Bcc86c024f6bd004772c4bef39249e2c
Jump to navigation
Jump to search
Description
Summary

INCOMPLETE SECTION OR ARTICLE
This section/article is being written and is therefore not complete.
Thank you for your comprehension.
Thank you for your comprehension.
Identification
| MD5 | bcc86c024f6bd004772c4bef39249e2c |
|---|---|
| SHA1 | 815c92f5061d6c3a7c094003975acdd68f714084 |
| SHA256 | caaaf550aa0e5a6cc81af048b5a7155e2aa5a52fc14c0a29867ecf4a36f7eeec |
| ssdeep | 3072:p8DTumuhez9/Xwwb50UUgaonCgV8c3Jc6gMxU+d9axMoPu:pFm7z9vwwb5RUga/s+6HeysO |
| File size | 100.6 KB ( 103030 bytes ) |
| File type | Win32 EXE |
| Magic literal | PE32 executable for MS Windows (GUI) Intel 80386 32-bit |
| TrID |
|
Detection
Antivirus detection
| Antivirus | Result | Update |
|---|---|---|
| Ad-Aware | Trojan.Generic.7224364 | 20140415 |
| AegisLab | 20140415 | |
| Agnitum | Worm.Ngrbot!nBqqjl///rY | 20140414 |
| AhnLab-V3 | Trojan/Win32.Agent | 20140414 |
| AntiVir | TR/Graftor.617589 | 20140415 |
| Antiy-AVL | Worm/Win32.Ngrbot | 20140415 |
| Avast | Win32:Flooder-HQ [Trj] | 20140415 |
| AVG | Dropper.Generic5.EHG | 20140415 |
| Baidu-International | Worm.Win32.Ngrbot.aON | 20140414 |
| BitDefender | Trojan.Generic.7224364 | 20140415 |
| Bkav | 20140415 | |
| ByteHero | 20140415 | |
| CAT-QuickHeal | Backdoor.Bifrose.AE6 | 20140415 |
| ClamAV | Win.Trojan.Ngrbot-13 | 20140415 |
| CMC | Worm.Win32.Ngrbot!O | 20140411 |
| Commtouch | W32/Dorkbot.G.gen!Eldorado | 20140415 |
| Comodo | Worm.Win32.Agent.BSM | 20140415 |
| DrWeb | BackDoor.Bifrost.40 | 20140415 |
| Emsisoft | Worm.Win32.Ngrbot (A) | 20140415 |
| ESET-NOD32 | a variant of Win32/Injector.URT | 20140415 |
| F-Prot | W32/Dorkbot.G.gen!Eldorado | 20140415 |
| F-Secure | Trojan.Generic.7224364 | 20140414 |
| Fortinet | W32/Dorkbot.AS!tr | 20140413 |
| GData | Trojan.Generic.7224364 | 20140415 |
| Ikarus | Backdoor.Win32.Bifrose | 20140415 |
| Jiangmin | Backdoor/Ruskill.ce | 20140415 |
| K7AntiVirus | Riskware ( b8133cd50 ) | 20140414 |
| K7GW | EmailWorm ( 002d22d51 ) | 20140414 |
| Kaspersky | Worm.Win32.Ngrbot.bzm | 20140415 |
| Kingsoft | Worm.Ngrbot.(kcloud) | 20140415 |
| Malwarebytes | 20140415 | |
| McAfee | Generic BackDoor.aew | 20140415 |
| McAfee-GW-Edition | Generic BackDoor.aew | 20140415 |
| Microsoft | Trojan:Win32/Injector.AB | 20140415 |
| MicroWorld-eScan | Trojan.Generic.7224364 | 20140415 |
| NANO-Antivirus | Trojan.Win32.Bublik.cjgnqh | 20140415 |
| Norman | Bifrose.CJGL | 20140415 |
| nProtect | Trojan.Generic.7224364 | 20140414 |
| Panda | Bck/Bifrost.gen | 20140414 |
| Qihoo-360 | HEUR/Malware.QVM02.Gen | 20140415 |
| Rising | PE:Backdoor.Win32.Fednu.qw!1075350914 | 20140414 |
| Sophos | Troj/Kazy-S | 20140415 |
| SUPERAntiSpyware | Trojan.Agent/Gen-Ruskill | 20140415 |
| Symantec | Backdoor.Trojan | 20140415 |
| TheHacker | W32/Ngrbot.bzm | 20140413 |
| TotalDefense | 20140415 | |
| TrendMicro | TSPY_NGRBOT_CA08296D.TOMC | 20140415 |
| TrendMicro-HouseCall | TSPY_NGRBOT_CA08296D.TOMC | 20140415 |
| VBA32 | Worm.Ngrbot | 20140414 |
| VIPRE | Trojan.Win32.Injector.ab (v) | 20140415 |
| ViRobot | Worm.Win32.A.Ngrbot.93696 | 20140415 |
Snort detection

INCOMPLETE SECTION OR ARTICLE
This section/article is being written and is therefore not complete.
Thank you for your comprehension.
Thank you for your comprehension.
Links
- Virustotal: https://www.virustotal.com/en/file/caaaf550aa0e5a6cc81af048b5a7155e2aa5a52fc14c0a29867ecf4a36f7eeec/analysis/1397545927/
- Malwr: https://malwr.com/analysis/MDc3ZDg1YTQ4MGY0NDg5NzhmY2ZiYTc1YWRmMzRlMzQ/
- Download: https://www.dropbox.com/s/3dh22x2pgczufsb/bcc86c024f6bd004772c4bef39249e2c.zip (pass: infected)
Artifacts
Persistence
The malware achieves persistence by creating following registry keys:
| Key | Name | Type | Value |
|---|---|---|---|
| HKLM\SOFTWARE\Microsoft\Active Setup\Installed Components\{9D71D88C-C598-4935-C5D1-43AA4DB90836} | stubpath | REG_EXPAND_SZ | C:\WINDOWS\system32\Bifrost\server.exe s |
| HKCU\Software\Microsoft\Windows\CurrentVersion\Run | ctfmon | REG_SZ | C:\WINDOWS\TEMP\services.exe |
| HKCU\Software\Microsoft\Windows\CurrentVersion\Run | msmmsgr | REG_SZ | C:\WINDOWS\TEMP\x\services.exe |
Files activity
Following files are created:
| File | Size | Type | Hash |
|---|---|---|---|
| C:\Documents and Settings\malware\Application Data\addons.dat | 25 KB (24821 bytes) | data (encrypted) |
|
| C:\WINDOWS\system32\Bifrost\logg.dat | 2.4 KB (2411 bytes) | Non-ISO extended-ASCII text, with NEL line terminators |
|
| C:\WINDOWS\system32\Bifrost\server.exe | 101KB (103030 bytes) | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows |
|
| C:\WINDOWS\Temp\services.exe | 101 KB (103030 bytes) | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows |
|
The malware copies itself to 2 locations:
- C:\WINDOWS\system32\Bifrost\server.exe
- C:\WINDOWS\Temp\services.exe
Registry database
Created entries
| Key | Name | Type | Value |
|---|---|---|---|
| HKLM\SOFTWARE\Bifrost | nck | REG_BINARY | ed 1b e6 27 b9 28 d6 32 74 c3 cd 74 fa 93 5b 67 |
| HKCU\Software\Bifrost | klg | REG_BINARY | 01 |
| HKCU\Software\Bifrost | plg1 | REG_BINARY | ea 44 dc 02 a3 27 d7 5f 11 ad b9 07 da f2 35 03 2a 35 8e 58 1b 0e 11 94 d4 f9 10 0d 18 48 b7 af da 5d 59 bf cd e5 bc b0 21 a8 58 eb 14 e8 13 8a ad 69 39 70 95 91 53 5e 9c 3c 53 77 15 3a c2 06 5b 13 df f5 40 38 26 56 14 e7 0f 84 ab b3 1d f6 b0 c6 b0 1e 68 5b 70 93 28 05 0a c5 2d 69 e5 88 99 b6 9d 02 12 80 47 d5 fd e3 11 cf 82 2a 3f eb dc db fe 5c fc a9 e2 24 96 58 84 2f 39 9b 65 8f 07 dd 00 93 9f 17 44 40 e1 28 66 c5 5f 99 d8 45 16 96 7b c9 61 11 f8 90 18 95 d1 97 26 05 44 ba e3 e1 73 99 ed c0 24 97 e5 6a b7 c4 f3 fd 87 5e a7 4e e8 38 35 4c 6d a6 66 fc 51 8e 31 64 b2 44 71 3d 2b d0 e8 b3 0f 9c d0 a8 c5 ef 3f d2 cb a2 57 73 4c d8 1a 15 1a fc 0c 29 05 4e 74 a2 f7 21 12 c6 a2 54 cf db 59 8a c3 ce ef 8f 8f 35 ba a5 0f 93 8d b2 29 5f f3 4d 04 fb 9b 74 85 41 36 3a d8 5a 8f 41 |
Deleted entries
| Key | Name | Type | Value |
|---|---|---|---|
| HKLM\SYSTEM\ControlSet001\Services\kmixer\Enum | 0 | REG_SZ | SW\{b7eafdc0-a680-11d0-96d8-00aa0051e51d}\{9B365890-165F-11D0-A195-0020AFD156E4} |
| HKLM\SYSTEM\CurrentControlSet\Services\kmixer\Enum | 0 | REG_SZ | SW\{b7eafdc0-a680-11d0-96d8-00aa0051e51d}\{9B365890-165F-11D0-A195-0020AFD156E4} |
Modified entries
| Key | Name | Type | Prev. value | New value |
|---|---|---|---|---|
| HKLM\SYSTEM\ControlSet001\Services\kmixer\Enum | Count | REG_DWORD | 0x00000001 | 0x00000000 |
| HKLM\SYSTEM\ControlSet001\Services\kmixer\Enum | NextInstance | REG_DWORD | 0x00000001 | 0x00000000 |
| HKLM\SYSTEM\CurrentControlSet\Services\kmixer\Enum | Count | REG_DWORD | 0x00000001 | 0x00000000 |
| HKLM\SYSTEM\CurrentControlSet\Services\kmixer\Enum | NextInstance | REG_DWORD | 0x00000001 | 0x00000000 |
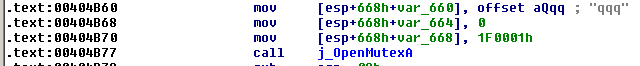
Mutexes
The malware creates following mutex: qqq
Network indicators
Contacted domains
- semaa.no-ip.biz
Encrypted payloads
Encrypted payloads are regularly sent to semaa.no-ip.biz on port 81/tcp:
00000000 b2 00 fa 00 e2 2d d6 67 cc 44 a2 c8 8c bf b2 4b .....-.g .D.....K
00000010 d5 e4 9c 8a f2 91 97 52 77 61 41 ac 34 65 3f 3e .......R waA.4e?>
00000020 16 2c 84 1e fc c1 c8 df 7c f9 c4 f3 1f b3 e2 67 .,...... |......g
00000030 82 cd 52 17 5a 16 73 81 67 ee ac a9 fd 8c 2f 6a ..R.Z.s. g...../j
00000040 1c e5 71 39 23 64 6f 6c df db a6 19 67 e6 db b8 ..q9#dol ....g...
00000050 51 d3 05 0e 0c 02 ce 9a 3a f2 4e 67 5f 9b f7 71 Q....... :.Ng_..q
00000060 21 ae 70 cc 31 8f 74 8b ef ab f9 7b 8f 5c 5b 14 !.p.1.t. ...{.\[.
00000070 3b 94 a0 9c ab 14 17 2f 47 74 6b 45 81 25 10 6f ;....../ GtkE.%.o
00000080 90 b1 0e e7 53 31 ef bd e5 72 c5 53 eb b3 5f 38 ....S1.. .r.S.._8
00000090 07 7c 6b 53 0d 7a 2f a8 6b e6 4c e0 f5 8a b8 a8 .|kS.z/. k.L.....
000000A0 bd d0 a3 ce 0d 12 e7 4d 7f 4d b9 35 6e 10 fd 5e .......M .M.5n..^
000000B0 37 b0 ea ec e7 4e 7....N
Static analysis
Sections
Name VirtAddr VirtSize RawSize Entropy ------------------------------------------------------------ .text 0x1000 0x773c 0x7800 6.387610 .data 0x9000 0x11b0 0x1200 7.547794 .rdata 0xb000 0xf20 0x1000 5.051954 .bss 0xc000 0x57e4 0x0 0.000000 .idata 0x12000 0x810 0xa00 4.399176 .rsrc 0x13000 0x8750 0x8800 7.917358
Resources
Name RVA Size Lang Sublang Type -------------------------------------------------------------------------------- RT_ICON 0x13100 0x777d LANG_NEUTRAL SUBLANG_NEUTRAL data RT_ICON 0x1a880 0xf LANG_NEUTRAL SUBLANG_NEUTRAL data RT_ICON 0x1a890 0xea8 LANG_NEUTRAL SUBLANG_NEUTRAL data RT_GROUP_ICON 0x1b738 0x14 LANG_NEUTRAL SUBLANG_NEUTRAL MS Windows icon resource - 1 icon
IAT
Strings
1+P@
XX+Z
X8+Z
X[^_
;MZt
0[^_
Y[^_
5adoy
\[^_
\[^_
<[^_
,[^_
,[^_
TEMP
TEMPf
TEMP
TEMPf
%4"A
%("A
%8"A
% "A
%$"A
,[^_
t6~
,[^_
,[^_
,[^_
<[^_
<[^_
,[^_
,[^_
}$;] t-
,[^_
,[^_
,[^_
$|c@
@DCUNG
t'Bt<
t3Bt6
$ t@
< tT< tP
Y[^]
8Pu#
<[^_
%d"A
%p"A
%x"A
%t"A
%T"A
%P"A
%@"A
%<"A
%L"A
%H"A
%0"A
%,"A
%X"A
%D"A
%?/?!
"o;h(Y
T*_}x:
j Bz
u\B&
y7bT
Ab61
T<*2
a.z9
DGt2
&5 M{
yM;-
jMG\^
C?9z
bcKU
!+g\
"%-U^7
PaH?
dv&4
wj-K
.n\
g&H`
~8lI
d^AE
;]>r
^(O=
W1O g_?
*,]I
Fv\;
Eub'z
\j#M
SRqDIK
_maz
mn`I:T`H
{OJW
z(~c
5_
=;&o
~?Pa w
WFgO
(>nH&p
gTzu
|k .T
B=!&|
!\1c
libgcj_s.dll
_Jv_RegisterClasses
Mars
UIIaaa12areplcervariablsse
5UIreplcervariablsse
OOIefwreplcervariablsse
IOO6replcervariablsse
IOreplcervariablsse
OO4s4replcervariablsse
Oreplcervariablsse
Ys3s3replcervariablsse
Y3replcervariablsse
Ys2s2replcervariablsse
Y4replcervariablsse
Yaaa12areplcervariablsse
Y5replcervariablsse
Yefwreplcervariablsse
Y6replcervariablsse
UYreplcervariablsse
Ureplcervariablsse
Js4s4replcervariablsse
Jreplcervariablsse
FRs3s3replcervariablsse
SDF3replcervariablsse
FSFs2s2replcervariablsse
SDFS4replcervariablsse
FDSaaa12areplcervariablsse
SDF5replcervariablsse
DFefwreplcervariablsse
6SFDreplcervariablsse
sqsreplcervariablsse
qsreplcervariablsse
qs4s4replcervariablsse
sqw3s3replcervariablsse
qw3replcervariablsse
wqs2s2replcervariablsse
qw4replcervariablsse
wqaaa12areplcervariablsse
qw5replcervariablsse
ewqfwreplcervariablsse
qw6replcervariablsse
wqreplcervariablsse
qwreplcervariablsse
des4s4replcervariablsse
aq1replcervariablsse
1bs3s3replcervariablsse
1a3replcervariablsse
1bs2s2replcervariablsse
1a4replcervariablsse
1baaa12areplcervariablsse
1a1b5replcervariablsse
1befwreplcervariablsse
1a6replcervariablsse
1breplcervariablsse
1areplcervariablsse
s4s4replcervariablsse
replcervariablsse
s3s3replcervariablsse
3replcervariablsse
s2s2replcervariablsse
4replcervariablsse
aaa12areplcervariablsse
5replcervariablsse
efwreplcervariablsse
6replcervariablsse
DEPACKEND
ERROR
%.2x
ee250412268cbd418c02a0fce843a69c
failed compatibility
Expected: %s
Got: %s
windir
services.exe
SOFTWARE\Microsoft\Windows\CurrentVersion\Run\
msmmsgr
cmd /c REG ADD HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run /v msmmsgr /t REG_SZ /d
ctfmon
cmd /c REG ADD HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run /v ctfmon /t REG_SZ /d
CreateProcessA
KERNEL32
NtUnmapViewOfSection
NtSetContextThread
VirtualAllocEx
NTDLL
GetThreadContext
NtWriteVirtualMemory
ResumeThread
tModuleHandleA
VirtualProtect
GetModuleFileNameA
CreateFileA
GlobalAlloc
GlobalFree
ReadFile
GetFileSize
CloseHandle
IsDebuggerPresent
FiLe encrypted successfully !
File access error :(
Invalid PE file !
Not enough memory :(
Files with a filesize of 0 aren't allowed !
There's no room for a new section :(
Too many sections !
Too much ImageImportDescriptors !
KeRnEl32.dLl
LoadLibraryA
GetProcAddress
sdS@
std::exception
std::bad_exception
__gnu_cxx::__concurrence_lock_error
__gnu_cxx::__concurrence_unlock_error
pure virtual method called
std::bad_alloc
../../runtime/pseudo-reloc.c
VirtualQuery (addr, &b, sizeof(b))
../../../../gcc-4.4.1/libgcc/../gcc/config/i386/cygming-shared-data.c
0 && "Couldn't retrieve name of GCClib shared data atom"
ret->size == sizeof(__cygming_shared) && "GCClib shared data size mismatch"
0 && "Couldn't add GCClib shared data atom"
-GCCLIBCYGMING-EH-TDM1-SJLJ-GTHR-MINGW32
N10__cxxabiv115__forced_unwindE
N10__cxxabiv117__class_type_infoE
N10__cxxabiv119__foreign_exceptionE
N10__cxxabiv120__si_class_type_infoE
N9__gnu_cxx24__concurrence_lock_errorE
N9__gnu_cxx26__concurrence_unlock_errorE
St13bad_exception
St9bad_alloc
St9exception
St9type_info
RegCloseKey
RegOpenKeyExA
RegQueryValueExA
AddAtomA
CloseHandle
CopyFileA
CreateMutexA
CreateProcessA
CreateSemaphoreA
ExitProcess
FindAtomA
FindResourceA
GetAtomNameA
GetCommandLineA
GetCurrentThreadId
GetLastError
GetModuleFileNameA
GetModuleHandleA
GetProcAddress
GetStartupInfoA
GetTickCount
GlobalAlloc
GlobalFree
InterlockedDecrement
InterlockedIncrement
LoadResource
LockResource
OpenMutexA
ReleaseSemaphore
SetLastError
SetUnhandledExceptionFilter
SizeofResource
Sleep
TlsAlloc
TlsFree
TlsGetValue
TlsSetValue
VirtualProtect
VirtualQuery
WaitForSingleObject
_write
__getmainargs
__p__environ
__p__fmode
__set_app_type
_assert
_cexit
_iob
_onexit
_setmode
abort
atexit
free
getenv
malloc
memcpy
memmove
printf
puts
remove
signal
sprintf
strcat
strcmp
strcpy
strncpy
GetActiveWindow
MessageBoxA
ADVAPI32.DLL
KERNEL32.dll
msvcrt.dll
msvcrt.dll
USER32.dll
@}3y
RWaf
4o i
HFw,
}SX"0K
wp+x
>|Fui
1cB1t"0
}c=g
Ap~rO
[S^HN
o-SMs
|SNj
z%t
HQzpH
.sCTA
|.?iI
.*aac
/5"Gz
V[d_4W
N7'=
xsx9
r$hY6
XcR+N
?q#3
Kf77
v,iF]
m>a1
kSi
"N,u
l%Vc
RyT'
rr~8
puj.%
Z6.)
n)J3*
!OUcK
mU9<i
6nuH
y_z\k:<q
x>\jn
[=HmJ
`~{C
l-RD
5Wzd
tN]Ev
mm|o
mn9IN
_T( a"n
>Z]
_Oi /
|n+;
b;$3
'dNBZ
I-):
K^|\
L_*@<
5}Rz
qntY
CH:^
aiIGH
sTs~
/X=~T
,bkI
g "(
EyMD
{DfL
L{Jo
aRgL3
$v+\
Lh_Pu
.FV`
` J
Rl#0
2j|$,
[`7Ra
`:0N
R(l2%
Tn"O
~+##
@a2f
n2AB
,Y S
o0{z
klfPSp
Yb/!
<~q:
%sn[
\'ci
&n}ot
jbHd
N`'-
p.U\
t}Y*
zhsi
&IsM
w7&5X
f]v4,I
0b?p
'6V}
2wm}
P/C|
Ag7W
< p_
7mVQ#
1+\?
S!_>L
}#:S
h&s<
@?W]x)
1C^N
gOx}
y6]Qs
Lzb_
- h3
IL.x
@C0H
r7cS
Uy?q
9x{s
}jis
RW aW
R13'\
H)o[:f
k5wa
,3|+L
iAx8A
jWV#
G>HY
,hgN}
Aw7%
6EKp
6~CW
0^rk
2{9
!]RW
S4^]
,Xc9
F`p?
Ol.n
O4=u
BB}'V
"?IE
"M@V~
Y!Y7
aEh'U
g)C;
}u9U
`W'F
_<Y%
cdHKF
$Oh4
-rF2
%9I-
7GdP
_Ym`L.0^
U$T.
iP{%
.#8$Gs
3tCQZ)Yi
8Fv%
9b8~
cJLk
Ovs`
mXe#*
>p[:F
`CKV#
8eM(<
b5rhe
%@|+AC$=
[':%l
BOU^O
|R_ Z
0P:/p
CWwN
F?\B
/mJ1F
c:f`w+
,z41:
YV3-
ceIzP
o\lCv
6%t[
HKE~~
*G`I
ybrMwy
3u&?
Up\9N
eZ?
d%]>
us4h)
,Nd+
qP%?
zly~
wV)3
Z<[5_
@-bN
*m_EwY
}J_d
]c;vz
1A_'_A[
wd_[
/Z>G
`lEEd&
1_.xV
gZmz
\C)1o
LME8n4?
|ta;XJi
`~+s
r8ai
H%M|
9L]8
XF[H
1#GJ{
8d#6<
iM&|
*U/|v>
xmMY
zd=F,
?'no
%eb)
@DDa
&91#[
@|IB
|8nO
]wb&
'w5{
+iS=P
0N8~X
:K[E
%8YR
FM2Xizp\e
_()f
zd9t
#^x#X
={5i
D0z,
8wd\`
[)M}Dfar
'7d(
N5dh
=\V5
U|ZR
cey~
)Ej@
Fq1f
'O81
,2ol
]:i|
=T"41
If@s
{Mxe
',K2K
AnMZK/4
6Gc>
$Z!(
(ZQC#
cg<&+u
ky~.
[7h?rV
%edjws
L)Oh
EGOoW
LaPL
@T-;
4,>2
su*_
$K^b
1P_=@
ZkA?
2*cm
.~AkW
z.%v
u6O@
~wlE&
v@`G
jRq`
.\Y6
Z0ca.ua)
{Jd/
iV/Y
"owvS
<>@B}0A
W,fx
<{Q
H&?#`
&`[M
|zP(d
QT R{
.9%}
QdeR
R?uV
}P@`
w8L#
]Ld4
hxm<
+~Mr
[{89
z8-[F
Cd%y
0V|Zd
DoC'
35Ld^
/ 99>8yzz
Yd@-D
hn$Y
z3Y;
e2|Pzn
{>^}
~0 kM
F{9O
j^J
+&M4X
Yi!(a1
y/^}!
B`s=
LlSa
cv~
2TWOIy
qA ?5
zfcp
7YEo
J:!8
}gY.
s_M>
8$8B
!9%9
J]-o
97P @c4-
Nc(L3
:Ar,n
ZLTM
7]-
qh<hj
?0(C6
^Y[r
E,j)
;PdZJ
rlad
#,7@
*ZCTc
j^P-o@B,^
w^af
0&|A
^U-.
(azSxv
c*+h
Lc A
~[`~T
g+kq}
:lKj
jr<a
L<*]%
W77A
C#[/>iiD>8!#7
SSSSSSSS
WU'%]469=EFHJNl0#A
!d"(.469=EFHJMTr
$(.469=EFHJ
$(.469=EFM
$(.469=ET
P!AW
$(.469F
$(.46J
fm,&
%53,&
/953,&
]:953,&
XYYYYO#
i=:953,&H
d*g
Ysssssss
i=;:953,M
qqqqqqq)A
m:::::::R
svvvvvvvgA
]:::::::M
B$1_`ajbgA
^::::::;M
K[d[
$(.469+A
)::::EMT
$(.46%A
`=JS
$(]#
R:953,&
=:953,&
TFB=:953,&
RHEB=:953,&
HEB=:953,&"\f
xgsTMJ
HEB=:953-\2
nNMJ
HEB=:`^[@
8nDDbih/[g
x!!ff
?[8?GOQY
0c%%\\))8?GlQV
lc%%\\))dd++ee//>nl
ed))dd++ee///^^^O
{{]^///^^^^Q
SMJJ
}zwmmhvLHFFHJMZ
YYYY
}}}yyyti=BF
JMRS
}}}yyytt
JMRS
}}}yyyttp
JMRT
}}}yyyttpD
OMRT
}}}yyyttppGW
luunniiDu
Comments
Keywords: NGRBot qqq Bifrost bcc86c024f6bd004772c4bef39249e2c