GreHack-2012/100-GrehAndroidMe-apk
Jump to navigation
Jump to search
| You are here | 100-GrehAndroidMe.apk
|
Description
CTF
GreHack CTF 2012 reverse engineering challenge (100 points).
Installation
mobisec@ubuntu:/opt/mobisec/Android/sdk/platform-tools$ ./adb -s emulator-5554 install /data/grehack/GrehAndroidMe.apk
994 KB/s (61622 bytes in 0.060s)
pkg: /data/local/tmp/GrehAndroidMe.apk
Success
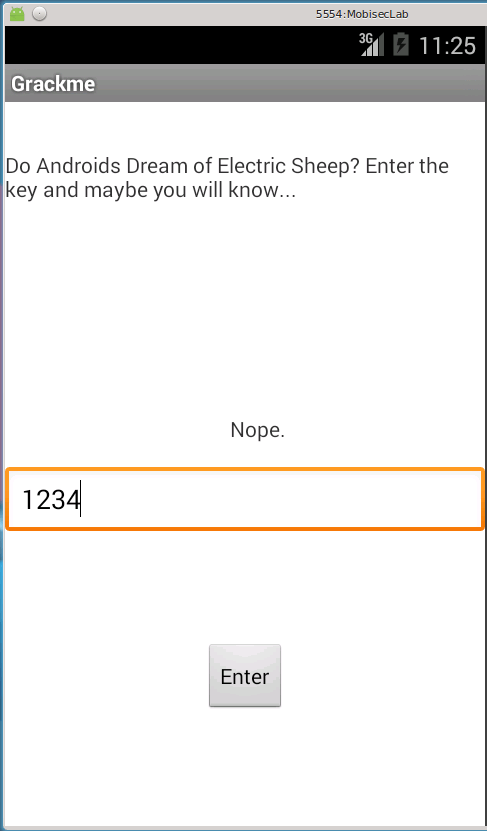
The Android application looks like this:
Basic identification
apktool
$ java -jar apktool_2.0.1.jar d GrehAndroidMe.apk I: Using Apktool 2.0.1 on GrehAndroidMe.apk I: Loading resource table... I: Decoding AndroidManifest.xml with resources... I: Loading resource table from file: /home/unknown/apktool/framework/1.apk I: Regular manifest package... I: Decoding file-resources... I: Decoding values */* XMLs... I: Baksmaling classes.dex... I: Copying assets and libs... I: Copying unknown files... I: Copying original files...
$ grep activity AndroidManifest.xml
<activity android:label="@string/title_activity_main" android:name=".MainActivity">
</activity>
dex2jar
$ ./d2j-dex2jar.sh GrehAndroidMe.apk dex2jar GrehAndroidMe.apk -> ./GrehAndroidMe-dex2jar.jar
$ ./jd-gui GrehAndroidMe-dex2jar.jar
JD-GUI shows the following classes:
Comments
Keywords: grehack-2012 reverse-engineering crackme android apk