Thc-hydra
Jump to navigation
Jump to search

This article is also available in one or more other languages
To view this article in French, click here

Description
THC-Hydra is a very fast (multi-threaded) network logon cracker which supports many different services:
|
|
|
|
Installation
Dependencies
| Name | Lib | Package |
|---|---|---|
| Xhydra (GUI) | sudo apt-get install pkg-config libgtk2.0-dev | |
| Openssl | libssl/ssl.h | sudo apt-get install libssl-dev |
| Postgres | libpq.so | sudo apt-get install libpq-dev |
| SVN (Subversion) | libsvn_client-1, libapr-1.so, libaprutil-1.so | sudo apt-get install libsvn-dev libapr1-dev libaprutil1-dev |
| firebird | libfbclient.so | sudo apt-get install firebird2.1-dev |
| MySQL client | libmysqlclient.so | sudo apt-get install libmysqlclient-dev |
| AFP | libafpclient.so | N/A |
| NCP | libncp.so, nwcalls.h | sudo apt-get install libncp-dev |
| SAP/R3 | librfc/saprfc.h | (See http://www.sdn.sap.com/irj/sdn/linux) |
| libssh | libssh/libssh.h | sudo apt-get install libssh-dev |
Install Hydra
$ cd /data/src/ $ wget http://freeworld.thc.org/releases/hydra-5.9-src.tar.gz $ tar xzvf hydra-5.9-src.tar.gz $ cd hydra-5.9-src/ $ ./configure $ make $ sudo make install
Usage
Command Line Interface (CLI)
Syntax
$ hydra [[[-l LOGIN|-L FILE] [-p PASS|-P FILE]] | [-C FILE]] [-e ns] [-o FILE] [-t TASKS] [-M FILE [-T TASKS]] [-w TIME] [-f] [-s PORT] [-S] [-vV] server service [OPT]
Options
- -R
- restore a previous aborted/crashed session
- -S
- connect via SSL
- -s <PORT>
- if the service is on a different default port, define it here
- -l <LOGIN> or -L <FILE>
- login with LOGIN name, or load several logins from FILE
- -p <PASS> or -P <FILE>
- try password PASS, or load several passwords from FILE
- -e <ns>
- additional checks, "n" for null password, "s" try login as pass
- -C <FILE>
- colon seperated "login:pass" format, instead of -L/-P options
- -M <FILE>
- server list for parallel attacks, one entry per line
- -o <FILE>
- write found login/password pairs to FILE instead of stdout
- -f
- exit after the first found login/password pair (per host if -M)
- -t <TASKS>
- run TASKS number of connects in parallel (default: 16)
- -w
- defines the max wait time in seconds for responses (default: 30)
- -v / -V
- verbose mode / show login+pass combination for each attempt
- server
- the target server (use either this OR the -M option)
- service
- the service to crack. Supported protocols: telnet ftp pop3[-ntlm] imap[-ntlm] smb smbnt http[s]-{head|get} http-{get|post}-form http-proxy cisco cisco-enable vnc ldap2 ldap3 mssql mysql oracle-listener postgres nntp socks5 rexec rlogin pcnfs snmp rsh cvs svn icq sapr3 ssh2 smtp-auth[-ntlm] pcanywhere teamspeak sip vmauthd firebird ncp afp
- OPT
- some service modules need special input (see README!)
Graphical User Interface (GUI)
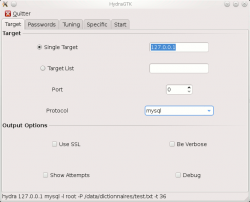
Target
|
This tab enables to specify the target and the protocol to attack.
|
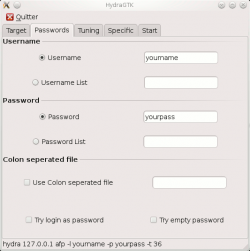
Passwords
|
This tab enables to specify the credentials to use for the brute-force attack.
|

Note
If you select both options "Username List" and "Password List", xhydra will try every combination of logins/passwords from specified files.
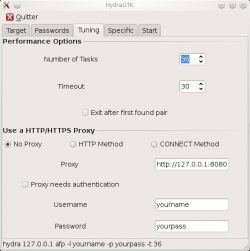
Tuning
|
This tab enables to fine-tune the brute-force attack.
|

Note
Notice that xhydra will automatically reduce the number of threads if needed (depends on the attacked service)
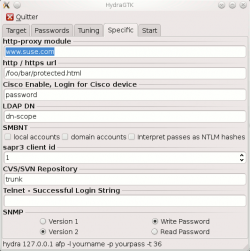
Specific
|
Some services need specific options. This tab enables to specify these options.
|
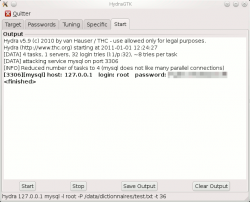
Start
|
This tab shows outputs of xhydra (attempts, successful credentials, verbose and debug information). It also controls the tool (start, stop, save, clear output).
|
Example
The following is an example of hydra run against a local MySQL database, on the root account:
$ hydra 127.0.0.1 mysql -l root -P /data/dictionnaires/test.txt -t 4 Hydra v5.9 (c) 2010 by van Hauser / THC - use allowed only for legal purposes. Hydra (http://www.thc.org) starting at 2011-01-01 13:01:15 [DATA] 4 tasks, 1 servers, 32 login tries (l:1/p:32), ~8 tries per task [DATA] attacking service mysql on port 3306 [3306][mysql] host: 127.0.0.1 login: root password: Password01 [STATUS] attack finished for 127.0.0.1 (waiting for childs to finish) Hydra (http://www.thc.org) finished at 2011-01-01 13:01:15