Mandiant-auditparser
Jump to navigation
Jump to search
| You are here: | AuditParser
|
Description
Audit Parser is a python based tool written by Ryan Kazanciyan at Mandiant. It converts the raw XML output generated by by Mandiant Intelligent Response, Redline, or IOC Finder into tab-delimited text files. These files contain extensive evidence from disk, registry, event logs, memory, and other parsed Windows artifacts that can be used for live response analysis. The tab-delimited data can easily be reviewed in spreadsheet applications like Microsoft Excel or LibreOffice Calc.
Installation
$ sudo aptitude install python-lxml $ cd /data/src/ $ git clone https://github.com/mandiant/AuditParser.git $ cd AuditParser/
Usage
Syntax
Usage: AuditParser.py [options]
Options
- -h, --help
- show this help message and exit
- -i INPATH, --input=INPATH
- XML input directory (req). NO TRAILING SLASHES
- -o OUTPATH, --output=OUTPATH
- Output directory (req). NO TRAILING SLASHES
- -t, --timeline
- Build timeline, requires --starttime and --endtime
- --starttime=STARTTIME
- Start time, format yyyy-mm-ddThh:mm:ssZ
- --endtime=ENDTIME
- End time, format yyyy-mm-ddThh:mm:ssZ
Examples
Output
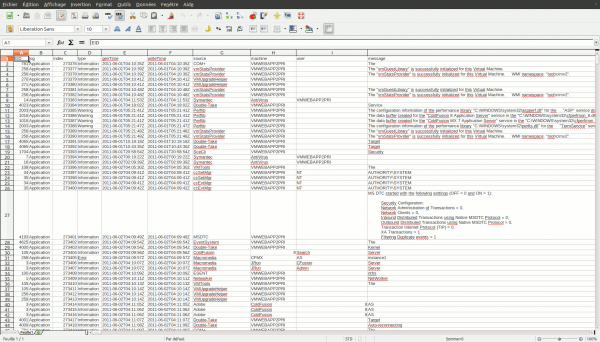
$ python AuditParser.py -i /data/tmp/20130329114223/ -o /data/tmp/ioc/ Parsing input file: /data/tmp/20130329114223/mir.w32ports.2d093875.xml Parsing input file: /data/tmp/20130329114223/mir.w32drivers-modulelist.7c57415e.xml Parsing input file: /data/tmp/20130329114223/mir.w32prefetch.735e3327.xml Parsing input file: /data/tmp/20130329114223/mir.w32services.652d723b.xml Parsing input file: /data/tmp/20130329114223/mir.w32kernel-hookdetection.08637537.xml Parsing input file: /data/tmp/20130329114223/mir.w32useraccounts.101b2855.xml Parsing input file: /data/tmp/20130329114223/mir.w32volumes.1a1e453a.xml Parsing input file: /data/tmp/20130329114223/mir.filedownloadhistory.130a6e43.xml Parsing input file: /data/tmp/20130329114223/mir.w32network-dns.67124311.xml Parsing input file: /data/tmp/20130329114223/mir.w32registryapi.232c5a3b.xml Parsing input file: /data/tmp/20130329114223/mir.w32processes-memory.1e571f14.xml Parsing input file: /data/tmp/20130329114223/mir.w32tasks.23246131.xml Parsing input file: /data/tmp/20130329114223/mir.w32systemrestore.226f2f7e.xml Parsing input file: /data/tmp/20130329114223/mir.formhistory.157a6f5f.xml Parsing input file: /data/tmp/20130329114223/mir.cookiehistory.5f075330.xml Parsing input file: /data/tmp/20130329114223/mir.w32eventlogs.4e3d0e14.xml Parsing input file: /data/tmp/20130329114223/mir.urlhistory.57026223.xml Parsing input file: /data/tmp/20130329114223/mir.w32network-arp.044d0a72.xml Parsing input file: /data/tmp/20130329114223/mir.w32scripting-persistence.21467952.xml Parsing input file: /data/tmp/20130329114223/mir.w32system.0a033e38.xml Parsing input file: /data/tmp/20130329114223/mir.w32drivers-signature.146f3b5b.xml Parsing input file: /data/tmp/20130329114223/mir.w32network-route.2e391015.xml Parsing input file: /data/tmp/20130329114223/mir.w32hivelist.27321078.xml Parsing input file: /data/tmp/20130329114223/mir.w32disks.32421969.xml Parsing input file: /data/tmp/20130329114223/mir.w32rawfiles.546e1004.xml
It results in a serie of txt files (separator: tabulator) that you can open with Calc or Excel:
Timeline analysis
One cool feature is the ability to extract all events from a given period of time:
$ python AuditParser.py -i /data/tmp/IOC-dragondildo.exe/ -o /data/tmp/ioc/ \
-t --starttime=2013-03-29T03:49:00Z --endtime=2013-03-29T03:53:00Z
$ cat /data/tmp/ioc/timeline.txt
Timestamp Time Desc RowType User EntryDesc EntryData Entry2Desc Entry2Data
2013-03-29T03:49:23 Modified RegistryItem BUILTIN\Administrators Path HKEY_LOCAL_MACHINE\SOFTWA
RE\Macromedia\ColdFusion\CurrentVersion\Clients\38161-89880284
2013-03-29T03:49:23 Modified RegistryItem BUILTIN\Administrators Path HKEY_LOCAL_MACHINE\SOFTWA
RE\Macromedia\ColdFusion\CurrentVersion\Clients\38161-89880284\urltoken Text CFID=38161&CFTOKEN=89880284
2013-03-29T03:49:23 Modified RegistryItem BUILTIN\Administrators Path HKEY_LOCAL_MACHINE\SOFTWA
RE\Macromedia\ColdFusion\CurrentVersion\Clients\38161-89880284\lastvisit Text {ts '2013-03-28 23:49:23'
}
2013-03-29T03:49:23 Modified RegistryItem BUILTIN\Administrators Path HKEY_LOCAL_MACHINE\SOFTWA
RE\Macromedia\ColdFusion\CurrentVersion\Clients\38161-89880284\timecreated Text {ts '2013-03-28 23:48:53'
}
2013-03-29T03:49:23 Modified RegistryItem BUILTIN\Administrators Path HKEY_LOCAL_MACHINE\SOFTWA
RE\Macromedia\ColdFusion\CurrentVersion\Clients\38161-89880284\hitcount Text 2
2013-03-29T03:49:23 Modified RegistryItem BUILTIN\Administrators Path HKEY_LOCAL_MACHINE\SOFTWA
RE\Macromedia\ColdFusion\CurrentVersion\Clients\38161-89880284\cftoken Text 89880284
2013-03-29T03:49:23 Modified RegistryItem BUILTIN\Administrators Path HKEY_LOCAL_MACHINE\SOFTWA
RE\Macromedia\ColdFusion\CurrentVersion\Clients\38161-89880284\cfid Text 38161
2013-03-29T03:50:17 Modified RegistryItem BUILTIN\Administrators Path HKEY_LOCAL_MACHINE\SOFTWA
RE\Macromedia\ColdFusion\CurrentVersion\Clients\38166-29139396
2013-03-29T03:50:17 Modified RegistryItem BUILTIN\Administrators Path HKEY_LOCAL_MACHINE\SOFTWA
RE\Macromedia\ColdFusion\CurrentVersion\Clients\38166-29139396\urltoken Text CFID=38166&CFTOKEN=29139396
2013-03-29T03:50:17 Modified RegistryItem BUILTIN\Administrators Path HKEY_LOCAL_MACHINE\SOFTWA
RE\Macromedia\ColdFusion\CurrentVersion\Clients\38166-29139396\lastvisit Text {ts '2013-03-28 23:50:17'
}
2013-03-29T03:50:17 Modified RegistryItem BUILTIN\Administrators Path HKEY_LOCAL_MACHINE\SOFTWA
RE\Macromedia\ColdFusion\CurrentVersion\Clients\38166-29139396\timecreated Text {ts '2013-03-28 23:49:47'
}
2013-03-29T03:50:17 Modified RegistryItem BUILTIN\Administrators Path HKEY_LOCAL_MACHINE\SOFTWA
RE\Macromedia\ColdFusion\CurrentVersion\Clients\38166-29139396\hitcount Text 2
2013-03-29T03:50:17 Modified RegistryItem BUILTIN\Administrators Path HKEY_LOCAL_MACHINE\SOFTWA
RE\Macromedia\ColdFusion\CurrentVersion\Clients\38166-29139396\cftoken Text 29139396
2013-03-29T03:50:17 Modified RegistryItem BUILTIN\Administrators Path HKEY_LOCAL_MACHINE\SOFTWA
RE\Macromedia\ColdFusion\CurrentVersion\Clients\38166-29139396\cfid Text 38166
[REMOVED]