Shell-in-a-box
Shell In A Box
What is Shell In A Box?
Description
ShellInABox is a service that enables to have a shell access to remote hosts via a web interface.
Web interface
ShellInABox web interface is a web terminal emulator. It integrates colors, editors, and all commands, like a standard console window.
Code review
ShellInABox is composed of:
- A server, coded in C
- A client (web browser) coded in JavaScript.
The client side uses an external stylesheet (styles.css) and an external JavaScript file (ShellInABox.js).
Is there any limitation in the commands?
- It seems that there is no limitation in the commands you issue.
- You can also use sudo to issue privileged commands.
- A reboot command has also been possible during the test.
Installation and service startup
Installation
$ cd /data/src/ $ wget http://shellinabox.googlecode.com/files/shellinabox-2.10.tar.gz $ tar xf shellinabox-2.10.tar.gz $ cd shellinabox-2.10/ $ ./configure $ make $ sudo make install
Starting service
To start the service, simply issue following command:
$ sudo shellinaboxd -s :\LOGIN
Service Fingerprinting
IANA database
IANA database (http://www.iana.org/assignments/port-numbers) references all registered ports numbers.
Default port (4200/tcp) used by ShellInABox hasn't been found in this database.
telnet
A telnet command issued against our target on port 4200/tcp provides us with useful information:
$ telnet 192.168.56.101 4200 Trying 192.168.56.101... Connected to 192.168.56.101. Escape character is '^]'. GET / HTTP/1.1 Host: 127.0.0.1:4200 HTTP/1.1 200 OK Content-Type: text/html Content-Length: 4818 <?xml version="1.0" encoding="utf-8"?> <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd"> <html xmlns="http://www.w3.org/1999/xhtml" xmlns:v="urn:schemas-microsoft-com:vml" xml:lang="en" lang="en"> <head> <!-- ShellInABox - Make command line applications available as AJAX web applications Copyright (C) 2008-2009 Markus Gutschke [email protected]
Nmap
Recent versions of Nmap (5.21) have integrated the ShellInABox banner in nmap-service-probes fingerprinting database.
match http m|^HTTP/1\.1 200 OK\r\n.*<\?xml version=\"1\.0\ " encoding=\"utf-8\"\?>\n<!DOCTYPE html PUBLIC \"-//W3C//DTD XHTML 1\.0 Transitional//EN\" \"http://www\.w3\.org/TR/xhtml1/DTD/xhtml1- transitional\.dtd\">\n<html xmlns=\"http://www\.w3\.org/1999/xhtml\" xmlns:v=\"urn:schemas-microsoft-com:vml\" xml:lang=\"en\" lang=\" en\">\n <head>\n <!--\n ShellInABox - Make command line applications available as AJAX web applications\n|s p/ShellInABox httpd /
And Nmap properly detects our service:
$ sudo nmap -sV -p 4200 192.168.56.101 Starting Nmap 5.21 ( http://nmap.org ) at 2010-10-01 09:12 CEST Nmap scan report for localhost.localdomain (127.0.0.1) Host is up (0.0050s latency). PORT STATE SERVICE VERSION 4200/tcp open http ShellInABox httpd Service detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 6.45 seconds
Brute-force

Thank you for your comprehension.
Sniffing
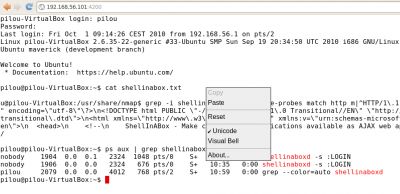
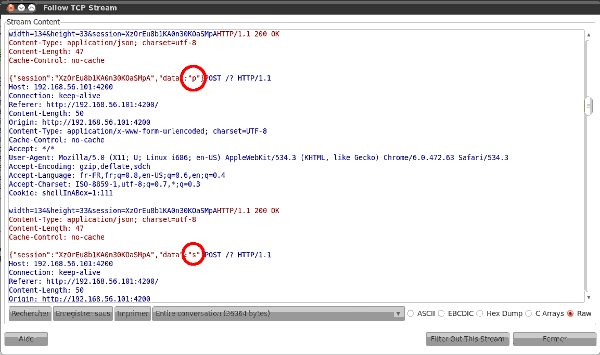
Sniffing has been done with wireshark without SSL/TLS. It shows that it is trivial to capture and recompose communication. The screenshot shows the beginning of the "ps aux" command.
How to secure?
- Compile ShellInABox with SSL/TLS support
- Install a blocking mechanism to prevent from brute-force attacks
- Change default port (-p)
- Check your logs (-v, --verbose)