Social-Engineering-Ninja
Description
Social Engineering Ninja (aka S-E Ninja) is a PHP toolkit with popular sites fake pages and anonymous mailer via mail() function in PHP.
Here is the complete list of phishing pages:
- Amazon.com
- Store.Apple.com
- Bank Of America
- Bank Of West
- Basic
- Cashu.com
- Comerica Bank
- Digg.com
- ebuddy.com (All Services)
- Facebook.com
- 53 Bank
- Gmail.com
- Godaddy.com
- Hotmail.com
- Mastercard.com
- Moniker Homepage (domainservice.com)
- Moniker Login (domainservice.com)
- Msn.com
- Myspace.com
- Onecard.com AR
- Onecard.com EN
- Oracle.com
- Paypal.com
- Rapidshare.com
- Travian.com AR
- Travian.com EN
- Twitter.com
- Visa.com
- Wachovia.com Bank
- Westrn Union
- Yahoo.com Mail
- Youtube.com
Installation
Create the database
$ mysql -u root -p mysql> CREATE USER seninja@localhost IDENTIFIED BY 'S3_N1nj4_P455'; mysql> CREATE DATABASE seninja; mysql> GRANT ALL PRIVILEGES ON seninja.* TO seninja@localhost;
Copy PHP files
These commands will enable to install SE-Ninja in the root of /var/www/. Adapt these commands to fit with your needs.
$ cd /var/www/ $ wget http://download331.mediafire.com/vywe7la8azog/fdid6239i37cplh/seninja-v0.2.rar $ unrar x seninja-v0.2.rar $ cd seninja-v0.2/ $ mv * .. $ rm -f -R seninja-v0.2/
Change configuration file
Edit /var/www/config/config.php and modify connection values:
$mysql_hostname = "localhost"; $mysql_username = "seninja"; $mysql_password = "S3_N1nj4_P455"; $mysql_database = "seninja";
Finish the installation
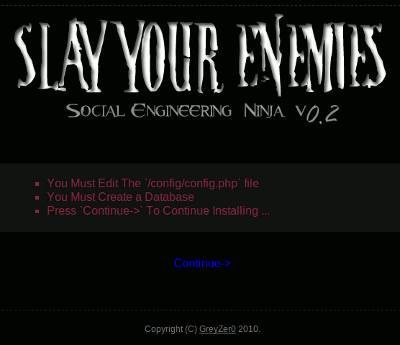
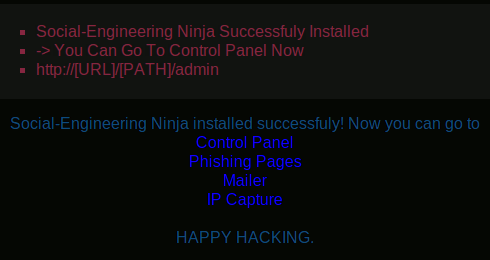
Go to http://localhost/install/. It should show following screen:
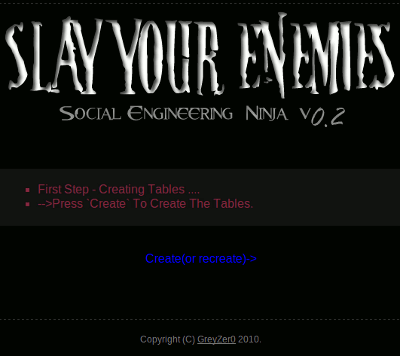
Click on "Continue". You should now have this screen:
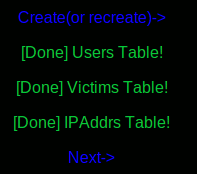
Click on "Create(or recreate)->"
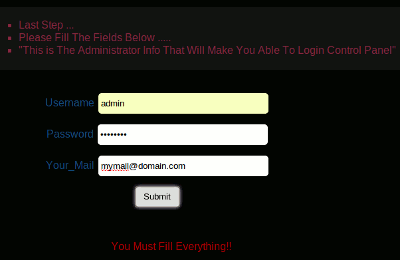
Once you have a success message, click on "Next->".
Complete the information by providing a login and password to be able to connect, and an email address to receive mail notifications (only if you have selected this option in the configuration file). Press the "Submit" button, then click on "Next->".
Usage
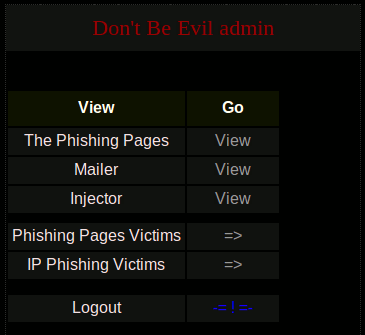
Admin module
To access the admin module, go to:
http://localhost/admin/
Authenticate with credentials you have provided during the installation. Once authenticated, you should get this:
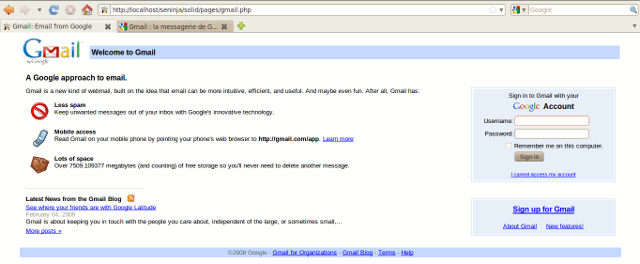
Phishing pages
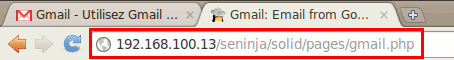
It is possible to view fake pages (phishing pages) by browsing in the /solid/pages/ directory.
Here is an example for the fake Gmail page:
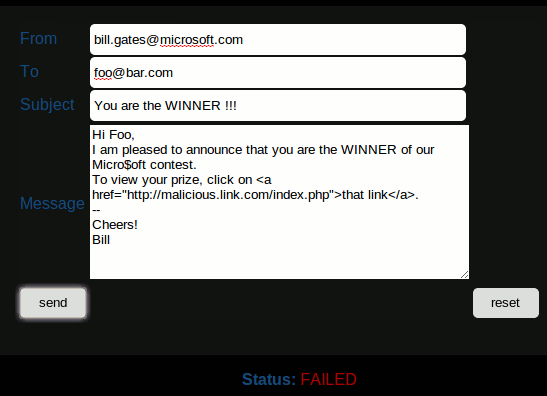
Mailer
The Mailer module enables to send anonymous mails:
injector

Thank you for your comprehension.
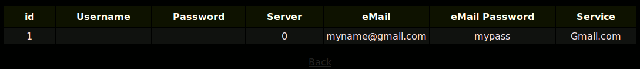
Phishing Pages Victims
This page shows the list of all stolen credentials:
IP Phishing Victims

Thank you for your comprehension.
Usage example
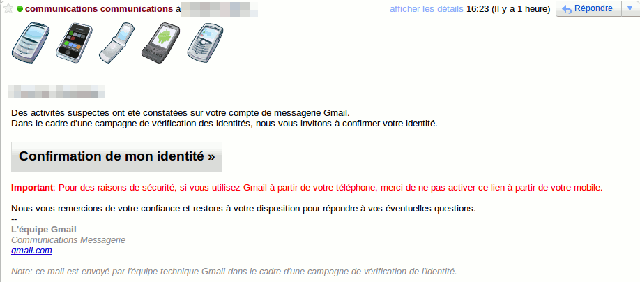
An attacker prepares a pretended mail from Gmail team with the Mailer module, containing a malicious link to an installation of Social Engineering Ninja and sends it to a victim. The victim clicks on the link and connects to the fake portal. He/she provides his/her credentials and is redirected to Gmail after a short period of time. Meanwhile, the credentials have been saved in the hacker's database.
Here is an example of such a mail. By clicking on the button, the victim is redirected to the fake Gmail portal.
See a video of a phishing example based on Twitter: http://www.youtube.com/watch?v=oQrF7Di57n0.
Protection
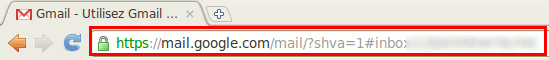
To avoid such tricks, always check the mail address before providing credentials or any other sensitive data.
By double clicking on the padlock, you can also check the validity of the certificate: