Hackthissite/Realistic/Level7
- Level: Realistic::7 (What's Right For America)
- URL: http://www.hackthissite.org/missions/realistic/6/
- Difficulty :





- Exercise: A homophobic hate group is spreading their conservative propaganda of blind obedience and bigoted war mongering. Help tolerance activists take over their website of ignorance and discrimination.
Message: Friend of freedom and liberty, I invite you to take a look at the hate speech being spewed over the web at http://www.hackthissite.org/missions/realistic/7/. It's so funny that conservatives keep saying they want to protect the values of America - freedom, tolerance, and democracy - but when it comes to personal choices like private marijuana use or same-sex marriages, they damn them to burn in eternal hell and send them to jail. This is a personal freedom issue. No one else is hurt if two consenting adults decide to marry. But people who claim to have the moral high ground decide to ruin it for everyone else and discriminate against same-sex couples. To think that they are talking about making a constitutional amendment to STOP OUR FREEDOM TO MARRY is ludicrous. This injustice must be stopped. There is an admin section on that website somewhere, perhaps hidden among their directory structure. It would be a great fight against moral tyranny and a victory for freedom if you could somehow hack into their website. Thank you.
- Solution:
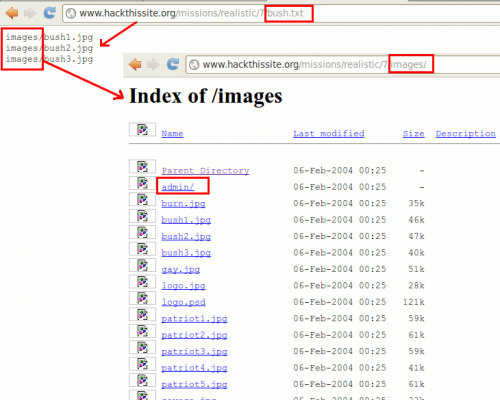
By clicking on the links (Patriotism | Long Live Bush | Nuke the bastards!) we notice that it calls the same page with a different parameter: showimages.php?file=<file.txt> to get the list of images. Furthermore, by calling one of these files in the url (e.g. war.txt), it displays the path to these pics (images/). In this directory, we see an admin/ directory, that seems to be protected by a .htaccess file.
Using the first info, we are able to get the content of the .htpasswd (http://www.hackthissite.org/missions/realistic/7/showimages.php?file=images/admin/.htpasswd) because showimages.php doesn't control the content of the parameters. You can get the content of the password file (.htpasswd) by copying it from the source code (administrator:$1$AAODv...$gXPqGkIO3Cu6dnclE/sok1). It is then easy to crack it with John The Ripper. We create a file named htpasswd, paste the string in it and do:
./john htpasswd
It gives us the combination of login/password: administrator/shadow