Category:Encryption
Description
- Malware often encrypt content (strings, content sent to C&C)
- A reversible cipher uses the same function to encode and decode
Online resources
- Cipher list and tools
- https://gist.github.com/tigertv/cd9ab0563c5012a36978cf0abfd34948
- Encoding/decoding tools
- https://gchq.github.io/CyberChef/
- https://cryptii.com/
- https://www.dcode.fr/
- https://paulschou.com/tools/xlate/
- https://www.guballa.de/vigenere-solver (able to brute force Vigenere key)
- https://quipqiup.com/ (able to brute force key)
- http://kripto.rf.gd/ (Enigmator)
- http://www.webutils.pl/index.php?idx=xx
- Hash crackers
- https://md5decrypt.net/
- https://md5hashing.net/
- Cipher identifier
- https://www.boxentriq.com/code-breaking/cipher-identifier
Detecting cryptography in malware
Strings and Imports
- Presence of typical strings (e.g. "OpenSSL 1.0.0a", "SSLv3 part of OpenSSL 1.0.0a", ...)
- Presence of typical imports (e.g. CryptAcquireContext, CryptCreateHash, ...)
Constants
- Using FindCrypt2 in IDA-Pro
- Using Krypto ANALyzer in PEiD
Entropy
Some algorithm can't be detected from constants because they build their structures on the fly. This is the case for the International Data Encryption Algorithm (IDEA) and the RC4 algorithms.
You can search for high-entropy content to detect such algorithms using IDA Entropy Plugin:
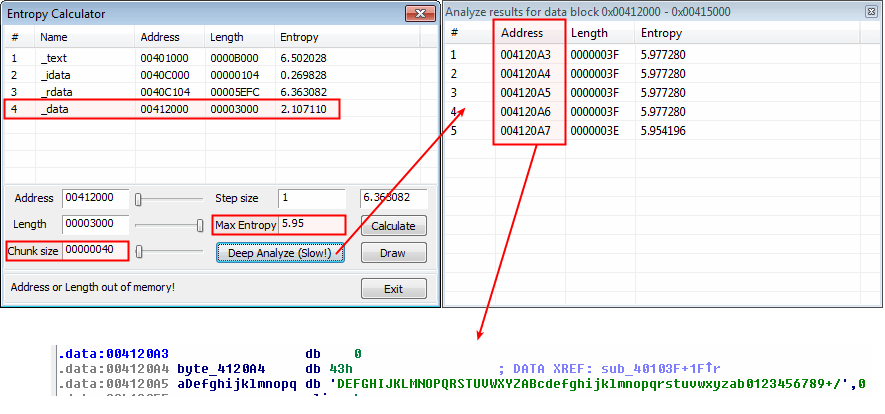
- Revealing base64 encoding with high 6-bit entropy in the data section (64-bit (0x40) chunk size with maximum entropy of 5.95)
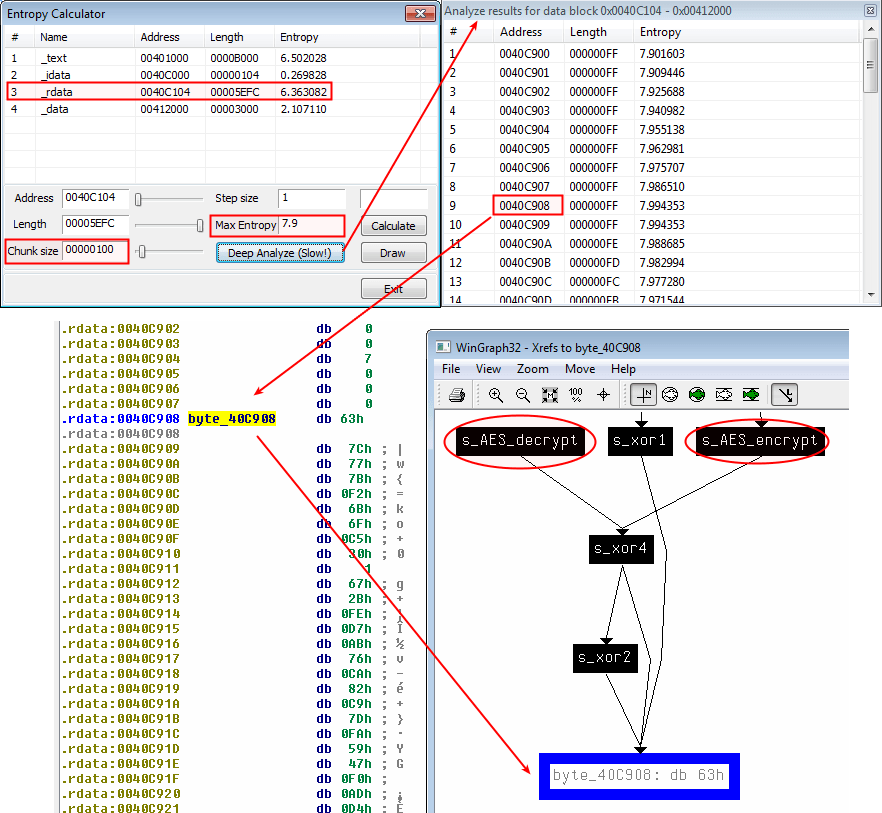
- Revealing AES encryption with high 8-bit entropy in the rdata section (256-bit (0x100) chunk size with maximum entropy of 7.9)
Decryption in practice
Basic decryption

Thank you for your comprehension.
Complex decryption
With OllyDbg
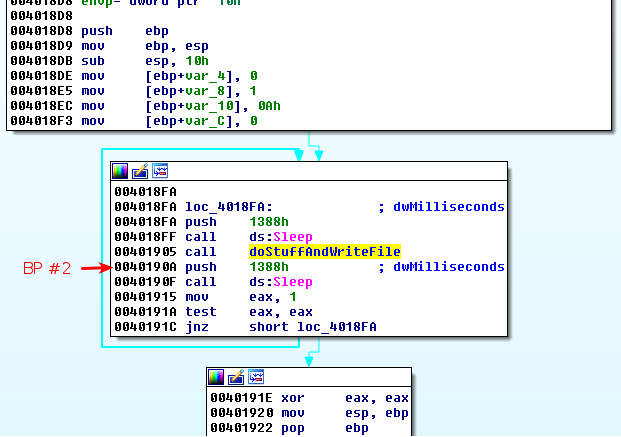
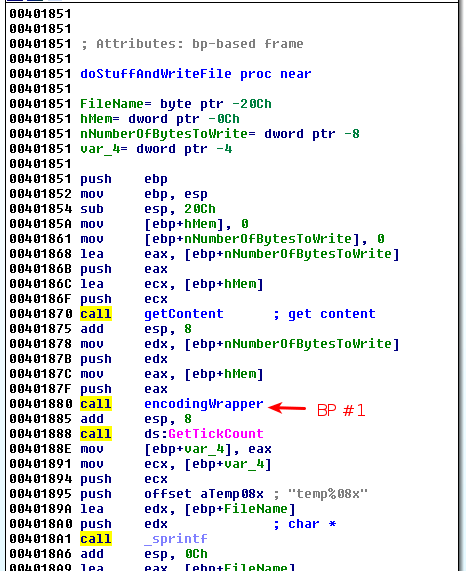
Suppose we are analyzing a malware that encrypts an image file (a bmp file) using a complex encryption mechanism and that the encryption routine is reversible (same routine to encrypt and decrypt). We can use modify the flow in the malware to decrypt encrypted content. Below is an example.
|
|
Let's setup 2 breakpoints in OllyDbg:
- At offset 0x401880, just before the content is encrypted
- At offset 0x40190A, just after the file is written
Once the program has reached our first breakpoint (0x401880), the arguments on the stack represent the buffer that is about to be encrypted:
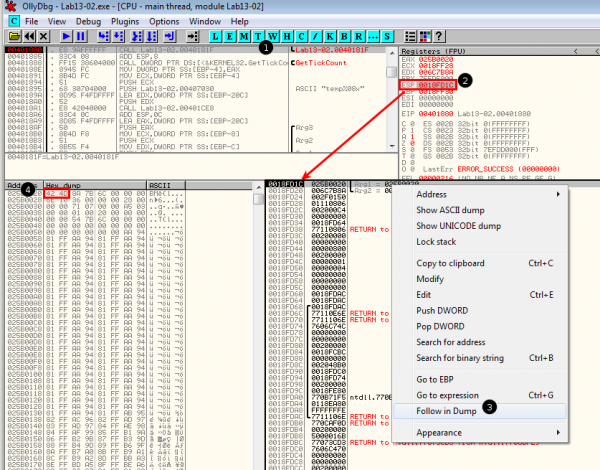
|
|
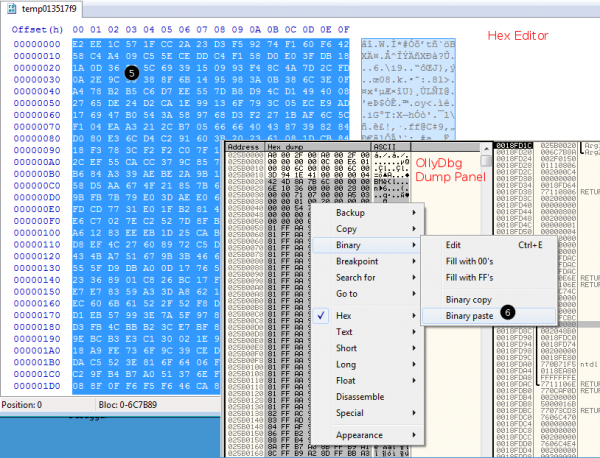
|
|
With python scripting in Immunity Debugger

Thank you for your comprehension.
Encypting volumes
Bitlocker
See here.
TrueCrypt

Thank you for your comprehension.
LUKS
What is LUKS?
LUKS (Linux Unified Key Setup) is the standard for Linux hard disk encryption. By providing a standard on-disk-format, it does not only facilitate compatibility among distributions, but also provides secure management of multiple user passwords. In contrast to existing solution, LUKS stores all setup necessary setup information in the partition header, enabling the user to transport or migrate his data seamlessly.
cryptsetup is the tool to use to mount LUKS volumes.
Find key in memory dump
You can find a LUKS key in a memory dump using aeskeyfind:
$ wget https://github.com/TeamCTF-PRIME/auto_vol/raw/master/aeskeyfind $ ./aeskeyfind memory.raw 8d3f527****************58dbc0ed1 $ echo "8d3f527****************58dbc0ed1" | xxd -r -p > key.bin
Mount LUKS volume
$ sudo apt install cryptsetup $ sudo modprobe dm-crypt $ mkdir /data/tmp/vol/ $ sudo cryptsetup open --type luks --master-key-file=key.bin forensic.img luks_vol
It will create a device /dev/mapper/luks_vola that we can now mount:
$ sudo mount /dev/mapper/luks_vola /data/tmp/vol/
Comments
Keywords: caesar crypto encryption base64 decode encode
Pages in this category
Subcategories
This category has the following 11 subcategories, out of 11 total.
E
- Encryption/RSA (4)
- Encryption/XOR (12)
Pages in category "Encryption"
The following 20 pages are in this category, out of 20 total.