Cobalt-Strike/Attacks/Packages/Windows-Executable
Jump to navigation
Jump to search
| You are here | Executable / Executable (S)
|
Attack
Description
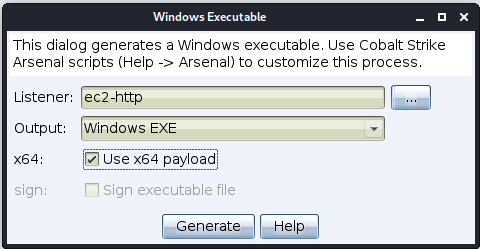
- Executable
- This package generates a Windows executable artifact that delivers a payload stager. This package gives you several output options.
- Executable (S)
- S = Stageless
- This package exports Beacon, without a stager, as an executable, service executable, 32-bit DLL, or 64-bit DLL.
- A payload artifact that does not use a stager is called a stageless artifact. This package also has a PowerShell option to export Beacon as a PowerShell script and a raw option to export Beacon as a blob of position independent code.