WackoPicko/Directory-Traversal
| You are here: | Directory Traversal
|
Description
A directory traversal (or path traversal) attack is the art of exploiting insufficient security validation/sanitization of user-supplied input file names, so that characters representing "traverse to parent directory" ("../" or "..\") are passed through to the URL.
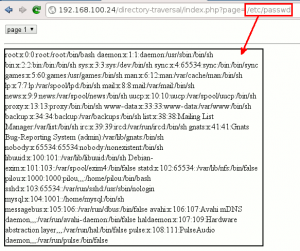
This attack enables one to access files that were not initially intended to be accessible by the application. A very common target is the famous "/etc/passwd file" that provides the attacker with login names, and eventually passwords hashes.
Proof of Concept
WackoPicko
WackoPicko suffers from a directory-traversal vulnerability. As you can see in the following portion of code from /pictures/upload.php, there is no proper sanitization of the $_POST["tag"] user input:
$_POST['name'] = str_replace("..", "", $_POST['name']);
$_POST['name'] = str_replace(" ", "", $_POST['name']);
$_POST['name'] = str_replace("/", "", $_POST['name']);
if (!file_exists("../upload/{$_POST['tag']}/"))
{
mkdir("../upload/{$_POST['tag']}", 0777, True);
}
$filename = "../upload/{$_POST['tag']}/{$_POST['name']}";
$relfilename = "{$_POST['tag']}/{$_POST['name']}";
It can enable a malicious users to overwrite any file the web server uses has access to.
Other example
In the example below (you can download the PoC here: http://dl.dropbox.com/u/10761700/poc-directory-traversal.tar.gz), the standard use is to select a file from the dropdown list to display it on the frame below.
This application is vulnerable to a directory traversal attack because:
- the limitation is only applied on the client side (the dropdown list values could be very easily bypassed by tampering the content of the request)
- inputs are not properly validated on the server's side (no whitelist of values).
How to detect?
How to protect against it?
- Don't consider these as secure approaches:
- Concatenate an extension to limit file types (e.g. {$_GET['page']}.txt). This could be bypassed with a NULL byte (%00) at the end of the url. For more information, refer to the examples section.
- Don't use string patterns such as "../" or "..\" to validate the inputs. Indeed, they could be bypassed by encoding them (URI encodings such as %3e%3e%3f).
- Don't consider file limitations via client-side controls (dropdown lists, JavaScript controls, ...) because they can be easily bypassed by tampering the request.
- These approaches are better:
- chroot (jail) your server installation (e.g. Apache jail)
- Don't directly process $_GET and $_POST variables. Challenge them against whitelists (e.g. with switch, case, ...). Ignore values out of this whitelist.