Category:Penetration-testing/Active-Directory
Description

Thank you for your comprehension.
Enumeration
Using the credentials we obtained in a previous machine; sandra:Password1234!, we can attempt to enumerate Active Directory. We can achieve this using BloodHound. There is a python bloodhound injester, which can be found here. It can also be installed using pip: pip install bloodhound.
unknown@kali:/data/tmp$ python3 -m pip install --user bloodhound
unknown@kali:/data/tmp$ bloodhound-python \
-d megacorp.local \
-u sandra -p "Password1234!" \
-gc pathfinder.megacorp.local \
-c all -ns 10.10.10.30
INFO: Found AD domain: megacorp.local
INFO: Connecting to LDAP server: Pathfinder.MEGACORP.LOCAL
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: Pathfinder.MEGACORP.LOCAL
INFO: Found 5 users
INFO: Connecting to GC LDAP server: pathfinder.megacorp.local
INFO: Found 51 groups
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: Pathfinder.MEGACORP.LOCAL
INFO: Done in 00M 07S
The json files should now be in the working directory, ready to be imported into BloodHound.
unknown@kali:/data/tmp$ ls -l *.json -rw-r--r-- 1 unknown unknown 3222 Jun 13 18:27 computers.json -rw-r--r-- 1 unknown unknown 3243 Jun 13 18:27 domains.json -rw-r--r-- 1 unknown unknown 85362 Jun 13 18:27 groups.json -rw-r--r-- 1 unknown unknown 12521 Jun 13 18:27 users.json
Installing and Starting BloodHound
For more details about BloodHound, refer to this tutorial.
First, we need to install neo4j and BloodHound.
unknown@kali:/data/tmp$ sudo apt install neo4j bloodhound
Next, we need to configure the neo4j service. We can accomplish this by running the following command
unknown@kali:/data/tmp$ sudo neo4j console
You will be then prompted to change your password. Next, we start BloodHound
unknown@kali:/data/tmp$ bloodhound --no-sandbox
Ensure you have a connection to the database; indicated by a ✔️ symbol at the top of the three input fields. The default username is neo4j with the password previously set.
Opening BloodHound, we can drag and drop the .json files, and BloodHound will begin to analyze the data.
A better option is to zip all *.json files and drag the resulting zip to BloodHound to import all files in one shot.
unknown@kali:/data/tmp$ zip megacorp.zip *.json adding: computers.json (deflated 74%) adding: domains.json (deflated 85%) adding: groups.json (deflated 95%) adding: users.json (deflated 91%)
We can select various queries, of which some very useful ones are Shortest Paths to High value Targets and Find Principles with DCSync Rights.
Shortest Paths from Domain Users to High Value Targets
Find Principles with DCSync Rights
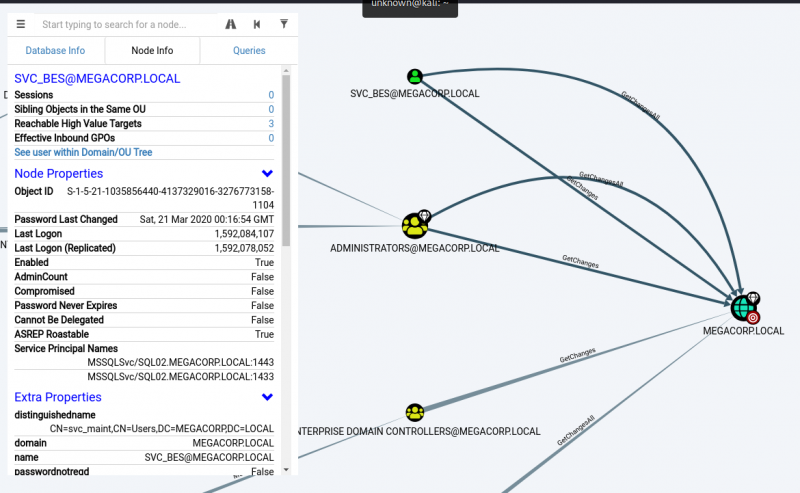
While the latter query returns this:
We can see that the svc_bes has GetChangesAll privileges to the domain. This means that the account has the ability to request replication data from the domain controller, and gain sensitive information such as user hashes.
Pages in category "Penetration-testing/Active-Directory"
The following 14 pages are in this category, out of 14 total.