Fiddler
Description
Fiddler is a free web debugging proxy that has many options and will be very convenient to analyze malware traffic. One of its feature is to perform MITM to decrypt SSL traffic.
Installation
User Interface
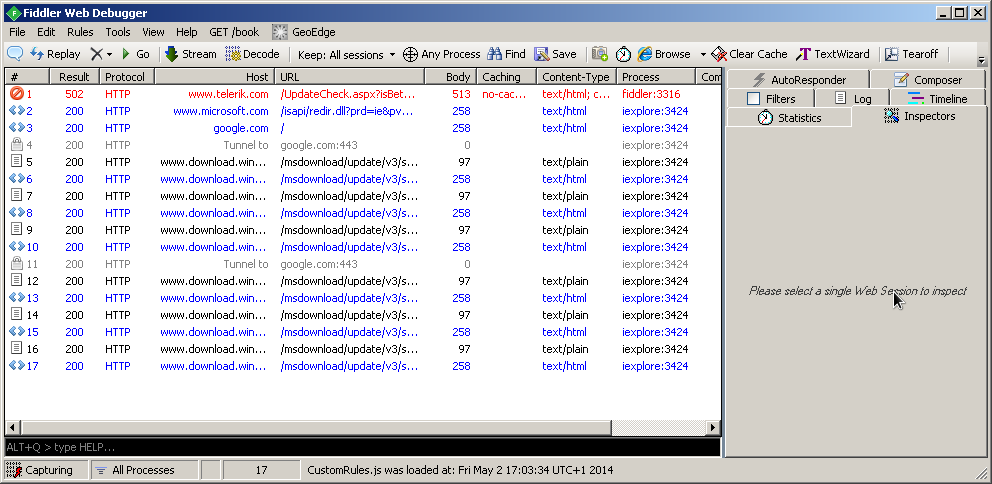
Web sessions window
Tabs
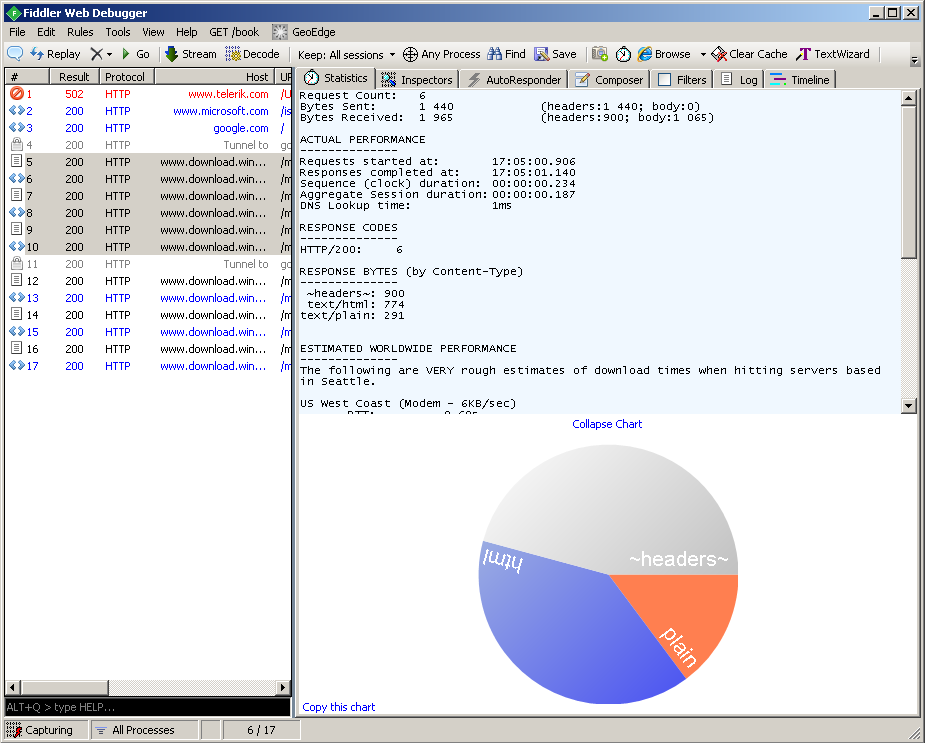
Statistics
Shows statistics on a selected session or a group of sessions.
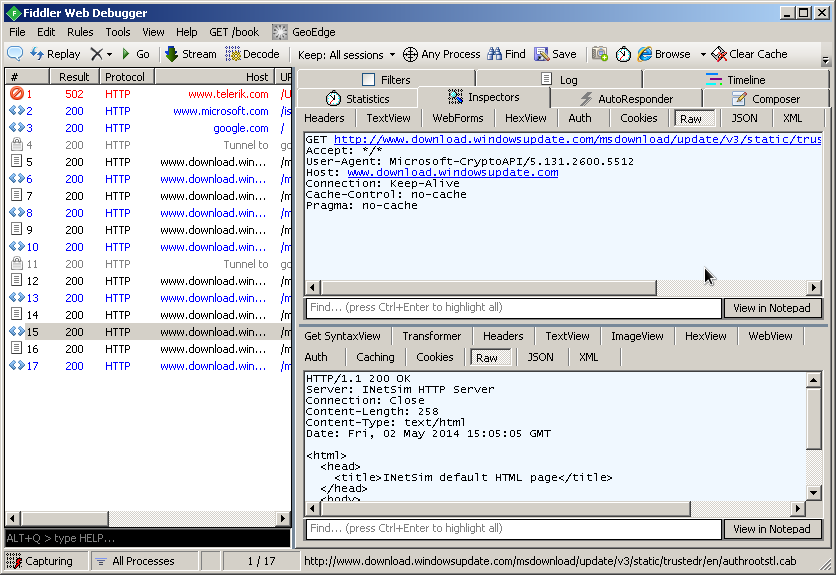
Session inspector
The session inspector shows the request and the response in different formats (Header, Raw, Hex, JSON, XML, ...). The response can even be rendered as image, web preview, highlighted syntax view, ...
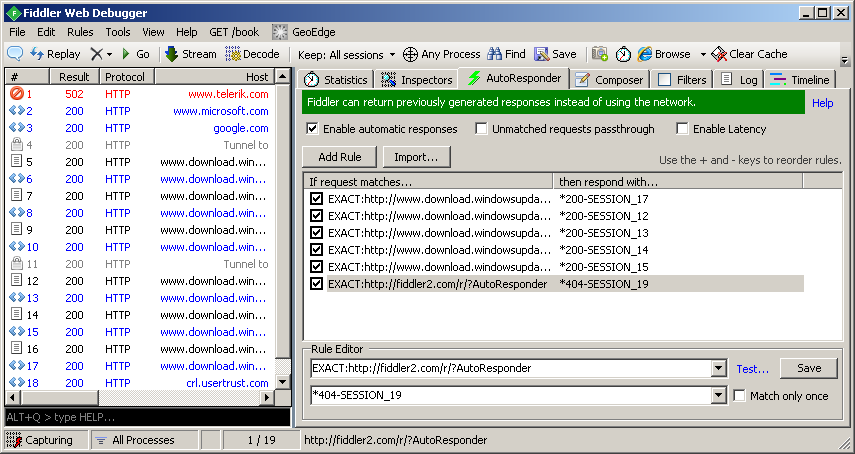
Auto Responder
Fiddler's AutoResponder tab allows you to return files from your local disk instead of transmitting the request to the server. For more information about rules, refer to the official documentation here: http://docs.telerik.com/fiddler/knowledgebase/autoresponder
Composer
The Composer enables to buid a request from scratch or from an existing web session (by dragging it to the composer window).
Filters
You can create filters to exclude some traffic from the capture.
Log
Fiddler logs window.
Timeline
Quick exec
QuickExec is a field that accepts several commands to control Fiddler from the Command Line (e.g. break on specific keywords or conditions, dump the sessions as zip file, ...).
For more information on available commands, go here: http://docs.telerik.com/fiddler/knowledgebase/quickexec/
Example: Decrypting malware HTTPS traffic
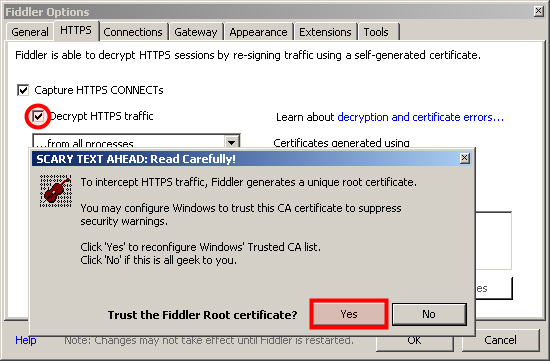
Prepare Fiddler to intercept and decrypt SSL traffic
First of all, you will need to prepare Fiddler to decrypt SSL traffic (Fiddler will perform Man In the Middle -- MITM). Go to Tools > Fiddler options, click on Decrypt SSL traffic and click on OK:
Emulate services
For this part, I have used REMnux with fakedns and INetSim running.
Run malware
It's time to run our malware and see what is in the SSL payloads:
Comments
Keywords: fiddler intercept network traffic MITM http https