Edf-fake-mails
Description
Several types of emails have been sent to people in France from people pretending to be *EDF*, a leading energy player in France. They try to convince users to click on malicious links.
This article analyzes these emails and give you advice about how to detect they are fake and dangerous emails.
Email 1
How does the email look like?
The first email looks like this:
De : Bleu ciel <[email protected]> Date : 6 septembre 2012 20:39 Objet : EDF: Votre prélèvement bancaire a été rejetée. À : "firstname lastname" <[email protected]> EDF-Bleu ciel Cher(e) Client(e) : N° F07180.3092.8300.0671 Votre paîement à été refusée par votre établissement bancaiire en raison d'un problème technique sur le systeme de prélêvement automatique, Pour eviter la pénalités de retard ,nous vous donnons la possibilité de pâyer en ligne votre systeme de prêlevement, Afin de régler votre prelevment automatique , www.particuliers-edf.com Lors d'êchec de regularisation de votre situation , nous procéderons à la suspênsion de fourniture d'energie ,Cette intervention vous sera facturée . Cette mesure peut encore être évitée si le réglement de la fâcture est assuré sous 48 heures directement auprès de notre service Merci de votre confiance . Cordialement, Votre conseiller EDF Bleu Ciel
First hints to notice (dramatically increases the likelihood of a malicious email):
- number of spelling mistakes in the mail (e.g. "paîement" instead of "paiement", "a été refusée" instead of "a été refusé", ...)
- Check that the reference (N° F07180.3092.8300.0671) does not correspond to your customer reference
First things to check:
- the sender seems correct (Bleu ciel <[email protected]>). However, it is not a sufficient reason to trust the email
- the domain (www.particuliers-edf.com) *seems* correct. However, we will analyze in the next section that it has nothing to do with an EDF related domain.
Analysis of the domain
Hosting information
The first thing to do in this case is to analyze the links. There is only one:
www.particuliers-edf.com
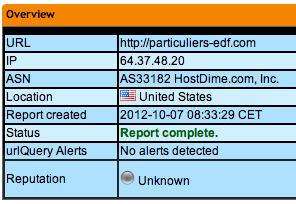
Let's use urlquery.net to analyze the domain:
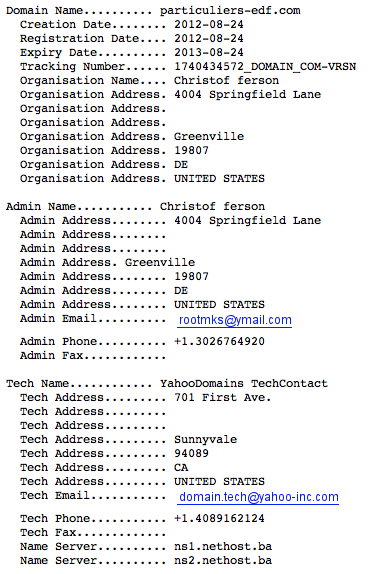
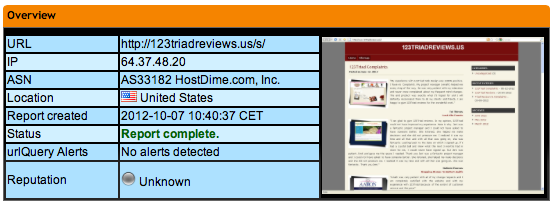
We immediately notice that the website is hosted in the US, which seems suspicious for such a famous french company. This is confirmed by the whois information:
Information provided by the website
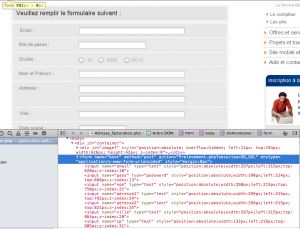
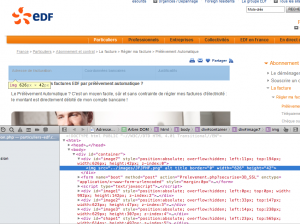
Now let's have a look at the website. It really looks like an EDF related website. However, the code analysis shows that everything is fake and that the website is only composed of a form. This one sends user inputs (personal data: email, password, name, postal address, phone number) to "Prelevement.php" hosted on the same domain.
All other content doesn't work (links are inactive, all content is made of pictures):
Analysis of the SSL certificate
One other hint is the fact that the entire site makes use of the HTTP protocol. Serious sites usually force the redirection to HTTPs (secured HTTP) to ensure the encryption of the communication when they deal with sensitive customers data, which is not the case here.
In addition:
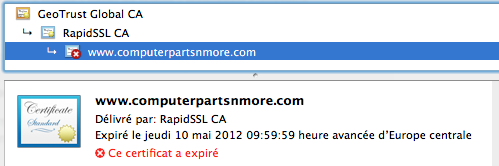
- the name that appears in the certificate (computerpartsnmore) is well known for scam attacks
- the certificate has expired:
Other email address used for the communication
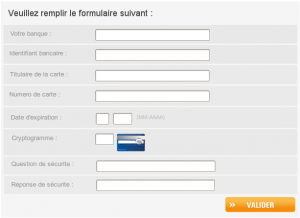
That said, nobody would trust this website because we have gathered enough information to know what this website is about. However, we have completed the form to know more about this website and people maintaining it. Once the first form completed, credit card related information are requested:
Once the form is fully completed, following confirmation mail is sent:
ACTIVATION DE VOTRE COMPTE? 7:50 AM EDF BLEUCIEL From: EDF BLEUCIEL ([email protected]) Sent: Sun 07/10/12 07:50 To: [email protected] Cher(e) lastname firstname Encore une fois, nous vous souhaitons la bienvenue chez EDF, et vous remercions de votre confiance. Attention : Votre dossier n'est pas encore validé. Pour bénéficier rapidement de nos services, merci de nous transmettre les documents suivants : [*] Une photocopie de votre pièce d'identité(recto et verso) [*] Un justificatif de domicile de moins de 3 mois [*] les deux face (recto et verso) de la carte bancaire avec , . laquelle vous avez procédé à l'inscription sur notre site Par email : [email protected] Vous avez des questions? Nos conseillers sont à votre écoute par email à l'adresse [email protected] DUPAS PIERRE Responsable Service client www.edf.com Rejoignez-nous sur Facebook EDF.com Cordialement, Votre conseiller EDF Bleu Ciel EDF SA au capital de 924 433 331 €, RCS Paris n° 552 081 317, siège social 22-30 av de Wagram 75382 Paris cedex 08. Copyright © EDF 2010
This time, the email is requesting additional information:
- A copy of the identity card
- Proof of residence
- A copy of the credit card
This information has to be sent to another email address using gmail.com (it has to be an email address the malicious team is able to access to):
[email protected].
Conclusions
The domain itself has nothing malicious (no exploit hosted on the website) and the attack is obviously a phishing attack which objective is to gather credit card information.
A lot of information are available to detect the attack. Please also refer to the final conclusions and best practices.
Also be informed that this attack is still working at the time of the analysis.
Email 2
How does the email look like?
De : Bleu ciel <[email protected]> Date : 21 août 2012 00:10 Objet : Avis de coupure : non reception de papiers À : "firstname.lastname" <[email protected]> Cher(e) EDF Client(e) : N° F07000.3012.9400.1332 Votre paîement à été refusée par votre établissement bancaîre en raison d'un problème technique sur le systeme de prélèvement automatique, Pour eviter la pénalités de retard ,nous vous donnons la possibilité de régler en ligne votre systeme de prelevement, Afin de régler votre prelevment automatique, cliquez ici Lors d'echec de regularisation de votre situation , nous procéderons à la suspension de fourniture d'energie ,Cette intervention vous sera fâcturée . Merci de votre confiance .
As for the previous email:
- the email seems to be sent from a correct email address (Bleu ciel <[email protected]>)
But you should immediately notice that:
- there are spelling mistakes
- the reference (F07000.3012.9400.1332) does not correspond to your customer reference
- the link points to 123triadreviews.us (put your mouse over the link without clicking it to reveal the domain)
Analysis of the domain
The analysis of the URL with UrlQuery.net shows that the domain is hosted in the US and doesn't look like an EDF related website:
This website is hosted on the same domain as particulars-edf.com (see first analysis):
Apart from this information, nothing leads to conclude that the website is malicious:
- none of the images contains malicious code: all scanned with VirusTotal
- none of the javascript is malicious
- the reputation of the website is clean: https://www.virustotal.com/url/744a81349d374e4d284a1e8188e57389acedf041e9a6fb1f94ea6e7e4461b8d8/analysis/1349606108/
- no post on the Internet indicates that this site is malicious
- Google safe browsing indicates that the website is clean: http://www.google.com/safebrowsing/diagnostic?site=123triadreviews.us
Hypothesis and conclusions
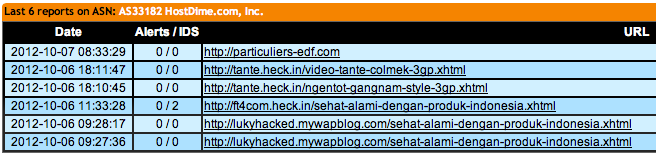
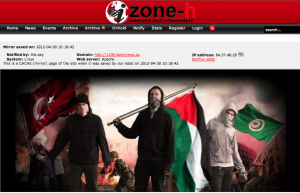
We can notice that the domain 123triadreviews.us has been hacked in the past (seen on zone-h.com):
As the domain does not look malicious and doesn't host any malicious content at the time of the analysis, one option is that the crackers team took over the website (they could have exploited a vulnerability) and uploaded malicious content. Once on the modified website, the malicious code is then executed by the browser. This attack is likely to exploit a vulnerability of unpatched browsers.
This attack is not working anymore.
Email 3
How does the mail look like?
De : BlueCiel <[email protected]> Date : 7 août 2012 06:52 Objet : avis de coupure : non reception de papiiers À : m <[email protected]> Cher(e) Cliient(e), Nous avons constatés un impayé sur votre dernière facture. La société EDF vous avise que le service d'énergie sera suspendu à compter du : 7 août pour redevance non payée. Cette mesure peut encore être évitée si le réglement de la facture est assuré sous 48 heures directement auprès de notre service Afin de régulariser votre situation veuillez vous refferez ci-dessous : << Accedez à votre compte >> Cordialement.
To be immediately noticed:
- the mail contains spelling mistakes
- the sender's email address is [email protected]
- the sender's name is "BlueCiel" instead of "Bleu Ciel"
- the link points to xtremenogales.com/edf
Analysis of the domain
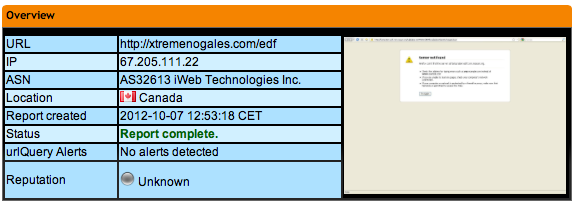
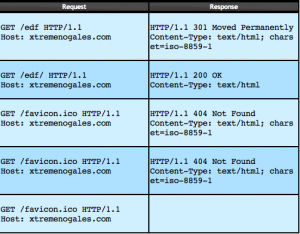
UrlQuery.net indicates that the domain is hosted in Canada and that the attack (/edf/) seems not to work (301 moved permanently) anymore:
The website seems clean:
- VirusTotal report: https://www.virustotal.com/url/95fd60dbd3478e9dc58c43baac16c15675ad9a0816f505a56bdabae43c3490cb/analysis/1349607926/
- URLQuery report: http://urlquery.net/report.php?id=218531
- McAfee site advisor: http://www.siteadvisor.com/sites/xtremenogales.com/summary/
- Google safe browsing: http://www.google.com/safebrowsing/diagnostic?site=xtremenogales.com
Also to notice: this domain (xtremenogales.com) has already been hacked in the past:
Hypothesis and conclusions
As for the previous case, it is likely that this website has been hacked by the crackers team who has modified it (uploaded malicious content in the /edf/ directory). As the content seems to have been withdrawn at the time of the analysis, no other information is available.
At the time of the analysis, it seems this the attack is not working anymore.
Conclusions and best practices
What such emails are about?
We have studied 3 cases that we can group into 2 types of attacks:
- scamming site (site asking for sensitive data that will be used by the crackers team)
- malicious websites (website that host malicious content trying to exploit vulnerabilities of unpatched browsers)
Such malicious mails often contain:
- code that will try to exploit a vulnerability of the client:
- mail clients (i.e. Thunderbird, Lotus Notes, ...)
- browsers (i.e. Google Chrome, Safari, Mozilla Firefox, Microsoft Internet Explorer, ...)
- links pointing to malicious domains:
- asking for sensitive data
- trying to exploit vulnerabilities of unpatched browsers
Best practices
Here are some best practices to avoid being trapped:
- Don't trust email, even those sent by your bank. It does not mean that you send them to trash but... analyze them first
- Analyze the sender's information: Name + email address
- if the mail contains attachments, always scan them with virustotal before opening them. Gmail will automatically scan attachments before delivering them, and can open them in Google docs to avoid the eventual code from being executed on your machine.
- Analyze the eventual links: put your mouse over the links to disclose the real domain!
- If you have any doubt regarding a domain, right click on it and select "copy link" from the contextual menu. Then paste it to URLQuery. It is a very useful site that will browse the link for you and show you how the link looks like, as well as provide you with useful information (hosting location, eventual security alarms, ...)
- Always have an updated browser:
- Update your browser when patches are available (e.g. Microsoft Windows updates, Mac Appstore, Linux updates, ...)
- Never trust third party updates. Some sites will popup a window claiming that your browser needs to be updated (e.g. Flash plugin, Java, ...). Don't trust them unless you absolutely know the reputation of the website.
- Never accept updates when connected to public hotspots. Wait being in a safe location (at home or at the office).
- If you have to provide sensitive data (e.g. credit card information), always check the certificate:
- is it outdated? If yes, don't provide any data and contact the company
- Is there a valid certificate? If the icon shows an invalid certificate or no certificate at all, never provide any sensitive data