Cobalt-Strike/Attacks/Web-Drive-by/System-Profiler
Jump to navigation
Jump to search
| You are here | System Profiler
|
Description
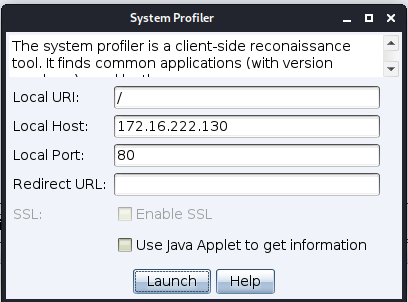
The System Profiler is a reconnaissance tool for the client-side attack process. This tool starts a local web-server and fingerprints any one who visits it. The System Profiler discovers the internal IP address of users behind a proxy along with several applications and their version information.
To start the System Profiler, go to Attacks -> Web Drive-by -> System Profiler.
Attack
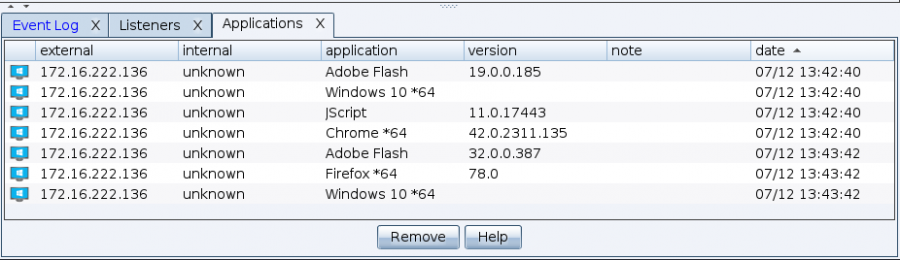
To view the results from the System Profiler, go to View -> Applications. Cobalt Strike will list all of the applications it discovered during the system profiling process.
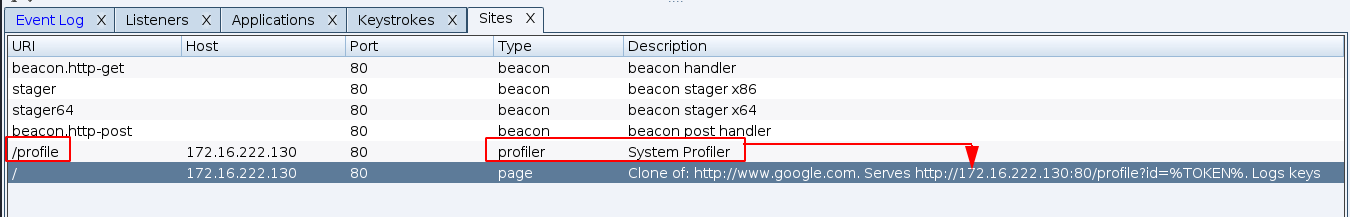
To make it even more plausible, combine it with the Clone Site attack: