Ssh
Tunneling
local/remote socket
Suppose you are at work and want to browse 192.168.1.4 at your home but you can only access your ssh server. Of course you could run a VPN connection to your home but you can also do that with SSH:
_________ ___________________________________
/ \ / \
| | | |
| [work] ===={internet}====> [ssh server] ----> [192.168.1.4] |
| | | |
\_____ ___/ \___________________________________/
Establish a secured http connection (tunneled in SSH):
$ ssh -NL 1234:192.168.1.4:80 user@remotesshserver
Then browse http://127.0.0.1:1234 to access remote 192.168.1.4:80
SOCKS proxy
A SSH tunnel can be used to browse Internet resources (e.g. domains blocked) using another server:
_________ _______________
/ \ / \
| | | |
| [work] ===={internet}====> [ssh server] |
| | | |
\_____ ___/ \________________/
|| ||
X blocked ||
___||____ ||
/ \ ||
| | allowed ||
| website |=======================
| |
\_____ ___/
To do that, you only need to bind your SSH connection to a local socket (e.g. on port 8080) as follows:
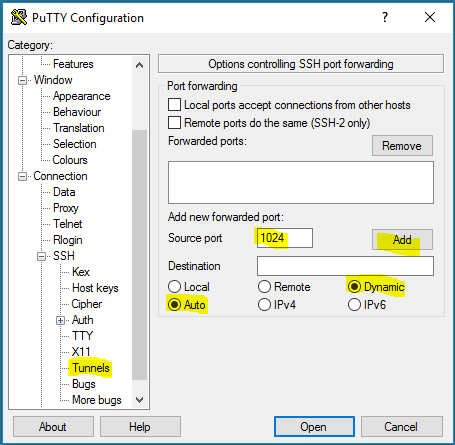
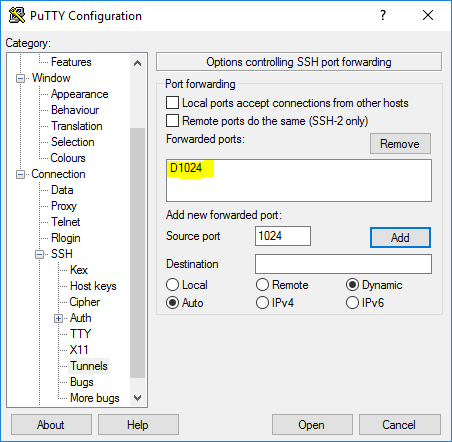
$ ssh -D 8080 user@remoteserver
On a Windows machine, you can do that with Putty:
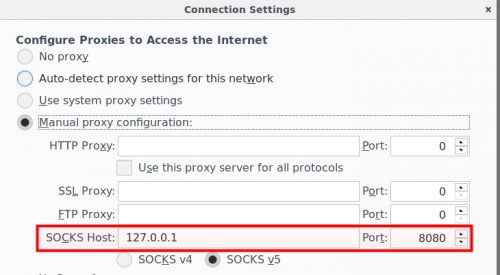
Then tell your browser to use a local SOCKS proxy as follows:
SSH without password
Standard user
Now, let's generate the keys:
On the client, run the following command and don't enter a passphrase when asked (leave empty):
$ ssh-keygen -t rsa
Now create the remote ~/.ssh directory:
$ ssh user@remotessh mkdir .ssh
And append the id_rsa.pub to the remote .ssh/authorized_keys file:
$ cat .ssh/id_rsa.pub | ssh user@remotessh 'cat >> .ssh/authorized_keys'
root access
Protect ssh root access as follows:
$ cat /etc/ssh/sshd_config ... PermitRootLogin without-password ...
This directive means that root access via ssh will be only possible via keys. Just do as previously and add id_rsa.pub to /root/.ssh/authorized_keys
rsync reverse
Suppose you have a remote server running on port 222/tcp and you want to perform an incremental backup from your client
$ rsync -avz -e "ssh -p 222" root@remotessh:/remote/path/ /local/path/ receiving incremental file list ./ test.txt test1/ test2/ sent 73 bytes received 171 bytes 162.67 bytes/sec total size is 5 speedup is 0.02