Forensicscontest-puzzle8
Description
This post is the answer to the forensics contest, puzzle #8.
Joe’s WAP is beaconing. Based on the contents of the packet capture, what are the SSID and BSSID of his access point?
- BSSID: 00:23:69:61:00:d0
- SSID: Ment0rNet
$ tshark -n -R wlan -r evidence08.pcap |grep SSID 1 0.000000 00:23:69:61:00:d0 -> ff:ff:ff:ff:ff:ff 802.11 105 Beacon frame, SN=3583, FN=0, Flags=........, BI=100, SSID=Ment0rNet (...TRUNCATED...)
How long is the packet capture, from beginning to end (in SECONDS, please round to the nearest full second)?
Using nsm-console, or just the capinfos utility, we can easily answer this question:
$ capinfos -u evidence08.pcap File name: evidence08.pcap Capture duration: 414 seconds
Beware using the evidence08.pcap file and not the evidence08-dec.pcap (generated by airdecap-ng) since this latest provides us with different results:
$ capinfos -u evidence08-dec.pcap File name: evidence08-dec.pcap Capture duration: 405 seconds
The capture length is 414 seconds.
How many WEP-encrypted data frames are there total in the packet capture?
Here is a useful online resource to write the filters: http://www.wireshark.org/docs/dfref/w/wlan.html
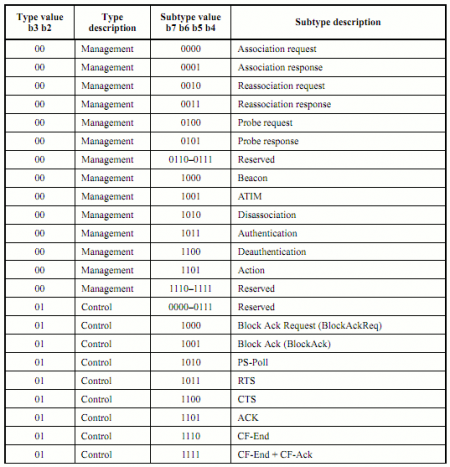
According to the IEEE 802.11 standard (page 62), to filter the data frames, the values of the frame control (FC) are:
- type: 10
- subtype: 0000
By combining the type and the subtype (wlan.fc.type_subtype), the binary value of 100000, converted in hexadecimal is: 0x20.
In addition, we also filter frames that are encrypted using WEP: wlan.fc.protected==1
At last, we filter on the appropriate BSSID: wlan.bssid == 00:23:69:61:00:d0
Combining the filters, here is the syntax:
$ tshark -r evidence08.pcap -R 'wlan.fc.type_subtype==0x20 && wlan.fc.protected==1 && wlan.bssid==00:23:69:61:00:d0' | wc -l 59274
There are 59274 WEP-encrypted data frames in our capture file.
Notice that using the statistics, tshark also provides the solution:
$ tshark -r evidence08.pcap -z io,phs [...TRUNCATED...] =================================================================== Protocol Hierarchy Statistics Filter: wlan frames:133068 bytes:6556285 wlan_mgt frames:15110 bytes:433527 data frames:59274 bytes:5526728 ===================================================================
How many *unique* WEP initialization vectors (IVs) are there TOTAL in the packet capture relating to Joe’s access point?
We first need to filter on the appropriate Access Point (AP):
wlan.bssid==00:23:69:61:00:d0
We also want to only keep frames that contain IVs:
wlan.wep.iv
To be able to count the number of frames, we must output the IVs by specifying it as a field:
-T fields -e wlan.wep.iv
The command is:
$ tshark -r evidence08.pcap -R 'wlan.bssid==00:23:69:61:00:d0 && wlan.wep.iv' -T fields -e wlan.wep.iv| sort -u |wc -l 29719
Joe's AP is generating 29719 unique WEP IVs during the capture.
What was the MAC address of the station executing the Layer 2 attacks?
We first crack the key with aircrack-ng:
$ aircrack-ng evidence08.pcap
We can then use airdecap-ng to generate an unencrypted capture file (evidence08-dec.pcap):
$ airdecap -w D0E59EB904 evidence08.pcap
The statistics are:
$ tshark -r evidence08-dec.pcap -z io,phs
[...TRUNCATED...]
===================================================================
Protocol Hierarchy Statistics
Filter:
eth frames:56692 bytes:3690010
ip frames:2868 bytes:1427722
udp frames:85 bytes:29395
http frames:59 bytes:21788
bootp frames:21 bytes:7182
dns frames:5 bytes:425
tcp frames:2783 bytes:1398327
http frames:904 bytes:1134807
image-gif frames:14 bytes:10204
tcp.segments frames:8 bytes:6592
malformed frames:1 bytes:1514
data-text-lines frames:3 bytes:3720
ipv6 frames:47 bytes:3654
icmpv6 frames:47 bytes:3654
arp frames:53777 bytes:2258634
===================================================================
We immediately notice that the majority of the traffic concerns the ARP protocol. By writting the appropriate filter, we can find what mac address is responsible of the traffic:
$ tshark -r evidence08-dec.pcap -R arp -T fields -e eth.src -e eth.dst | sort | uniq -c 12664 00:11:22:33:44:55 00:23:69:61:00:ce 2 00:11:22:33:44:55 ff:ff:ff:ff:ff:ff 1 00:23:69:61:00:ce 00:11:22:33:44:55 1 00:23:69:61:00:ce de:ad:be:ef:13:37 3 00:23:69:61:00:ce ff:ff:ff:ff:ff:ff 41104 1c:4b:d6:69:cd:07 ff:ff:ff:ff:ff:ff 2 de:ad:be:ef:13:37 ff:ff:ff:ff:ff:ff
The traffic looks like:
$ tshark -r evidence08-dec.pcap -R 'eth.src==1c:4b:d6:69:cd:07 && arp' | head -n 20 694 174.581146 1c:4b:d6:69:cd:07 -> ff:ff:ff:ff:ff:ff ARP 42 Who has 192.168.1.100? Tell 192.168.1.1 695 174.979009 1c:4b:d6:69:cd:07 -> ff:ff:ff:ff:ff:ff ARP 42 Who has 192.168.1.100? Tell 192.168.1.1 696 174.980033 1c:4b:d6:69:cd:07 -> ff:ff:ff:ff:ff:ff ARP 42 Who has 192.168.1.100? Tell 192.168.1.1 697 174.983103 1c:4b:d6:69:cd:07 -> ff:ff:ff:ff:ff:ff ARP 42 Who has 192.168.1.100? Tell 192.168.1.1 698 174.987200 1c:4b:d6:69:cd:07 -> ff:ff:ff:ff:ff:ff ARP 42 Who has 192.168.1.100? Tell 192.168.1.1 699 174.988185 1c:4b:d6:69:cd:07 -> ff:ff:ff:ff:ff:ff ARP 42 Who has 192.168.1.100? Tell 192.168.1.1 700 174.989207 1c:4b:d6:69:cd:07 -> ff:ff:ff:ff:ff:ff ARP 42 Who has 192.168.1.100? Tell 192.168.1.1 701 174.990785 1c:4b:d6:69:cd:07 -> ff:ff:ff:ff:ff:ff ARP 42 Who has 192.168.1.100? Tell 192.168.1.1 702 174.991810 1c:4b:d6:69:cd:07 -> ff:ff:ff:ff:ff:ff ARP 42 Who has 192.168.1.100? Tell 192.168.1.1 703 174.992256 1c:4b:d6:69:cd:07 -> ff:ff:ff:ff:ff:ff ARP 42 Who has 192.168.1.100? Tell 192.168.1.1 704 174.993305 1c:4b:d6:69:cd:07 -> ff:ff:ff:ff:ff:ff ARP 42 Who has 192.168.1.100? Tell 192.168.1.1 705 174.994879 1c:4b:d6:69:cd:07 -> ff:ff:ff:ff:ff:ff ARP 42 Who has 192.168.1.100? Tell 192.168.1.1 706 174.995391 1c:4b:d6:69:cd:07 -> ff:ff:ff:ff:ff:ff ARP 42 Who has 192.168.1.100? Tell 192.168.1.1 707 174.996375 1c:4b:d6:69:cd:07 -> ff:ff:ff:ff:ff:ff ARP 42 Who has 192.168.1.100? Tell 192.168.1.1 708 174.997439 1c:4b:d6:69:cd:07 -> ff:ff:ff:ff:ff:ff ARP 42 Who has 192.168.1.100? Tell 192.168.1.1 709 174.998425 1c:4b:d6:69:cd:07 -> ff:ff:ff:ff:ff:ff ARP 42 Who has 192.168.1.100? Tell 192.168.1.1 710 174.999487 1c:4b:d6:69:cd:07 -> ff:ff:ff:ff:ff:ff ARP 42 Who has 192.168.1.100? Tell 192.168.1.1 711 175.000472 1c:4b:d6:69:cd:07 -> ff:ff:ff:ff:ff:ff ARP 42 Who has 192.168.1.100? Tell 192.168.1.1 712 175.001537 1c:4b:d6:69:cd:07 -> ff:ff:ff:ff:ff:ff ARP 42 Who has 192.168.1.100? Tell 192.168.1.1 713 175.003544 1c:4b:d6:69:cd:07 -> ff:ff:ff:ff:ff:ff ARP 42 Who has 192.168.1.100? Tell 192.168.1.1
We can conclude that the mac address of the station making the layer 2 attacks is 1c:4b:d6:69:cd:07.
How many *unique* IVs were generated (relating to Joe’s access point)
By the attacker station?
We first need to filter on the appropriate AP:
wlan.bssid==00:23:69:61:00:d0
We also need to filter the frames that come from the attacker:
wlan.sa==1c:4b:d6:69:cd:07
To know the number of IVs generated by the attacker station:
$ tshark -r evidence08.pcap -R 'wlan.bssid==00:23:69:61:00:d0 && wlan.sa==1c:4b:d6:69:cd:07 && wlan.wep.iv' -T fields -e wlan.wep.iv| sort -u | wc -l 14133
The answer is 14133.
By all *other* stations combined?
$ tshark -r evidence08.pcap -R 'wlan.bssid==00:23:69:61:00:d0 && wlan.sa!=1c:4b:d6:69:cd:07 && wlan.wep.iv' -T fields -e wlan.wep.iv| sort -u | wc -l 15587
What was the WEP key of Joe’s WAP?
The aircrack-ng suite helps us decrypting the key:
$ aicrack-ng evidence08.pcap
Aircrack-ng 1.1
[00:00:00] Tested 587 keys (got 26805 IVs)
KB depth byte(vote)
0 3/ 4 D0(33536) BC(33024) 27(33024) 1F(33024) 7B(31744) 2F(31744) FF(31488) CA(30976) 96(30720) C9(30720) 69(30720) 6F(30720) DF(30464) E8(30464)
1 0/ 1 E5(38656) 82(33024) 0C(32256) 3C(32000) EB(31744) 42(31488) 8B(31232) 3D(31232) 8C(31232) 31(30976) 32(30976) 6A(30976) 07(30976) 58(30976)
2 0/ 5 9E(34048) 27(33792) 7A(32768) E9(32512) 8B(31744) C3(31744) D0(31488) 7B(31488) 2B(31488) 36(31488) BF(31232) E0(31232) 3D(30976) 4A(30720)
3 0/ 3 B9(35328) 57(35072) B1(34048) 7C(33024) 00(32768) 06(32512) CF(32256) 9C(31744) 09(31488) 3F(31232) 7F(31232) 47(31232) D6(31232) 2B(31232)
4 8/ 10 A9(31488) B9(31232) 10(31232) 95(30976) A5(30976) 7A(30976) 08(30720) E1(30720) C8(30720) 8B(30720) B2(30464) B3(30464) 87(30464) 52(30464)
KEY FOUND! [ D0:E5:9E:B9:04 ]
Decrypted correctly: 100% The key is D0E59EB904.
What were the administrative username and password of the targeted wireless access point?
List of tshark filters for HTTP: http://www.wireshark.org/docs/dfref/h/http.html
$ tshark -r evidence08-dec.pcap -R 'http.request && http.authbasic' -T fields -e http.authbasic | uniq admin:admin
Tshark is really helpful once more. We filter the HTTP requests (http.request) that contain a Base64 authentication (http.authbasic) and we display the content of the Base64 (-T fields -e http.authbasic). Notice that tshark automatically decodes the Base64:
- username: admin
- password: admin
With such credentials, no way that anyone accessing the LAN won't be able to administer the router ;-)
What was the WAP administrative passphrase changed to?
By filtering the HTTP requests (-R http.request) and displaying the details (-V) of the packets, it is easy to guess that the new passphrase is sent as a parameter in the URL (form GET method):
$ tshark -r evidence08-dec.pcap -V -R 'http.request' | grep -i pass SecurityMode=3&CipherType=1&PassPhrase=hahp0wnedJ00&GkuInterval=3600&layout=en