An-interesting-forensics-analysis
Introduction
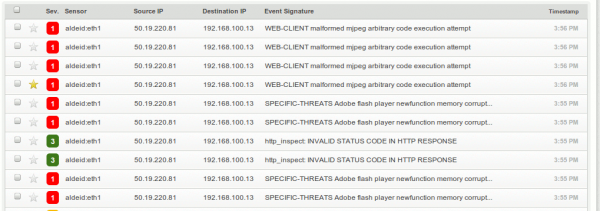
Today I have received a mail from one of my colleagues, containing a link to download a zip archive from his Dropbox account (I wont't tell you what it is ;-). Fine! I'm downloading it when I notice that my Snort probe is sending me strange alerts:
I decide to investigate...
Investigation
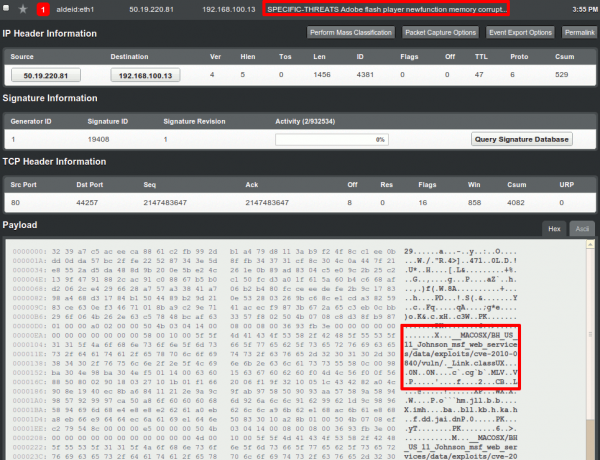
Taking one vulnerability randomly, say "SPECIFIC-THREATS Adobe flash player newfunction memory corrupt...", here are the details:
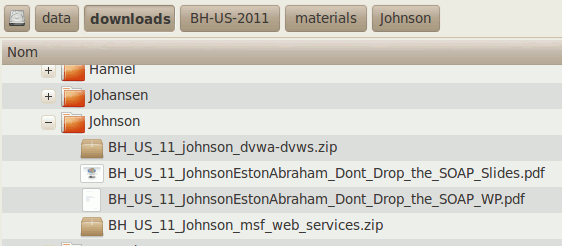
We immediately notice the name of what seems to be a file. By looking in the archive (a zip file) that I just downloaded, I notice that the structure corresponds to what I see here:
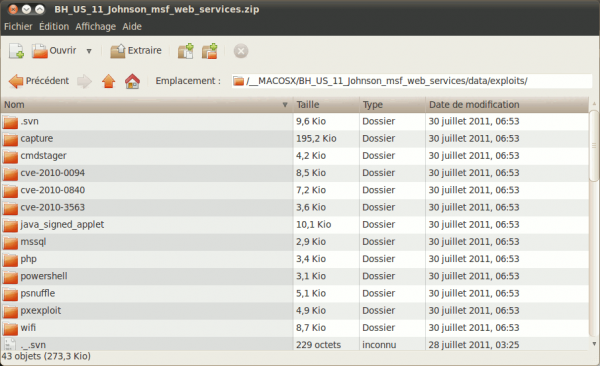
By entering in the zip file, we can confirm the tree structure provided in the details of the alert:
The question is to know what file has triggered the alert.
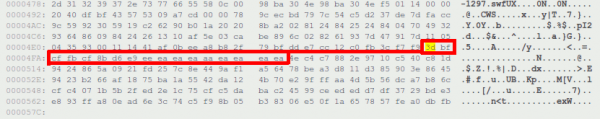
My Snort rule file contains the signature:
# cd /usr/local/etc/snort/rules/ # grep -i "adobe flash player newfunction memory" | grep 19408 * snort.rules:alert tcp $EXTERNAL_NET $HTTP_PORTS -> $HOME_NET any (msg:"SPECIFIC-THREATS Adobe flash player newfunction memory corruption exploit attempt"; flow:to_client,established; content:"CWS|09|"; content:"|3D BF CF FB CF 8B D6 E9 EE EA EA EA AA EA EA EA|"; within:16; distance:94; metadata:policy balanced-ips drop, policy security-ips drop, service http; reference:cve,2010- 0197; reference:cve,2010-1297; classtype:attempted-admin; sid:19408; rev:1;)
... that I can see in the details of the alert:
Let's create a small python script that will parse every file in the zip archive and search for our pattern from the hexadecimal representation of each file:
#!/usr/bin/env python
import os.path
from binascii import hexlify
def listdirectory(path):
f=[]
for root, dirs, files in os.walk(path):
for i in files:
f.append(os.path.join(root, i))
return f
ldir = listdirectory("/home/sdamaye/tmp/")
for f in ldir:
of = open(f, 'r')
if '3dbfcffbcf8bd6e9eeeaeaeaaaeaeaea' in hexlify(of.read()):
print 'Sig found in %s' % f
of.close()
Here are the results:
$ python test.py Sig found in /home/sdamaye/tmp/BH_US_11_Johnson_msf_web_services.zip Sig found in /home/sdamaye/tmp/BH_US_11_Johnson_msf_web_services /BH_US_11_Johnson_msf_web_services/data/exploits/CVE-2010-1297.swf Sig found in /home/sdamaye/tmp/BH_US_11_Johnson_msf_web_services /BH_US_11_Johnson_msf_web_services/data/exploits/.svn/text-base /CVE-2010-1297.swf.svn-base
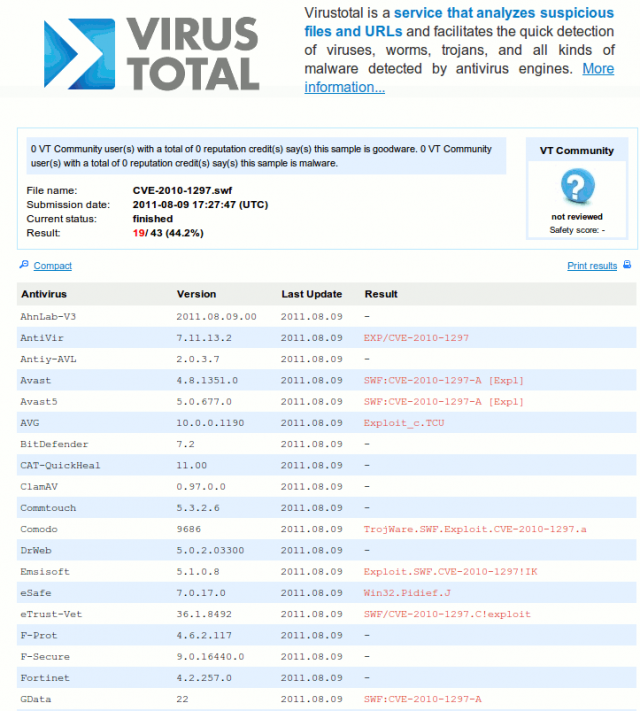
A submission of CVE-2010-1297.swf to VirusTotal confirms that the file is the one I was looking for: