Fb1569b5a3266444d676e5f82d6bac85
Description
Summary

Thank you for your comprehension.
Packer
The file is not packed.
Identification
| MD5 | fb1569b5a3266444d676e5f82d6bac85 |
|---|---|
| SHA1 | f0d76b3806e58ae5363a78dcc62b5e27a90a7ecf |
| SHA256 | 5b7228947b256f36bd98dde1622799cda8f7a7aa0f3196aba08200fe8439dfee |
| ssdeep | 768:OIVlbMb8fL1YwirvVmcWXhi+I661D/wlzPDruLDTB:OsiADEtLWxSHh |
| imphash | 1cb870387607e7be0740f69126dcaf5e |
| File size | 42.0 KB ( 43008 bytes ) |
| File type | Win32 EXE |
| Magic literal | PE32 executable for MS Windows (GUI) Intel 80386 32-bit |
Antivirus detection
| Antivirus | Result | Update |
|---|---|---|
| AVG | I-Worm/Doomjuice.A | 20140220 |
| Ad-Aware | Win32.Worm.Doomjuice.A | 20140220 |
| Agnitum | Worm.Doomjuice!sS8KPxF1s1E | 20140220 |
| AhnLab-V3 | Win32/Doomjuice.worm.43008 | 20140220 |
| AntiVir | Worm/Doomjuice | 20140220 |
| Antiy-AVL | Worm[Net]/Win32.Doomjuice | 20140219 |
| Avast | Win32:Doomjuice-C [Wrm] | 20140220 |
| Baidu-International | Worm.Win32.Doomjuice.AoF | 20140220 |
| BitDefender | Win32.Worm.Doomjuice.A | 20140220 |
| Bkav | W32.Clod54f.Trojan.b1f4 | 20140220 |
| CAT-QuickHeal | W32.Doomjuice | 20140220 |
| CMC | Generic.Win32.fb1569b5a3!MD | 20140220 |
| Commtouch | W32/Backdoor.URMY-3995 | 20140220 |
| Comodo | Worm.Win32.Doomjuice.~BA | 20140220 |
| DrWeb | Win32.HLLW.MyDoom.43008 | 20140220 |
| ESET-NOD32 | Win32/Doomjuice.A | 20140220 |
| Emsisoft | Win32.Worm.Doomjuice.A (B) | 20140220 |
| F-Prot | W32/Backdoor.HST | 20140220 |
| F-Secure | Win32.Worm.Doomjuice.A | 20140220 |
| Fortinet | W32/MyDoom.B@mm | 20140220 |
| GData | Win32.Worm.Doomjuice.A | 20140220 |
| Ikarus | Net-Worm.Win32.Doomjuice.A | 20140220 |
| Jiangmin | I-Worm/MyDoom.c | 20140220 |
| K7AntiVirus | Backdoor ( 0f33269f0 ) | 20140220 |
| K7GW | Trojan ( 00004e2c1 ) | 20140220 |
| Kaspersky | Net-Worm.Win32.Doomjuice.a | 20140220 |
| Kingsoft | Worm.Doomjuice.a.(kcloud) | 20140220 |
| McAfee | W32/Doomjuice.gen | 20140220 |
| McAfee-GW-Edition | W32/Doomjuice.gen | 20140220 |
| MicroWorld-eScan | Win32.Worm.Doomjuice.A | 20140220 |
| Microsoft | Worm:Win32/Doomjuice.A | 20140220 |
| NANO-Antivirus | Trojan.Win32.Doomjuice.bmlcj | 20140220 |
| Norman | Malware | 20140220 |
| Panda | W32/Doomjuice.A.worm | 20140220 |
| Qihoo-360 | Win32/Worm.e90 | 20140220 |
| Rising | PE:Trojan.Win32.Generic.122D4E91!304959121 | 20140219 |
| Sophos | W32/Doomjuice-A | 20140220 |
| Symantec | W32.HLLW.Doomjuice | 20140220 |
| TheHacker | W32/DoomJuice.worm | 20140220 |
| TotalDefense | Win32/Doomjuice.A | 20140220 |
| TrendMicro | TROJ_GEN.R0CBC0CIC13 | 20140220 |
| TrendMicro-HouseCall | TROJ_GEN.R0CBC0CIC13 | 20140220 |
| VBA32 | Worm.Doomjuice | 20140220 |
| VIPRE | BehavesLike.Win32.Malware.ssc (mx-v) | 20140220 |
| ViRobot | Worm.Win32.Net-Doomjuice.43008 | 20140220 |
| nProtect | Worm/W32.Doomjuice.43008 | 20140220 |
| ByteHero | 20140220 | |
| ClamAV | 20140220 | |
| Malwarebytes | 20140220 | |
| SUPERAntiSpyware | 20140220 |
Defensive capabilities

Thank you for your comprehension.
Dynamic analysis
Network indicators
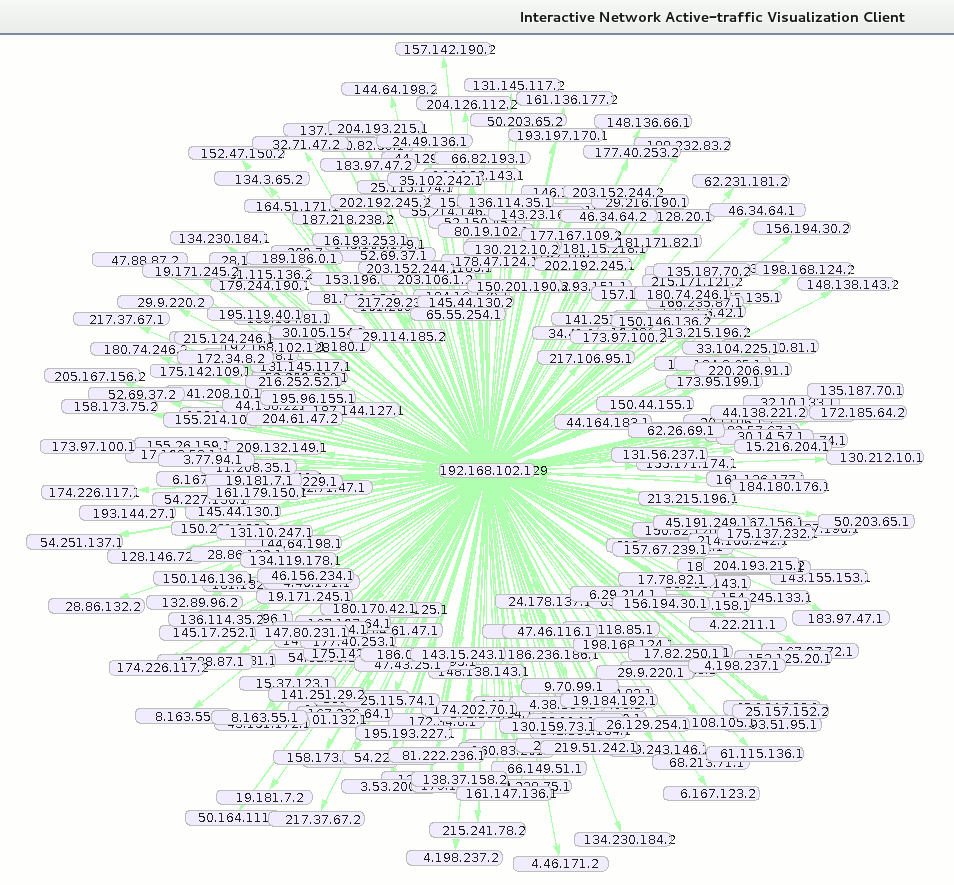
Connections to random IPs on port 3127 (screenshot made from Inav):
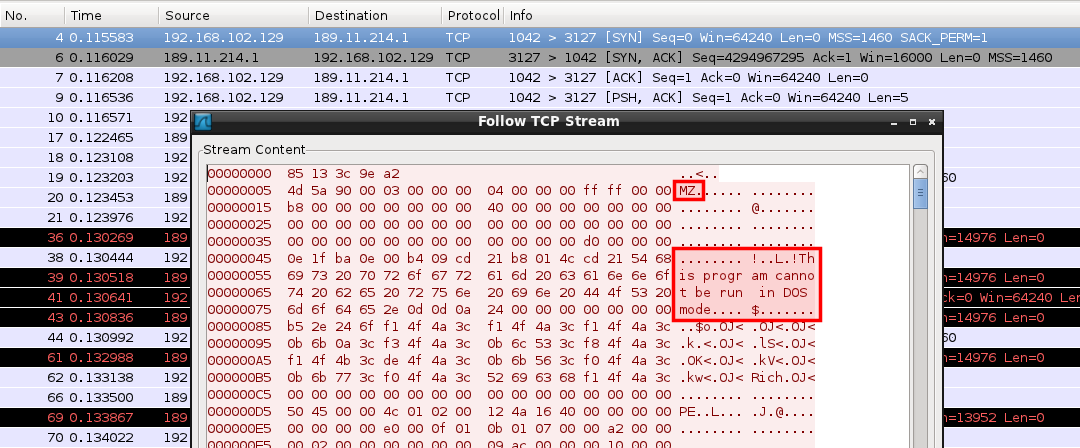
An executable file seems to be pushed to the remote hosts:
Looking for "0x85 0x13 0x3C 0x9E 0xA2" on Google reveals that this is probably a command sequence that the MyDoom worm used to upload files through its backdoor.
Files
sync-src-1.00.tbz
Following file is created:
| Path |
|
|---|---|
| Name | sync-src-1.00.tbz |
| MD5 | 32d24e642e87affc9eb692ef4bf97772 |
Once unziped, this produces following structure:
sync-1.00/ |-- lib.c |-- lib.h |-- main.c |-- makefile |-- massmail.c |-- massmail.h |-- msg.c |-- msg.h |-- p2p.c |-- _readme.txt |-- resource.ico |-- resource.rc |-- scan.c |-- scan.h |-- sco.c |-- sco.h |-- work | |-- bin2c.c | |-- cleanpe.cpp | |-- crypt1.c | |-- rot13.c | `-- stub.exe |-- xdns.c |-- xdns.h |-- xproxy | |-- client.c | |-- makefile | `-- xproxy.c |-- xsmtp.c |-- xsmtp.h |-- zipstore.c `-- zipstore.h
This is the source code of the MyDoom.A worm.
Doomjuice looks through the network for the open port 3127/tcp, which is used by MyDoom. If a computer is infected by any of the Worm/MyDoom version, Worm/Doomjuice uses the MyDoom backdoor components to install and activate itself on this computer.
intrenat.exe
The malware copies itself as C:\WINDOWS\system32\intrenat.exe
| Path | C:\WINDOWS\system32\ |
|---|---|
| Name | intrenat.exe |
| MD5 | fb1569b5a3266444d676e5f82d6bac85 |
Registry keys
Registry key added:
| Path | HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
|---|---|
| Name | Gremlin |
| Type | REG_SZ |
| Value | C:\WINDOWS\system32\intrenat.exe |
Mutexes

Thank you for your comprehension.
Static analysis
Sections
Name VirtAddr VirtSize RawSize Entropy -------------------------------------------------------------------------------- .text 0x1000 0xa0be 0xa200 6.909625 .data 0xc000 0xa4 0x200 3.184141
Strings
BZh91AY&SY
^WJ\
ws7e
q|,}
;/3v
.MO*BP
OMO(
8%"k
+!ZH2PPFf
li4JR
1(e"
6fWU
YY~J
_3y0
4&ZSI
Z*#
i5IFR
#e*T
jhSX
d!M
3zT;
cPL(
1=Wb
[cct
u=3f
QWYZ
CV7!P
!=CC
{3Ll
,fB&
wIsvG]
OK{/H
"I DW
n$blk
vF0ll+
?=`6b
V!(F
!-E)
.|Xx
$c$e
W36a
Bop;
6kHaX
>'>.
<~/T
T `{
DnHI"
9ip*
0,{Ja
l,?)GA
)>#/+
@R@
JoK~
}'C-*}
RBS4
,[jp
8ono5
z/Owy
(xf;I
i@b
'kx^^
DpbD
Y}<3
Ux"Sp
l,*p[
Q@x F
33(@
Bako
FDDy
Euz1{
LT_X_7}?W
FybG/_~
9%8M
0AE5
h8aT[
7JGC
2dE2h5!
dD)I&K
Z Kndg
yFr(
nskAv
Ne .
7"5R
5*J
NWCy
>PVN1
dWA
]-Kw
sN<%z9x}
?<CNl
c5N?O
?TG3
&E0g
pQU:~to
oT=~
8a|k
B#~0
jQGz
J#,(@$8<
[DlcA
8"oC
g"AVO
|_02|
FPL
zLYxU_
1Cw.yjf5v
E"P'
&TU:
v>mK
k#|K
R#aQ!OL
7{+$
Ls%JDS
`}[<
QYAa
z\.%|
{.|'
C1P2
m-2el
pzj_^
gbi0
<V}#<
%tgjN}
ue6c
-W3IN
vbl+
MrBX/
c`3)
K,[h
Pj&4
u\-v
Y*)G
9hJ.h\
&eUqr
J*) J
nEZ
Pz%R
`$Aq
Cig{
faS4
t<Os=C
_YP
O/0`f
lo4F
Q$'%C
fFMh
%f<J
Q:/Y
BsKF
FI!$$8
e~RF
(/|6h
b"MW
C%_4pQ
-8f`
#1EWe
6 BM
c@2D
#K~;4h
C-q<
Df>&T_
b&)%k&
Of0
II4?
/'!9L
i)e%
E<~C9
QMJ2
&YVg
8_ 8
@b@#J
p#eDV
#Vjo
a.i_
qZu`bH
#i;v
/!;n
Ylb6
36}J
R`H2
cnx'
sO.l
s,H@
*@(3
\p0:x
(olKB
aLOs
oLI8
DF(-E
jLDlD!
#!}-
LKGj
&*JHi8
yAx]O 0U
!IA:
hl05
$p8|
u/Pt
FG C
8f>~
&E"
+Pw
;?6jW
&lcG
$XZc
73?N
4l|r2
{CZ{
BD( F
OLX{)
RA]S
kWmj
Lc+l
}?OYx
D<rp
F8`m
_GWQ
b&&G'(
W P}
pkK\
<hR]
!oas
(eE9
g-PZ
a-^w
P\8P
YoJ5
Z^*
DKp!
~O>PL
aJpL
aBW#
M l4
9BhN
I4J[6D)
Q})I@i
-DxD
3ssi
"a7!6
9a!7
,v}{
\]6n
BF2I;
B<_c
+1N$
"xe7
"6"2
<"{@
)#"!Z
5~k[}
y.u"
p"S
ok]k
Vo C
^ooC
}R;;
5T_k
5E?Bv
l[RM
oZ]WW&
.FHF
r&'F
4>rK
{OFP
joO4ZQ
muRl
r~<8
_6_8l
"c#!4
lm6=
K0T-SAj
F,P"
z'q!R
17r=
!&'
H ii
A0|{
I_N~
Yn|2j
DBG#
b=69C
L`-B-k
ww_/w
&&&q
R{[J
?=/U
.UJn
a#2}
$~va
S+'m
0V2C
x6B*
eeqX#
u<}8x0
qTH{l
Azcdj
/mp<|\#
Adg
X;Yb
<aZH]
{zLB
4#|+}
\i6n
!Q4cCn
22=@
!" s
fRIM
8>gi
,[9q0x
QSRY
r9sH
)OO3
L4Ot<IA
Axb
),c>
"W7/+
og55
CjjAQ
Nu'=]lmN2S
GD\)
0_*^
vQy(L
PF"!
bfHX(*
vq $!
4TIf
<oM6
uFYh@
7,h(
Kod&1
>Z2'W&
yIJ+(4
j4F*
%2%"
J`8z
"F41
j/Vk
QW.+
#2)
q~k@~
@T#`b
:M-1
~Y~G
L5hF
#;#b
_uQh
OP {
Jg>x
['@1
I;zO
Fey#
~LO.u
Xe2F&
e$s$
>lo^Z
'N=@H>
,"Em9
tq"p
k.rN
$R0p
W3SYKR
X~5;
7c),p
'# sC
jbM5
m)c$
~H-L
=v,Tl=
7p9J
0Ym|
I75uU
p9M,
Y6Ts
HT<?%
QUEU
>bhcb
dF|~>o
ginwLT
w/[w
#G5k
j9R4&-!
"3&r
/Q w
JV+e
'&VD
G ink
N2w$
BF "
U,05
LXGe s0
]x$"h
6rNq
6RhX
g|xn
"hb_
5-y`
s&9I 9
LhU/
fjfR
MU1$d
(F^f3
$hcf
f1]*
Vkzz
BDdI$a
$gPU
"9@9
H