IScanner
Description
iScanner is a tool developed by iSecur1ty to analyze suspicious patterns (e.g. hidden IFRAMES) in files. It will produce a full report of the findings.
Installation
Download iScanner:
$ cd ~/src/ $ git clone https://github.com/iSecur1ty/iScanner.git $ cd iScanner/
Choose a login and password (replace with correct values) for the iscanner mysql account:
$ sed -i 's/mysql_user\ =\ ""/mysql_user="root"/' core/config.py web_ui/Module/web_config.py $ sed -i 's/mysql_pass\ =\ ""/mysql_pass="P55w0rd"/' core/config.py web_ui/Module/web_config.py
Then install iScanner:
$ sudo python setup.py install
When prompted, enter the root mysql credentials.
Usage
Command Line (CLI)
Syntax
iScanner is installed in /etc/iscanner/.
Syntax: sudo ./iscanner.py [path_to_scan] [scan_type] [scan_name]
Options
- path_to_scan
- Directory containing the files to be scanned
- scan_type
- Can be one of the following:
- -A: iScanner will search for Malware in all types of files; PHP, JS, HTML, PERL, RUBY, PYTHON.
- php: iScanner will search for Malware in PHP files.
- js: iScanner will search for Malware in JavaScript files.
- html: iScanner will search for Malware in HTML files.
- scan_name
- Name of the scan that will be saved
Web UI
Update the password
Before you can access the web UI, you need to update the password (only 1 account is currently available).
$ python web_ui/Module/ui_login <login> <password>
For example:
$ python web_ui/Module/ui_login iscanner P44w0rd
Start the Web UI
The server can be started by issuing (adapt the port):
$ cd /web_ui/ $ sudo ./main.py 127.0.0.1 8081
Then point your browser to http://127.0.0.1:8081/.
Interface
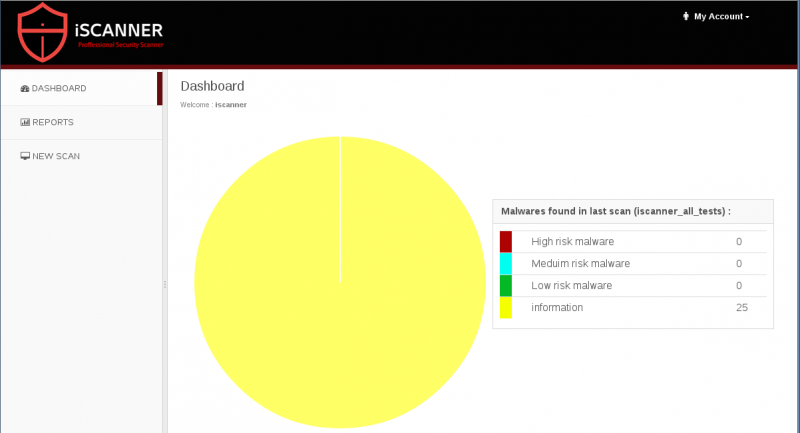
Dashboard
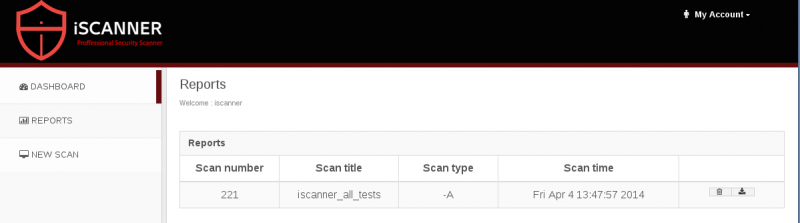
Reports
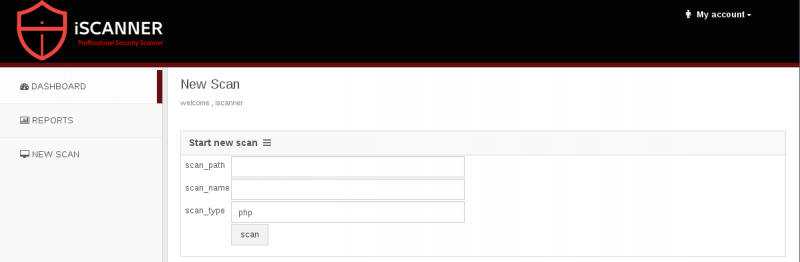
New scan
Write your own signatures
The signatures are saved in the database, in the malware_information table:
+-------------+--------------+------+-----+---------+----------------+ | Field | Type | Null | Key | Default | Extra | +-------------+--------------+------+-----+---------+----------------+ | id | int(11) | NO | PRI | NULL | auto_increment | | name | text | NO | | NULL | | | signature | text | NO | | NULL | | | description | text | NO | | NULL | | | risk | text | NO | | NULL | | | type | varchar(255) | NO | | NULL | | +-------------+--------------+------+-----+---------+----------------+
Currently, there are 27 signatures, distributed as follows:
+--------+-------------+ | type | count(type) | +--------+-------------+ | PERL | 2 | | PHP | 24 | | PYTHON | 1 | +--------+-------------+
Here are some examples:
+----+------+---------------------------+------------------------------------------------------------------------------------------------------+
| id | type | name | signature |
+----+------+---------------------------+------------------------------------------------------------------------------------------------------+
| 5 | PHP | C99_PHP_SHELL | c99sh_getupdate() |
| 10 | PHP | EVAL_BASE64_PHP_CODE | eval(base64_decode( |
| 16 | PHP | METASLOIT_PHP_METERPRETER | $s = $f("tcp://{$ip}:{$port}") |
| 27 | PERL | ZONE-H_PERL_SCRIPT | $sock = IO::Socket::INET->new(PeerAddr => "www.zone-h.org", PeerPort => 80, Proto => "tcp") or next; |
| 32 | PHP | SEC_WAR_SHELL | $fp2 = fopen(".htaccess","w+"); |
+----+------+---------------------------+------------------------------------------------------------------------------------------------------+
Example
$ sudo ./iscanner.py /data/malware/ -A iscanner_all_tests
Database Connected Successfully
[+] Scanning files has started at ------------------Fri Apr 4 13:46:51 2014
opening temp filetemp
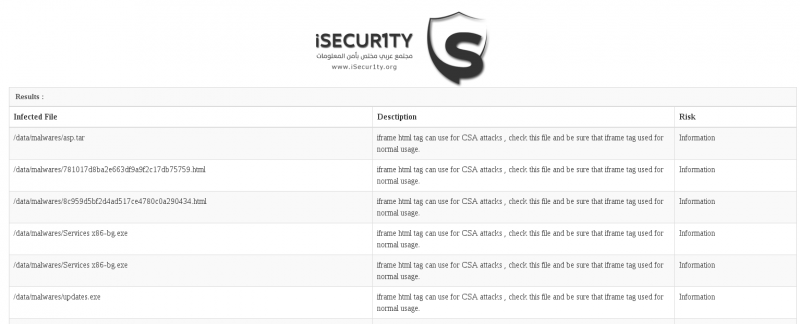
There is an infection found in /data/malware/asp.tar
There is an infection found in /data/malware/781017d8ba2e663df9a9f2c17db75759.html
There is an infection found in /data/malware/8c959d5bf2d4ad517ce4780c0a290434.html
There is an infection found in /data/malware/Services x86-bg.exe
[SNIP]
Total infection is 25
your report is saved at : /etc/iscanner/reports/iscanner_all_tests..html
0.01 (1): INSERT INTO scans_info (scan_time, scan_name, scan_type, risk_high, scan_path, risk_information, infected_files_number, risk_meduim, risk_low) VALUES ('Fri Apr 4 13:47:57 2014', 'iscanner_all_tests', '-A', 0, '/etc/iscanner/web_ui/static/reports/iscanner_all_tests..html', 25, 25, 0, 0)
0.02 (2): SELECT last_insert_id();
New Report Inserted successfully
The HTML report looks like this: