OfficeMalScanner/OfficeMalScanner
| You are here: | OfficeMalScanner
|
Description
OfficeMalScanner is a MS Office forensic tool to scan for malicious traces, like shellcode heuristics, PE-files or embedded OLE streams.
The tool will look for several strings and API calls to guess if the document is likely to be malicious:
- FS:[30h]
- FS:[00h]
- API-Hashing signature
- API-Name GetSystemDirectory string
- API-Name CloseHandle string
- API-Name VirtualAlloc string
- API-Name GetProcAddr string
- API-Name LoadLibrary string
- Function prolog signature
- CALL next/POP signature
- ...
Usage
Syntax
Usage: OfficeMalScanner <PPT, DOC or XLS file> <scan | info> <brute> <debug>
Options & Switches
Options
- scan
- scan for several shellcode heuristics and encrypted PE-Files
- info
- dumps OLE structures, offsets+length and saves found VB-Macro code
- inflate
- decompresses Ms Office 2007 documents, e.g. docx, into a temp dir
Switches
Following switches are intended to be used in combination with the scan option:
- brute
- enables the "brute force mode" to find encrypted stuff
- debug
- prints out disassembly resp hexoutput if a heuristic was found
Examples
info option (tested with a legacy XLS binary)
C:\tools\OfficeMalScanner>OfficeMalScanner.exe "C:\Documents and Settings\malware\Bureau\vbmacros\vbmacro.xls" info
+------------------------------------------+
| OfficeMalScanner v0.58 |
| Frank Boldewin / www.reconstructer.org |
+------------------------------------------+
[*] INFO mode selected
[*] Opening file C:\Documents and Settings\malware\Bureau\vbmacros\vbmacro.xls
[*] Filesize is 33280 (0x8200) Bytes
[*] Ms Office OLE2 Compound Format document detected
[*] Format type Excel
--------------------------------------
[Scanning for VB-code in VBMACRO.XLS]
--------------------------------------
Sheet1
Sheet2
Sheet3
ThisWorkbook
-----------------------------------------------------------------------------
VB-MACRO CODE WAS FOUND INSIDE THIS FILE!
The decompressed Macro code was stored here:
------> C:\tools\OfficeMalScanner\VBMACRO.XLS-Macros
-----------------------------------------------------------------------------
Notice that OfficeMalScanner has extracted the macros (saved in C:\tools\OfficeMalScanner\VBMACRO.XLS-Macros) contained in the Excel sheeets. Let's have a look at the last one contained in the ThisWorkBook sheet:
Attribute VB_Name = "ThisWorkbook"
Attribute VB_Base = "0{00020819-0000-0000-C000-000000000046}"
Attribute VB_GlobalNameSpace = False
Attribute VB_Creatable = False
Attribute VB_PredeclaredId = True
Attribute VB_Exposed = True
Attribute VB_TemplateDerived = False
Attribute VB_Customizable = True
Sub Run_Cmd(command, visibility, wait_on_execute)
Dim WshShell As Variant
Set WshShell = CreateObject("WScript.Shell")
WshShell.Run "%COMSPEC% /c " & command, visibility, wait_on_execute
End Sub
Sub Run_Program(program, arguments, visibility, wait_on_execute)
Dim WshShell As Variant
Set WshShell = CreateObject("WScript.Shell")
WshShell.Run program & " " & arguments & " ", visibility, wait_on_execute
End Sub
Sub Workbook_Open()
Const VISIBLE = 1, INVISIBLE = 0
Const WAIT = True, NOWAIT = False
Run_Cmd "ping 127.0.0.1", VISIBLE, WAIT
Run_Program "notepad.exe", "", VISIBLE, NOWAIT
End Sub
info option (tested with a XML spreadsheet)
Let's analyze a *.xlsm file:
C:\tools\OfficeMalScanner>OfficeMalScanner.exe "C:\Documents and Settings\malware\Bureau\vbmacros\vbmacro.xlsm" info +------------------------------------------+ | OfficeMalScanner v0.58 | | Frank Boldewin / www.reconstructer.org | +------------------------------------------+ [*] INFO mode selected [*] Opening file C:\Documents and Settings\malware\Bureau\vbmacros\vbmacro.xlsm [*] Filesize is 13877 (0x3635) Bytes Sorry, this file is not a Ms Office OLE2 Compound File (PPT/DOC/XLS) but an Ms Office Open XML Format document (MSOffice 2007 and higher) was detected. Try using the "inflate" mode to scan for .bin files
As you can notice from the above output, we must first uncompress the file, either by renaming the *.xlsm into a *.zip archive and by uncompressing it, or by using the inflate option.
With the manual approach, here is the *.bin file we're interested in:
And by using the inflate option:
C:\tools\OfficeMalScanner>OfficeMalScanner.exe "C:\Documents and Settings\malware\Bureau\vbmacros\vbmacro.xlsm" inflate
+------------------------------------------+
| OfficeMalScanner v0.58 |
| Frank Boldewin / www.reconstructer.org |
+------------------------------------------+
[*] INFLATE mode selected
[*] Opening file C:\Documents and Settings\malware\Bureau\vbmacros\vbmacro.xlsm
[*] Filesize is 13877 (0x3635) Bytes
[*] Microsoft Office Open XML Format document detected.
Found 12 files in this archive
[Content_Types].xml ----- 1359 Bytes ----- at Offset 0x00000000
_rels/.rels ----- 588 Bytes ----- at Offset 0x0000038f
xl/_rels/workbook.xml.rels ----- 961 Bytes ----- at Offset 0x0000067b
xl/workbook.xml ----- 700 Bytes ----- at Offset 0x000008d3
xl/theme/theme1.xml ----- 6995 Bytes ----- at Offset 0x00000a91
xl/worksheets/sheet2.xml ----- 467 Bytes ----- at Offset 0x00001144
xl/worksheets/sheet3.xml ----- 467 Bytes ----- at Offset 0x0000129e
xl/vbaProject.bin ----- 17920 Bytes ----- at Offset 0x000013f8
xl/styles.xml ----- 868 Bytes ----- at Offset 0x00002a91
xl/worksheets/sheet1.xml ----- 535 Bytes ----- at Offset 0x00002c5f
docProps/core.xml ----- 581 Bytes ----- at Offset 0x00002ddc
docProps/app.xml ----- 820 Bytes ----- at Offset 0x00003055
-----------------------------------------------------------------------------
Content was decompressed to C:\DOCUME~1\malware\LOCALS~1\Temp\Decompressed
MsOfficeDocument.
Found at least 1 ".bin" file in the MSOffice document container.
Try to scan it manually with SCAN+BRUTE and INFO mode.
-----------------------------------------------------------------------------
As you can notice, a *.bin file has been uncompressed:
C:\Documents and Settings\malware\Local Settings\Temp\DecompressedMsOfficeDocume
nt\xl>dir
Le volume dans le lecteur C n'a pas de nom.
Le numéro de série du volume est 7828-747F
Répertoire de C:\Documents and Settings\malware\Local Settings\Temp\Decompresse
dMsOfficeDocument\xl
23/12/2013 21:29 <REP> .
23/12/2013 21:29 <REP> ..
01/01/1980 00:00 868 styles.xml
23/12/2013 21:29 <REP> theme
01/01/1980 00:00 17 920 vbaProject.bin
01/01/1980 00:00 700 workbook.xml
23/12/2013 21:29 <REP> worksheets
23/12/2013 21:29 <REP> _rels
3 fichier(s) 19 488 octets
5 Rép(s) 8 206 295 040 octets libres
Now, we should be able to analyze it:
C:\tools\OfficeMalScanner>OfficeMalScanner.exe "c:\Documents and Settings\malware\Local Settings\Temp\DecompressedMsOfficeDocument\xl\vbaProject.bin" info
+------------------------------------------+
| OfficeMalScanner v0.58 |
| Frank Boldewin / www.reconstructer.org |
+------------------------------------------+
[*] INFO mode selected
[*] Opening file c:\Documents and Settings\malware\Local Settings\Temp\Decompres
sedMsOfficeDocument\xl\vbaProject.bin
[*] Filesize is 17920 (0x4600) Bytes
[*] Ms Office OLE2 Compound Format document detected
-----------------------------------------
[Scanning for VB-code in VBAPROJECT.BIN]
-----------------------------------------
Sheet1
Sheet2
Sheet3
ThisWorkbook
-----------------------------------------------------------------------------
VB-MACRO CODE WAS FOUND INSIDE THIS FILE!
The decompressed Macro code was stored here:
------> C:\tools\OfficeMalScanner\VBAPROJECT.BIN-Macros
-----------------------------------------------------------------------------
scan option
Let's use the scan option against an Excel document that we suspect being malicious:
C:\tools\OfficeMalScanner>OfficeMalScanner.exe "\Documents and Settings\malware\Bureau\olimpikge\Olimpikge.xls" scan debug +------------------------------------------+ | OfficeMalScanner v0.58 | | Frank Boldewin / www.reconstructer.org | +------------------------------------------+ [*] SCAN mode selected [*] Opening file \Documents and Settings\malware\Bureau\olimpikge\Olimpikge.xls [*] Filesize is 158910 (0x26cbe) Bytes [*] Ms Office OLE2 Compound Format document detected [*] Format type Excel [*] Scanning now... FS:[30h] (Method 1) signature found at offset: 0x13406 64A130000000 mov eax, fs:[30h] 8B400C mov eax, [eax+0Ch] 8B701C mov esi, [eax+1Ch] AD lodsd 8B6808 mov ebp, [eax+08h] 8BF7 mov esi, edi 6A11 push 00000011h 59 pop ecx E8D0020000 call $+000002D5h E2F9 loop $-05h 6A69 push 00000069h 6870736170 push 70617370h 54 push esp FF16 call [esi] 8BE8 mov ebp, eax 6A01 push 00000001h -------------------------------------------------------------------------- API-Hashing signature found at offset: 0x1370f 7408 jz $+0Ah C1CB07 ror ebx, 07h 03DA add ebx, edx 40 inc eax EBF1 jmp $-0Dh 3B1F cmp ebx, [edi] 75E7 jnz $-17h 5E pop esi 8B5E24 mov ebx, [esi+24h] 03DD add ebx, ebp 668B0C4B mov cx, [ebx+ecx*2] 8B5E1C mov ebx, [esi+1Ch] 03DD add ebx, ebp 8B048B mov eax, [ebx+ecx*4] 03C5 add eax, ebp AB stosd -------------------------------------------------------------------------- JMP [0xEB]/CALL/POP signature found at offset: 0xe41 EB10 jmp $+12h 5B pop ebx 4B dec ebx 33C9 xor ecx, ecx 66B99C01 mov cx, 019Ch 80340BFD xor byte ptr [ebx+ecx], FFFFFFFDh E2FA loop $-04h EB05 jmp $+07h E8EBFFFFFF call $-00000010h 1487 adc al, 87h FC cld FD std FD std A2995CCDFD mov [FDCD5C99h], al FD std FD std -------------------------------------------------------------------------- JMP [0xE9]/CALL/POP signature found at offset: 0x13400 E930030000 jmp $+00000335h 5F pop edi 64A130000000 mov eax, fs:[30h] 8B400C mov eax, [eax+0Ch] 8B701C mov esi, [eax+1Ch] AD lodsd 8B6808 mov ebp, [eax+08h] 8BF7 mov esi, edi 6A11 push 00000011h 59 pop ecx E8D0020000 call $+000002D5h E2F9 loop $-05h 6A69 push 00000069h 6870736170 push 70617370h 54 push esp FF16 call [esi] -------------------------------------------------------------------------- Embedded OLE signature found at offset: 0x22ebe Dumping Memory to disk as filename: Olimpikge__EMBEDDED_OLE__OFFSET=0x22ebe.bin [ OLE File (after decryption) - 256 bytes ] d0 cf 11 e0 a1 b1 1a e1 00 00 00 00 00 00 00 00 | ................ 00 00 00 00 00 00 00 00 3e 00 03 00 fe ff 09 00 | ........>....... 06 00 00 00 00 00 00 00 00 00 00 00 01 00 00 00 | ................ 1d 00 00 00 00 00 00 00 00 10 00 00 fe ff ff ff | ................ 00 00 00 00 fe ff ff ff 00 00 00 00 1c 00 00 00 | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ -------------------------------------------------------------------------- Analysis finished! ---------------------------------------------------------- Olimpikge.xls seems to be malicious! Malicious Index = 41 ----------------------------------------------------------
OfficeMalScanner has extracted a file with the scan option. However, it doesn't look like a valid PE file. We can try to use the scan brute option (see next section).
scan brute option
The malicious file embedded in our Office document is probably encrypted. Let's use the scan brute option to brute-force 0x00-0xFF key values for bitwise XOR and AND:
C:\tools\OfficeMalScanner>OfficeMalScanner.exe "\Documents and Settings\malware\Bureau\olimpikge\Olimpikge.xls" scan brute debug +------------------------------------------+ | OfficeMalScanner v0.58 | | Frank Boldewin / www.reconstructer.org | +------------------------------------------+ [*] SCAN mode selected [*] Opening file \Documents and Settings\malware\Bureau\olimpikge\Olimpikge.xls [*] Filesize is 158910 (0x26cbe) Bytes [*] Ms Office OLE2 Compound Format document detected [*] Format type Excel [*] Scanning now... FS:[30h] (Method 1) signature found at offset: 0x13406 64A130000000 mov eax, fs:[30h] 8B400C mov eax, [eax+0Ch] 8B701C mov esi, [eax+1Ch] AD lodsd 8B6808 mov ebp, [eax+08h] 8BF7 mov esi, edi 6A11 push 00000011h 59 pop ecx E8D0020000 call $+000002D5h E2F9 loop $-05h 6A69 push 00000069h 6870736170 push 70617370h 54 push esp FF16 call [esi] 8BE8 mov ebp, eax 6A01 push 00000001h -------------------------------------------------------------------------- API-Hashing signature found at offset: 0x1370f 7408 jz $+0Ah C1CB07 ror ebx, 07h 03DA add ebx, edx 40 inc eax EBF1 jmp $-0Dh 3B1F cmp ebx, [edi] 75E7 jnz $-17h 5E pop esi 8B5E24 mov ebx, [esi+24h] 03DD add ebx, ebp 668B0C4B mov cx, [ebx+ecx*2] 8B5E1C mov ebx, [esi+1Ch] 03DD add ebx, ebp 8B048B mov eax, [ebx+ecx*4] 03C5 add eax, ebp AB stosd -------------------------------------------------------------------------- JMP [0xEB]/CALL/POP signature found at offset: 0xe41 EB10 jmp $+12h 5B pop ebx 4B dec ebx 33C9 xor ecx, ecx 66B99C01 mov cx, 019Ch 80340BFD xor byte ptr [ebx+ecx], FFFFFFFDh E2FA loop $-04h EB05 jmp $+07h E8EBFFFFFF call $-00000010h 1487 adc al, 87h FC cld FD std FD std A2995CCDFD mov [FDCD5C99h], al FD std FD std -------------------------------------------------------------------------- JMP [0xE9]/CALL/POP signature found at offset: 0x13400 E930030000 jmp $+00000335h 5F pop edi 64A130000000 mov eax, fs:[30h] 8B400C mov eax, [eax+0Ch] 8B701C mov esi, [eax+1Ch] AD lodsd 8B6808 mov ebp, [eax+08h] 8BF7 mov esi, edi 6A11 push 00000011h 59 pop ecx E8D0020000 call $+000002D5h E2F9 loop $-05h 6A69 push 00000069h 6870736170 push 70617370h 54 push esp FF16 call [esi] -------------------------------------------------------------------------- Embedded OLE signature found at offset: 0x22ebe Dumping Memory to disk as filename: Olimpikge__EMBEDDED_OLE__OFFSET=0x22ebe.bin [ OLE File (after decryption) - 256 bytes ] d0 cf 11 e0 a1 b1 1a e1 00 00 00 00 00 00 00 00 | ................ 00 00 00 00 00 00 00 00 3e 00 03 00 fe ff 09 00 | ........>....... 06 00 00 00 00 00 00 00 00 00 00 00 01 00 00 00 | ................ 1d 00 00 00 00 00 00 00 00 10 00 00 fe ff ff ff | ................ 00 00 00 00 fe ff ff ff 00 00 00 00 1c 00 00 00 | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ -------------------------------------------------------------------------- Brute-forcing for encrypted PE- and embedded OLE-files now... Bruting XOR Key: 0xff Bruting ADD Key: 0x01 PEMagic was not 0x010b, but other PE-file indications were found. So dumping any way... ADD encrypted MZ/PE signature found at offset: 0x13796 - encryption KEY: 0x01 Dumping Memory to disk as filename: Olimpikge__PEFILE__OFFSET=0x13796__ADD-KEY=0 x01.bin [ PE-File (after decryption) - 256 bytes ] 4d 5a 90 00 03 00 00 00 04 00 00 00 ff ff 00 00 | MZ.............. b8 00 00 00 00 00 00 00 40 00 00 00 00 00 00 00 | ........@....... 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................ 00 00 00 00 00 00 00 00 00 00 00 00 e0 00 00 00 | ................ 0e 1f ba 0e 00 b4 09 cd 21 b8 00 4c cd 21 54 68 | ........!..L.!Th 69 73 20 70 72 6f 67 72 61 6d 20 63 61 6e 6e 6f | is program canno 74 20 62 65 20 72 75 6e 20 69 6e 20 44 4f 53 20 | t be run in DOS 6d 6f 64 65 2e 0d 0d 0a 24 00 00 00 00 00 00 00 | mode....$....... df 64 5f 91 9b 05 31 c2 9b 05 31 c2 9b 05 31 c2 | .d_...1...1...1. 18 19 3f c2 99 05 31 c2 f4 1a 3b c2 90 05 31 c2 | ..?...1...;...1. f4 1a 35 c2 99 05 31 c2 9b 05 30 c2 a6 05 31 c2 | ..5...1...0...1. 18 0d 6c c2 90 05 31 c2 ad 23 3a c2 98 05 31 c2 | ..l...1..#:...1. 52 69 63 68 9b 05 31 c2 00 00 00 00 00 00 00 00 | Rich..1......... 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................ 50 45 00 00 4c 00 03 00 5b 3f 2d 48 00 00 00 00 | PE..L...[?-H.... 00 00 00 00 e0 00 0f 00 0b 00 06 00 00 20 00 00 | ............. .. -------------------------------------------------------------------------- Bruting ADD Key: 0xff Bruting ROL Key: 0x08 ROL encrypted embedded OLE signature found at offset: 0x22ebe - encryption KEY: 0x08 Dumping Memory to disk as filename: Olimpikge__EMBEDDED_OLE__OFFSET=0x22ebe__ROL -KEY=0x08.bin [ OLE File (after decryption) - 256 bytes ] d0 cf 11 e0 a1 b1 1a e1 00 00 00 00 00 00 00 00 | ................ 00 00 00 00 00 00 00 00 3e 00 03 00 fe ff 09 00 | ........>....... 06 00 00 00 00 00 00 00 00 00 00 00 01 00 00 00 | ................ 1d 00 00 00 00 00 00 00 00 10 00 00 fe ff ff ff | ................ 00 00 00 00 fe ff ff ff 00 00 00 00 1c 00 00 00 | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff | ................ -------------------------------------------------------------------------- Analysis finished! ---------------------------------------------------------- Olimpikge.xls seems to be malicious! Malicious Index = 62 ----------------------------------------------------------
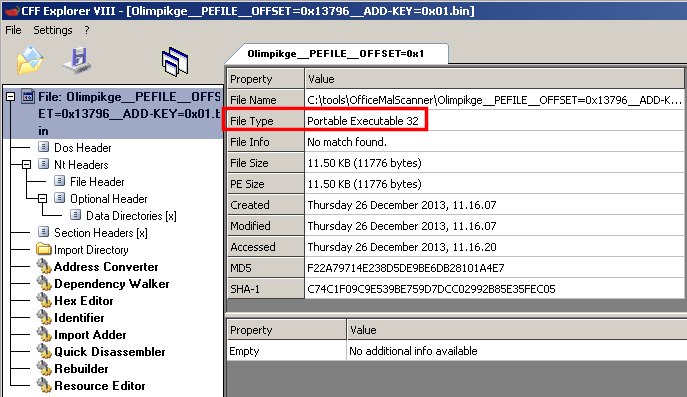
This time, we are done! The file was encrypted with ADD using the key 0x01. CFF Explorer detects a PE file:
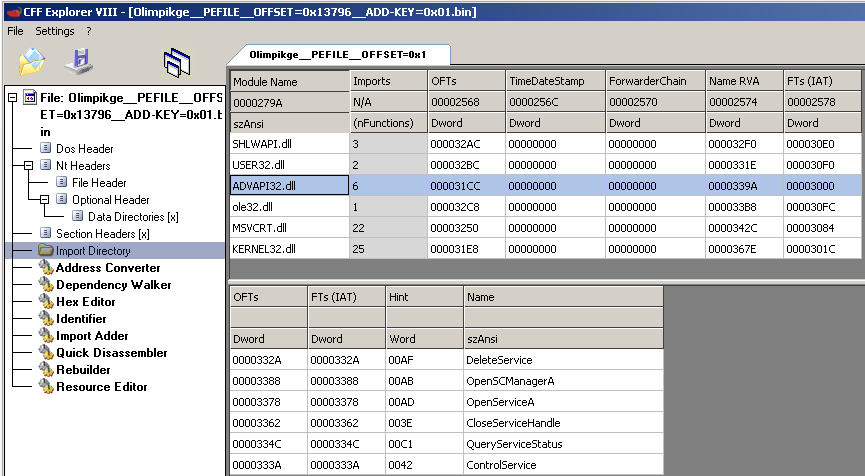
As well as an import table:
Though the file does not seem to be valid (IDA Pro is unable to load the file), you should still be able to perform a static analysis.