Autopsy
Description
Autopsy is an open source digital forensics platform that analyzes hard drives, smart phones, media cards, etc.
Installation (Autopsy 4.15.0)
Single vs multi user
2 installations types are possible:
- Desktop/Single-user: SQLite database
- Cluster/Multiple-users: PostgreSQL
This tutorial only covers the first type of installation.
Windows
- Download link: https://github.com/sleuthkit/autopsy/releases/download/autopsy-4.15.0/autopsy-4.15.0-64bit.msi
Linux/Mac OS X
Prerequisites
Detailed installation: http://myjourneyintech.com/dfir/autopsy/infosec/2018/06/11/Install-Autopsy.html
$ sudo dnf install testdisk sleuthkit sqlite-jdbc
Install the sleuthkit-java version: https://github.com/sleuthkit/sleuthkit/releases/download/sleuthkit-4.9.0/sleuthkit-java_4.9.0-1_amd64.deb.
Java. Also set the JAVA_HOME environment variable (e.g. add export JAVA_HOME=/usr/java/jdk-x64/ to your ~/.bashrc file)
Autopsy
- Download the Autopsy ZIP file
Cases and Data Sources structure
Cases and data sources
Autopsy investigations are cases. Within a case, you can add the following data sources:
- Disk images or VM files (e.g. E01, raw dd, raw Android image, vmware, ...)
- Local disk (supports DOS, GPT, Mac, BSD, Solaris)
- Logical files/folders (Supported file systems: NTFS, FAT/ExFAT, HFS+, ISO9660, Ext 2/3/4, YAFFS2, UFS)
- Unallocated Space Image File (no structure)
- Output from Autopsy Logical Imager
- Memory Image File (Volatility)
When you create a new case, the following structure will be automatically created (in the below example, Case1 is the name of the case that has been created):
.
└── Case1
├── autopsy.db
├── Cache
├── Case1.aut
├── Export
├── Log
│ ├── autopsy.log.0
│ └── autopsy.log.0.lck
├── ModuleOutput
│ ├── Image Gallery
│ │ ├── case1_20200505_160736.properties
│ │ └── drawable.db
│ └── keywordsearch
│ └── data
│ └── solr4_schema2.2
│ └── index
│ ├── segments_1
│ ├── segments.gen
│ └── write.lock
├── Reports
├── SolrCore.properties
└── Temp
$OrphanFiles
The $OrphanFiles folder contains files that do no longer have a parent folder.
$CarvedFiles
- Autopsy has the ability to recover deleted files without relying on the file system knowledge. It rather relies on the file structure internals.
- Autopsy relies on PhotoRec for the carving process.
- Carved files are stored within the $CarvedFiles directory
$Unalloc
- Unalocated space is considered as a file by Autopsy
- Will appear within the $Unalloc folder
User Interface
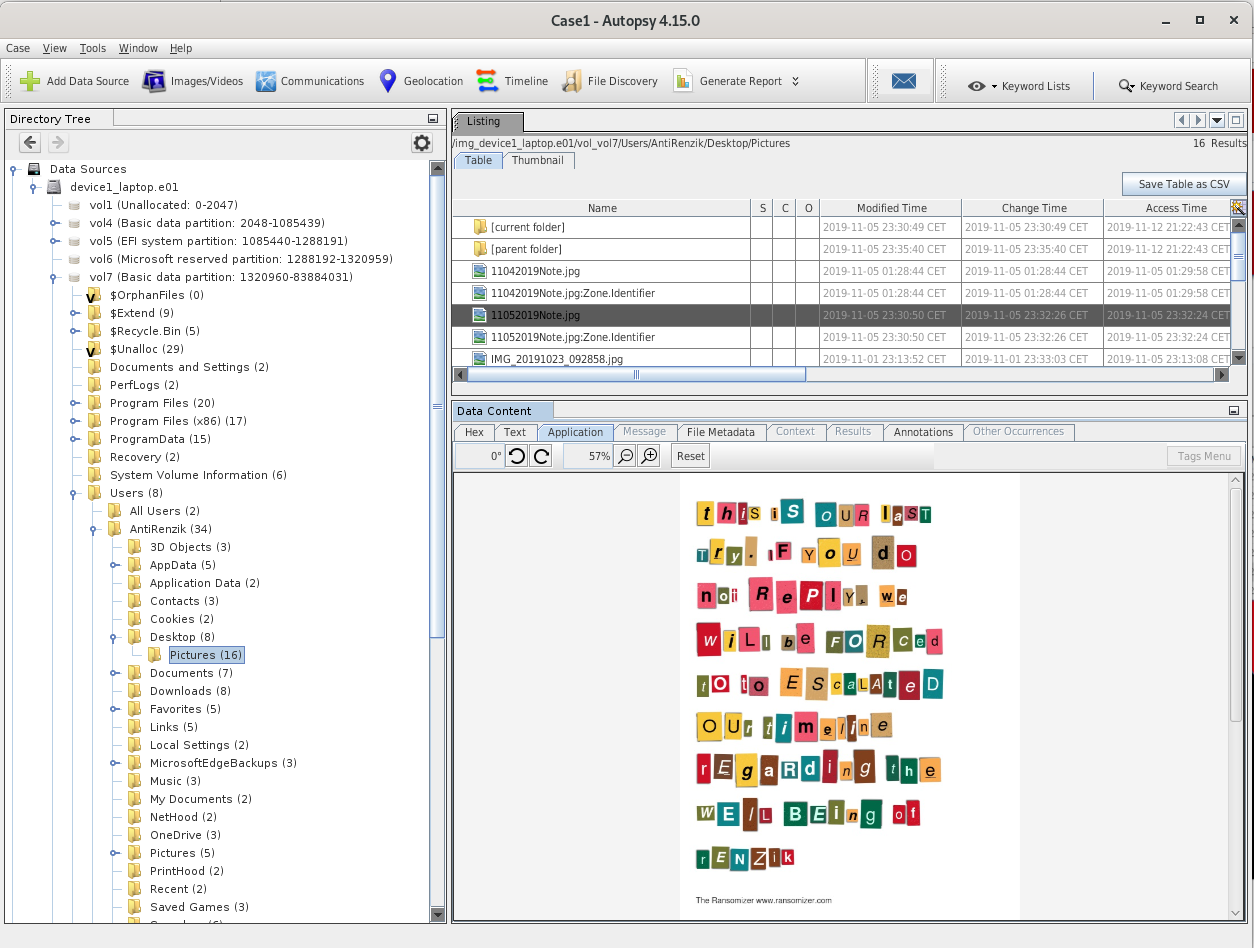
Overall
Here is what Autopsy looks like when you have created a case and added data sources:
Tree (menu)
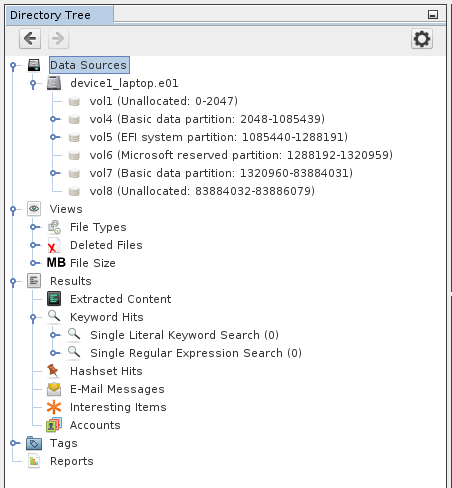
The tree on the left has 5 top-level nodes:
- Data sources
- Shows data added to the case, sorted by drive and directories
- Views
- Shows same files as the data sources, organized by metadata
- Useful for viewing files of a given type (images, documents, executables, etc.)
- Results
- Results from the analysis of ingest modules (lower levels of analysis and organization)
- Tags
- List of files and results that have been tagged by the examiner
- Reports
- Reports generated manually or automatically (modules)
Table view
- Will refresh when a node is selected from the tree
- You can rearrange columns
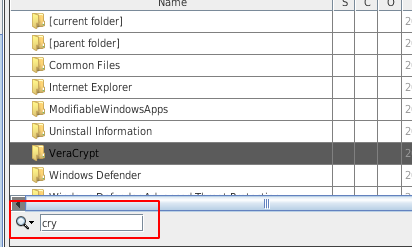
- To search, click on any item and type a few characters. The search field will appear:
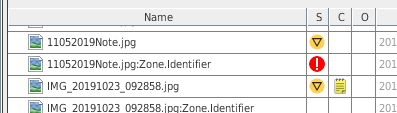
- Columns S, C, O:
- S(core): Item is interesting or notable (automatic detection, or manual tagging)
- C(comments): Indicates if item has a comment
- O(currences): Indicates how many times this item has been seen in past cases (requires Central Repository)
Content Viewer
- Automatically reloaded with the item selected from the table view.
- Several tabs:
- Hex: basic hex viewer. Push the "Launch in HxD" button for a more powerful hex editor (requires HxD to be installed)
- Text: several text searches (strings, indexed text, translation). Indexed text might be relevant for PDF or Word documents
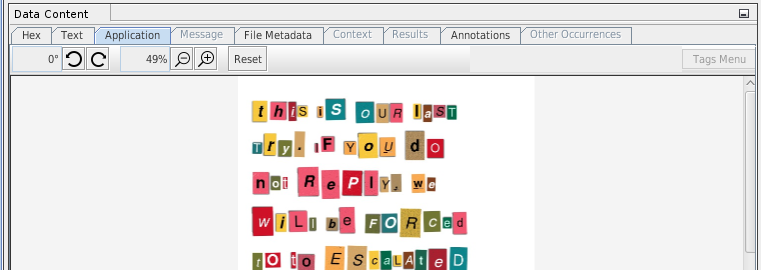
- Application: file type specific viewer (picture viewer, text viewer, video player, sqlite viewer, HTML viewer...)
- Message: relevant for emails. Email-like viewer
- File Metadata: Shows metadata of the selected file (name, type, MIME type, size, file name allocation, ...)
- Context:
- Results: all analysis results performed on selected file (e.g. hashes)
- Annotations: shows tags and comments from past cases and current one (provided Central Repository is enabled)
- Other occurences: shows where the file is found in previous cases (provided Central Repository is enabled)
Depending on installed modules, you may have additional tabs (e.g. Video Triage).
Toolbar
The toolbar shows more focused interfaces, including:
- Timeline: events sorted by time
- Image galerie: pictures and videos grouped by folders
- Communications: accounts, messages, call logs, etc.
Modules
Download modules
- https://www.autopsy.com/add-on-modules/
- Video Triage: Efficiently triage video content by splitting video files up into easily viewable thumbnail images (keyframes).
- Law Enforcement Bundle: Integrate Project Vic and C4P/All databases to identify known child exploitation images.
- https://github.com/sleuthkit/autopsy_addon_modules
- Ingest modules analyze files as they are added to the case. This is most common type of module.
- Content viewer modules are in the lower right corner of Autopsy and they display a file or selected item in some way.
- Report modules run at the end of the analysis and can generate various types of reports (or can do various types of analysis).
- Data source processors modules allow for different types of data sources to be added to a case.
Plugins installation
- To install a java based plugin, go to Tools > Plugins > Downloaded and click on the "Add Plugins" button.
- For python modules, go to Tools > Python Plugins
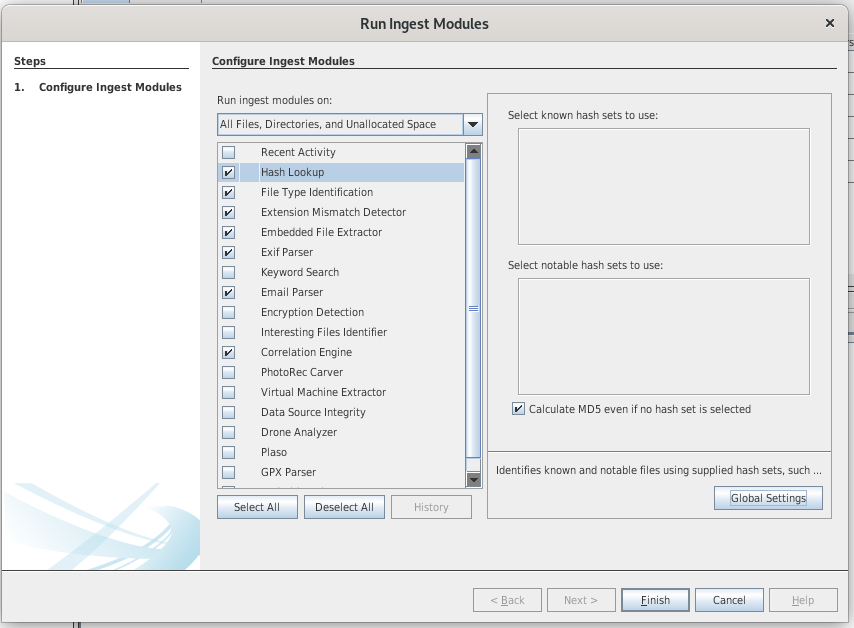
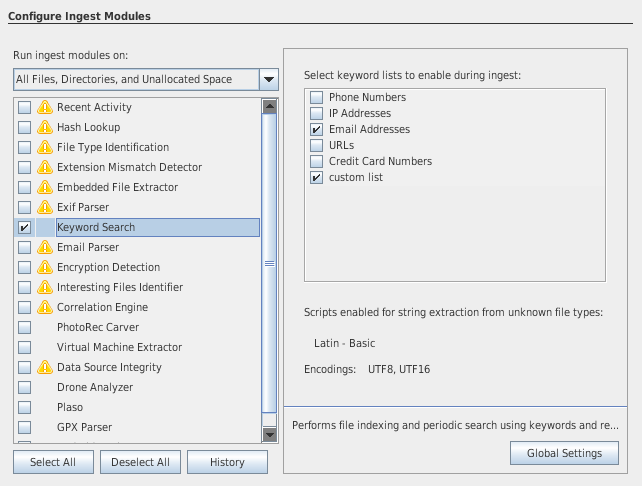
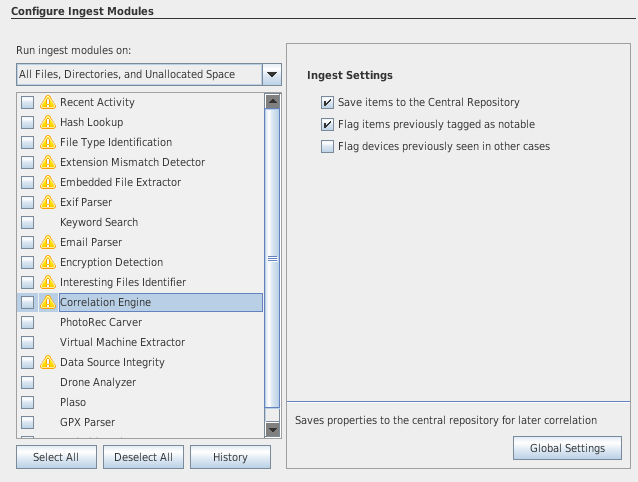
Ingest modules
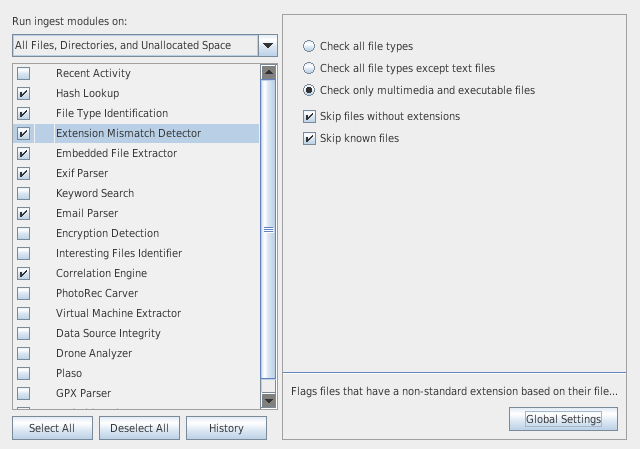
- Ingest modules (plugins) are responsible for analyzing the data.
- hashing
- keyword searching
- web activity
- registry analysis
- file type identification
- extension mismatch
- ...
- There are 2 types of ingest modules:
- file ingest modules (file hashes, hash lookup, EXIF extraction, add text to keyword index, ...)
- data sources ingest modules (web browser activity, registry activity, ...)
- Ingest modules are processed by the Ingest Manager, which runs in the background
- You can define ingest filters to only process a specific file type (e.g. *.jpg, *.png, ...)
- Results of the ingest modules are saved as Blackboard Artifacts
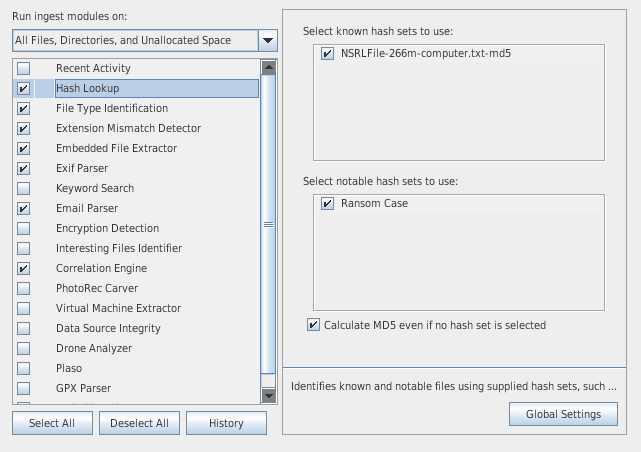
Hash Lookup
- Autopsy allows for multiple known bad hash databases to be set. Autopsy supports the following formats:
- EnCase: An EnCase hashset file.
- MD5sum: Output from running the md5, md5sum, or md5deep program on a set of files.
- NSRL: The format of the NSRL database.
- HashKeeper: Hashset file conforming to the HashKeeper standard.
There are 2 types of hash sets:
- Known hash set
- Use the "Import hash set" button from the global settings to import an existing hashset
- Recommended hashset to import: National Software Reference Library (NSRL)
- You can get a pre-indexed version of the NSRL hash set from here: https://sourceforge.net/projects/autopsy/files/NSRL/NSRL-266m-computer-Autopsy.zip/download
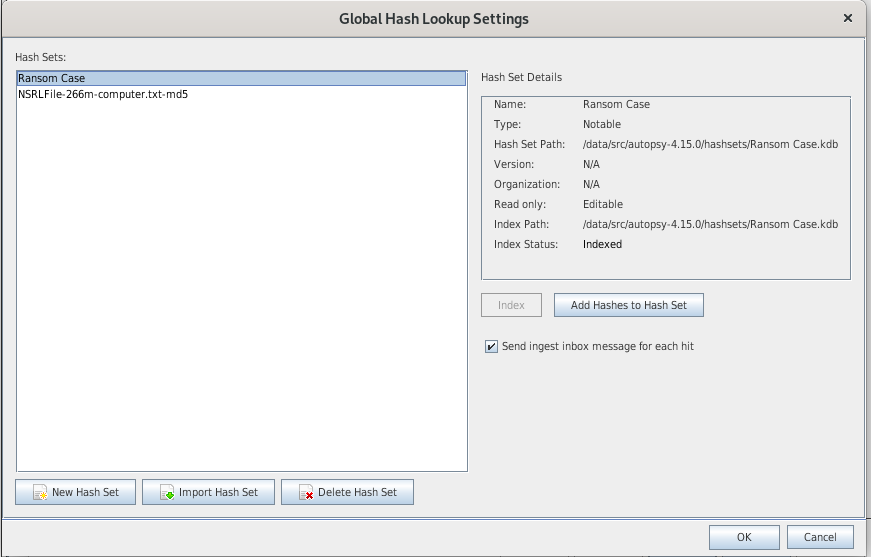
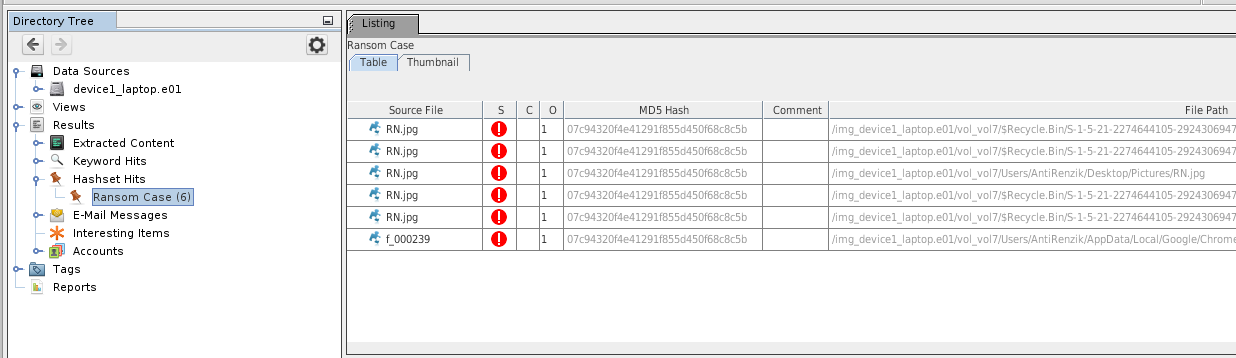
- Notable shash set
- Click on the "New hash set" button to create a custom hash set
- Click on the "add hashes to hashset" button to add items to the hashset (e.g. MD5 hashes)
- results appear in tree, under Results > Hashset Hits:
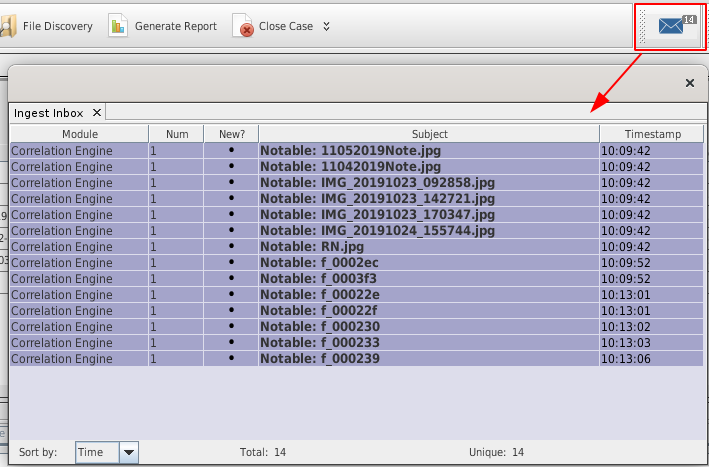
- During the ingestion process, notable files will be added to your Inbox:
File Type Identification
- Uses the Tika module from Apache to identify files based on files signatures (not extensions)
- Recommended to leave enabled (Required by some other modules)
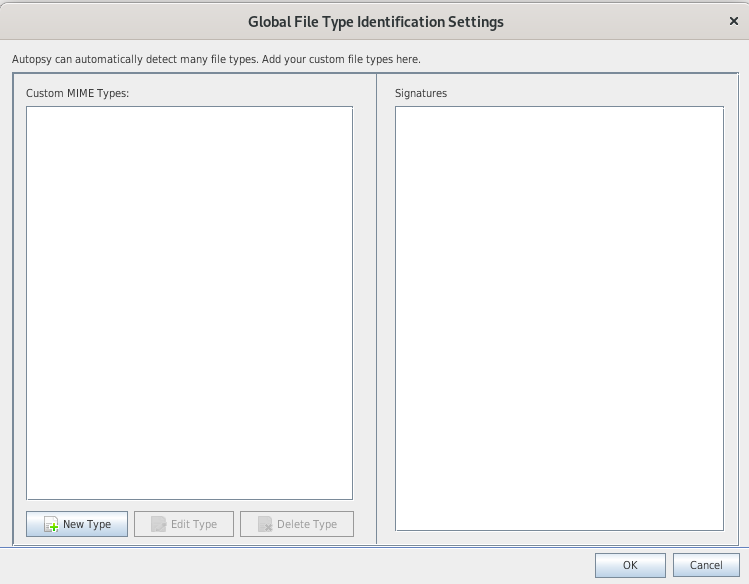
- You can define custom MIME types in the global settings
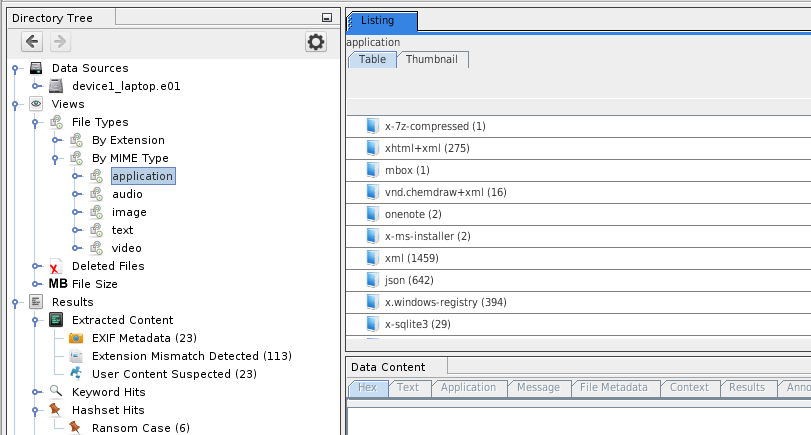
- Results appear in the tree under Views > File Types > By MIME Type:
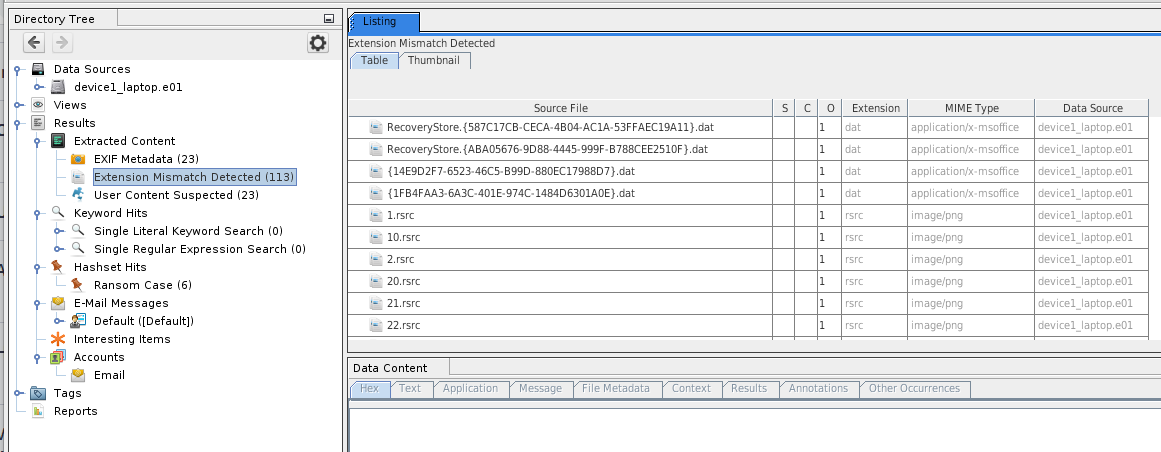
Extension Mismatch Detector
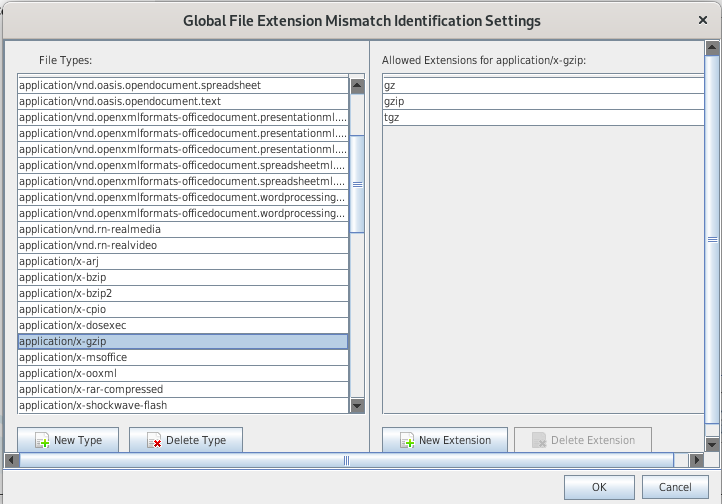
- This module will identify file extension mismatch by comparing the results of the "file type identification" module and the extension of the file.
- Will output many false positives due to temporary files (*.0, *.1, *.tmp, ...), backup files (*.bak, *.init, ...)
- Use the "global settings" to modify the file mapping
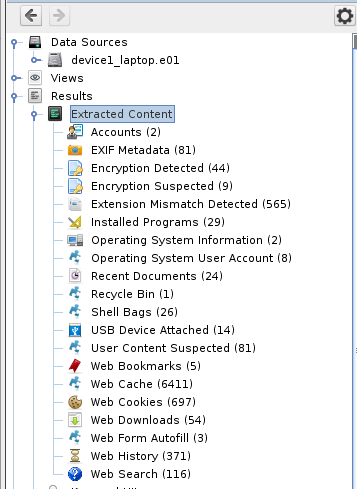
- Results appear in the tree under Results > Extracted Content > Extension Mismatch Detected:
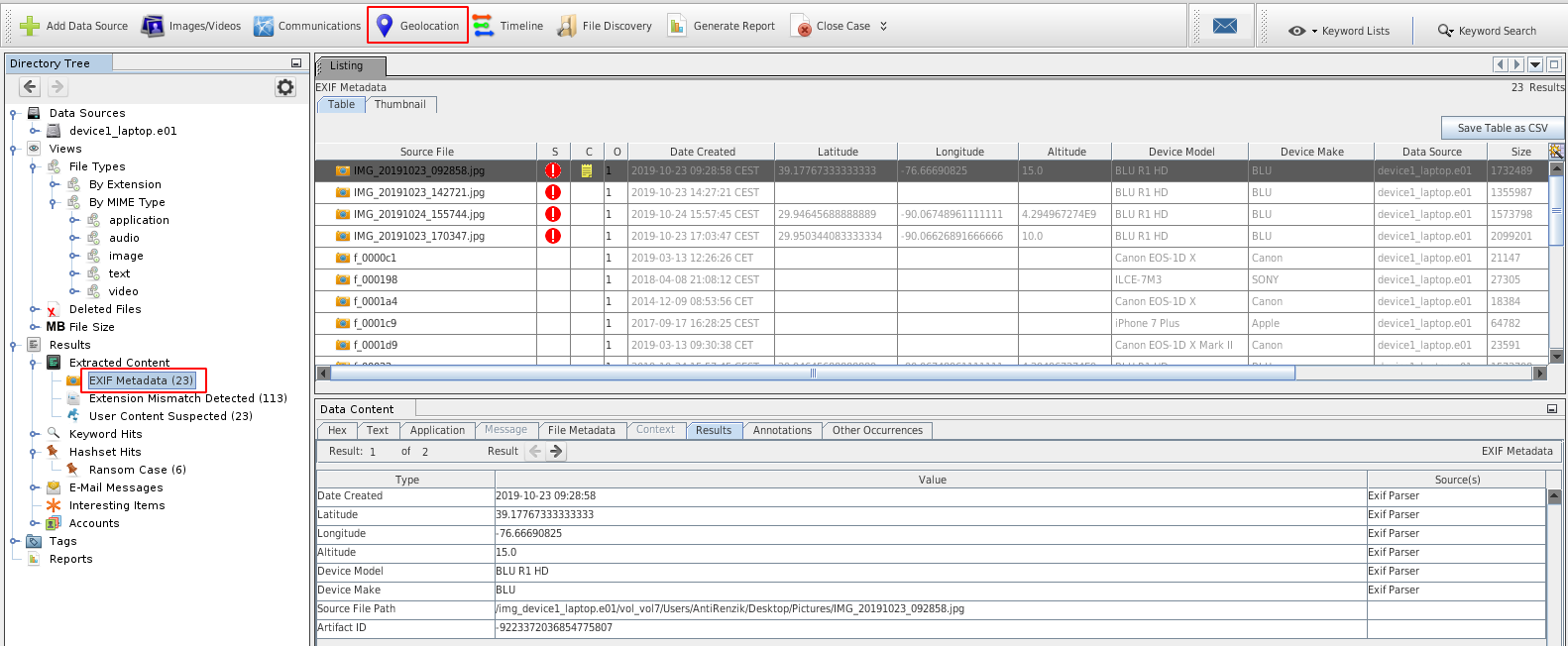
EXIF parser
- Extracts metadata from images.
- Results appear in the tree under Results > Extracted Content > Exif metadata:
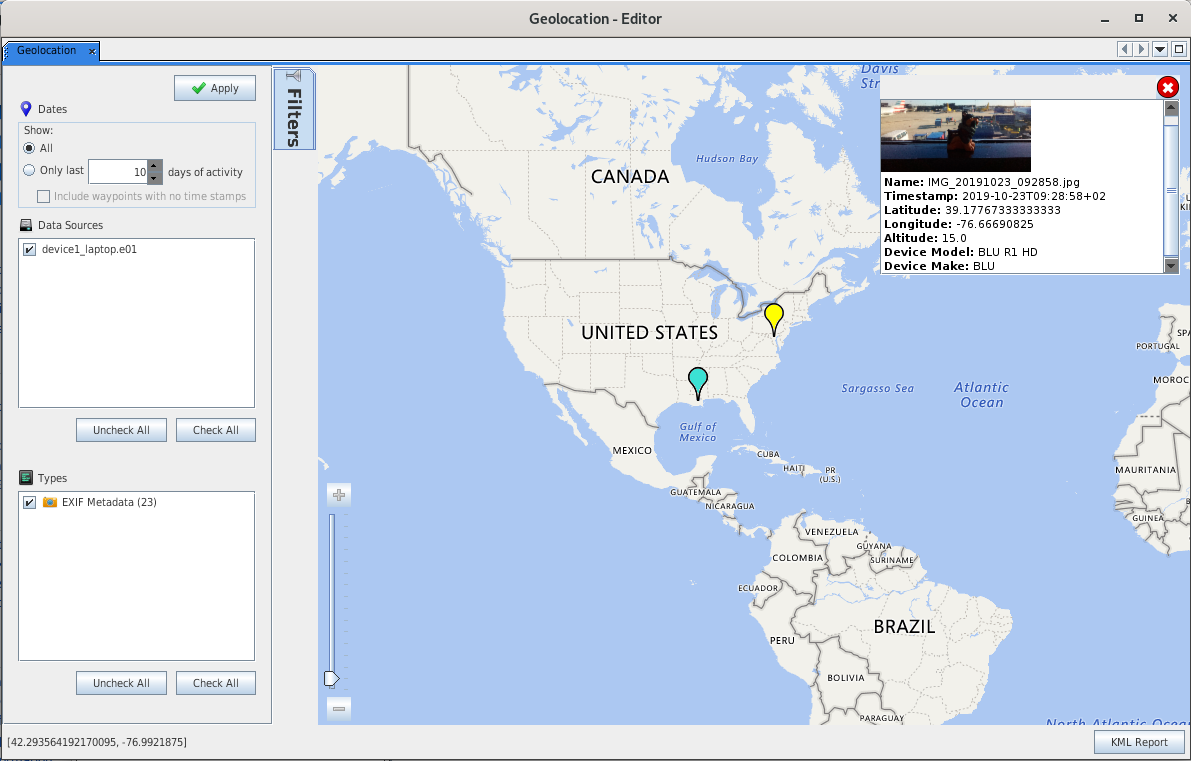
By clicking on the "Geolocation" button, you can also see where the pictures have been taken (provided geolocation tags are present):
Embedded File Extractor
- Extracts embedded files in archives (*.zip, *.rar, ...)
- Extracts images from Office and PDF files
- Results appear directly from the tree view:
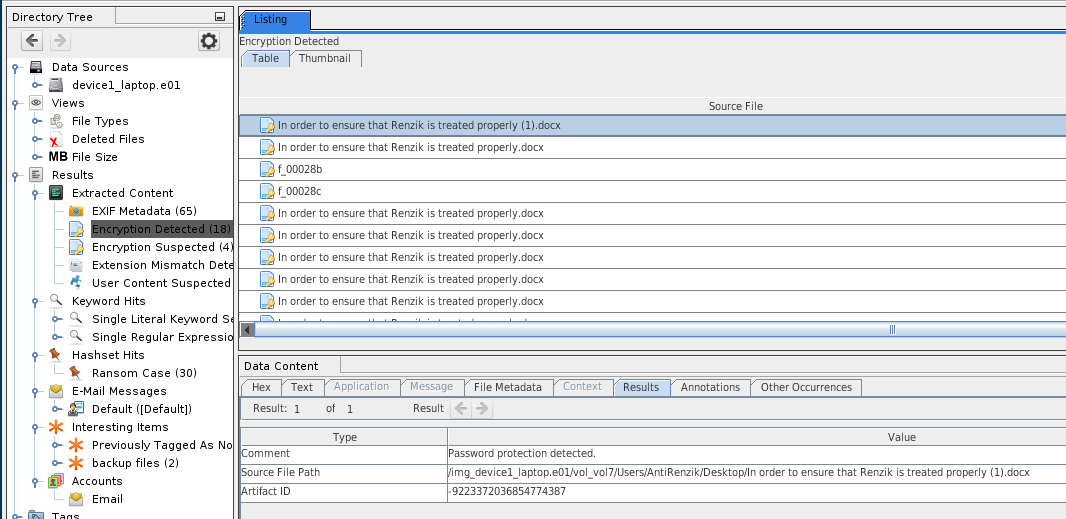
- Password protected compressed archives:
- can't be automatically analyzed. They will appear under Results > Extracted Content > Encryption Detected.
- Right click on the archive and select "unzip contents with password"
Email Parser
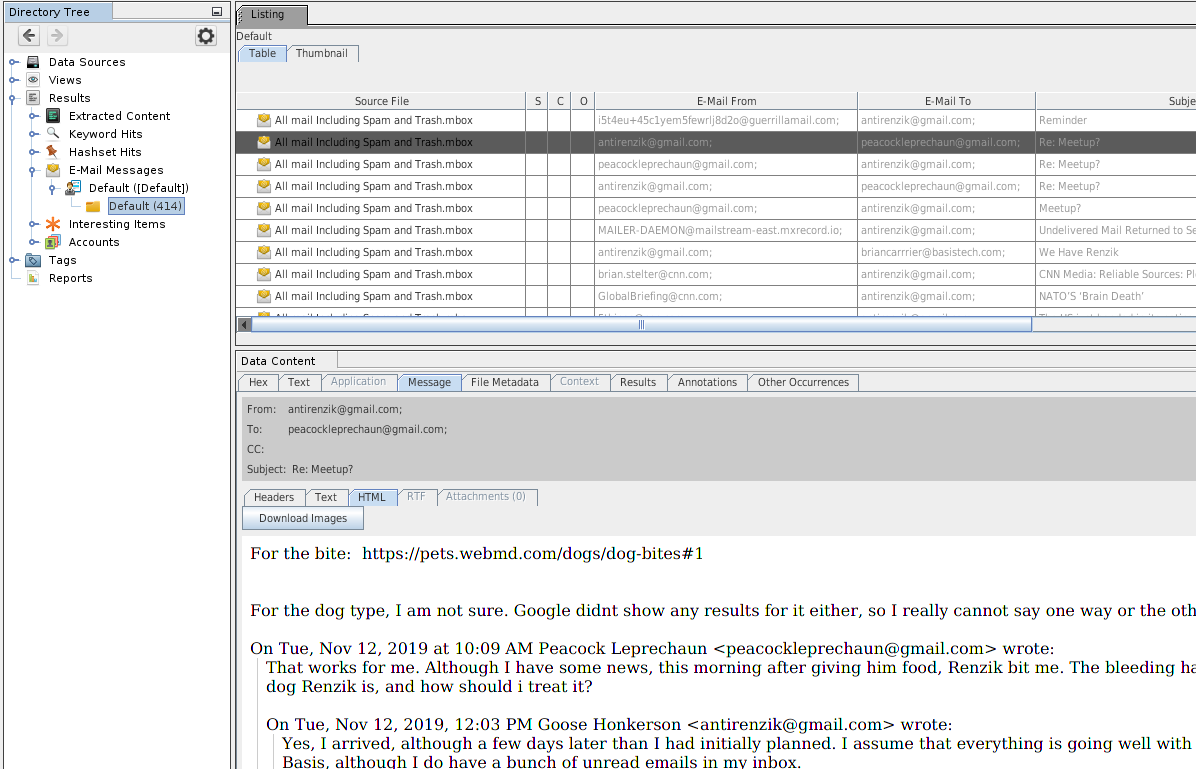
- Parses *.mbox, *.pst and *.eml files
- Extracts attachments as children of the messages
- Group mesages into threads
- Results appear in the tree under Results > Email messages
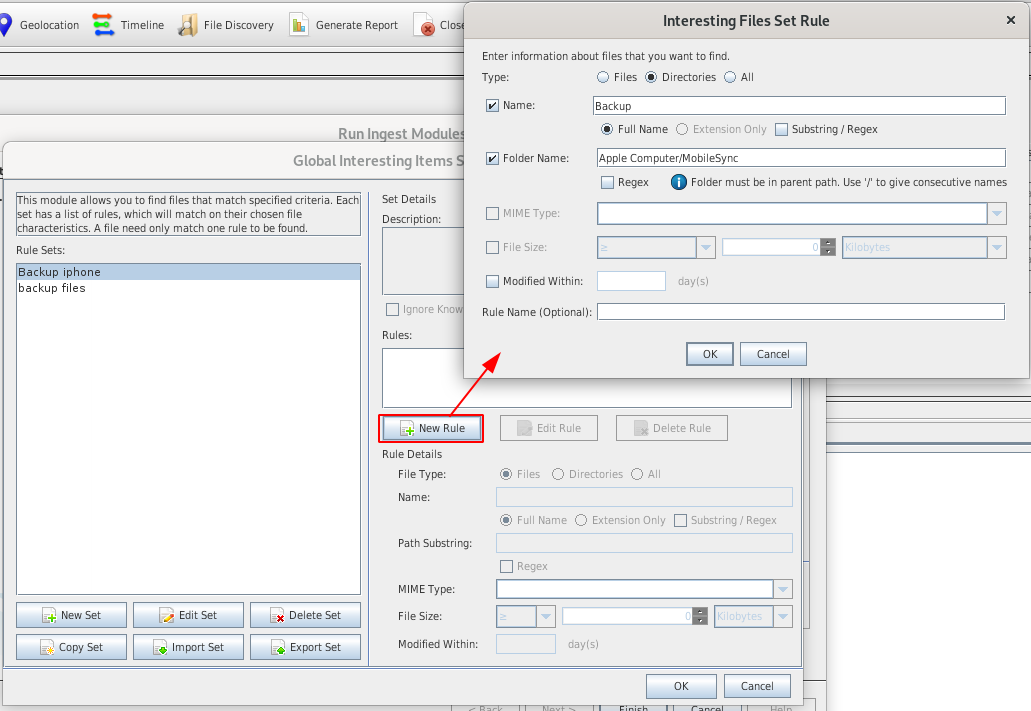
Interesting Files
- Flags files and folder as "interesting" based on rules you have defined
- Organized by sets containing rules
- Examples:
- iphone backups
- Rule1: (type="directories", fullname="iphone Backup", foldername="/Apple Computer/MobileSync/")
- vmware images
- Rule 1: (type="files", fullname="vmplayer.exe", name="Program EXE")
- Rule 2: (type="files", extension="vmdk", name="VMDK File")
- bitcoin wallets
- cloud storage clients
- ...
- iphone backups
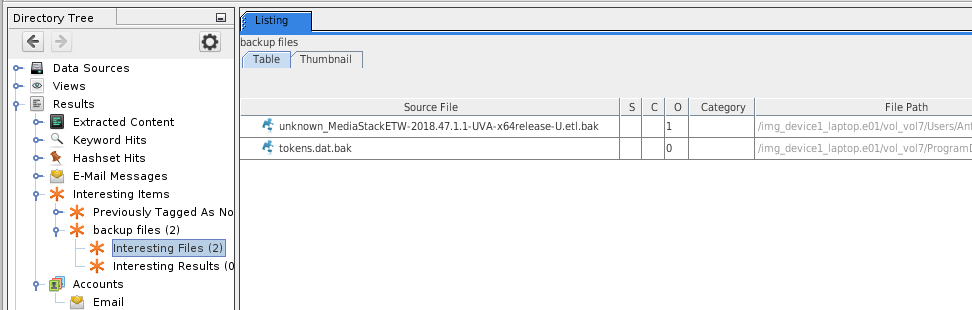
- Results will appear in the tree under Results > Interesting items:
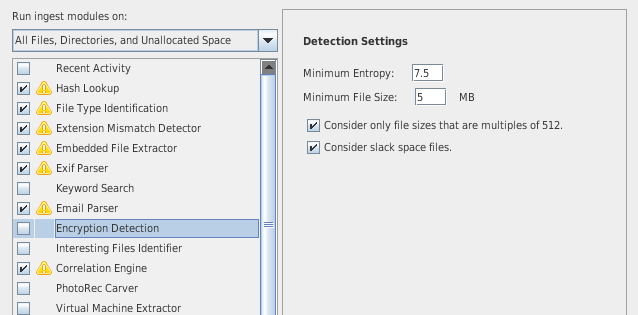
Encryption Detection
- Flag files and volumes that are or may be encrypted
- Can detect passwords on Office documents
- Results will appear in the tree under:
- Results > Extracted Content > Encryption Detected
- Results > Extracted Content > Encryption Suspected
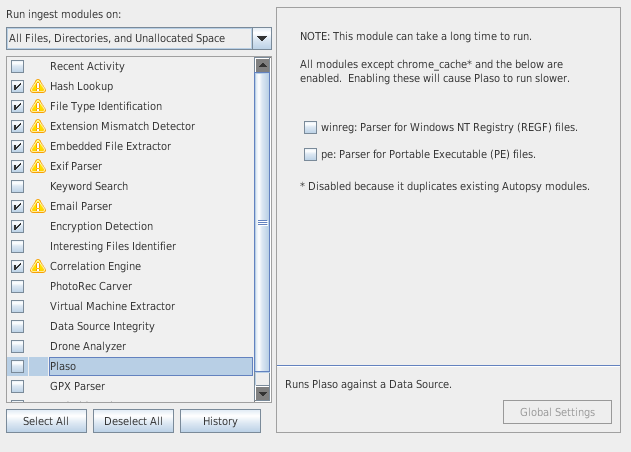
Plaso

- Relies on Plaso to extract timestamps in order to put artifacts on the timeline
- Scan various logs and file types to extract timestamps
Virtual Machine Extractor
- Analyzes virtual machines in data sources
- Detects presence of *.vmdk and *.vhdi files
- Feeds them back in as data sources
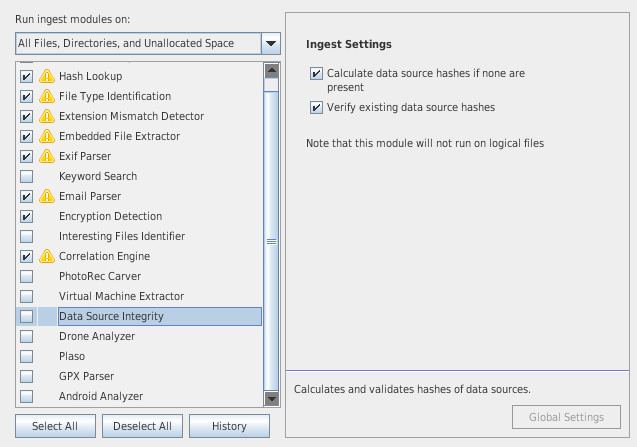
Data Source Integrity
- Validates and calculates hash of disk image (to ensure integrity of evidence)
- Retrieves hash from E01 images, or manual user entry when a new data source is added
- Triggers alerts if hashes are different
- Results appear in the tree, under Results > Extracted Content > Verification Failure
Recent Activity
- Extracts recent user activity:
- Web Activity
- bookmarks, cookies, downloads, ...
- Artifacts may vary depending on the browser (see below table)
- Artifacts from the same nature are merged whatever browser they come from
- Registry Activity (USB devices, user accounts, installed programs, program runs)
- Recycle Bin Activity
- Web Activity
| History | Cookies | Bookmarks | Downloads | Cache | Addresss Auto Fill | Web Form Auto Fill | |
|---|---|---|---|---|---|---|---|
| Chrome | ● | ● | ● | ● | ● | ● | ● |
| Firefox | ● | ● | ● | ● | ● | ● | |
| Internet Explorer | ● | ● | ● | ||||
| Edge | ● | ● | ● | ||||
| Safari | ● | ● | ● | ● |
- Results will be found in the tree, under Results > Extracted Content
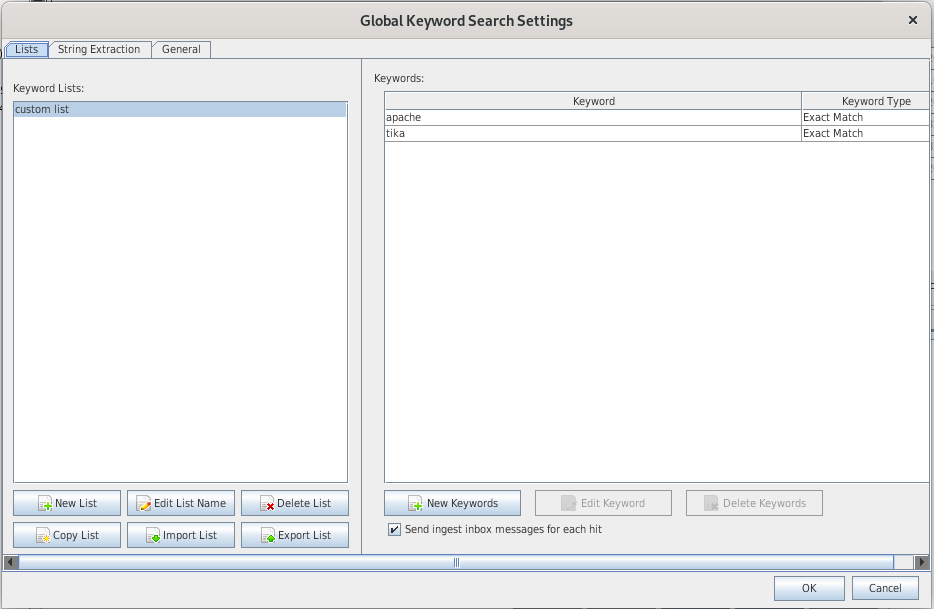
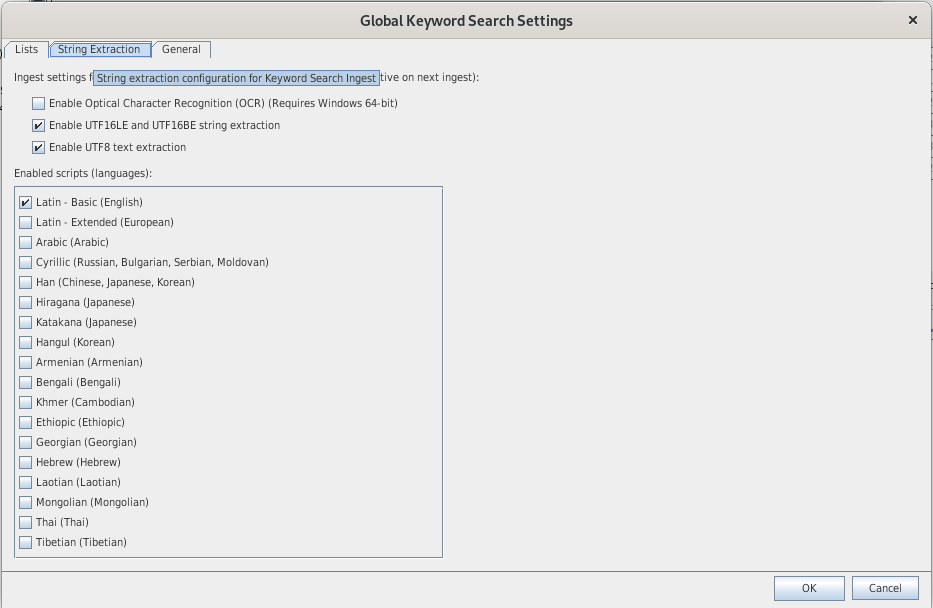
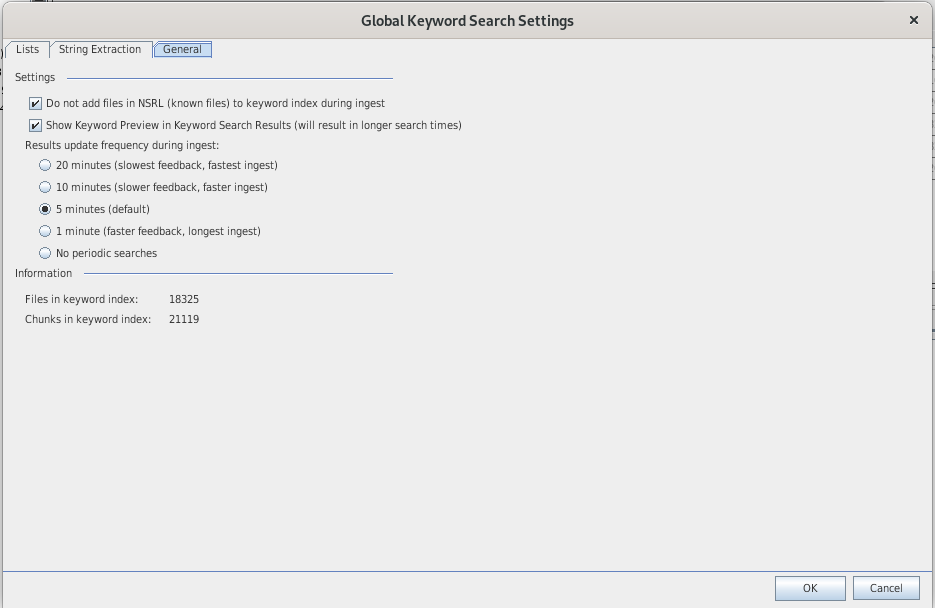
Keyword Search
Indexes
- Text searches rely on indexes, specific to each case
- A text index is an organized collection of words and the files that contain them.
- Relies on Apache Solr search engine
- There are already defined indexes (phone numbers, credit cards numbers, ...)
You can define new indexes:
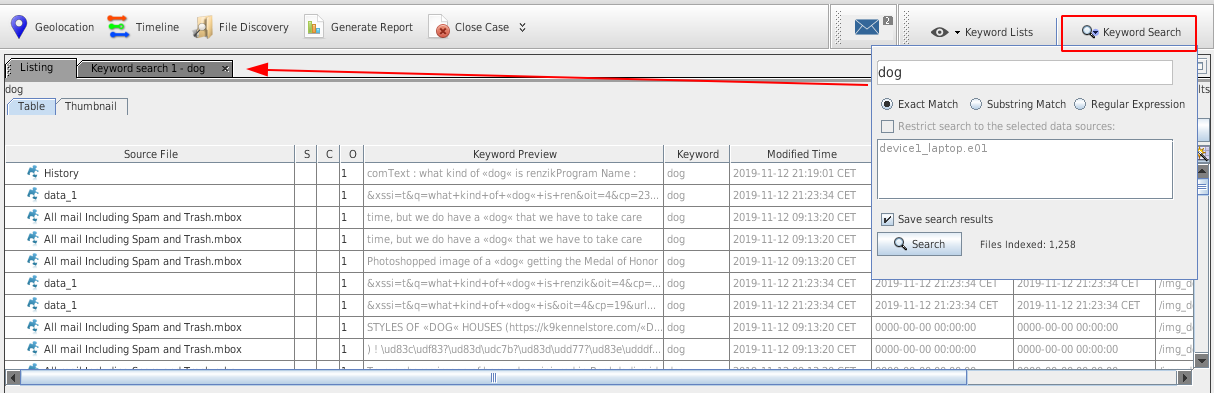
Search
You can search:
- exact matches ("ear" will only match "ear")
- substrings ("ear" will match both "ear" and "bear")
- regular expressions (existing regex have been defined for US phone number, IP addresses, emails, URLs, ..)
To do a search, hit the Keyword search button:
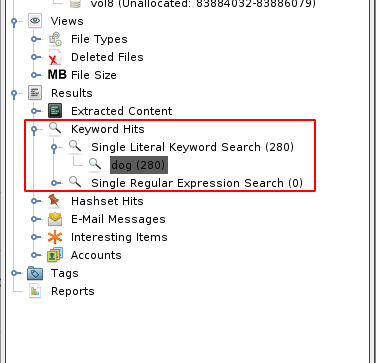
Search results can also be found in the tree view, under Results > Keyword Hits:
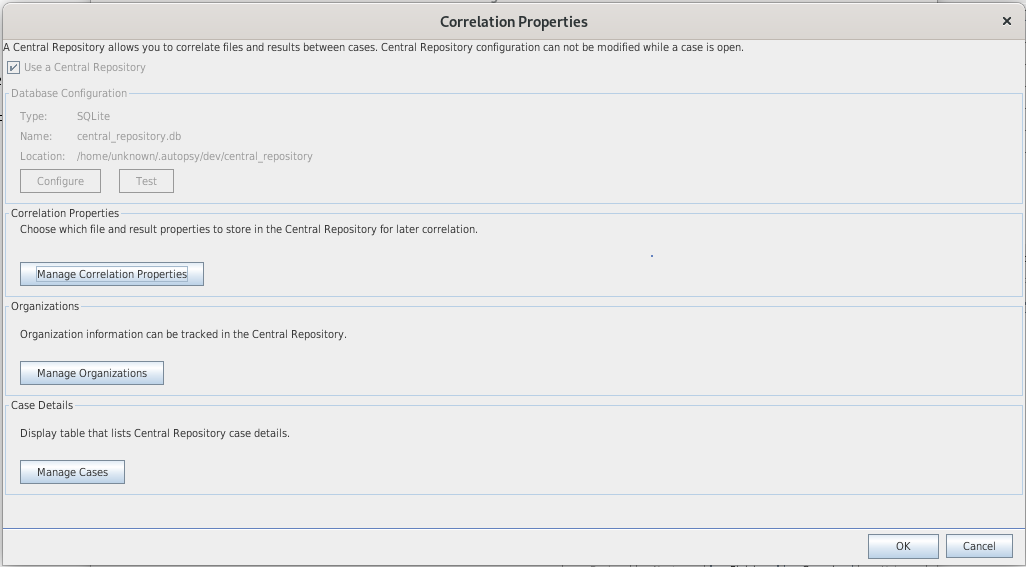
Correlation Engine
- The Correlation engine has 2 main features:
- Query the Central Repository: correlates the current case with other cases and flag iteams tha were previously notable
- Add data to Central Repository: add data from current case to ensure correlation for future cases
- Data that can be correlated: MD5, Domain names, Email addresses, phone numbers, USB device IDs, wifi SSIDs
- The Correlation engine module can be configured to generate alerts based on the existence of previously seen data.
- Results will appear in the tree, under Results > Interesting items > Previously Tagged As Notable
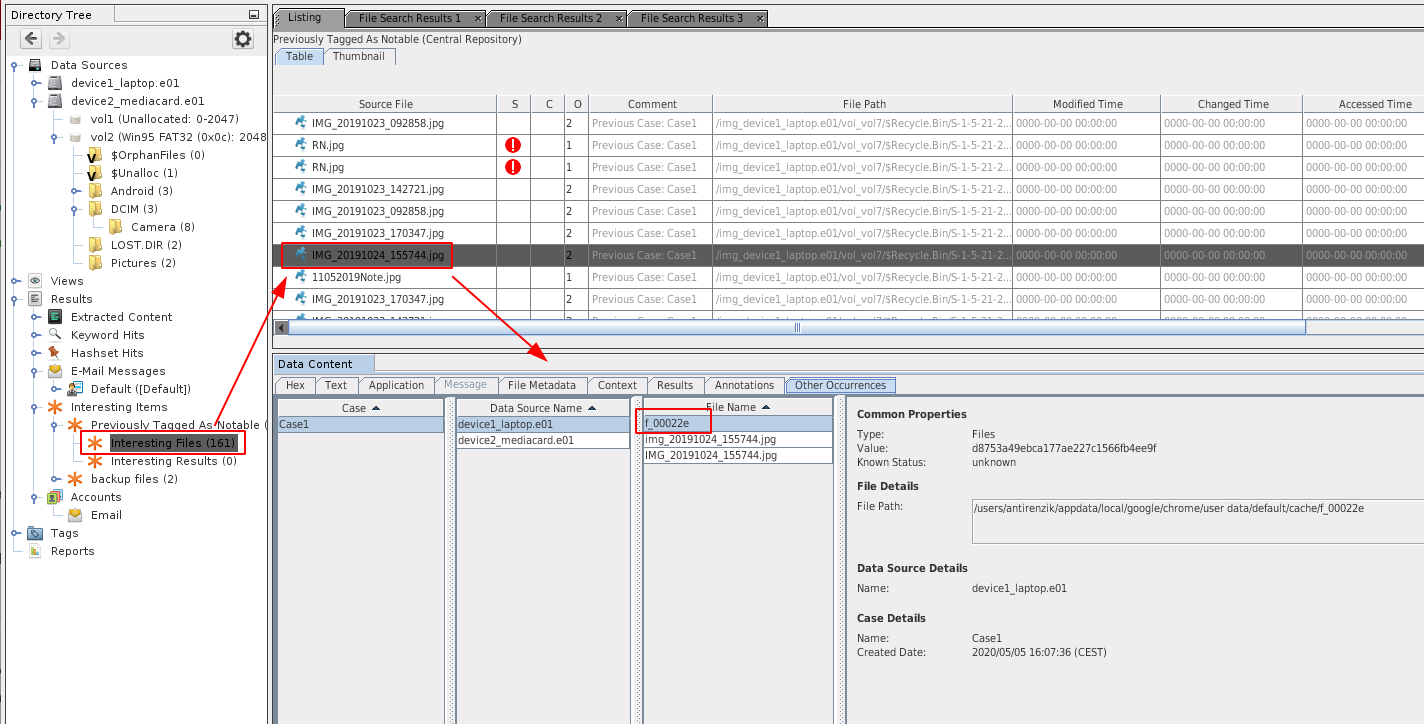
Below is an example:
We have a case containing 2 data sources, and we want to know if a specific file (the highlighted *.jpg image) was found accross the data sources. The correlation engine has automatically identified that the file was found on both data sources (based on the common MD5) and lists the different file names under which the file was present.
Android Analyzer
- Locates SQLite databases and files from Android and third party apps.
- Parses the databases
- Adds results to the blackboard
- Can extracts calls logs, contacts, messages, browsers apps, file transfer apps, geo apps (constant improvements added to future versions)
- Results will be shown in the tree under Results > Extracted Content
Special toolbars & features
Tags and Comments
Tags
- Tags are used for reporting evidences, and can also serve other cases
- You can add tags on files by right clicking on them
- For images, you can either tag the picture or a portion of it
- When tagging a file, you can also mark at as notable (will generate alerts by the correlation engine if the file is found in future cases)
- Tagged files appear in the tree under Tags (bookmarks, Suspicious, ..)
Comments
- Comments allow to make notes about why a file is tagged
- Comments will appear in the reports
- To comment, right click on a file and select "Tag and Comment"
- Commented files will have a special icon in the "C" column of the results table.
TimeLine
- Allows to graphically view the activity of the analyzed system over time.
- Relies on other modules to extract timestamps (file times, web activity, EXIF, Plaso, Android, ...)
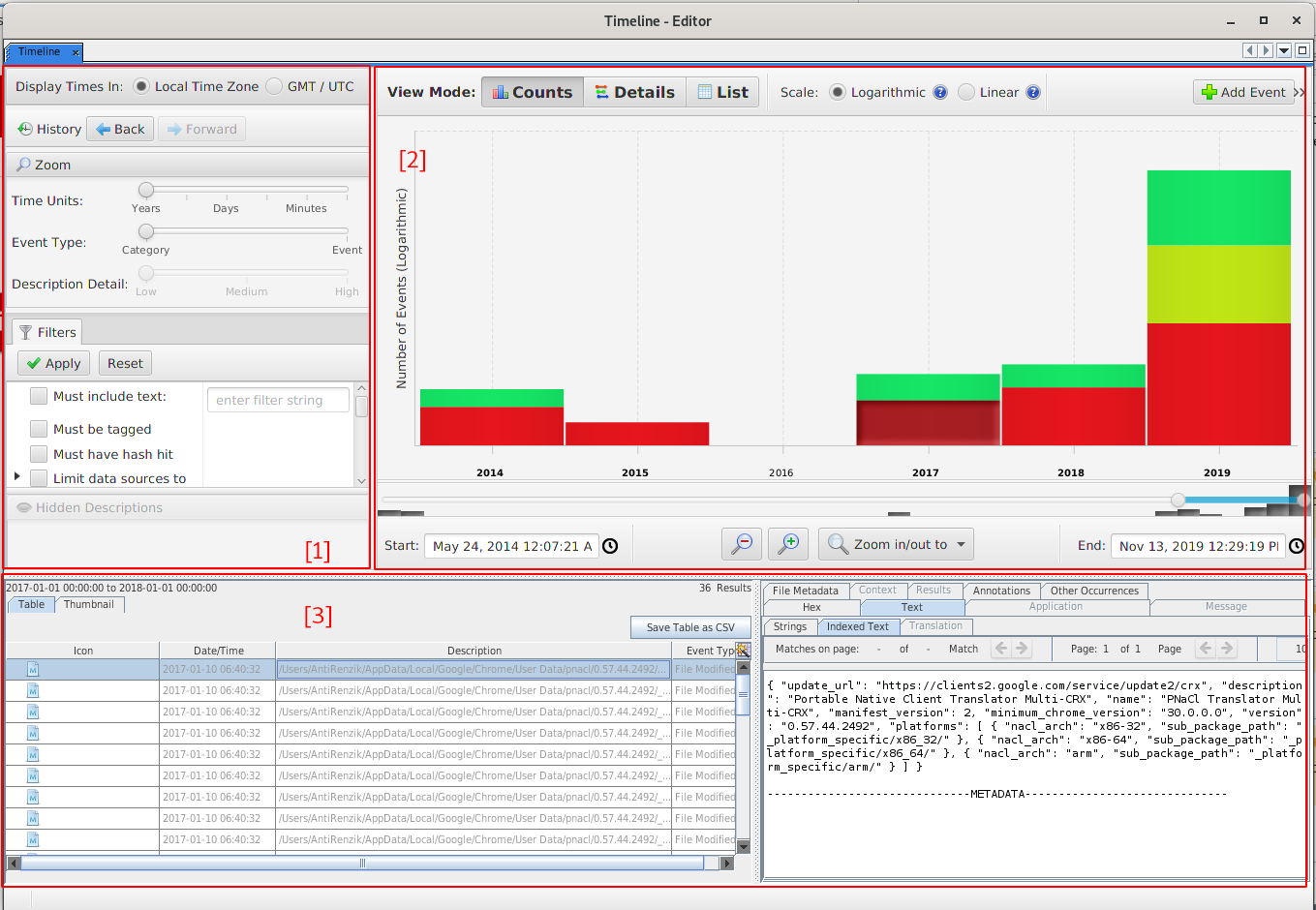
- Layout:
- Filters (1)
- Events (2)
- Files and Content (3)
- 3 Views (tabs):
- Counts
- Bar chart view to show number of events (e.g. when was the system last used, first used, ...)
- Double clicking on year drills down to months, then to days, ...
- Colors: red=file system, green=web activity, blue=misc types
- Details
- Shows specific events (what event occured on a given day, what happened after a file was downloaded, ...)
- Events are clustered together to prevent data overload
- The [+] and [-] icons on clusters expand and collapse the cluster
- You can also show/hide clusters, and pin/unpin (will put the cluster on top on the view)
- You can also place a marker (will show a vertical red line)
- List
- Shows all events in order in a basic table
Image gallery
- Dedicated interface to review images and videos
- Displays images organized by folder, prioritized based on density of hash hits and number of images in folder
- Requires file type, hash and Exif information
- Borders signify what is known about an image:
- purple dashed for hash hits
- other colors for tagging / categorization
Communications
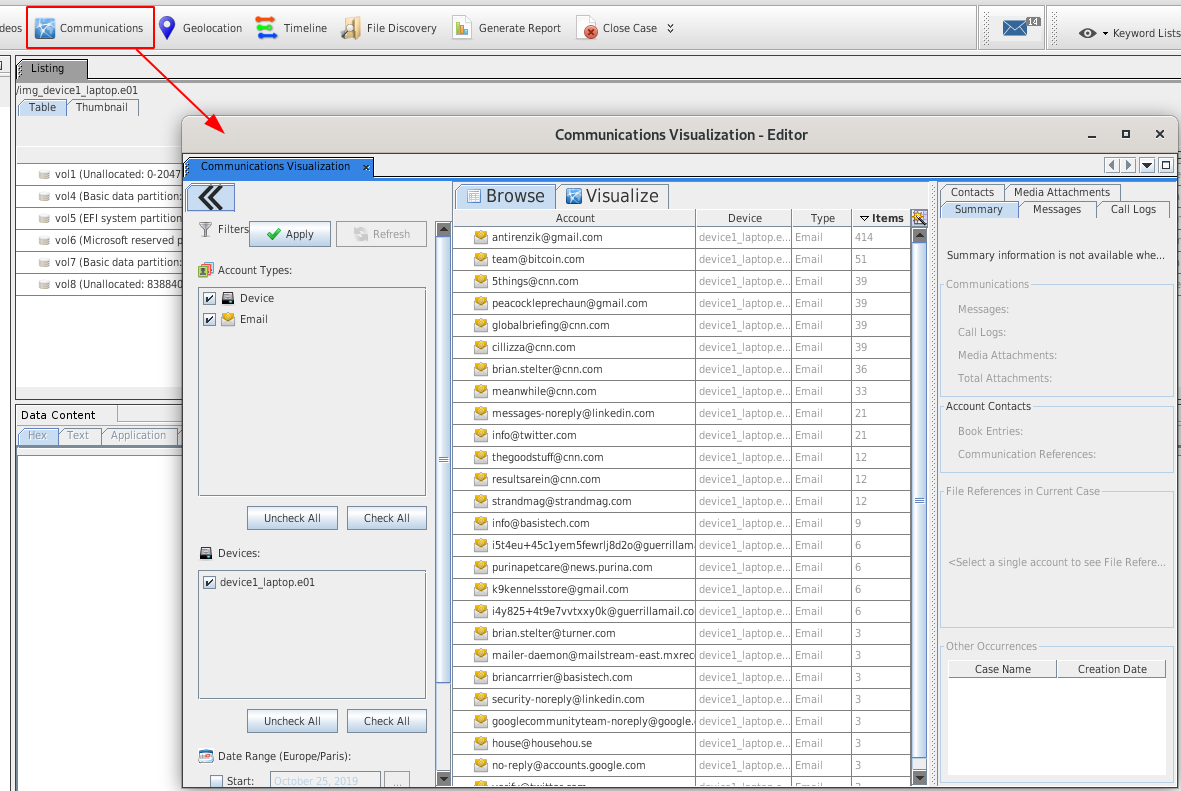
File:Autopsy-ui-communications.png
- This interface is focused on accounts and not data types
- Accounts have types (e.g. email) and identifier (e.g. [email protected])
- A relationship is identified if one person ([email protected]) is sending an email to [email protected]
- Device account is a special account created for each data source to represent the physical device when no better account ID is found (e.g. call log database defines only the other recipient)
- Relies on other ingest modules (Android Analyzer, email, ...)
- The interface is composed of:
- filters (data sources, account types, date range)
- results (that meet the filter criteria), sorted by number of messages
- relationship details (once an account is selected). Several tabs (summary, messages, call logs, contacts, media)
Generate report
- Reports can be exported as HTML, Excel, text, KML, portable case (kind of a filtered Autopsy case with only tagged files)...
- A report will contain the outcome of the analysis module and the tagged items.
- When you create a report, you will have several options (all results, all tagged results, specific tagged results)
- For Excel reports, 1 data type / worksheet
- Files reports will show what files are in the case (1 line / file). You can choose the columns that will be included in the report.
Comments
Keywords: autopsy sleuthkit investigation case forensics extraction