Category:Digital-Forensics/Computer-Forensics/COM-Component-Object-Model
Description
The Component Object Model (COM) is a Microsoft interface standard that enables different applications to call each other without knowledge of specifics. It's implemented as a client/server framework where the client is the application that uses COM objects and the server is the reusable software component.
An application that makes use of COM must call one of these 2 functions:
GUID, CLSID and IID
COM objects are accessible via their Globally Unique Identifiers (GUID) also called Class Identifiers (CLSID) and their Interface Identifiers (IID). The CoCreateInstance function is used for that purpose.
CLSIDs are listed by the Registry database in 2 keys:
- HKLM\SOFTWARE\Classes\CLSID
- HKCU\SOFTWARE\Classes\CLSID
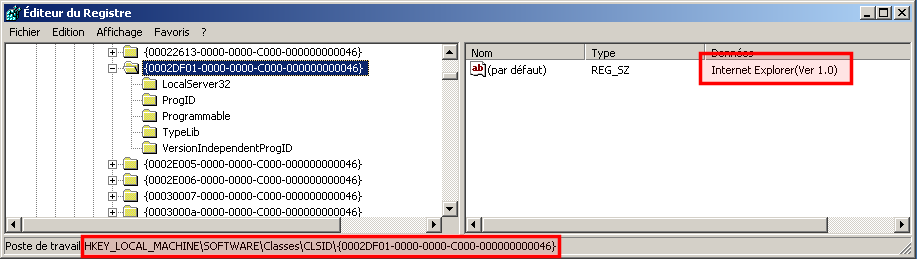
Here is the CLSID for Internet Explorer (0002DF01-0000-0000-C000-000000000046):
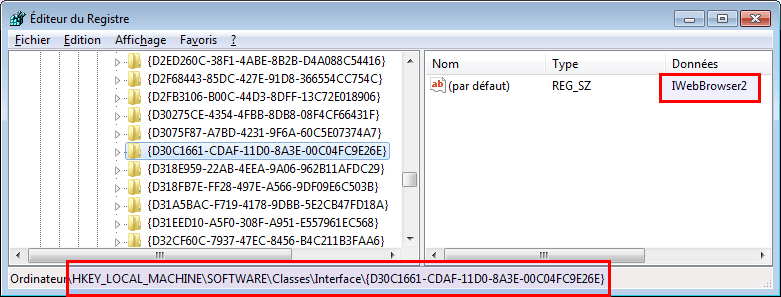
Here is the RIID for IWebBrowser2 interface (D30C1661-CDAF-11D0-8A3E-00C04FC9E26E):
Example
.text:00401003 push 0 ; pvReserved
.text:00401005 call ds:OleInitialize
.text:0040100B test eax, eax
.text:0040100D jl short loc_401085
.text:0040100F lea eax, [esp+24h+ppv]
.text:00401013 push eax ; ppv
.text:00401014 push offset riid ; riid
.text:00401019 push 4 ; dwClsContext
.text:0040101B push 0 ; pUnkOuter
.text:0040101D push offset rclsid ; rclsid
.text:00401022 call ds:CoCreateInstance
.text:00401028 mov eax, [esp+24h+ppv]
.text:0040102C test eax, eax
.text:0040102E jz short loc_40107F
.text:00401030 lea ecx, [esp+24h+pvarg]
.text:00401034 push esi
.text:00401035 push ecx ; pvarg
.text:00401036 call ds:VariantInit
.text:0040103C push offset psz ; "http://www.malsite.com/x.html"
.text:00401041 mov [esp+2Ch+var_10], 3
.text:00401048 mov [esp+2Ch+var_8], 1
.text:00401050 call ds:SysAllocString
.text:00401056 lea ecx, [esp+28h+pvarg]
.text:0040105A mov esi, eax
.text:0040105C mov eax, [esp+28h+ppv]
.text:00401060 push ecx
.text:00401061 lea ecx, [esp+2Ch+pvarg]
.text:00401065 mov edx, [eax]
.text:00401067 push ecx
.text:00401068 lea ecx, [esp+30h+pvarg]
.text:0040106C push ecx
.text:0040106D lea ecx, [esp+34h+var_10]
.text:00401071 push ecx
.text:00401072 push esi
.text:00401073 push eax
.text:00401074 call dword ptr [edx+2Ch]
.text:00401077 push esi ; bstrString
.text:00401078 call ds:SysFreeString
.text:0040107E pop esi
.text:0040107F
.text:0040107F loc_40107F:
.text:0040107F call ds:OleUninitialize
The malware initializes COM at address 0x00401005 with OleInitialize and obtains a pointer to the COM object at address 0x00401022 with CoCreateInstance. To identify the COM object, we need to click on riid and rclsid:
.rdata:00402058 ; IID rclsid
.rdata:00402058 rclsid dd 2DF01h ; Data1
.rdata:00402058 dw 0 ; Data2
.rdata:00402058 dw 0 ; Data3
.rdata:00402058 db 0C0h, 6 dup(0), 46h ; Data4
.rdata:00402068 ; IID riid
.rdata:00402068 riid dd 0D30C1661h ; Data1
.rdata:00402068 dw 0CDAFh ; Data2
.rdata:00402068 dw 11D0h ; Data3
.rdata:00402068 db 8Ah, 3Eh, 0, 0C0h, 4Fh, 0C9h, 0E2h, 6Eh; Data4
Hereis what we obtain:
- rclsid: 0002DF01-0000-0000-C000-000000000046, which corresponds to Internet Explorer
- riid: D30C1661-CDAF-11D0-8A3E-00C04FC9E26E, which corresponds to IWebBrowser2
The COM functionnality is accessed from address 0x0040105C.
Following this instruction, EAX points to the location of the COM object.
At address 0x00401065, EAX is dereferenced and EDX points to the beginning of the COM object itself.
At address 0x00401074, the function at an offset of +0x2C from the object is called. It corresponds to the Navigate function of the IWebBrowser2 interface. When this function is called, the URL http://www.malsite.com/x.html will be browsed with Internet Explorer.
Comments
Pages in category "Digital-Forensics/Computer-Forensics/COM-Component-Object-Model"
The following 10 pages are in this category, out of 10 total.