48e29119b03641499492336695c29ffd
Jump to navigation
Jump to search
Description
- SHA256: 66a296fb5c388db8005c850f6c14fcfc36447bdc24a142ed4f6153d260846845
- SHA1: 7c0eff63cdea6ea46f2a89f24e6f62e859e5e819
- MD5: 48e29119b03641499492336695c29ffd
- File size: 92.5 KB ( 94720 bytes )
- File type: Win32 EXE
- Location: C:\System Volume Information\_restore{513E13D9-9DEA-495E-B9CA-81E5CC08F4FD}\RP282\A0279980.com
- File name: A0279980.com
PE Signature:
- Copyright: Copyright Mamuze© 2013
- Publisher: House
- Product: Sunce
- Version: 3, 0, 0, 0
- Original name: Voda.exe
- Internal name: Travka
- File version: 1, 3, 4, 7
- Description: Marko
- Comments: Praslin
Detection
Antivirus detection
Detection ratio: 42/48 (2013-10-01)
| Antivirus | Result | Update |
|---|---|---|
| Agnitum | Trojan.DL.Andromeda!OVR9prejAzY | 20130930 |
| AhnLab-V3 | Spyware/Win32.Zbot | 20130930 |
| AntiVir | TR/Dldr.Andromeda.tze | 20131001 |
| Antiy-AVL | Trojan/Win32.Generic | 20131001 |
| Avast | Win32:Downloader-SYZ [Trj] | 20131001 |
| AVG | SHeur4.BFHZ | 20131001 |
| Baidu-International | Trojan.Win32.Agent.40 | 20131001 |
| BitDefender | Trojan.Generic.KDV.927010 | 20131001 |
| Bkav | W32.GamarueSymmiA.Trojan | 20130927 |
| CAT-QuickHeal | Worm.Gamarue.B | 20131001 |
| Commtouch | W32/Backdoor.LOGQ-7581 | 20131001 |
| Comodo | TrojWare.Win32.Injector.AFHI | 20131001 |
| DrWeb | BackDoor.Andromeda.22 | 20131001 |
| Emsisoft | Trojan.Generic.KDV.927010 (B) | 20131001 |
| ESET-NOD32 | a variant of Win32/Injector.AEYF | 20131001 |
| F-Secure | Trojan.Generic.KDV.927010 | 20131001 |
| Fortinet | W32/Injector.AFHI!tr | 20131001 |
| GData | Trojan.Generic.KDV.927010 | 20131001 |
| Ikarus | Worm.Win32.Gamarue | 20131001 |
| K7AntiVirus | Riskware | 20130930 |
| K7GW | Riskware | 20130930 |
| Kaspersky | Trojan-Downloader.Win32.Andromeda.tze | 20131001 |
| Kingsoft | Win32.Troj.Undef.(kcloud) | 20130829 |
| Malwarebytes | Trojan.Bot.RV | 20131001 |
| McAfee | RDN/Generic Downloader.x!di | 20131001 |
| McAfee-GW-Edition | RDN/Generic Downloader.x!di | 20131001 |
| Microsoft | Worm:Win32/Gamarue.I | 20131001 |
| MicroWorld-eScan | Trojan.Generic.KDV.927010 | 20131001 |
| Norman | Injector.FGGB | 20131001 |
| nProtect | Trojan-Downloader/W32.Andromeda.94720 | 20131001 |
| Panda | Trj/OCJ.D | 20131001 |
| PCTools | Trojan.Fakeavlock | 20131001 |
| Rising | Trojan.Win32.Generic.148E617B | 20130930 |
| Sophos | Troj/Bckdr-RPN | 20131001 |
| SUPERAntiSpyware | Trojan.Agent/Gen-Dropper | 20131001 |
| Symantec | Trojan.Fakeavlock | 20131001 |
| TheHacker | Trojan/Injector.aeyf | 20130930 |
| TrendMicro | TROJ_SPNR.0BDA13 | 20131001 |
| TrendMicro-HouseCall | TROJ_SPNR.0BDA13 | 20131001 |
| VBA32 | BScope.Trojan.MSA.5417 | 20131001 |
| VIPRE | Trojan.Win32.Generic!BT | 20131001 |
| ViRobot | Trojan.Win32.S.Zbot.94720 | 20131001 |
Network indicators
SIEM
POST /in.php HTTP/1.1 Host: orzdwjtvmein.in User-Agent: Mozilla/4.0 Content-Type: application/x-www-form-urlencoded Content-Length: 72 Connection: close upqchC83slHHEu1nnIKGIwiLrHo3Vt68T3yqvhQu2TqetQn3qIy7Q6bpTfDUtYFR593/MQ==
Network connections
| IP | Domain |
|---|---|
| 65.55.184.26 | www.update.microsoft.com |
| 195.22.26.231 | xdqzpbcgrvkj.ru |
| 195.22.26.231 | anam0rph.su |
| 195.22.26.231 | orzdwjtvmein.in |
| 195.22.26.231 | ygiudewsqhct.in |
| 195.22.26.231 | bdcrqgonzmwuehky.nl |
| 109.236.84.12 | somicrososoft.ru |
| 95.211.98.157 | |
| 65.55.184.155 | |
| 8.8.4.4 | |
| 195.22.26.231 | |
| 109.236.84.12 |
Backdoor feature
It seems that the svchost.exe process that is dropped by the malware opens a socket on port 8000/tcp.
C:\>netstat -anb [SNIP] TCP 0.0.0.0:8000 0.0.0.0:0 LISTENING 52804 C:\WINDOWS\system32\ws2_32.dll -- composants inconnus -- C:\Documents and Settings\All Users\svchost.exe C:\WINDOWS\system32\kernel32.sll [svchost.exe]
Host based indicators
Files

INCOMPLETE SECTION OR ARTICLE
This section/article is being written and is therefore not complete.
Thank you for your comprehension.
Thank you for your comprehension.
Registry
Following registry key has been modified:
- Registry key path: HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\SunJavaUpdateSched
- Old value: C:\Program Files\Fichiers communs\Java\Java Update\jusched.exe
- New value: C:\Documents and Settings\All Users\svchost.exe
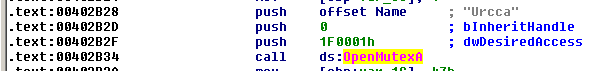
Mutex
A mutex called "Urcca" is created:
Analysis
Imports
- KERNEL32.dll
- LoadLibraryA
- OpenMutexA
- SizeofResource
- GetModuleHandleA
- LoadResource
- GetProcAddress
- FindResourceA
- CloseHandle
- GetCurrentProcessId
- WaitForSingleObject
- CreateThread
- GetFileSize
- ADVAPI32.dll
- RegCloseKey
Malware Dropper architecture
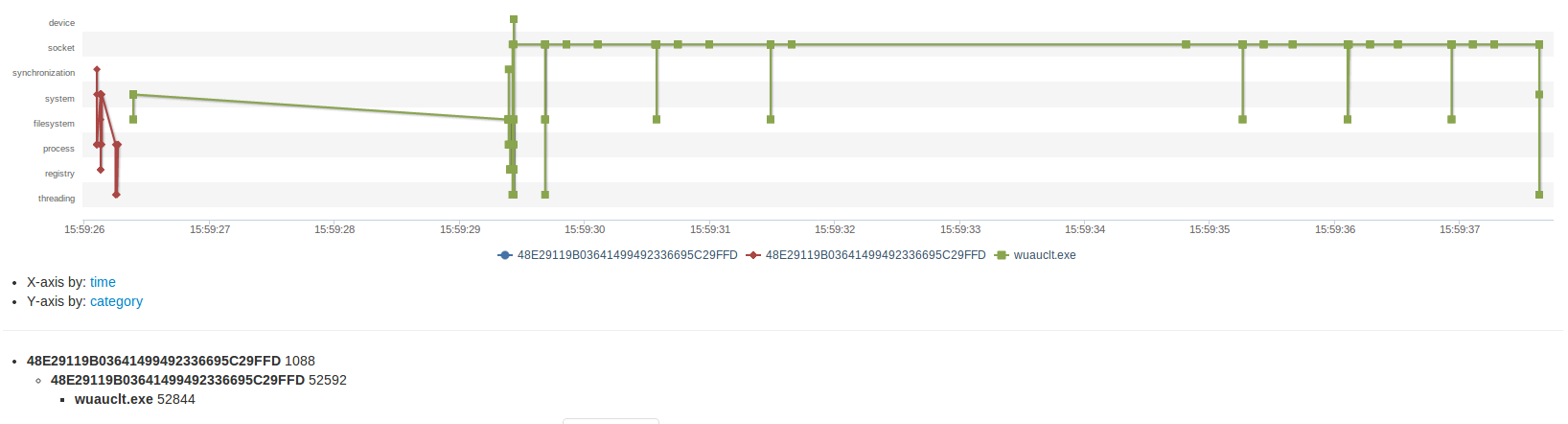
This malware is a dropper. Indeed, as depicted on the below picture, we can see that socket features are only activated by the wuauclt.exe which is dropped by the initial malware.
Remediation
Following tools have been confirmed to be able to detect/clean the infection:
Links
- Download: https://www.dropbox.com/s/mfrwf529cqk0uos/48e29119b03641499492336695c29ffd.zip (pass: infected)
- VirusTotal: https://www.virustotal.com/en/file/66a296fb5c388db8005c850f6c14fcfc36447bdc24a142ed4f6153d260846845/analysis/1380624308/
- Malwr: https://malwr.com/analysis/OWZhYTc3NWFjNGVkNDFmN2IzYjAxZTMzZGRkNWZmY2Q/