WackoPicko/SessionID-vulnerability
| You are here: | SessionID vulnerability
|
Description
The session information associated with administrative accounts is handled differently than the information associated with the sessions of normal users.
The functionality associated with normal users uses PHP’s session handling capabilities, which is assumed to be free of any session-related vulnerabilities (e.g. session fixation, easily-guessable session IDs).
However the admin section uses a custom session cookie to keep track of sessions. The value used in the cookie is a non-random value that is incremented when a new session is created. Therefore, an attacker can easily guess the session id and access the application with administrative rights.
Proof of Concept
Description
To analyze the distribution of SessionIDs generated for the administration login, we use WebScarab. We will demonstrate that the distribution of SessionIDs is incremental and hence predictable.
In addition, the comparison of 2 server responses (administration and standard user authentication forms) will show the differences between cookies types.
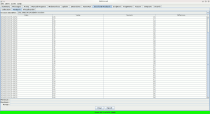
WebScarab
A sessionID analysis in WebScarab enables to easily demonstrate that the session ID (session=x) has an incremental distribution over time:
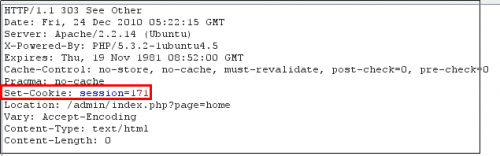
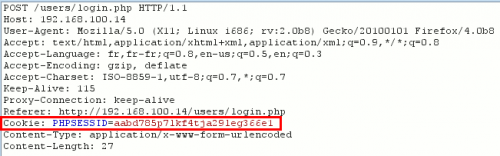
Cookies
These 2 responses from the server show the differences of cookies implementations used between the administration and the standard user authentication mechanisms.
How to detect?
How to protect against it?
Such predictable sessionIDs often come from specifics implemented by the developer. Rather prefer native cookie generation than a specific implementation that could lead to weak and guessable mechanisms.