SharifCTF-2016/srm
| You are here | srm (50 points)
|
Description
The file (RM.exe) is a Windows 32 bit executable:
| MD5 | 105e5372413ad12b2fd78485d54b785b |
|---|---|
| SHA1 | 1dee31b54de559b5f1f948c865ad45bcd2e549fb |
| SHA256 | 78ba82e5136f3222b493b7cf2628b949a8f18d61cdcdf216f01d24ad9f9cff05 |
| File | PE32 executable (GUI) Intel 80386, for MS Windows |
Analysis
Running the executable
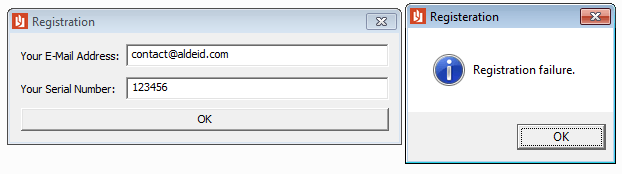
When launched, the program shows a graphical interface with 2 fields: an email address and a serial number:
Attempting to put some incorrect email or serials provides us with following messages:
- Your E-mail address is not valid
- Registration failure
DialogFunc
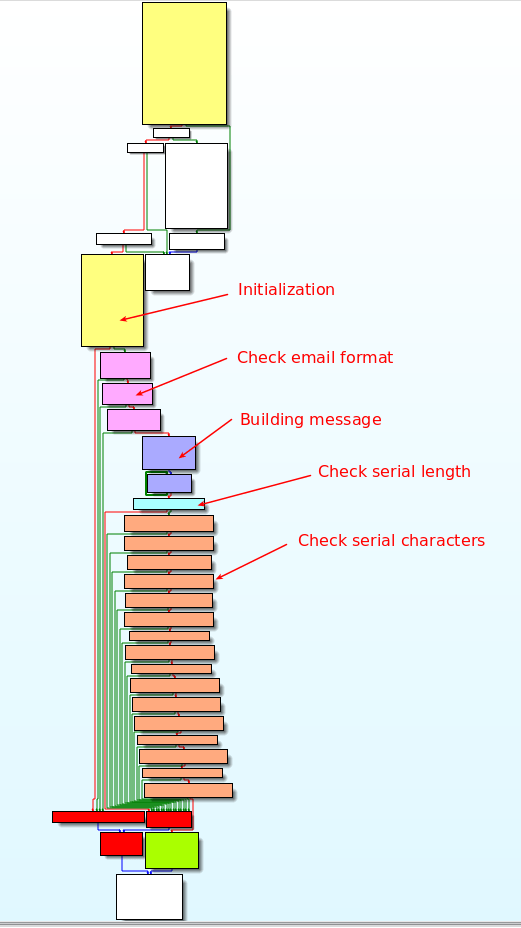
Graph overview
It should be quite straightforward to identfy that the interesting code is located in the DialogFunc function at offset 0x401280. Below is the graph overview of the function:
Checks
Without detailing every line of code, the program first checks the email format. If the user input provided for the email field does not contain required characters (@, ., ...), the program jumps to the invalid email format section.
.text:00401364 lea eax, [ebp+my_email]
.text:0040136A push offset a_ ; "."
.text:0040136F push eax
.text:00401370 call check_email_valid
.text:00401375 add esp, 8
.text:00401378 test eax, eax
.text:0040137A jz short loc_401346
.text:0040137C lea eax, [ebp+my_email]
.text:00401382 push offset a_ ; "."
.text:00401387 push eax
.text:00401388 call check_email_valid
.text:0040138D add esp, 8
.text:00401390 cmp byte ptr [eax+1], 0
.text:00401394 jz short loc_401346
.text:00401396 lea eax, [ebp+my_email]
.text:0040139C push offset unk_410A38 ; '@'
.text:004013A1 push eax
.text:004013A2 call check_email_valid
.text:004013A7 add esp, 8
.text:004013AA cmp byte ptr [eax+1], 2Eh
.text:004013AE jz short loc_401346
Later, at offset 0x4013F7, the serial length is checked. If the serial is not 16 characters long, the program jumps to the bad boy.
.text:004013F7 sub ecx, edx
.text:004013F9 cmp ecx, 10h ; len(my_serial) = 16
.text:004013FC jz short loc_401407
Checking serial characters
Then, each of the serial characters is tested. If a test fails, the program jumps to the bad boy, which would have been brute force a good candidate. But let's perform a static analysis. The full section is commented below:
.text:00401407 mov ecx, dword ptr [ebp+my_serial_00] ;
.text:00401407 ; ecx = my_serial
.text:0040140D cmp cl, 43h ; my_serial[0] = 'C'
.text:00401410 jnz short invalid_serial
;-----------------------------------------------------------------------------
.text:00401412 movsx eax, [ebp+my_serial_15]
.text:00401419 add eax, 43h
.text:0040141C cmp eax, 9Bh ; my_serial[15] = 0x9B - 0x43 = 'X'
.text:00401421 jnz short invalid_serial
;-----------------------------------------------------------------------------
.text:00401423 movsx ecx, ch ; ch = my_serial[1]
.text:00401426 lea eax, [ecx-3]
.text:00401429 cmp eax, 57h ; my_serial[1] = 0x57 + 3 = 'Z'
.text:0040142C jnz short invalid_serial
;-----------------------------------------------------------------------------
.text:0040142E movsx eax, [ebp+my_serial_14] ; eax = my_serial[14]
.text:00401435 add eax, ecx ; ecx = my_serial[1] = 'Z' (0x5A)
.text:00401437 cmp eax, 9Bh ; my_serial[14] = 0x9B - 0x5a = 'A'
.text:0040143C jnz short invalid_serial
;-----------------------------------------------------------------------------
.text:0040143E movsx ecx, [ebp+my_serial_02] ; ecx = my_serial[2]
.text:00401445 lea eax, [ecx+1]
.text:00401448 cmp eax, 3Ah ; my_serial[2] = 0x3A - 0x1 = '9'
.text:0040144B jnz short invalid_serial
;-----------------------------------------------------------------------------
.text:0040144D movsx eax, [ebp+my_serial_13] ; eax = my_serial[13]
.text:00401454 add eax, ecx ; ecx = my_serial[2] = '9' (0x39)
.text:00401456 cmp eax, 9Bh ; my_serial[13] = 0x9B - 0x39 = 'b'
.text:0040145B jnz short invalid_serial
;-----------------------------------------------------------------------------
.text:0040145D cmp [ebp+my_serial_03], 64h ; my_serial[3] = 'd'
.text:00401464 jnz short invalid_serial
;-----------------------------------------------------------------------------
.text:00401466 movsx eax, [ebp+my_serial_12]
.text:0040146D add eax, 64h
.text:00401470 cmp eax, 9Bh ; my_serial[12] = 0x9B - 0x64 = '7'
.text:00401475 jnz short invalid_serial
;-----------------------------------------------------------------------------
.text:00401477 cmp [ebp+my_serial_04], 6Dh ; my_serial[4] = 'm'
.text:0040147E jnz invalid_serial
;-----------------------------------------------------------------------------
.text:00401484 movsx eax, [ebp+my_serial_11]
.text:0040148B add eax, 81h
.text:00401490 cmp eax, 0C8h ; my_serial[11] = 0xC8 - 0x81 = 'G'
.text:00401495 jnz invalid_serial
;-----------------------------------------------------------------------------
.text:0040149B movsx ecx, [ebp+my_serial_05]
.text:004014A2 lea eax, [ecx-2Dh]
.text:004014A5 cmp eax, 44h ; my_serial[5] = 0x44 + 0x2D = 'q'
.text:004014A8 jnz invalid_serial
;-----------------------------------------------------------------------------
.text:004014AE movsx eax, [ebp+my_serial_10]
.text:004014B5 add eax, ecx ; ecx = my_serial[5] = 'q' (0x71)
.text:004014B7 cmp eax, 0AAh ; my_serial[10] = 0xAA - 0x71 = '9'
.text:004014BC jnz invalid_serial
;-----------------------------------------------------------------------------
.text:004014C2 cmp [ebp+my_serial_06], 34h ; my_serial[6] = '4'
.text:004014C9 jnz invalid_serial
;-----------------------------------------------------------------------------
.text:004014CF movsx eax, [ebp+my_serial_09]
.text:004014D6 add eax, 34h
.text:004014D9 cmp eax, 9Bh ; my_serial[9] = 0x9B - 0x34 = 'g'
.text:004014DE jnz invalid_serial
;-----------------------------------------------------------------------------
.text:004014E4 cmp [ebp+my_serial_07], 63h ; my_serial[7] = 'c'
.text:004014EB jnz invalid_serial
;-----------------------------------------------------------------------------
.text:004014F1 movsx eax, [ebp+my_serial_08]
.text:004014F8 add eax, 63h
.text:004014FB cmp eax, 9Bh ; my_serial[8] = 0x9B - 0x63 = '8'
.text:00401500 jnz invalid_serial
Solution
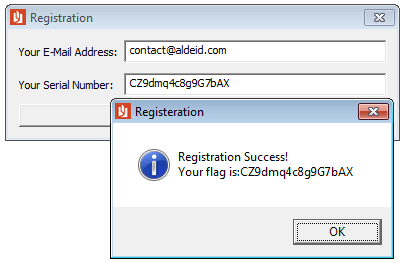
The above code eventually leads to the following serial:
CZ9dmq4c8g9G7bAX
It is our flag!
Comments
Keywords: sharif 2016 challenge reversing