D281c0a66c24d46b2412f5c80c77711a
Jump to navigation
Jump to search
Description
Idetification
| packed | unpacked | |
|---|---|---|
| MD5 | d281c0a66c24d46b2412f5c80c77711a | a5a5ed26f73d974ade21f9a215a124d5 |
| SHA1 | 805794a0260a2d9d64ed26e86e4cc4263da7a048 | 5a12fd9c34c6ee239aeafd2141d71cec84bac8cf |
| SHA256 | 018bb573ce4414e3db8078dc3b942c08d60ad9be5731adbdd2d43d548f187026 | 859082e7f389991bfabb050b37f3c398a67f6d92b950026fa7e65e6d7d05c9d6 |
| ssdeep | 768:CyYATzZ1dN7Vy/DHLCe5uehwKyA0eF5PmWLrgPtQrzC6dCj+cR0+JruK+RhT6u:CXixmTjuv9m1mWLcPtQ5K+cR0auK+b | 1536:CyMDtXdmkiZyIidcORB4VJazcRf7Q7S+0vhCCUeDk3urI:1MD5dmkQyIVOHm7h7tGF8I |
| imphash | e9589c23987a4ed41385f34bc7051ea1 | bc3e8ebed1995e5267a5199146b9eddb |
| File size | 47.4 KB ( 48540 bytes ) | 80.9 KB ( 82844 bytes ) |
| File type | Win32 EXE | Win32 EXE |
| Magic literal | PE32 executable for MS Windows (GUI) Intel 80386 32-bit | PE32 executable for MS Windows (GUI) Intel 80386 32-bit |
Antivirus detection
| Antivirus | Result (packed) | Result (unpacked) | Update |
|---|---|---|---|
| Ad-Aware | Dropped:Trojan.PWS.OnlineGames.KEDO | Dropped:Trojan.PWS.OnlineGames.KEDO | 20140221 |
| Agnitum | Trojan.PWS.OnLineGames!x3W9GkIuZjc | Trojan.PWS.OnLineGames!x3W9GkIuZjc | 20140221 |
| AhnLab-V3 | Trojan/Win32.Genome | Trojan/Win32.WOW | 20140221 |
| AntiVir | TR/Kazy.39008.8 | TR/Kazy.39008.8 | 20140221 |
| Antiy-AVL | Trojan[GameThief]/Win32.WOW | Trojan[GameThief]/Win32.WOW | 20140219 |
| Avast | Win32:Spyware-gen [Spy] | Win32:Spyware-gen [Spy] | 20140221 |
| AVG | Win32/Cryptor.dropper | PSW.OnlineGames | 20140221 |
| Baidu-International | Trojan.Win32.OnLineGames.Asia | 20140221 | |
| BitDefender | Dropped:Trojan.PWS.OnlineGames.KEDO | Dropped:Trojan.PWS.OnlineGames.KEDO | 20140221 |
| Bkav | W32.Clod2d2.Trojan.ba92 | 20140221 | |
| ByteHero | 20140221 | ||
| CAT-QuickHeal | TrojanPWS.OnLineGame.LP5 | TrojanPWS.OnLineGame.LP5 | 20140221 |
| ClamAV | W32.Trojan.Onlinegames-19 | 20140221 | |
| CMC | Trojan.Win32.GenK!O | Trojan.Win32.GenK!O | 20140220 |
| Commtouch | W32/Zuten.B.gen!Eldorado | W32/Zuten.B.gen!Eldorado | 20140221 |
| Comodo | TrojWare.Win32.Downloader.Agent.KAC | 20140221 | |
| DrWeb | Trojan.MulDrop4.17429 | Trojan.MulDrop4.17429 | 20140221 |
| Emsisoft | Dropped:Trojan.PWS.OnlineGames.KEDO (B) | Dropped:Trojan.PWS.OnlineGames.KEDO (B) | 20140221 |
| ESET-NOD32 | a variant of Win32/PSW.OnLineGames.QNW | a variant of Win32/PSW.OnLineGames.PXO | 20140221 |
| Fortinet | W32/Onlinegames.QNW!tr | W32/Onlinegames.QNW!tr | 20140221 |
| F-Prot | W32/Zuten.B.gen!Eldorado | W32/Zuten.B.gen!Eldorado | 20140221 |
| F-Secure | Dropped:Trojan.PWS.OnlineGames.KEDO | Dropped:Trojan.PWS.OnlineGames.KEDO | 20140221 |
| GData | Dropped:Trojan.PWS.OnlineGames.KEDO | Dropped:Trojan.PWS.OnlineGames.KEDO | 20140221 |
| Ikarus | Virus.Win32.Cryptor | Trojan-PWS.Win32.Kykymber | 20140221 |
| Jiangmin | TrojanDropper.Agent.ccaz | TrojanDropper.Agent.ccaz | 20140221 |
| K7AntiVirus | Password-Stealer ( 0040f0db1 ) | Password-Stealer ( 0040f0db1 ) | 20140221 |
| K7GW | Riskware ( 0040f0f51 ) | Password-Stealer ( 0040f0db1 ) | 20140220 |
| Kaspersky | Trojan-GameThief.Win32.WOW.sukt | Trojan-GameThief.Win32.WOW.sukt | 20140221 |
| Kingsoft | Win32.PSWTroj.WOW.su.(kcloud) | 20140221 | |
| Malwarebytes | Trojan.Agent | 20140221 | |
| McAfee | Artemis!D281C0A66C24 | PWS-OnlineGames.lx | 20140221 |
| McAfee-GW-Edition | Artemis!D281C0A66C24 | PWS-OnlineGames.lw | 20140221 |
| Microsoft | PWS:Win32/OnLineGames.LP | PWS:Win32/OnLineGames.LP | 20140221 |
| MicroWorld-eScan | Dropped:Trojan.PWS.OnlineGames.KEDO | Dropped:Trojan.PWS.OnlineGames.KEDO | 20140221 |
| NANO-Antivirus | Trojan.Win32.Siggen.bobzsj | Trojan.Win32.Siggen.bobzsj | 20140221 |
| Norman | Troj_Generic.ERTZM | Troj_Generic.ERTZM | 20140221 |
| nProtect | Trojan-PWS/W32.WebGame.48540.D | Dropped:Trojan.PWS.OnlineGames.KEDO | 20140221 |
| Panda | Adware/SecurityProtection | Trj/Genetic.gen | 20140221 |
| Qihoo-360 | 20140220 | ||
| Rising | PE:Trojan.Win32.Generic.14505F82!340811650 | PE:Stealer.Zuten!1.64CA | 20140221 |
| Sophos | Mal/PWS-AL | Mal/GamerPWS-G | 20140221 |
| SUPERAntiSpyware | Trojan.Agent/Gen-FakeAV[LZI] | 20140221 | |
| Symantec | Infostealer | 20140221 | |
| TheHacker | Posible_Worm32 | 20140220 | |
| TotalDefense | Win32/Gamepass.QEP!generic | Win32/Gamepass.QEP!generic | 20140221 |
| TrendMicro-HouseCall | TSPY_ONLINEG.NUR | TSPY_ONLINEG.NUR | 20140221 |
| TrendMicro | TROJ_GEN.R3OCCEM | TROJ_GEN.R3OCCEM | 20140221 |
| VBA32 | TrojanPSW.OnLineGames2 | Heur.Trojan.Hlux | 20140221 |
| VIPRE | Trojan-PWS.Win32.OnLineGames.lpk (v) | Trojan-PWS.Win32.OnLineGames.lpk (v) | 20140221 |
| ViRobot | Trojan.Win32.A.PSW-Wow.48540.B | 20140221 |
Defensive capabilities
Packer
The malware is packed with UPX.
$ ./upx -d /data/tmp/1.exe -o /data/tmp/1-unpacked.exe
Ultimate Packer for eXecutables
Copyright (C) 1996 - 2013
UPX 3.09 Markus Oberhumer, Laszlo Molnar & John Reiser Feb 18th 2013
File size Ratio Format Name
-------------------- ------ ----------- -----------
82844 <- 48540 58.59% win32/pe 1-unpacked.exe
Unpacked 1 file.
Dynamic Analysis
Network indicators

INCOMPLETE SECTION OR ARTICLE
This section/article is being written and is therefore not complete.
Thank you for your comprehension.
Thank you for your comprehension.
Files
Embedded PE
ResourceHacker and pescanner confirm the presence of 3 executable resources in the executable:
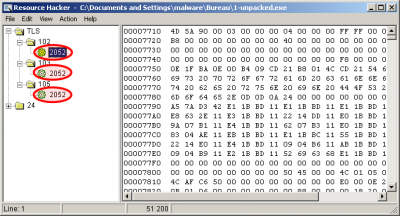
$ ./pescanner.py /data/tmp/1-unpacked.exe [SNIP] Signature scans ================================================================================ YARA: embedded_exe 0x4e => This program cannot be run in DOS mode 0x175e => This program cannot be run in DOS mode 0x4f5e => This program cannot be run in DOS mode 0x775e => This program cannot be run in DOS mode Resource entries ================================================================================ Name RVA Size Lang Sublang Type -------------------------------------------------------------------------------- TLS 0x20b110 0xc800 LANG_CHINESE SUBLANG_CHINESE_SIMPLIFIED PE32 executable (DLL) (GUI) Intel 80386, for MS Windows TLS 0x205110 0x3800 LANG_CHINESE SUBLANG_CHINESE_SIMPLIFIED PE32 executable (DLL) (GUI) Intel 80386, for MS Windows TLS 0x208910 0x2800 LANG_CHINESE SUBLANG_CHINESE_SIMPLIFIED PE32 executable (DLL) (GUI) Intel 80386, for MS Windows RT_MANIFEST 0x217910 0x292 LANG_CHINESE SUBLANG_CHINESE_SIMPLIFIED XML document, UTF-8 Unicode (with BOM) text, with CRLF line terminators [SNIP]
whhfd028.ocx
The following file is created:
| File name | whhfd028.ocx |
|---|---|
| Path | C:\WINDOWS\system32\whhfd028.ocx |
| MD5 | 90eb3aa19541b367388fd5f79ae5d36c |
| SHA1 | 7b80f7ea7a2dfe4baf43d1940e6f5f29af544427 |
| SHA256 | 9a3ad8dbda43a10f7856a0c22a8bdeab6d20cc5f81f72b08a182ae794c2b21da |
| ssdeep | 192:VvRzbkHGhz07lOgHs71Dbkkm6EsjJ5ihHbr:FRz8Ghz09Y1D3rhm |
| File size | 14.0 KB ( 14336 bytes ) |
| File type | Win32 DLL |
| Magic literal | PE32 executable for MS Windows (DLL) (GUI) Intel 80386 32-bit |
00178B47ce.dll
| MD5 | f1f49fb85ab029ad86c02ebecb892b12 |
|---|---|
| SHA1 | 664a602f8e843218c1158571714cd0adee1da939 |
| SHA256 | f8f3abcf8d43377b49d1edce23a667c9efd9cde86e9afee228e8c3b093013f13 |
| ssdeep | 192:cjbjEyfon/ZtXNfKpF+vXXxbI/86uyvdo:H+on/ZLIsfhbIl |
| imphash | 2ae87a1a4975ba37b3c2dc836fea332d |
| File size | 10.0 KB ( 10240 bytes ) |
| File type | Win32 DLL |
| Magic literal | PE32 executable for MS Windows (DLL) (GUI) Intel 80386 32-bit |
Registry keys
Following keys are created:
| HKLM\SYSTEM\ControlSet001\Control\Keyboard Layouts\E0200804 | |
|---|---|
| Ime File | WHHFD028.OCX |
| Layout Text | US |
| Layout File | kbdus.dll |
| HKLM\SYSTEM\CurrentControlSet\Control\Keyboard Layouts\E0200804 | |
|---|---|
| Ime File | WHHFD028.OCX |
| Layout Text | US |
| Layout File | kbdus.dll |
Static Analysis
Sections (unpacked version)
Name VirtAddr VirtSize RawSize Entropy -------------------------------------------------------------------------------- .text 0x1000 0x9e0 0xa00 5.971897 .bss 0x2000 0x2005f0 0x0 0.000000 .data 0x203000 0x514 0x600 4.316239 .CRT 0x204000 0x4 0x200 0.061163 .rsrc 0x205000 0x12ba8 0x12c00 6.332730
Strings (unpacked version)
SVWj@3
5h0`
5p0`
>SSj
_^[]
h<1`
FGKJ
_^[]
FGKJ
_^[]
QQS3
WSSj
5$0`
=l0`
PWVS
VhX$`
5`0`
X_^[
PRRh
SVWj@3
5x0`
jfPS
jgPS
jiPS
hx1`
hl1`
hP1`
X_^[
.ocx
whh27018
SeDebugPrivilege
kernel32
IsWow64Process
ConsentPromptBehaviorAdmin
SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
\system32\
CSOL
%s "%s" pfjaoidjglkajd %s
%s "%s" m3
%s "%s" pfjieaoidjglkajd
%08Xce.dll
whh98%s.ocx
whhfd%s.ocx
CloseHandle
ReadFile
CreateFileA
GetTickCount
WriteFile
FindClose
FindFirstFileA
GetWindowsDirectoryA
SetFilePointer
SetFileTime
GetFileTime
GetFileSize
GetModuleFileNameA
GetModuleHandleA
FreeResource
LoadResource
SizeofResource
FindResourceA
GetProcAddress
GetCurrentProcess
CreateProcessA
ExitProcess
KERNEL32.DLL
wsprintfA
USER32.dll
AdjustTokenPrivileges
LookupPrivilegeValueA
OpenProcessToken
RegCloseKey
RegSetValueExA
RegOpenKeyExA
ADVAPI32.dll
SHELL32.dll
sprintf
strchr
strlen
memcpy
MSVCRT.dll
WSOCK32.dll
!This program cannot be run in DOS mode.
Rich=
.text
`.bss
.data
.rsrc
@.reloc
VWj@
SVWj
X_^[
YYWS
t@~>
t<~:
VWj@Y3
h4A
Ph@4
Wj@3
h<A
SVWj@3
h@A
Ph@4
SVW3
hHA
VWj>Y3
=D@
j@Y3
hXA
H_^t
hXA
PhpA
5H@
%|@
%t@
% @
.ocx
IME File
%s%s
System\CurrentControlSet\Control\Keyboard Layouts\
Keyboard Layout\Preload
whhfd*
%02x*
win39%08x.dll
MSGO
Chinese( PRC )
SeDebugPrivilege
\system32\
CloseHandle
CopyFileA
GetTickCount
FindClose
FindNextFileA
FindFirstFileA
GetWindowsDirectoryA
GetProcAddress
LoadLibraryA
LocalAlloc
lstrcpyA
lstrcatA
TerminateProcess
GetCurrentProcess
GetModuleFileNameA
MultiByteToWideChar
GetTempPathA
KERNEL32.dll
ActivateKeyboardLayout
SystemParametersInfoA
GetKeyboardLayoutList
GetKeyboardLayout
RegisterClassExA
LoadCursorA
UnregisterClassA
MessageBoxA
USER32.dll
RegSetValueExA
RegCloseKey
RegQueryValueExA
RegOpenKeyA
AdjustTokenPrivileges
LookupPrivilegeValueA
OpenProcessToken
ADVAPI32.dll
SHELL32.dll
sprintf
memset
strcpy
strlen
strrchr
strcat
strchr
MSVCRT.dll
ImmIsIME
IMM32.dll
IMEHost.dll
CandWndProc
CompWndProc
IMEClearPubString
IMESetPubString
ImeConversionList
ImeEnumRegisterWord
ImeInquire
ImeRegisterWord
ImeUnregisterWord
StatusWndProc
UIWndProc
pfjieaoidjglkajd
ImeConfigure
ImeDestroy
ImeEscape
ImeGetRegisterWordStyle
ImeProcessKey
ImeSelect
ImeSetActiveContext
ImeSetCompositionString
ImeToAsciiEx
NotifyIME
1)101C1u1
1#2T2r2
2h3o3
4&4T4a4
8%838
8e:q:x:
0^0i0
0v2|2
!This program cannot be run in DOS mode.
Rich
.bss
.data
.reloc
.ocx
SeDebugPrivilege
WSPStartup
%02x*
win%08x.dll
VWj@
5$
SVWj/3
h@!
h@-
SVWj
h !
SVWj@3
h,!
SVW3
=\
h4!
Hu8V
=D
%t
%x
%|
%l
%d
%`
CloseHandle
CopyFileA
GetTickCount
FindClose
FindNextFileA
FindFirstFileA
GetWindowsDirectoryA
GetModuleFileNameA
LoadLibraryA
MultiByteToWideChar
GetProcAddress
GetLastError
GlobalAlloc
GlobalFree
LoadLibraryW
ExpandEnvironmentStringsW
GetModuleFileNameW
KERNEL32.dll
wsprintfW
USER32.dll
AdjustTokenPrivileges
LookupPrivilegeValueA
OpenProcessToken
ADVAPI32.dll
SHELL32.dll
sprintf
memset
strcpy
_except_handler3
strchr
swprintf
memcmp
wcscpy
memcpy
strcat
strstr
MSVCRT.dll
WSCWriteProviderOrder
WSCInstallProvider
WSCEnumProtocols
WSCGetProviderPath
WS2_32.dll
UuidCreate
RPCRT4.dll
LSP.dll
WSPStartup
D1H1Z1
2=2M2\2
6P7v7
7<8M8V8]8
9&9A9~9 :
;D<i<o<y<
<,=2=B=H=N=T=
!This program cannot be run in DOS mode.
Rich
.bss
.data
.CRT
.vmp0
`.reloc
SeDebugPrivilege
InternetCloseHandle
InternetReadFile
InternetOpenUrlA
InternetOpenA
WININET.dll
%02X
CSOL
%s_%d.jpg
WinInet
POST
HttpSendRequestEx
other
Type
Option
action=getRate
%02X%02X%02X%02X%02X%02X
CSOL_%s.tmp
%s%s
\\.\
ServiceName
SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkCards
cstrike-online.exe
hw.dll
nmconew.dll
jahCSOL27018_rel_regamle_%08d_
Counter-Strike Online
Value001
QQVh
t?Ht*Ht
:MZu
WVVV
=40
t$$VV
}"j(V
t$ j
t$$VV
580
SVWh
5<0
H_H^
u8!E
QQSVW3
Xf9E
HH_^][
FGKJ
_^[]
QQS3
WSSj
5t0
=p0
PWVS
<1&u
1|A;
t[BS
QZ^&
jxY+
WQhD:
FYYj
SVWj@3
=4
VWj@Y3
VPPPhSU
WSSj
SQVPW
SVWj
D$ hKk
O@/f!
SVWj?3
Phd
h<:
@_^[
VVVVh
t$Vh
QSV3
VVVVV
tOWVh
t.9u
SVWj?3
5<0
SSSSh
jPXSSj
tgSh
=4
=4
_u.9]
=
=
Yv;V
=T1
Y~!V
SVWj@3
5T1
=4
Y_^[
SVWj@3
j PSh
h ;
Yu&;
t'Ht
Hu7h
5d0
Yt>8
=X
PPPh
SVW3
u+WP
SVWj
h(
j@Y3
Ph$;
5@1
5T1
SVW3
QQSVW3
Vh4;
95P
F;5P
=\
5<0
=\
=\
=<
D$$P
%D
=<
D$$P
%L
Wj@3
h\;
Wj@3
hh;
Wj@3
hh;
SVWj@3
5t1
ht;
hl;
Ph@;
Ph@;
hd
Shd
VWj?
hd
h,!
Vh|!
%|#
5D"
VVVhv}
PPPhc}
5D"
5d0
VWhH<
=,<
h@<
h <
=L<
_^t-Ht"Ht
8MZu
FF9]
X_^[
s<j@
vTSP
QQS3
tXVWSP
SPVW
SVW
=(0
etAS
X_^[
YYt
[u&3
5x1
5d0
SWj>3
=(0
Yt&S
Yt&S
j@Y3
j@Y3
tAj\
%`0
% 1
%$1
%(1
%,1
%X1
AddVectoredExceptionHandler
InitializeCriticalSection
LeaveCriticalSection
EnterCriticalSection
Thread32Next
CloseHandle
SetThreadContext
GetThreadContext
OpenThread
GetCurrentProcessId
Thread32First
CreateToolhelp32Snapshot
VirtualProtect
GetProcessHeap
HeapAlloc
Process32Next
Process32First
GetFileSize
CreateFileA
GetModuleFileNameA
LoadLibraryA
GetModuleHandleA
WideCharToMultiByte
MultiByteToWideChar
GetProcAddress
FindClose
FindFirstFileA
OpenProcess
GetTempPathA
GetCurrentProcess
ReleaseMutex
GetLastError
CreateMutexA
Sleep
DeleteFileA
GetLocalTime
ReadFile
SetFilePointer
IsBadReadPtr
VirtualFree
VirtualAlloc
SetThreadPriority
CreateThread
GetTickCount
GetPrivateProfileStringA
ExitProcess
TerminateProcess
WritePrivateProfileStringA
DeviceIoControl
lstrcmpiA
SetUnhandledExceptionFilter
KERNEL32.dll
wsprintfA
GetWindow
PostMessageA
GetClassNameA
GetWindowTextA
GetDesktopWindow
FindWindowA
USER32.dll
GDI32.dll
AdjustTokenPrivileges
LookupPrivilegeValueA
OpenProcessToken
RegCloseKey
RegOpenKeyExA
RegQueryValueExA
RegEnumKeyExA
ADVAPI32.dll
SHELL32.dll
memset
memcpy
_except_handler3
strcat
strlen
_itoa
_stricmp
free
malloc
strchr
sprintf
strncpy
isspace
isalnum
atoi
strcpy
??3@YAXPAX@Z
??2@YAPAXI@Z
strstr
sscanf
_vsnprintf
rand
srand
strrchr
_strlwr
MSVCRT.dll
WSOCK32.dll
gdiplus.dll
_strupr
_strcmpi
Stolor.dll
pfjaoidjgfdjkj
pfjaoidjglkajd
t)at
$}ve]
GPh/
l$(Qf
${+`f
h;q:
l$ Yf
D$0R
|$Lf
D$$`
l$$C
WhfhW
T$(P
5Y6q
hz50b
59;
SThZ
ha=g
L$(f
#$A8
l]tV
@\l[
x4[I
/\l1
L!,
c-7X
StQYI
ihA'
i1X&
Xq+
$&~D
\-\.
-}@TW`h>
D$(Jh
#"'!S
DCge
h0A (d
A-L)
0s=wvS
FT! *6
@<;/+
h[;v
}\@jbEL
L]S#
D$@J
hp*~ d
wSl$
!l[_3>
P8K~DE
6]:O
na@)
f!gH:
kFED
D$<J
J->/J
}ZO2
<JRw
qH0z
_,N60H"/
UV&{.W
$\l1
],3|
gDc>+
65(Z
NG$M,
HRMm
{XQZLd
#.;(
-83T
NQc+
E#6w2
D*"\l
B|U!
ny/k
"\l0
WV4L
s'N;&
zj?)Q`
D$$J(g
Rn|X
~F$!X=ZS
/835
g x.,p
u~0l
1&CS
uu{K
4u82
) Ai
\l|w
o7sY
wrYP
I8V`{C
UG~-
D$<J
D$<5
AuU \
C8Kwr
A?8nRx
XrG6
a50V$W
2]Dw
\l}C'
Qyal
I|-V
>xYP
wvT"n
H%eLK?
D$ Jh
eamXS
x.l
(GG>
582|Y1M
5q9p
|<v<-
Pyq@r
]lcd
Ta9ox
hJ(5
H}-l}
0}|.
54vy,
Cw``
`ZZ8rc
+c9P
7TY!
\Z4C
$j(8
u3|6
NI>Y6
7KF@@
`k%2
D$ J
D$$7A
h@fE
e%P9
|,["
Q8)O\$
:-l>9
x&$
>|*@
.' Z
Ut]M
axa$
4?fA
^maXX
"IBE
61v.
$J(5
M}uT}
D$ J
@ueK
~q@d
k=COyz
D$$}
a]vq
*N<9P
-X<B
x1R<
l>lbh
yp[s
Ls$0
)a14#
L9K?z
y@^D
#xZ0
AIIj32
9QY0Y
Cdb/K
.@vD
yKbe
XNKW$
qXNOs$
&F&_!0X
8NGw$
yPzA
qhNFS$2
,odF
(NKf$
P{fd
S?YO
!J{vA
L@XU
Upfl
J^v+
;hugH
]/dQ
NC_$
[{fY
GE]Y,
s| ]6.n
OM!l
%?Lm}~
hpb~@
Dw>h
R}fC
=%=9=H=^=k=v=
>.>3>9>
>g?p?
0d0k0
102=2D2s2
2&353;3E3J3W3d3v3
334?4c4
6M6m7
7\8t8
535y5
9~9-:4:;:z:
?!?(?I?b?
L0b0v0
0$1[1o1
2@3L3X3d3r3
4%4,4[4t4{4
5E5k5w5
616]6
8,92:E:P:W:\:r:
>V>^>g>m>s>y>
? ?*?[?
2&3:3a3p3x3
5$5E5O5\5
5f6q6}6
747?7F7
8/848:8a8
:[:`:f:|:
;1;:;I;
<$<><L<R<]<p<z<
='=9=A=H=V=^=d=y=
>;>B>Q>^>e>y>
?0?E?Z?
0"1k1k2
3)3/3A3R3h3
3#4(4D4W4
4B5H5N5T5c5o5v5
6?6E6S6o6
6c7t7
8?8T8a8
:!:':2:::B:L:V:^:s:z:
;,;4;;;O;T;
<*<J<`<~<
="=(=.=4=:=@=F=L=
6+:7:
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<assembly xmlns="urn:schemas-microsoft-com:asm.v1" manifestVersion="1.0">
<assemblyIdentity version="1.0.0.0"
processorArchitecture="X86"
name="IsUserAdmin"
type="win32"/>
<description>Description of your application</description>
<!-- Identify the application security requirements. -->
<trustInfo xmlns="urn:schemas-microsoft-com:asm.v2">
<security>
<requestedPrivileges>
<requestedExecutionLevel
level="highestAvailable"
uiAccess="false"/>
</requestedPrivileges>
</security>
</trustInfo>
</assembly>
IAT (unpacked version)
|
ADVAPI32
|
KERNEL32
|
MSVCRT
|