Category:Digital-Forensics/Computer-Forensics/Anti-Reverse-Engineering/Packers/FSG
| You are here: | FSG
|
Description
FSG states for Fast Small Good.
Here are the release dates:
| Version | Release date |
|---|---|
| FSG 1.0 | 2002 January |
| FSG 1.1 | 2002 April |
| FSG 1.2 | 2002 May |
| FSG 1.3 | 2002 August |
| FSG 1.31 | 2002 August |
| FSG 1.33 | 2002 November |
| FSG 2.0 | 2004 May |
Unpacking FSG 1.0
SFX module
It is possible to find the real entry point with the SFX module and then dumping the process with OllyDump.
Find OEP by Section Hop
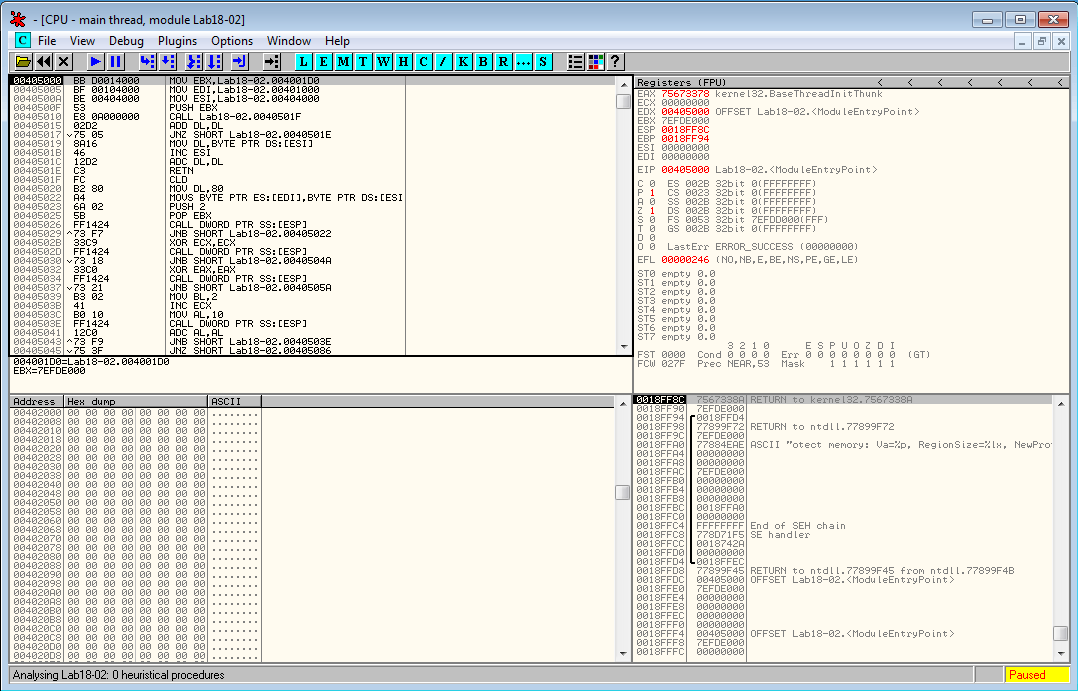
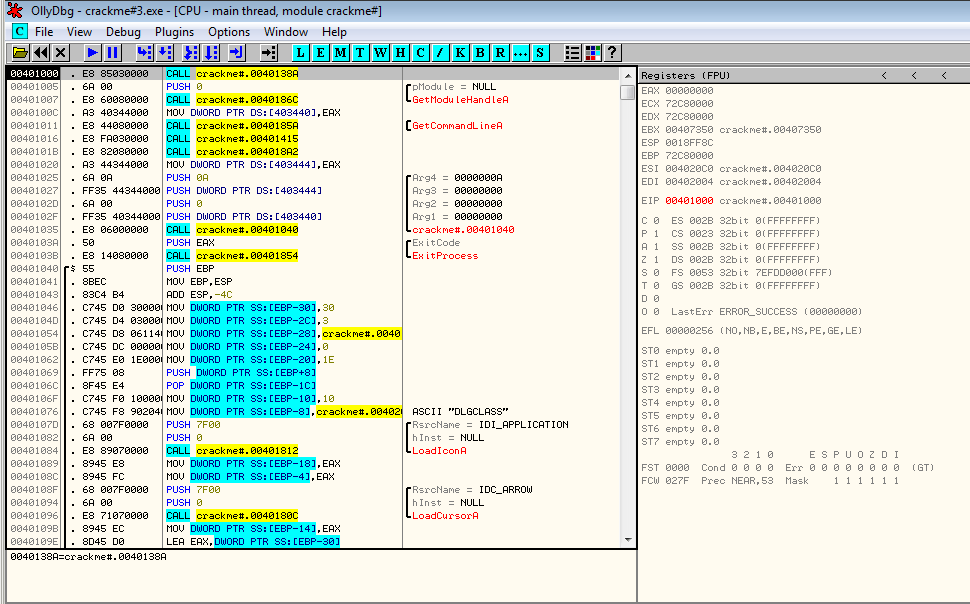
Below is an example of a malware packed with FSG 1.0. When it is run, it stops at entry point 0x401050:
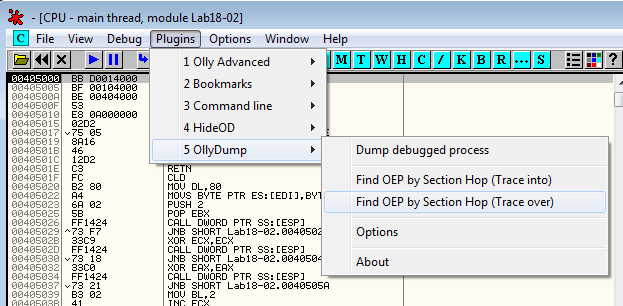
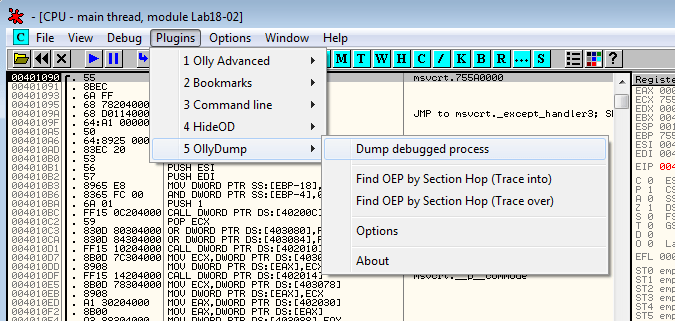
Let's try to find the OEP with Plugins > OllyDump > Find OEP by Section Hop (Trace over):
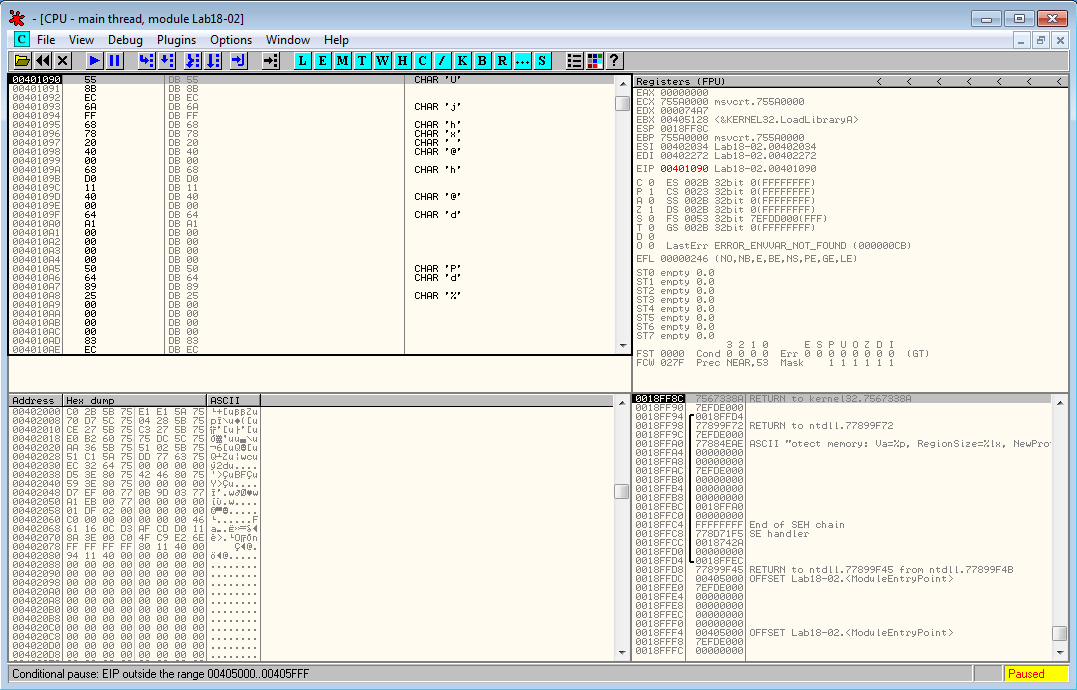
The plugin has found the OEP at 0x401090, which is encouraging because this location is close to the beginning of the executable (0x401000)
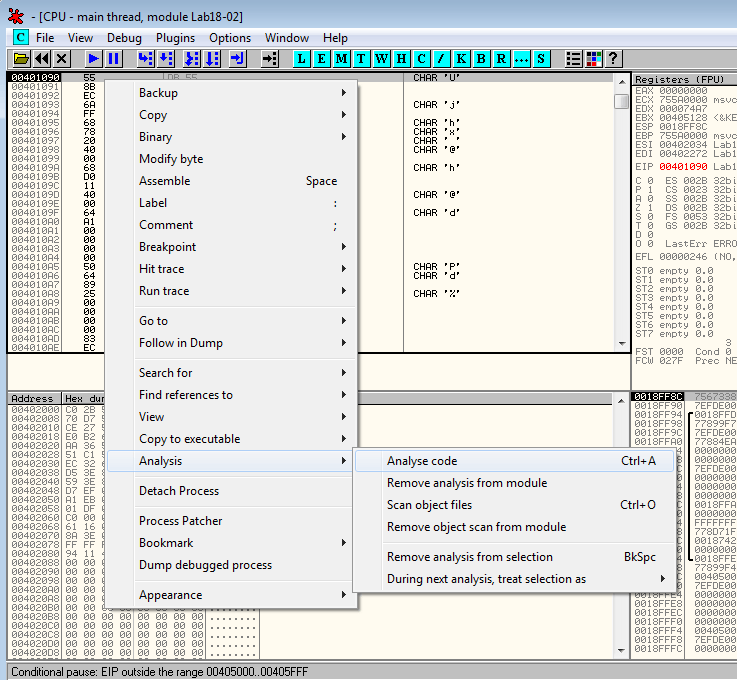
OllyDbg hasn't disassembled the code at this location. Right click on the first byte of the code and select Analysis > Analyze code
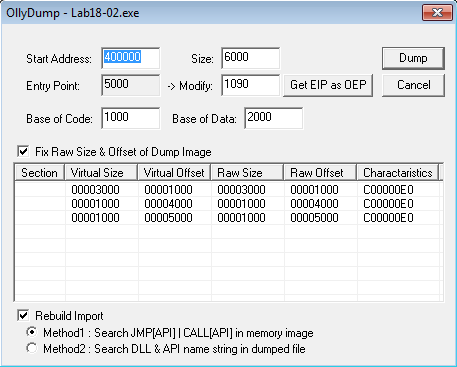
It seems to be the beginning of a function, which confirms that we likely to have found the OEP. Let's dump the process (Plugins > OllyDump > Dump debugged process):
Accept the default values and click on the Dump button. We're done.
Unpack FSG 2.0
Let's unpack this program. PEiD shows that the program is packed with "FSG 2.0 -> bart/xt".
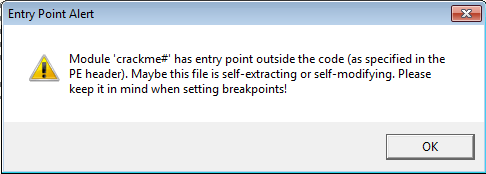
Open the program in OllyDbg. It will warn that the entry point is outside of the code's section. Just hit OK.
The program stops at the beginning of the unpacking routine:
00400154 > 8725 4C734000 XCHG DWORD PTR DS:[40734C],ESP ; Save ESP to 0x40734C
0040015A 61 POPAD ; Retrieve registers
0040015B 94 XCHG EAX,ESP ; Loads ESP into EAX
0040015C 55 PUSH EBP ; EBP = 0x4020A8
Later in the code, we can see a serie of conditional jumps as follows:
004001CD ^78 F3 JS SHORT crackme#.004001C2
004001CF 75 03 JNZ SHORT crackme#.004001D4
004001D1 FF63 0C JMP DWORD PTR DS:[EBX+C]
Put a breakpoint at the last jump (0x4001D1 in our example) and run the program. When the brekapoint is hit, step into (F7).
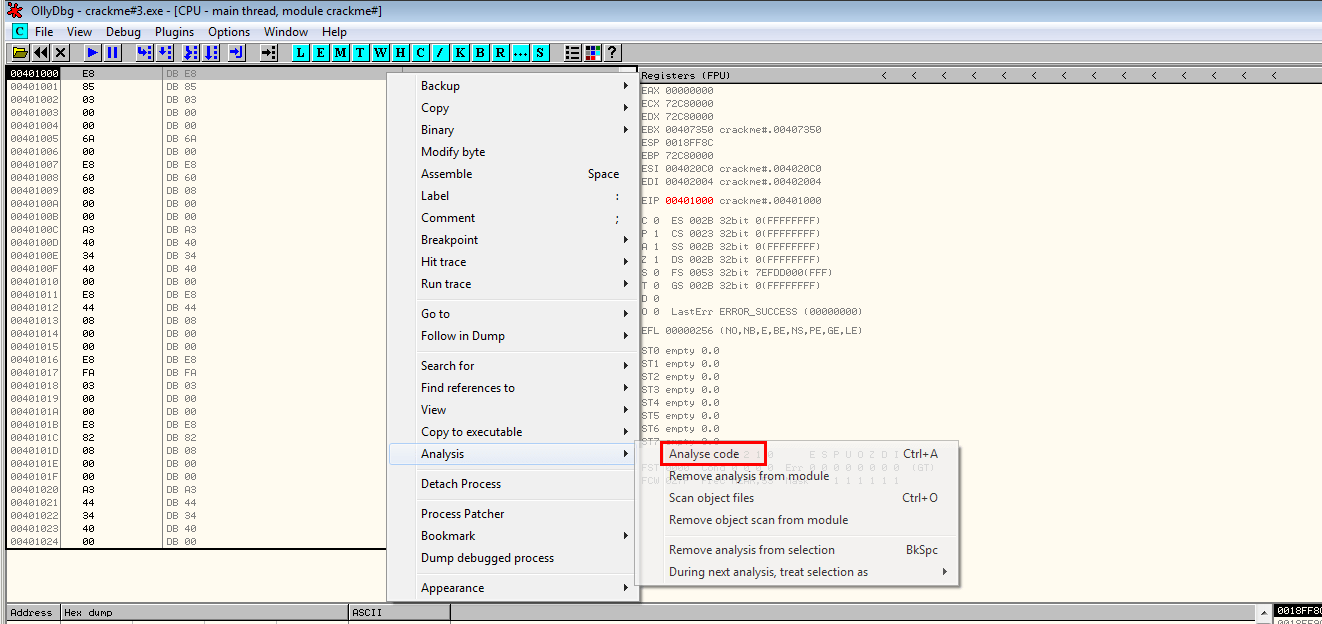
The code at this location hasn't been interpreted by OllyDbg. Right click and select Analysis > Analyze code
This is the unpacked code. All you need to do is to dump the code with OllyDump.
Comments
Pages in category "Digital-Forensics/Computer-Forensics/Anti-Reverse-Engineering/Packers/FSG"
The following 2 pages are in this category, out of 2 total.