Port knocking et spa:Spa
Single Packet Authorization : Fwknop
Description
Il n’existe pas de package Debian disponible pour installer directement fwknop. C’est pourquoi nous installerons fwknop à partir des sources. Cette installation est néanmoins aisée car basée sur l’exécution d’un seul script Perl.
Pré-requis
Les packages suivants doivent être installés au préalable :
# apt-get install mailutils ntpdate libpcap-dev
Installation
Installation de base
# cd /usr/local/src # wget http://cipherdyne.org/fwknop/download/fwknop-1.9.3.tar.gz # tar xzvf fwknop-1.9.3.tar.gz # cd fwknop-1.9.3 # ./install.pl
Une série de questions vous est alors posée. Les réponses sont en gras (lorsque la touche ENTER est pressée sans option, le choix retenu est celui par défaut, entre crochets, parmi les options proposées).
[+] fwknop can act as a server (i.e. monitoring authentication packets
and sequences, and taking the appropriate action on the local system
to alter the firewall policy or execute commands), or as a client (i.e.
by manufacturing authentication packets and sequences).
In which mode will fwknop be executed on the local system? (Note that
fwknop can still be used as a client even if you select "server" here).
(client/[server]): << ENTER >>
[+] In server mode, fwknop can acquire packet through a pcap file that is
generated by a sniffer (or through the Netfilter ulogd pcap writer), or
by sniffing packets directly off the wire via the Net::Pcap perl
module.
Fwknop can also acquire packet data from iptables syslog messages, but
this is only supported for the legacy port knocking mode; Single Packet
Authorization (SPA), which is used in the pcap modes, is a better
authorization strategy from every perspective (see the fwknop man page
for more information). If you intend to use iptables log messages (only
makes
sense for the legacy port knocking mode), then fwknop will need to
reconfigure your syslog daemon to write kern.info messages to the
/var/lib/fwknop/fwknopfifo named pipe. It is highly recommended
to use one of the pcap modes unless you really want the old port
knocking method.
Which of the following data acquistion methods would you like to use?
([pcap], file_pcap, ulogd, syslogd, syslog-ng): << ENTER >>
[+] It appears that the following network interfaces are attached to the
system:
eth0
eth1
lo
sit0
Which network interface would you like fwknop to sniff packets from?
<< eth0 >>
[+] Would you like access alerts sent to a different address ([y]/n)?
<< ENTER >>
[+] To which email address(es) would you like fwknop alerts to be sent?
You can enter as many email addresses as you like; each on its own
line.
End with a "." on a line by itself.
Email Address: << email_1@localhost >>
Email Address: << email_2@localhost >>
Email Address: .
[+] Enable fwknop at boot time ([y]/n)? << ENTER >>
L’installation de base de fwknop permet d’utiliser des paquets SPA protégés par un simple mot de passe. Néanmoins, il est fortement conseillé d’utiliser des clés GPG à la place. Le paragraphe qui suit explique comment procéder.
Génération des clés GPG
La procédure de génération et d’échange des clés peut se schématiser comme suit :
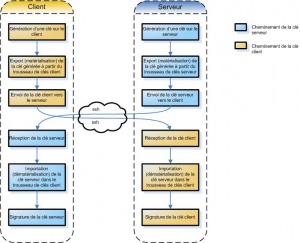
Les étapes sont détaillées dans les points qui suivent.
Génération de la clé sur le serveur
Sur le serveur, exécutez les commandes suivantes :
# gpg --gen-key
gpg (GnuPG) 1.4.6; Copyright (C) 2006 Free Software Foundation, Inc.
This program comes with ABSOLUTELY NO WARRANTY.
This is free software, and you are welcome to redistribute it
under certain conditions. See the file COPYING for details.
Please select what kind of key you want:
(1) DSA and Elgamal (default)
(2) DSA (sign only)
(5) RSA (sign only)
Your selection? << ENTER >>
DSA keypair will have 1024 bits.
ELG-E keys may be between 1024 and 4096 bits long.
What keysize do you want? (2048) << ENTER >>
Requested keysize is 2048 bits
Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
Key is valid for? (0) << ENTER >>
Key does not expire at all
Is this correct? (y/N) y
You need a user ID to identify your key; the software constructs the user ID from the Real Name, Comment and Email Address in this form:
"Heinrich Heine (Der Dichter) <[email protected]>"
Real name: a011830
Email address: [email protected]
Comment: fwknop server key
You selected this USER-ID:
"a011830 (fwknop server key) <[email protected]>"
Change (N)ame, (C)omment, (E)mail or (O)kay/(Q)uit? O
You need a Passphrase to protect your secret key.
Enter passphrase: **********
Repeat passphrase: **********
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
+++++++++++++++.+++++++++++++++++++++++++..++++++++++++++++++++++++++++++.+++++++++++++++++++++++++.+++++.+++++++++++++++..+++++++++++++++.+++++.............+++++
gpg: key 5576C643 marked as ultimately trusted
public and secret key created and signed.
gpg: checking the trustdb
gpg: 3 marginal(s) needed, 1 complete(s) needed, PGP trust model
gpg: depth: 0 valid: 1 signed: 0 trust: 0-, 0q, 0n, 0m, 0f, 1u
pub 1024D/5576C643 2008-05-12
uid a011830 (fwknop server key) <[email protected]>
sub 2048g/D9394B4D 2008-05-12
Remarque :
Pendant la génération de la clé, il se peut que le message suivant apparaisse :
“Not enough random bytes available. Please do some other work to give the OS a chance to collect more entropy! (Need 227 more bytes)”.
Dans ce cas, connectez-vous à un autre terminal (tty) ou ouvrez une nouvelle connexion ssh et forcez le disque dur du serveur à fonctionner en effectuant des actions de recherche par exemple.
Vérification de la clé générée sur le serveur
Pour vérifier que la clé a été correctement générée, utilisez la commande suivante :
# gpg -–list-keys /root/.gnupg/pubring.gpg ------------------------ pub 1024D/37673824 2008-05-11 uid a011830 <[email protected]> sub 2048g/4E21A015 2008-05-11
Exportation de la clé publique générée sur le serveur
Exportons (matérialisation) la clé générée :
# gpg -a --export 37673824 > server.asc
Génération de la clé sur le client :
Vous devez maintenant générer la clé sur le client. Cette opération a été réalisée en environnement Cygwin grâce au package GnuPG.
$ gpg --gen-key $ gpg --list-keys /home/a011830/.gnupg/pubring.gpg -------------------------------- pub 1024D/C67130D2 2008-05-11 uid a011830 (fwknop client key) <[email protected]> sub 2048g/645F157F 2008-05-11 $ gpg -a --export C67130D2 > client.asc
Utilisez la function scp (copie sécurisée) pour transférer la clé client vers le serveur.
$ scp client.asc [email protected]: [email protected]'s password: ********** client.asc 100% 1699 1.7KB/s 00:00
Exportation de la clé serveur vers le client
Faites de même sur le serveur pour transférer la clé vers le client.
# scp server.asc [email protected]: [email protected]’s password: ********** server.asc 100% 1699 1.7KB/s 00:00
Signature des clés
Il est maintenant nécessaire d’importer et signer les clés.
Les commandes suivantes doivent être exécutées sur le serveur :
# gpg --import client.asc gpg: key C67130D2: public key "a011830 (fwknop client key) <[email protected]>" imported gpg: Total number processed: 1 gpg: imported: 1
Récupérez maintenant l’ID de la clé client puis signez la par les commandes suivantes :
# gpg --edit-key C67130D2
Command> sign
pub 1024D/C67130D2 created: 2008-05-12 expires: never usage: SC
trust: unknown validity: unknown
Primary key fingerprint: DBEE EE35 78BC CE59 0EC8 2317 AB0F 8396 5576 C643
a011830 (fwknop client key) <[email protected]>
Are you sure that you want to sign this key with your
key "a011830 (fwknop server key) <[email protected]>" (37673824)
Really sign? (y/N) y
You need a passphrase to unlock the secret key for
user: "a011830 (fwknop server key) <[email protected]>"
1024-bit DSA key, ID 37673824, created 2008-05-12
Command> quit
Save changes? (y/N) y
Faites de même sur le client :
$ gpg --import server.asc $ gpg --edit-key 37673824 Command> sign Command> quit
|
Port Knocking : Knockd
|
[Sommaire] |
[Suivant]
Paramétrage
|