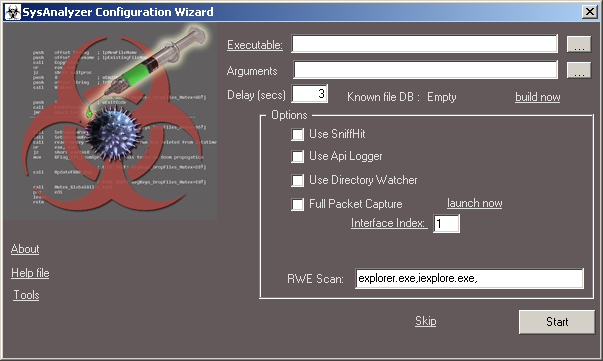
When first run, SysAnalyzer will present the user with the following configuration wizard:
The executable path textbox represents the file under analysis. It can be filled in either by
- Dragging and dropping the target executable on the SysAnalyzer desktop icon
- Specifying the executable on the command line
- Dragging and Dropping the target into the actual textbox
- Using the browse for file button next to the textbox
Once this is done, the user can specify the following options to be used for the analysis:
- Delay - time in seconds between before and after snapshots
- Sniff Hit - whether to launch a specialized http/irc sniffer for analysis
- Api Logger - whether to inject a api logging dll into the target
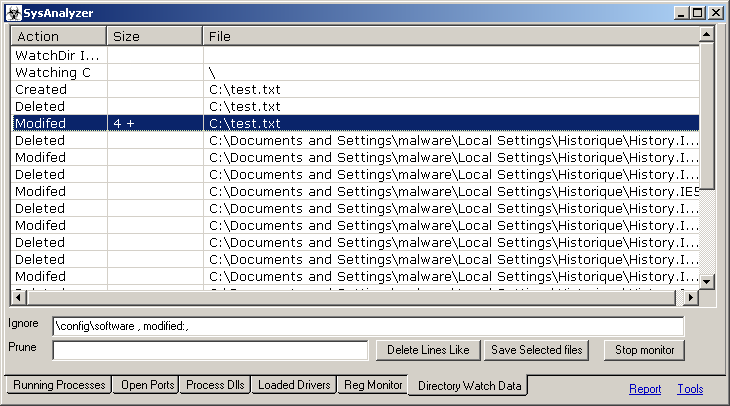
- Directory Watcher - whether to monitor filesystem for all file creation activities
- Full Packet Capture - whether to run a full packet capture (not limited to HTTP and IRC communications)
These options are saved to a configuration file and do not need to be entered each time. Note that users can also select the "Skip" link in order to proceed to the main interface where they can manually control the snapshot tools.
Once these options are filled in and the user selects the "Start button" the options will be applied, a base snapshot of the system taken, and the executable launched.
Manual analysis
If you click on "Skip", you will be redirected to the manual analysis interface.
Snapshots
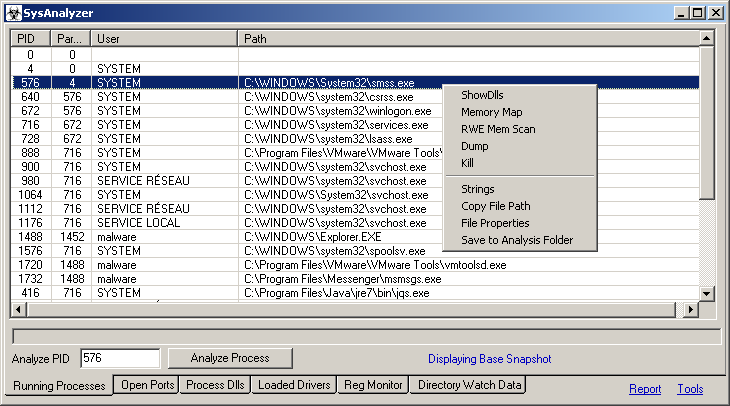
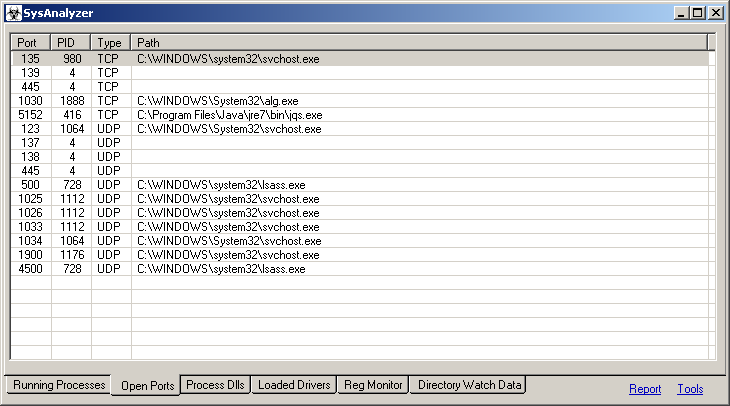
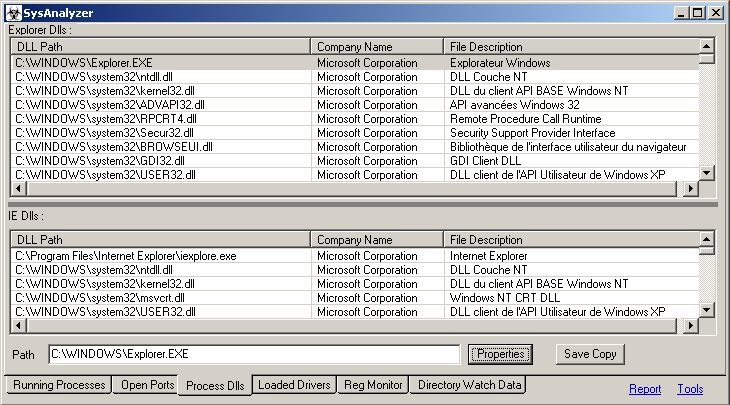
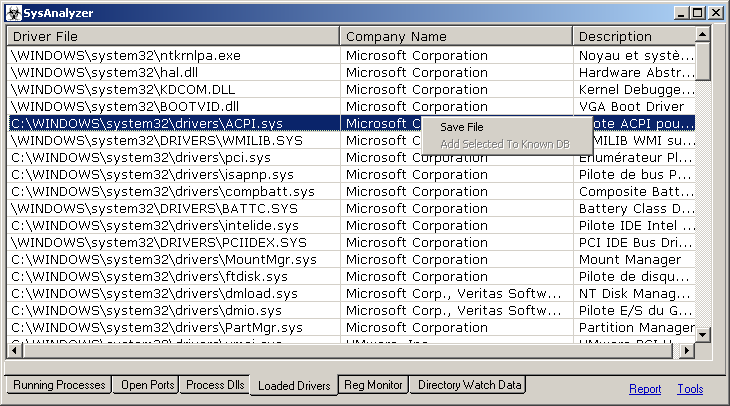
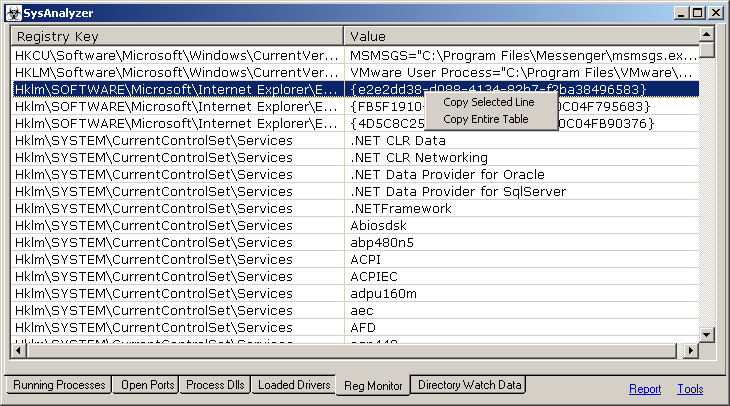
SysAnalyzer's is designed to take snapshots of the following system attributes:
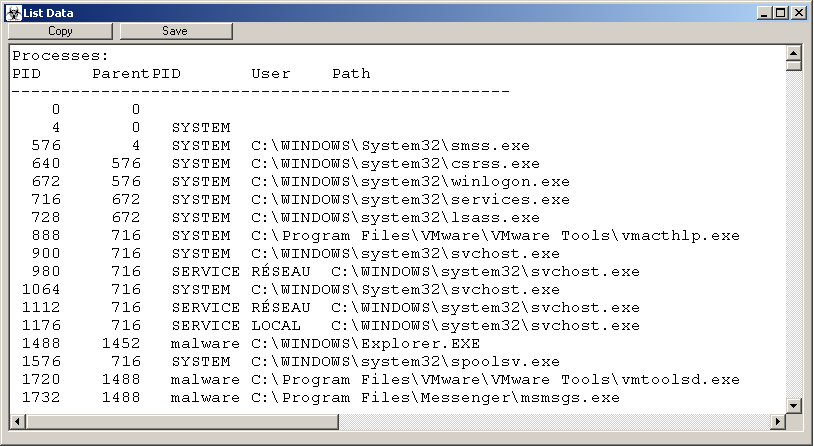
- Running processes
- Open ports and associated process
- Dlls loaded into explorer.exe and Internet Explorer
- System Drivers loaded into the kernel
- Snapshots of certain registry keys
Each logged catagory is stored on its own tab in the main interface. The report link to the bottom right of the main interface can conglomerate all of this log data and place it into a simple text report for the user.
Known files database
The known file database feature is used to allow you to efficiently filter your results so as to hide known trusted files from display.
In order to use it from the main wizard form, click skip , then goto the tools menu and choose the menu item to build known file db. This will bring up a seperate form where you can launch the system file scanner which will enumerate all exe, dll, and sys files on your system. Make sure to only run this on a known clean system because any files it detects will be assumed to be clean in the future. It will store the file name, path, version and hash. Once this completes, you can close this form and select the tools menu item for hide known files. When this menu item is checked, all known files in the database will be hidden from display in the listboxes. If there are known clean files still displayed (files outside of the scanned default directories) just click the tools menu item to update known files. This form will list all of the unknown files presently shown in a given snapshot and allow you to easily mark the ones you trust as known.
If you have built a known database, known files will display in blue. Known files that have had their MD5 hash change will show in red.
Tabs
Running processes
Open ports
Process Dlls
Loaded drivers
Reg Monitor
Directory Watch Data
Report
- Search All Tabs: enables to search a given string in all tabs
- Copy All Selected Entries: copy all selected text
- Show Snapshot 1: show data captured in the first snapshot
- Show Snapshot 2: show data captured in the second snapshot
- Show Diff Report: show differences between the 2 snapshots
- Take Snapshot 1: take an initial snapshot to be compared with a second one
- Take Snapshot 2: take a second snapshot to be compared with the first one
- Start Over: go back to the beginning (wizard main screen)
- Build Known File DB: The Known Files Database feature is used to allow you to efficiently filter your results so as to hide known trusted files from display.
- Hide Known Files: hide all files added to the Known Files Database
- Updated Known Db
- Report Viewer: show report
- About
- Manual Tools
- Scan Procs for Unknown Dlls
- Scan Procs For Dll
- RWE Mem Scan