RDTSC-Read-Time-Stamp-Counter
Description
The Read-Time-Stamp-Counter (RDTSC) instruction can be used by malware to determine how quicky the processor excutes the program's instructions. It returns the count of the number of ticks since the last system reboot as a 64-bit value placed into EDX:EAX.
Slowness in the processor's execution might indicate the presence of malware analysis tools, such as a debugger.
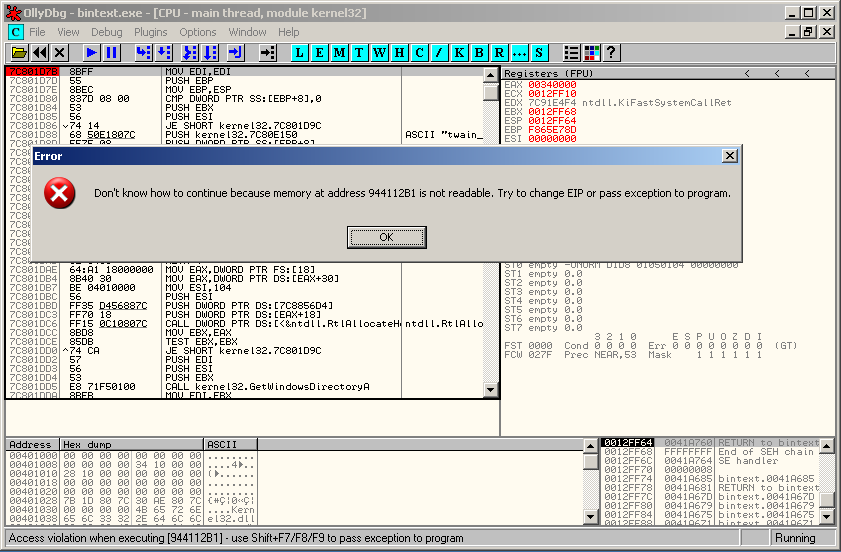
Following error messages can appear:
To identify the location of the timing defense, one approach is to activate the trace (beware, it could take a long time):
- To activate the trace: Debug > Trace Into (or Ctrl+F11)
- To see the trace log: View > Run trace
After a while, you should see the error message:
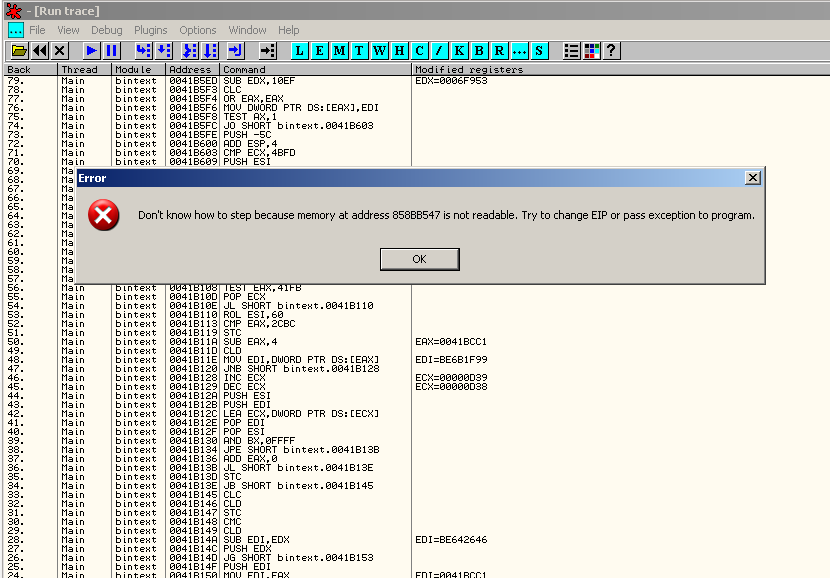
Scroll down at the end of the trace and check what instruction could have crashed the program:
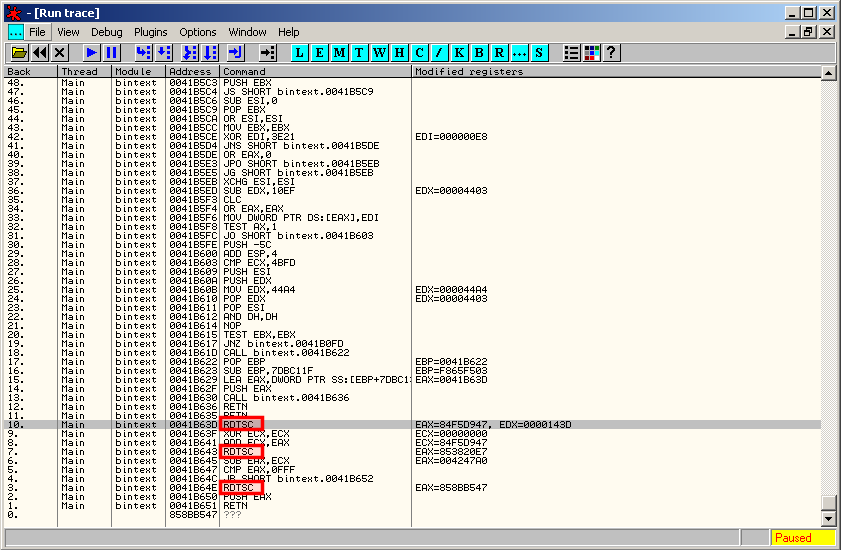
You can notice the presence of several RDTSC instructions, which is the sign of an attempt to detect our debugging environment. You can press ENTER to go to the assembly context:
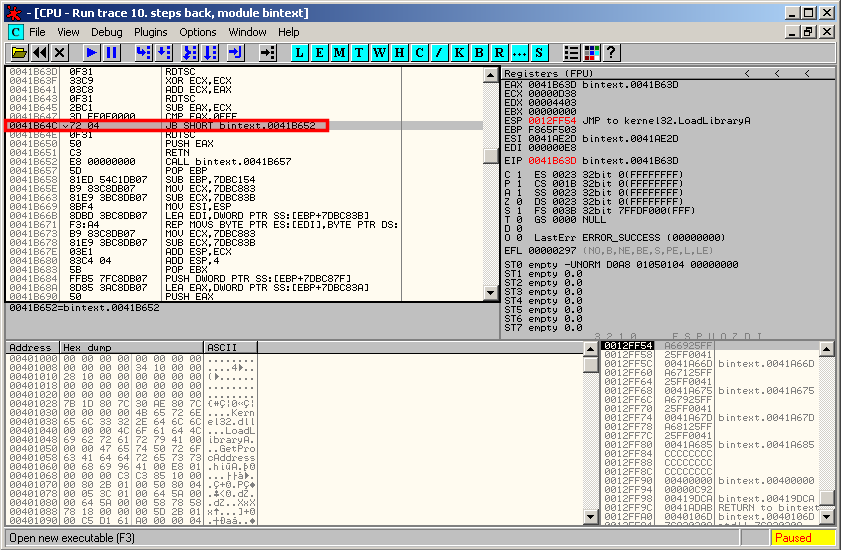
Notice that there is a jump that seems to be responsible for the crash. We will need to patch this instruction.
Overcome RDTSC defense
You can bypass the timing defenses by checking the "Anti-RDTSC" option in the OllyAdvanced plugin.