GreHack-2012/50-A Nice Security Project
Jump to navigation
Jump to search
| You are here | 50-A Nice Security Project
|
Description
GreHack CTF 2012 reverse engineering challenge (50 points).
When you run the challenge, you see that the program is expecting the password to be provided as a parameter:
C:\CTF>rev50_A_Nice_Security_Project.exe Usage: rev50_A_Nice_Security_Project.exe pass C:\CTF>rev50_A_Nice_Security_Project.exe password Wrong password
Analysis
Interesting code
start is calling sub_401190 at offset 0x4014F5:
.text:004014E0 start proc near
.text:004014E0 sub esp, 0Ch
.text:004014E3 mov ds:dword_405040, 0
.text:004014ED call sub_4023D0
.text:004014F2 add esp, 0Ch
.text:004014F5 jmp sub_401190
.text:004014F5 start endp
sub_401190 is then calling sub_4017B8 at offset 0x4013F4 and sub_4017B8 is calling sub_401726 at offset 0x4017ED.
sub_401726
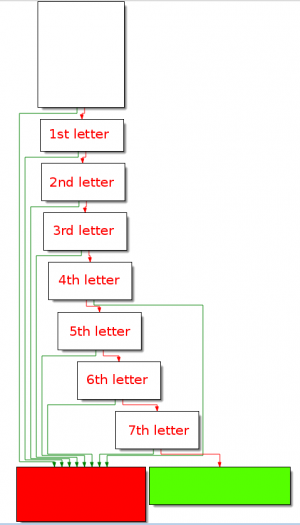
The function layout is as follows:
As you can see, each letter of the provided password is tested. If one of the letter is not the expected one, the test fails and the code jumps to the bad boy. If all letters are correct, the code eventually jumps to the good boy.
Below is the code:
.text:00401726 sub_401726 proc near
.text:00401726
.text:00401726 Format = dword ptr -28h
.text:00401726 var_C = dword ptr -0Ch
.text:00401726 arg_0 = dword ptr 8
.text:00401726 arg_4 = dword ptr 0Ch
.text:00401726
.text:00401726 push ebp
.text:00401727 mov ebp, esp
.text:00401729 sub esp, 28h
.text:0040172C mov [ebp+var_C], 0
.text:00401733 cmp [ebp+arg_4], 7
.text:00401737 jnz short loc_4017AA
.text:00401739 mov eax, [ebp+arg_0]
.text:0040173C movzx eax, byte ptr [eax]
.text:0040173F cmp al, 'S' ; 1st letter: 'S'
.text:00401741 jnz short loc_4017AA
.text:00401743 mov eax, [ebp+arg_0]
.text:00401746 add eax, 1
.text:00401749 movzx eax, byte ptr [eax]
.text:0040174C cmp al, 'P' ; 2nd letter: 'P'
.text:0040174E jnz short loc_4017AA
.text:00401750 mov eax, [ebp+arg_0]
.text:00401753 add eax, 2
.text:00401756 movzx eax, byte ptr [eax]
.text:00401759 cmp al, 'a' ; 3rd letter: 'a'
.text:0040175B jnz short loc_4017AA
.text:0040175D mov eax, [ebp+arg_0]
.text:00401760 add eax, 3
.text:00401763 movzx eax, byte ptr [eax]
.text:00401766 cmp al, 'C' ; 4th letter: 'C'
.text:00401768 jnz short loc_4017AA
.text:0040176A mov eax, [ebp+arg_0]
.text:0040176D add eax, 4
.text:00401770 movzx eax, byte ptr [eax]
.text:00401773 cmp al, 'I' ; 5th letter: 'I'
.text:00401775 jnz short loc_4017AA
.text:00401777 mov eax, [ebp+arg_0]
.text:0040177A add eax, 5
.text:0040177D movzx eax, byte ptr [eax]
.text:00401780 cmp al, 'o' ; 6th letter: 'o'
.text:00401782 jnz short loc_4017AA
.text:00401784 mov eax, [ebp+arg_0]
.text:00401787 add eax, 6
.text:0040178A movzx eax, byte ptr [eax]
.text:0040178D cmp al, 'S' ; 7th letter: 'S'
.text:0040178F jnz short loc_4017AA
.text:00401791 mov eax, offset aGratzMan ; "Gratz man :)"
.text:00401796 mov [esp+28h+Format], eax ; Format
.text:00401799 call printf
.text:0040179E mov [esp+28h+Format], 0 ; Code
.text:004017A5 call exit
.text:004017AA ; ---------------------------------------------------------------------------
.text:004017AA
.text:004017AA loc_4017AA:
.text:004017AA mov [esp+28h+Format], offset Str ; "Wrong password"
.text:004017B1 call puts
.text:004017B6 leave
.text:004017B7 retn
.text:004017B7 sub_401726 endp
The solution is SPaCIoS:
C:\CTF>rev50_A_Nice_Security_Project.exe SPaCIoS Gratz man :)
Comments
Keywords: grehack-2012 assembly x86 reverse-engineering crackme