Bypass-proxies-firewalls
Introduction
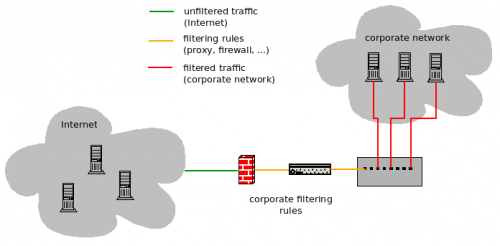
What are proxies and firewalls?
Below is the architecture you will face in most cases in your company:
Why proxies and firewalls?
Proxies and firewalls have different objectives.
The firewall:
- Ensures that only the authorized protocols go through the network (e.g. FTP, SSH, ... could be blocked)
- Can split/define the networks (e.g. on one side the corporate network, and the DMZ on the other side)
On the other hand, the proxy:
- Prevents from downloading unauthorized (illegitimate) content or from browsing unauthorized sites (blacklists, string pattern, ...)
- Controlled/limited freedom on the internet
Why bypassing proxies and firewalls
- Bypass organization's restrictions or censored networks
- Penetration-testing
- Share tools over the network, that are considered as non-authorized/unclean
- Protect your privacy
Bypass methods
Proxify the traffic
Proxy (HTTP, Socks)
Web proxies
Lots of web proxies on the internet:
- hidemyass.com
- fetch4.me
- surf-web-safely.com
- open-surf.com
- freesurfproxy.org
- open-browser.com
- newipnow.com
- proxify.com
- proxeasy.com
- proxy-plus.com
- totalnetprivacy.com
- ...
Use Content Distribution Networks
- Coral Content Distribution Network is a peer-to-peer content distribution network. To bypass a proxy, add ".nyud.net" after the domain (e.g. http://foo.com/bar/ becomes http://foo.com.nyud.net/bar/).
Tunneling
Tunneling consists of encapsulating a protocol in another one (e.g. encapsulation of a non initially authorized protocol in another one that is authorized).
The special case of HTTPS (HTTP over SSL) could be considered as tunneling in a way. Indeed, it can enable to bypass proxy rules.


Thank you for your comprehension.
Encryption
- Encryption can enable to bypass a proxy / firewall and is quite effective (e.g. PGP encryption)
Archives
- Attachments in a mail can be checked and purified by firewalls
- Ways to bypass: put the file in one or more archives (jar, arj, cab, 7z)
- All gears don't handle attachments the same way; compressing the attachment may be a solution to bypass.
- For most of gears, default politic for out of the limits values is "PASS". Following table shows an example of implementation for archives:
| Parameter | Max. value | Default val. |
|---|---|---|
| Max. number of layers | 16 | |
| Individual file size (archive) | 100MB | 10MB |
| Uncompressed file size | 500MB | |
| Num. of files in archive | 10,000 |
Content-Range header
- Fragment file in multiple files
Data-URL
- Exploit non-checked tags (e.g. <img src="data:MIMEType..." />) enables to include an encoded file (e.g. base64).
Include files in PDF
- This method is less effective now (implemented in gears rules)
- See Metasploit module: embeddedFiles
XMLHttp Requests
- Used with chunk
- Data in XML format
Use your mobile as a modem
- Tethering
Spoofing
If the proxy supports authentication, it is probable that rules are conditioned by the user who authenticates. Spoofing this identity could enable to elevate your privileges.
Another filter could consists of detecting privileges with computer physical addresses (mac address) or worse, by IP addresses. Spoofing mac addresses could lead in this case to privileges elevation.
Take over a server in the DMZ
Taking over a server from the DMZ and use it as a proxy could enable to bypass corporate filtering rules.